
by Blog Staff | Feb 29, 2012 | Industry Intel, Threat Lab
In our continued series of how Android malware authors continue adding functionality to their work we take a look at GoManag. First seen last year, targeting Chinese speakers, GoManag is a Trojan that installs as a service so it can run in the background, collects device information and downloads payloads. Its odd name comes from part of a URL it attempts to contact to.
Malicious GoManag app running in the background as the name “Google Search (Enhanced)”
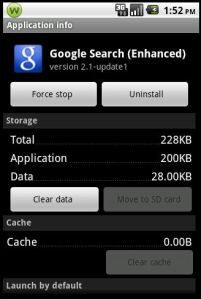
(more…)

by Blog Staff | Feb 29, 2012 | Industry Intel, Threat Lab
According to independent sources, the author of the most popular web malware exploitation kit currently dominating the threat landscape, has recently issued yet another update to the latest version of the kit v1.2.2.

More details:
(more…)

by Blog Staff | Feb 29, 2012 | Industry Intel, Threat Lab
Just like today’s modern economy, in the cybercrime ecosystem supply, too, meets demand on a regular basis.
With malware coding for hire propositions increasing thanks to the expanding pool of talented programmers looking for ways to enter the cybercrime ecosystem, it shouldn’t be surprising that cybercriminals are constantly releasing new malware loaders, cryptors, remote access trojans, or issuing updates to web malware exploitation kits on a periodic basis, using the outsourcing market model.
Continuing the “Peek inside…” series, in this post I’ll profile the Elite Malware Loader. In the wild since 2009, the malware loader is still under active development according to a recently spotted advertisement within the cybercrime ecosystem.
(more…)

by Blog Staff | Feb 27, 2012 | Industry Intel, Threat Lab
The vibrant cybercrime underground ecosystem offers countless ways to monetize the malware-infected hosts at the disposal of the malicious attacker.

From converting them to anonymization proxies assisting cybercriminals in covering their Web activities, to launching DDoS attacks, and using them to disseminate spam and more malicious threats, cybercriminals have a vast arsenal of monetization tactics in their arsenal.
In this post we’ll profile a recently advertised service offering thousands of Facebook “Likes”, Twitter followers, and YouTube views, all for the modest price of a couple of hundred rubles, entirely relying on malware-infected hosts for supporting their infrastructure.
(more…)

by Blog Staff | Feb 25, 2012 | Industry Intel, Threat Lab

Cybercriminals are currently spamvertising ‘Termination of your CPA license‘ emails, enticing users into clicking on a malicious link supposedly redirecting to the complaint.pdf file.
More details:
(more…)

by Blog Staff | Feb 25, 2012 | Industry Intel, Threat Lab
The ever-adapting cybercrime ecosystem is constantly producing new underground releases in the form of malware loaders, remote access trojans (RATs), malware cryptors, Web, IRC and P2P based command and control interfaces, all with the clear objective to undermine current security solutions.
Continuing the “A peek inside…” series, in this post I will profile a malware loader recently advertised within the cybercrime ecosystem , namely, the Ann Malware Loader.
(more…)

by Blog Staff | Feb 25, 2012 | Industry Intel, Threat Lab
Security researchers from StopMalvertising.com have intercepted a malvertising campaign using Yahoo’s ad network, that ultimately leads to a malicious payload in the form of fake security software known as scareware.
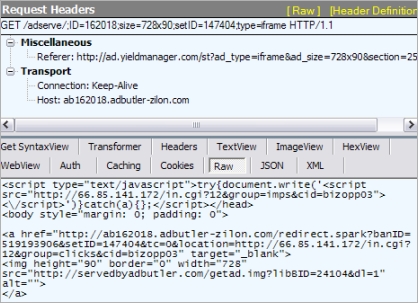
More details:
(more…)

