By Marco Giuliani
In the past few weeks a Chinese security company called Qihoo 360 blogged about a new BIOS rootkit hitting Chinese computers. This turned to be a very interesting discovery as it appears to be the first real malware targeting system BIOS since a well-known proof of concept called IceLord in 2007. The malware is called Mebromi and contains a bit of everything: a BIOS rootkit specifically targeting Award BIOS, a MBR rootkit, a kernel mode rootkit, a PE file infector and a Trojan downloader. At this time, Mebromi is not designed to infect 64-bit operating system and it is not able to infect the system if run with limited privileges.
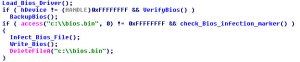
The infection starts with a small encrypted dropper that contains five crypted resource files: hook.rom, flash.dll, cbrom.exe, my.sys, bios.sys. The goal of these files will be presented later in this analysis.
The infection is clearly focused on Chinese users, because the dropper is carefully checking if the system it’s going to infect is protected by Chinese security software Rising Antivirus and Jiangmin KV Antivirus. To gain access to the BIOS, the infection first needs to get loaded in kernel mode so that it can handle with physical memory instead of virtual memory.
Many of you may recall the old CIH/Chernobyl infection, the infamous virus discovered in 1998 that was able to flash the motherboard BIOS, erasing it. Even CIH needed to gain kernel mode access to reach the BIOS, though at the time the virus was exploiting a privilege escalation bug in Windows 9x operating system which allowed it to overwrite the Interrupt Descriptor Table with its own payload from user mode, then triggering the overwritten interrupt handler and its malicious code is executed in kernel mode. Mebromi does not use such kind of privilege escalation trick anymore, it just needs to load its own kernel mode driver which will handle the BIOS infection. To do so, it uses two methods: it could either extract and load the flash.dll library which will load the bios.sys driver, or it stops the beep.sys service key, overwriting the beep.sys driver with its own bios.sys code, restart the service key and restore the original beep.sys code.
The bios.sys driver is the code which handle the BIOS infection. To read the BIOS code, it needs to map the physical memory located at physical memory address 0xF0000, this is where the BIOS ROM usually resides. Once read, the driver verifies if the BIOS ROM is Award BIOS, by checking the presence of the string: $@AWDFLA. If found, the driver tries to locate the SMI port that will be used by the rootkit to flash the BIOS ROM.
If the BIOS ROM matches the string, the rootkit saves a copy of the BIOS to the file C:bios.bin and pass the next step to the user mode component of the infection. The dropper extracts two files: cbrom.exe and hook.rom. Cbrom.exe is a legitimate tool developed by Phoenix Technologies, used to modify the Award/Phoenix BIOS ROM binaries. Hook.rom is the rootkit ISA BIOS ROM that is added to the BIOS binary, containing the rootkit infection. The dropper executes cbrom.exe with the /isa switch parameter, passing the hook.rom file. Before actually injecting the malicious ISA ROM, the dropper checks the BIOS ROM code looking for the “hook rom” string, used as a marker of the infection. If found, it means that the BIOS is already infected and it doesn’t need to be infected again.
After that the bios.bin file has been modified, the bios.sys driver send to the BIOS SMI port the command 0x29, used to erase the BIOS flash, and then the command 0x2F used to write the new BIOS ROM code to the BIOS ROM.
The BIOS is now infected, and the dropper goes to its next step: infecting the Master Boot Record. The infection is 14 sectors long and the original MBR is stored to the sector 7. To avoid potential startup issues, the infected MBR stores a copy of the original MBR’s partition table. Finally the dropper extracts the my.sys driver on the root of the C: drive. My.sys is a kernel mode rootkit that hijacks disk.sys’s IRP major functions, by redirecting the IRP_MJ_READ/WRITE and IRP_MJ_DEVICE_CONTROL native functions. It is used to hide the infection on the disk. Even if the BIOS infection doesn’t succeed, the rootkit does infect the MBR.
