
by Blog Staff | Apr 23, 2012 | Industry Intel, Threat Lab
Dear blog readers, are you going to this year’s InfoSec 2012, event in London?
If so, don’t forget to stop by Webroot’s stand G90, where I’ll be briefing our visitors on “Current and Emerging Trends Within the Cybercrime Ecosystem” on the 24th of April to 26th of April.

More details:
(more…)

by Blog Staff | Apr 16, 2012 | Industry Intel, Threat Lab
In order for cybercriminals to launch, spam, phishing and targeted attacks, they would first have to obtain access to a “touch point”, in this case, your valid email address, IM screen name, or social networking account.
Throughout the years, they’ve been experimenting with multiple techniques to obtain usernames (YouTube user names, IM screen names, Hotmail email addresses) and valid email addresses from unsuspecting end and corporate users.
In this post we’ll profile a recently released Russian DIY email harvester, and emphasize on the difference between notice and experienced cybercriminals in the context of the tactics and techniques they use to obtain a potential victim’s email address.
More details:
(more…)

by Blog Staff | Apr 14, 2012 | Industry Intel, Threat Lab
Earlier this week, HP’s Software Security Response Team issued a security bulletin, alerting users that certain HP ProCurve 5400 zl switches were shipped with malware installed on the associated compact flash cards. No details were given about the type of malware shipped to unaware customers.

More details on the affected switches, including their serial numbers:
(more…)

by Blog Staff | Apr 13, 2012 | Threat Lab
On Tuesday, Adobe released a security bulletin, warning users of several vulnerabilities which could give a remote attacker access to the targeted PC.
The update affects Adobe Reader X (10.1.2) and earlier versions for Windows and Macintosh, Adobe Reader 9.4.6 and earlier 9.x versions for Linux, and Adobe Acrobat X (10.1.2).
More details:
(more…)

by Blog Staff | Apr 12, 2012 | Industry Intel, Threat Lab
On Tuesday, Microsoft issued 6 security bulletins, 4 of them critical, and 2 important updates. The bulletins fix a total of 11 vulnerabilities in Windows, Microsoft Office, and Internet Explorer.
According to Microsoft, the company has already observed targeted malware attacks taking advantage of the MS12-027 vulnerability. In order to mitigate the risks posed by these currently circulating targeted attacks, the company is advising users to disable the ActiveX controls via the Trust Center Settings > ActiveX Settings, option.
More details:
(more…)

by Blog Staff | Apr 6, 2012 | Threat Lab
 According to the latest prenotification security advisory from Adobe, next week, the company plans to issue a ‘security update’ for Adobe Reader X (10.1.2) running on Windows, Linux and Macintosh.
According to the latest prenotification security advisory from Adobe, next week, the company plans to issue a ‘security update’ for Adobe Reader X (10.1.2) running on Windows, Linux and Macintosh.
Adobe’s products are under permanent fire from malicious cybercriminals, exploiting known vulnerabilities in Adobe’s products, who succeed, primarily relying on the fact that end and corporate users are not patching in a timely manner.
More details:
(more…)

by Blog Staff | Apr 6, 2012 | Industry Intel, Threat Lab
 Yesterday, Google updated its Chrome browser to 18.0.1025.151 on Windows, Mac, Linux and Chrome Frame.
Yesterday, Google updated its Chrome browser to 18.0.1025.151 on Windows, Mac, Linux and Chrome Frame.
Next to patching multiple usability bugs, the latest update has also patched numerous vulnerabilities reported through Google’s security bugs bounty program.
More details:
(more…)

by Blog Staff | Apr 5, 2012 | Industry Intel, Threat Lab
Want to buy anonymous access to hacked PCs, spam-free SMTP servers (Simple Mail Transfer Protocol), or compromised bank accounts?
A newly launched underground Web service, is currently offering access to hundreds of hacked PCs, SMTP servers, and hacked bank accounts.
Let’s take a deeper look:
(more…)

by Blog Staff | Apr 3, 2012 | Industry Intel, Threat Lab
Cybercriminals are currently spamvertising yet another social-engineering driven malicious email campaign, this time impersonating U.S Airways.

Upon clicking on the malicious links found in the emails, end and corporate users are exposed to client-side exploits courtesy of the BlackHole web malware exploitation kit.
More details:
(more…)

by Blog Staff | Apr 2, 2012 | Industry Intel, Threat Lab
Remember the email hacking for hire service which Webroot extensively profiled in this post “Email hacking for hire going mainstream“?
Recently, I stumbled upon another such service, advertised at cybercrime-friendly web forums, offering potential customers the opportunity to hack a particular Mail.ru and Gmail.com email address, using a variety of techniques, such as brute-forcing, phishing, XSS vulnerabilities and social engineering.
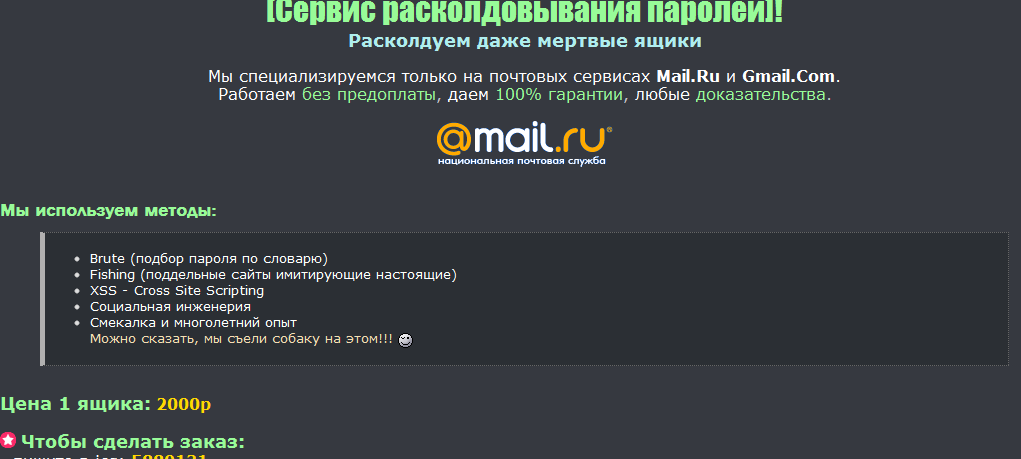
More details:
(more…)

by Blog Staff | Apr 2, 2012 | Threat Lab
Last week Adobe released the APSB12-17 Flash Player update. The update patches two critical security flaws — CVE-2012-0772 and CVE-2012-0773 — in the Adobe Flash player, and also, for the first time ever, introduces auto-patching mechanism. The update affects the following operating systems – Windows, Mac OS X, Linux and Solaris.

More details:
(more…)
















