Remember the underground service offering millions of harvested emails for sale profiled at the Webroot Threat Blog in January?
It appears that cybercriminals are continuing to innovate in this underground market segment by offering geolocated databases of millions of harvested emails for better targeting in their upcoming spam campaigns.
In this post, I’ll profile yet another cybercrime underground service selling millions of harvested emails to potential cybercriminals.
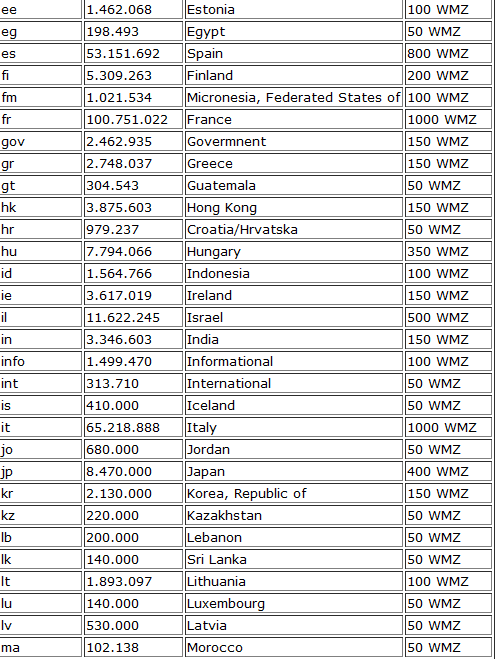
What’s particularly interesting about this service compared to the previous one profiled at the Webroot Threat Blog is that it offers segmented databases of harvested emails based on a particular country, or multiple gTLDs for better campaign targeting in upcoming spam campaigns, and targeted attacks.
Screenshots of the inventory of harvested emails currently offered for sale:
Next to mass marketing campaigns, the segmented databases could be used for launching targeted attacks against a particular country, which in combination with localization — translating the spam message into the native language of the prospective recipient — and event-based social engineering attacks, could increase the probability of successful interaction with the malicious emails.
In respect to targeted malware attacks, the service is currently offering 2.462.935 U.S government email addresses, and another 2.178.000 U.S military email addresses.
Cybercriminals often collect these through active data mining of malware-infected hosts, or through direct web crawling using commercial and private email harvesting tools.
U.S government and U.S military users whose emails have been exposed are advised to be extra vigilant for potential targeted malware attacks enticing them into downloading and executing a malicious attachment, or attempting to trick them into clicking on a client-side exploits serving link found in the emails.
You can find more about Dancho Danchev at his LinkedIn Profile. You can also follow him on Twitter.










Wow, this is 1st sale of its kind LOL..
this is one heck of a trick lol… cool running cyber crimilans!!