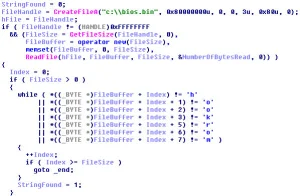
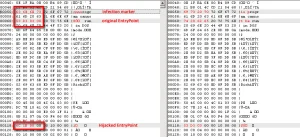
At the next system startup, after the BIOS POST phase, the malicious code injected inside it prepares the full MBR infection (all the first 14 sectors are stored inside the malicious BIOS rom, 7168 bytes in total) and checks the MBR code of the hard drive looking if the infection is already present. To do it, the BIOS malicious code checks for the presence of the string “int1” at the offset 0x92. If the string is not found, the BIOS malicious rom will overwrite all the first 14 sectors of the hard drive, thus restoring the MBR infection.
The system startup procedure continues and the control now passes to the malicious master boot record. Here the malicious payload analyzes the original MBR partition table and looks for the active partition, checking if it’s using a NTFS or FAT32 file system. The malicious MBR code contains indeed NTFS/FAT32 parser routines, used to get inside the file system to look for winlogon.exe or wininit.exe file. When found, the malicious code contains a file infection payload, able to inject malicious code inside the specified file and hijack the entry point of it. Before infecting the file, the MBR malicious code checks if it is already infected, by looking for the string “cnns” at the offset 0x50 from the beginning of the PE file. This is the infection marker. If the string is not found, the infection stores a crypted payload – about 600 bytes of code – inside winlogon.exe or wininit.exe and hijacks the PE entry point to the beginning of it, saving the original entry point at the offset 0x60.
The job of the MBR infection ends here, waiting for the Windows startup which will load the patched executable. When loaded, the payload self-decrypt its malicious code and loads in memory the my.sys driver. Then it tries to download an additional infection from the (now unavailable) URL address: http://dh.3515.info:806/test/91/calc[removed].
The concept behind Mebromi is not new. In fact we must recall the IceLord BIOS rootkit published in 2007, a public proof of concept able to target Award BIOS rom, using an approach very similar to the Mebromi one – or should we say that Mebromi is more than just inspired by the IceLord rootkit?
Storing the malicious code inside the BIOS ROM could actually become more than just a problem for security software, giving the fact that even if an antivirus detect and clean the MBR infection, it will be restored at the next system startup when the malicious BIOS payload would overwrite the MBR code again. Developing an antivirus utility able to clean the BIOS code is a challenge, because it needs to be totally error-proof, to avoid rendering the system unbootable at all. The job of handling with such specific system codes should be left to the developers of the specific motherboard model, who release BIOS updates along with specific tool to update the BIOS code.
On the other hand, although this kind of infection is potentially one of the most persistent infections known out there in the wild, it will hardly become a major threat because of the level of complexity needed to achieve the goal. While a kernel mode infection or a MBR infection could still work in a generic way among all the PC out there – and they still have a huge available free space to play with, a BIOS-based rootkit needs to be fully compatible with all major BIOS rom out there, it should be able to infect all the different releases of Award, Phoenix, AMI BIOS’s out there; a level of complexity that is simply unasked for writing a good persistent infection (e.g. TDL rootkit, various Rustock releases, ZeroAccess rootkit among all). In fact, why is Mebromi only targetting Award BIOS rom? Perhaps because there was already a known proof of concept that is 5 years old targeting Award BIOS ROM available online.
Are BIOS rootkits a real threat? Yes, we can consider Mebromi the first real BIOS rootkit incident discovered in the wild – let’s consider IceLord BIOS rootkit more a proof of concept. Should we be concerned about BIOS rootkits? Well, while we try to discover whether our PC is infected by an unknown and super-stealth BIOS rootkit, let’s try and look if there is a more “humble” kernel mode rootkit which is already infecting our PC, allowing a remote attacker to silently own our system.