by Blog Staff | Feb 23, 2012 | Industry Intel, Threat Lab
How is it possible that in an industry dominated by advanced performance metrics and benchmarking tests, cybercriminals still manage to release unique malware that remains undetected for weeks by major antivirus vendors?
It’s pretty simple. Cybercrime is innovating much faster than the security industry is.
It used to be that cybercriminals hacked from the fringe, often acting alone and for personal fame. Now, cybercrime is a profitable career. It’s among the top national defense issues; it’s leveraged as a form of political protest; and it’s a relatively easy field to break into.
You might be surprised to how easy it is for anyone to access black markets online, pay a small fee (or nothing at all), and gain access to malicious processes that wreak havoc on company websites, steal financial information, and much more. And their labors are producing countless malware samples each day.
Here’s an up-close look at some of the nasty tactics today’s hackers are using—and why security vendors can’t stop them with yesterday’s approach.
4 Ways Hackers are Winning
- Do-it-yourself (DIY) malware cryptors – Malware cryptors, as we cyber nerds call them, are designed to mask malware from being discovered by computer security programs. Cybercriminals can build malware cryptors on their own with relative ease. The idea is: once malware authors release their cryptors into the wild, they have the ability to keep changing it until their malware becomes unrecognizable to antivirus scans. That’s a big “one up” over traditional security.
- Managed malware crypting services – Think of malware as a key that is trying to find a door (someone’s device) to unlock. Instead of trying to make your own custom key, you could go to someone who already knows a specific key is going to work. That’s the idea behind malware crypting as a managed service. This process allows cybercriminals to obtain only the malicious executables (the things that make your computer go “boom”) that have the best chance of being effective—without having to build anything on their own.
- Server-side polymorphism (SSP) – Server-side polymorphism (say that two times fast!) is malware that is difficult to identify by a computer scan, no matter how many times you clean your system. What’s particularly important to highlight is how it renders traditional server antivirus software totally useless.
- Quality assurance processes within the cybercrime ecosystem – Cybercriminals aren’t sloppy about their work. Before a malware campaign is launched, cybercriminals will usually pre-scan their malicious executable against all popular antivirus engines in order to ensure that it will successfully bypass the signature-based malware scanning used by them. The process is highly automated and is often offered as a service at selected cybercrime-friendly online communities.
So what is the security industry’s big mistake?
Habit. Security companies have been relying solely on an outdated system, signature-based threat detection, for catching malware and other threats—a system that slows down people’s computers and doesn’t address today’s threat environment.
Signature-based threat detection works like this:
- A new virus or malware variant is discovered
- An antivirus vendor creates a new signature to protect against that specific piece of malware.
- The antivirus or malware signature is tested, and then pushed out to the vendor’s customers in the form of a signature update.
Year after year, the goal for antivirus companies has been to collect the most antivirus and malware signatures. This not only slows down your computer because it requires a large amount of space on your hard drive, but it also relies heavily on YOU to update your own
antivirus program, which increases the risk for infection.
This means that even on the day you purchase most security suites, they are outdated and ill-equipped to protect you against the newest malware. By the time updates are addressed, it’s often too late. In other words, we’ve been trying to bob for apples in a barrel when we should be dumping the barrel upside down.
Dumping the barrel upside down
The future of online security can and should be based on behavior-based blocking techniques, which analyzes files by looking at how they’re acting and what they’re attempting to do, rather than comparing them to a list of known threats. It’s our best option to get a leg up on hackers.
Not only does signature-based threat detection slow your computer down, it also opens a rather large window for new malware to reach your Internet-connected devices while you wait for critical updates. It’s time for the security industry to wake and smell the malware. We did. And that’s why we created Webroot® SecureAnywhere™—an award-winning new approach to behavior-based Internet security.
As a consumer of computer security products, it’s important to know why cybercriminals currently have the upper hand on a fair amount of cyber security companies. We created this article to help you stay informed. If you’d like to learn more about signature-based threat detection on antivirus technology, Wikipedia does a pretty nice job of explaining the subject (click here to go to the article).

by Blog Staff | Feb 17, 2012 | Threat Lab
We’ve all seen software grow. We watch as our favorite software adds on new features and becomes better at what it does. Malware writers are no different, they want their software to have more features as well as steal even more information. PJApps is a good example of this. PJApps is a Trojan that’s been around for a while causing havoc by being bundled in legitimate applications found in alternative Android markets, it is capable of opening a backdoor, stealing data and blocking sms behind the scenes. In one variant of PJApps it requests the following permissions to steal information:
INTERNET
RECEIVE_SMS
SEND_SMS
READ_HISTORY_BOOKMARKS
WRITE_HISTORY_BOOKMARKS
INSTALL_PACKAGES
WRITE_EXTERNAL_STORAGE
READ_PHONE_STATE
Here’s some of things the older variants of PJApps stole:
-SIM Card Number
-Telephone Number
-IMSI Number

(more…)

by Blog Staff | Feb 17, 2012 | Industry Intel, Threat Lab
Which is the most targeted mobile operating system?
According to the recently released 2011 Mobile Threats Report from our partners at Juniper Networks, that’s the Android OS.
Key summary points from the report:
(more…)

by Blog Staff | Feb 17, 2012 | Industry Intel, Threat Lab
Cybercriminals are currently spamvertising a “You just received a e-card form somebody” themed malware campaign, impersonating Hallmark.
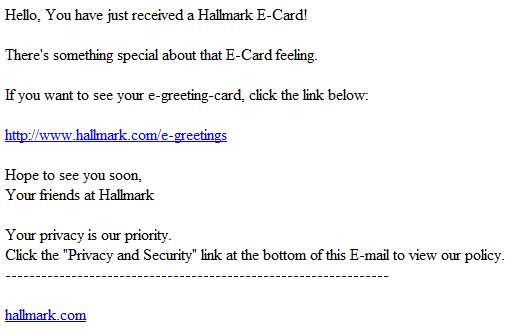
More details:
(more…)

by Blog Staff | Feb 15, 2012 | Industry Intel, Threat Lab
On Monday, Twitter announced that it’s introducing support for secure HTTPS connections to all users by default.

More details:
(more…)

