brilliant break down, keep us posted on any developments
The statement at the end of the article which states that this kind of infection is hardly a major threat is somewhat erroneous. Considering world-wide mass infections, this method may not be practical. However, what should be evident based on the discussion at the beginning of this article is that this type of malware is extremely focused. The developer is only looking to infect very specific hardware in a specific locale. Most organizations standardize on a partcular hardware vendor. For someone to use this technology to maintain a persistent presence in a particular organization is where this type of malware presents a major threat.
Hello,
you are definitely right, Mebromi could be used for targeted attacks. I’ve actually said that it is a real threat, not just a proof of concept.
With major threat, I mean something that can easily spread worldwide. This is not the case because Mebromi is well focused on specific hardware.
Furthermore, we must say that there are many other examples of threats which have been able to spread and infect thousands of computers without being noticed by security companies for months. We can talk about Rustock rootkit, ZeroAccess rootkit, TDL rootkit, advanced threats working in kernel mode, able to infect computers worldwide, without being restrcited to specific hardware.
We can step back in the past and recall Gromozon, user mode (not even kernel mode) rootkit which has been able to freely spread for at least 5 months before being detected by security products.
All of this just to say that BIOS rootkits are a real threat, actually they could be used for targeted attacks. Though, virus writers don’t really need to focus on BIOS rootkits if they want to write an advanced threat able to stay invisible for all the time needed to steal data from the infected PC or remote control it. They can still do it without the restriction caused by hardware compatibility.
Regards,
Marco
this is old news to me i been dealing with it since feb 2011 when my Tosh Sat 305-35 caught on fire. So from logs and recovered Charred remains Of that comp and and My Touch Pro 2 which was also burned.
Id love to be proved wrong if anyone wants to. Now at the time that was a new computer and Was running linux Ubuntu and Win 7 ultimate 64x. . So heres the kicker… Why After Almost 7 months Do i still have it infecting 2 comps 3 laptops my My new TP2 and the 3 Replacements i recieved since feb , my Palm pre my sisters Sam Galaxy. Even my mustang and my brothers focus the Answer hit me 2 months ago… Bluetooth Links them all together. Thats the only possible link and untill i evens said this out load I tested it by looking at my phone which was so full of modified dlls and reg keys It Shows enum drivers using the blue tooth and Wlan Lan to Parse almost any simple device encryptions. And saving all Mac addresses it comes in contact with And Patching every piece of hardware. all I need to do somedays is just spend 30 mins at a kinko and within 15 mins i stat hearing paper jams Faxes not connecting and Terminal POS Stalling and Eventually the places is down for repairs. So why not just wipe it well its not that easy anymore its managed to convert my phone from win mo 6.5 to Win Ce.. Added the Netbios to it and the computers . The phones are the ultimate Trojans you take them everywhere your at least 8 ft from all the comps you touch and with Blue tooth used to sync Wifi To Maintain Connections To my home comp from miles away. Able to send meta deta to car stereos looking for song info. credit card reader and A Fm/Digital Tv tuner. Its gotten attached to everything On Usb’s and Storage it ceates a small 8mb partion etc etc etc
And From what Im looking at I first got this from my brother who downloads Flash Video Not sure the site but we all know the kind that would have one rushing in and clicking on a Fake Adobe flash downloader and not questioning why it installed without making you close the browsers fiRst. He had an old HP that was Utterly Infected it had BT and never bothered me untill feb 2 I buy a BT Dongle connected my comp to the phone. And went to sleep woke up at 7next morning choking on smoke with my am on fire And the Half the room Already lit. So again Pleace prove Me wrong id love nothing more and maybe help me clear this all. i welcome any requests for logs Or sample code.
So your brother downloaded porn and now you have a mass-destructive bluetooth armagedon?
Looks like trolling, seriously. A virus can’t set a computer on fire.
Glad to see you’ve moved over to the Webroot blog, Marco. Always enjoyed your writeups on Prevx. Keep it technical, keep it advanced!
=)
most computer attacks on us gov. networks come from asia, most computer hardware-built in asia. to much of this hardware is infected out of the box.
its not that hard to remove the bmw virus
if it is infected on a laptop… simply remove the battery and hold down on the power button for around 15 seconds. this should reset ur bios to factory mode. after that… all u needa do is delete all partition, format and install an OS
on a desk top… u would need to remove the tiny battery on ur mother board for around 1-2 hours
then use a windows cd to delete, format all partitions and reinstall windows.
well im not sure if i really got the BMW virus… cuz in ur article it says it only infect chinese antivirus users
well im an avg/ avast user and after i got the bios virus
both avast and avg said i have not entered the registration code correctly… at the same time o.0
i was also no able to system restore… system restore was also removed from my services
i was also not able to uninstall things
when i tried to reinstall windows… this message came up
“windows is unable to receive data from disk”
and within 2 hours i got the blue screen of death and upon reboot it said my hdd is not registered (that was like a wtf moment for me)
so i suggested to myself that it was a bios problem… and cutting the power to it seemed like a reasonable solution
so i cut the power to my laptop with the method above
and WAH LAH!
i was able to reinstall windows :3
You don’t always need to remove the battery. Holding the power button with the PC unlugged sometimes work. In others, you can check for a reset CMOS jumper.
Marco,
one question. Does the BIOS really get reset to its original state by just removing the battery or shortening the correct jumpers on the mobo? To my knowledge, this should for sure erase the CMOS configuration data, but are we sure that the same happens for the firmware?
And another question: could the BIOS write-protect password / MBR protect (that old “anti virus protection” in old BIOS) stop threats like Mebromi?
P.S.: great article, keep going on such interesting topics. I’m citing you in my researches.
Ciao,
Marco
Removing the battery doesn’t flash the BIOS back to the original ROM it had.
Just had friend who downloaded “JailBreak”. Broke his iPad and killed PC.
This M/C I got could not restore or get into. BUT StopZilla was on M/C as well as AVG.
SZ said it had infections but couldnt get rid of them.
Tried reinstall on CD and M/C came up with no HDD’s found.
Tried another earlier version CD and M/C came up with BSD.
Tried Linux distro works OK.
Partitioned HDD and format, installed Ubuntu OK and ran OK.
Tried going back to reinstall XP, starts loading then same thing BSD.
Then got DOS Floppy with new BIOS upgrade.
First deleted BIOS with jumpers !.
Then loaded DOS and new BIOS worked OK.
M/C booted up with new revision of BIOS.
Retried with Ubuntu OK.
Then tried to reinstall XP from different CD, no go BSD.
Checked all CD’s that I had used on M/C and found corrupted.
SZ found Trojan and back door hack “Open Pass” !.
This M/C is a Dell Precision 390 with an 8MB BIOS.
This is a lot of room to hide things in.
I believe the BIOS is corrupted and clearing NVRAM & reloading BIOS does not clear out original.
There needs to be a proper flushing of BIOS with Write all 1’s and 0’s and verify.
Rgds Gordon.
@Marco Giulani:
How did You extracted this rootkit’s code? Using some decompiler or disassembler (like IDA Pro) and guessing the code flow? Or maybe You found Mebroni’s source somewhere in internet?
Cheers
Basically after a low level format of the hard drive, after installing Windows XP, my computer gets bad root certain and my computer is secretly added to a domain. The hacker installs in group policy, ADSI Edit and SIDwalker Security Manager and turns my Atari CDROM drive on my laptop into SCSI
Then server operators are added to the universal plug and play device and the Smartcard service. Network configuration operators are added to DNS cache service as well as DHCP client service.
Then the install Full21install and DNS spoof me so instead of getting Microsoft updates I get a bunch if the hackers programming tools like C++ etc.
I have been fighting this on all my computers since March and it almost has killed me. Once they gain access they log key strokes to gain access to any router I buy by setting up a hidden VPN bridge to RAS async adapter or teredo or 6 to4 adapter. Then they have full access on my system.
They use RIS and NDIS to remote install Windows CE over top of XP’s shell by doing a remote unattended install with my Broadcom Xtreme Gigabyte NIC card.
They have infect my ACPI and then create a 7mb partition trout the ACPI or NVRAM in the BIOS. I am having big troubles trying to flash my bios as it says MAC address invalid The bios virus rewrites the windows install to add all kinds of goodies, Trojans, fixes my antivirus and adds BDA tuner to classes toot in the registry
I have fought this for 5 months and am at a loss and very stressed. Please help.
Yes, this is indeed the latest threat. Came across one recently and finally solved it;
At first i cleaned a customers laptop from virusses and spyware with all the usual progams (combofix, mbam, roguekiller, otl, KAV resue disk, msert, rootrepeal, gmer, aswmbr, tdsskiller, emsisoft kit, etc), but after 2 reboots the virus had infected autochk.exe again.
I finally got a bit desparate 🙂 and reinstalled Vista through the recovery partition (it’s an asus laptop K50IN series). Guess what, 2 reboots and Combofix reported that autochk.exe was infected again!!
The laptop is in a tightly secured LAN and hacks through a $ADMIN share can be excluded.
Now i got even more desparate :)) I ended up deleting all partitions on the disk and did a clean install with my official vista DVD. And again, 2 reboots later the laptop was infected again!
I then repeated this with a brand new harddisk and an install from an official DVD but still the virus came back.
So: Brand new harddisk, official Vista DVD, no usb sticks or whatever in the laptop and still after 2 reboots Combofix reported autochk.exe as infected.
At this point i was left with 2 possible causes; Either Combofix reported a virus incorrectly or the machine was infected through bios. Now i highly trust Combofix and on the other hand a bios virus has last been seen by me back in 1999 (tsjernobyl virus).
So i took out the infected disk, downloaded the latest bios on a clean PC and saved it on a new usb stick. Booted the infected laptop and went into the bios (with F2 key), started the Easy Flash utily from there and flashed the bios. I attached the infected disk as a usb disk to a clean computer and removed all partitions. Next i placed the empty disk into the laptop and reinstalled Vista from DVD.
The laptop has been fully installed now (all updates and software needed) and i’ve again scanned it with all programs mentioned before. And now it’s finally clean and it stays clean, no matter how many reboots 🙂
My conclusion is that the laptop was indeed infected with a bios virus, in a very very sophisticated way.
Just wanted to share this with you 🙂 cause bios virusses are rare and undetectable themselves. if you want more info feel free to e-mail me.
Jaapm
You talk a lot about the new complex Rootkit. But how do you fix it? I have been fighting it since last March and exhausted close to 1000 hours with it.
I have tried reflashing the bios with the hard drive removed and then plugged the hard drive in once bitdefender is loaded with the latest update files. Some of my infected Bios’s will not flash as you can see it flashes in a second and then reboots. I can take an old Windows XP CD with SP1 and after a low level format install Windows. After the installation is complete I can see many new services etc to know that I am already hacked. If I buy a new laptop and try and flash a tainted bios on an ASUS dark knight router, the router actually hangs the new laptop and after the flash is finished, the new laptop is infected at the bios level. It doesn’t matter if it is a Linux based bios on a router or an Award motherboard bios, they keep getting me even if I change ISP’s. on a Windows 7 fresh install the infected Bios will install the hacker code into the 100mb boot partition Windows 7 creates when you first set up Windows. It is literally a nightmare as no matter what I do the end result is the hacker adds my computers to a hidden AD domain using Microsoft ADS and they add server operators to all my devices and they add a bunch of hidden VPN mini-ports to bind to my physical network card and then they have full access to my computer. They use a bunch of Microsoft scripting and Assembly as well as .NET, Smsbios, avoid, nvram, WMI, WBEM and them they go undetected with all anti-virus programs. They use sub-components if Tcp/ip like ISOTP as well as IPX and AppleTalk. They use the scheduled tasks in Windows after windows is finished installing to complete more of their tasks. If I try right after windows has finished installing to get Windows updates, I get 100 fake Windows update files with more hacker code. It is so bad after 30 years of computers I am about yo throw the towel in for good!!
Dear Brent,
Sorry for my late reply, i haven’t checked this website in a while and only recently received your e-mail.
What is to be imperative for a final solution is the fact that you need to flash the bios _without_ any harddisk attached to your machine. Also no other devices or network cable should be attached when you flash the bios; Only the usb stick with the new bios on it should be attached!! ON The Asus laptop i cleaned, i was able to flash the bios with the easyflash utility, which is inside the bios itself and accessed through the F2 key.
If this is not possible (either because the machine has no easyflash utility or the easyflash utility itself has been modified so it doesn’t do a full flash of the bios) it will NOT be possible to clean your machine. The only option left at this point would be to actually replace the bios chip; Hardware inside your PC or laptop, but i doubt if you could get a hold of this chip and then solder it onto your motherboard.
You also mention: If I buy a new laptop and try and flash a tainted bios on an ASUS dark knight router, the router actually hangs the new laptop and after the flash is finished, the new laptop is infected at the bios level.
Do NOT use an Asus router, it appears many Asus products are infected when they leave the factory already and attaching a laptop or PC to an Asus router already can infect your laptop or PC on bios level.
When flashing the bios on your laptop or PC, make sure you have NO devices attached, except for the usb stick that contains the new bios.
So when you flash the bios with the easyflash utility make sure no devices (No disk, no routers no network cable etc, are attached to your machine). If you suspect your network card to be infected, disable it before you flash the bios of your laptop.
Ok, assuming you’re able to flash the bios on your laptop now successfully, the next step is to clean your old harddisk. I did this by attaching the old hard disk as a usb device to a clean computer (so NOT your laptop 🙂 The hardware i used for this is a Digitus IDE/Sata Hard drive usb cable adapter(DA-70200). Do a low level format of this disk or remove all partitions and when you’re done boot that clean PC where you have attached your old disk to, with HIREN boot CD 15.1
On this CD is a program called Parted Magic 6.7 (Linux based rescue environment). Start this program, you should get a desktop with a few icons on it (File manager, System profiler, Keybord layout, Disk health, Monitor settings, Network manager and Partition Editor). If you do not get this desktop, choose Xorg in the menu you will get and this will show you the desktop i just mentioned).
Start Partition Editor and see if there are no partitions (if you removed them all or did a low-level format). In case you already created a new partion on your old hard disk which is now attached as a usb disk, make sure there is no small partion at the end of the disk (usually 1 or 2 MB in size). If there is such a small partition, resize the partition in front of it and add the size of the very small partition at the end to the normal partition. This will get rid of the small partition at the end of the disk.
If this all went well you’re laptop now has a clean bios flashed and your old hard disk has no partitions or at least no small hidden partitions at the end of your disk.
Do not attach any devices yet to your laptop (Also NO network cable!!), but you can put in the empty harddisk again and boot the laptop from a windows install DVD (i used a Vista install DVD). From here on it’s a normal clean windows install 🙂
A few more remarks;
* Do NOT install Java, this is the perfect vehicle for virusses to get around.
* Disable client for Microsoft networks on your network card.
* Disable file and printer sharing on your network card.
* Do not install Flash unless you _really_ need it (No one does _really_ need it btw 🙂
What i’m about to state now may seem a bit ridiculous but i’m still gonna throw it out here as it is what i see in real life;
The hacking atm is of an unprecedented level, it originates in Russia and many many institutions and companies are hacked.
(Banks, ISP’s here in the Netherlands, Microsoft Windows update, DNS servers etc. They all pay ‘ransom’ to stay up and running and the Russian hackers have set up banks to store the money they receive. I know many of you will laugh at this point and that’s probably the best thing to do as the internet would really have to change to get rid of this (New DNS structures, no more Java, no more scripting and no more flash etc. Also companies like Asus would have to start using a different bios and all this goes way to far to fix the problem overnight …
My suspision is that DNS servers are infected and through injection, websites are infected which in turn infect PC’s and laptops.
I hope you had fun reading this, you can do with it whatever you like and i hope it actually helps you solving your problem.
As for me, i still service my customers, but in many cases it comes down to a clean install now, without Java!!, rather then trying to clean the PC/laptop of virusses. If there is no Java on the freshly installed machine, the customer is 95% Secure.
As antivirus i install Microsoft security essentials. Running a full scan with this scanner is the best there is out there atm in my opinion.
Ok, good luck with fighting this, don’t spend another 1000 hours on it 🙂 but instead get another laptop (Not an ASUS ofc) that has a different bios than Asus products use.
Greetings
Jaapm
jaapmenist@versatel.nl
http://www.computerjaap.nl
Well it seems I’m a victim of similar or same attacks. Since I’m in the very early stages of figuring this out I don’t know for sure yet but the attack seems to be bios based. I posted here http://superuser.com/questions/555394/gateway-p-6860fx-bios-options-greyed-grayed-out about the attack looking for answers.
In that post I detail how my bios boot password was over rode and now I just have user access to the bios, flashing bios did not fix it even with all hard drives removed and I think I made the flashing cd from an uninfected machine.
The bios did upgrade but still almost all options are grayed/greyed out in bios so I can’t choose to go back to default bios. It’s a Gateway P-6860FX laptop with phoenix bios. I haven’t discovered a jumper on the motherboard (if you know if there is one and or where it’s at please post about it) yet and if I can’t wipe the bios and cmos (if you know a way to clean the bios please reply) then I’ll have to get a new laptop.
Any suggestions would be very welcomed.
Does anyone come on here? Email me I have similar virus that seems to have taken control of wife and any device connected. My whole family iPhones have been acting weird and mine was fully compromised. I have isolated scripts and programming code to share (in txt file) My kids are scared and I need to get rid of this. It is from Russia as well
Brian, I’m sorry to hear of how troubled you feel from the threat you’re encountering.
All Threat related concerns/inquiries need to be dealt with by our Advanced Malware Removal Team directly:
Support Number: 1-866-612-4227 M-F 7am−6pm MT
Send us a Support Ticket: https://detail.webrootanywhere.com/servicewelcome.asp
Warm Regards,
Josh P.
Social Media Coordinator
After 33 years in computers and my home network was attacked at the BIOS level on my computers and my routers and spending over a 1000 hours trying to solve it, I got to a point where I could buy a brand new laptop, shut off the wireless network card and not plug the cat5 LAN cable in, after 10 minutes, the laptop was hacked at the BIOS level. I did not plug in any USB keys or external hard drives and I was still hacked. I finally figured out the hacker was using either radio or satellite waves to infect my computers.
After I found that out, I quit computers 100% abdvthst was 5.5 years ago.
Hackers ruined computers for home users. I certainly wouldn’t want to work in IT security in this day and age.
Marco,
one inquiry. Does the BIOS truly get reset to its unique state by simply expelling the battery or shortening the right jumpers on the mobo? As far as anyone is concerned, this ought to without a doubt delete the CMOS design information, however would we say we are certain that the same occurs for the firmware?
What’s more, another inquiry: could the BIOS compose ensure secret key/MBR secure (that old “hostile to infection assurance” in old BIOS) stop dangers like Mebromi?
P.S.: awesome article, continue going on such fascinating points. I’m refering to you in my explores.