The vibrant cybercrime ecosystem is populated by a diverse set of market players. From sellers, to buyers and vendors, sophisticated cybercriminals next to novice cybercriminals, everyone is persistently looking for ways to monetize their assets and increase their revenue.
Over the past two years, the industry witnessed the maturing business models in use by cybercriminals, and the rise of the so called cybercrime-as-a-service underground market propositions. Cybercriminals of all kinds have realized that managed services are the future that offer an efficient revenue generating platform for everyone to take advantage of.
In this post, I’ll profile a recently advertised boutique cybercrime-friendly E-shop, operated by what appears to be a novice cybercriminal looking for ways to monetize his fraudulently obtained assets.
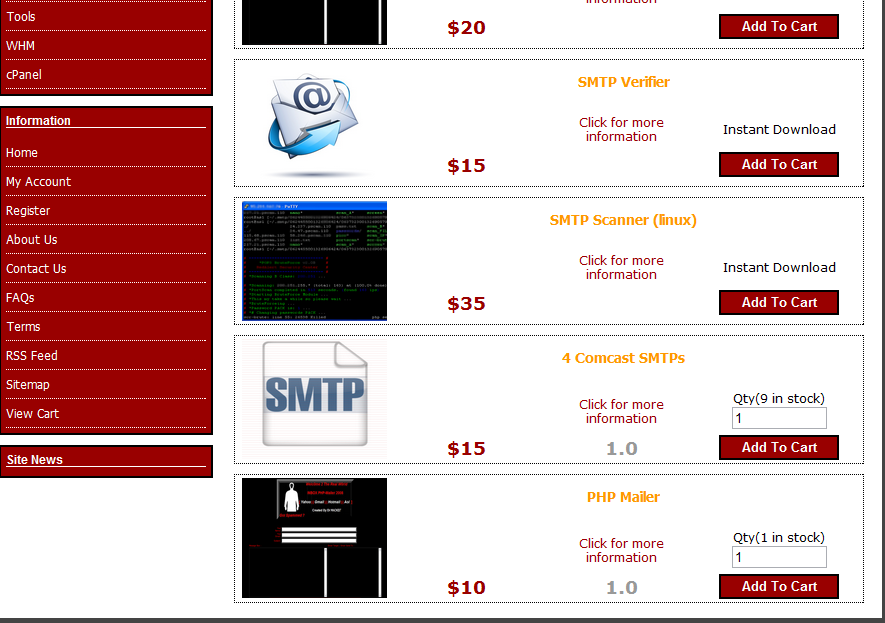
Screenshots of a DIY cybercrime-friendly E-shop:
His inventory of underground market goods and products includes:
- SMTP servers, SMTP Verifier, SMTP Scanner, access to RDP+AMS hosts, Leads, PHP Mailers, compromised cPanels, compromised Web Shells, compromised servers with Root access
The boutique cybercrime-friendly shop is a great example of how novice cybercriminals will not only attempt to monetize the fraudulently obtained underground goods, they will also attempt to monetize commodity goods that are freely available at the disposal of average cybercriminals.
Webroot will continue monitoring the shop’s latest propositions and future development.
You can find more about Dancho Danchev at his LinkedIn Profile. You can also follow him on Twitter.








So in short kids are paying real money for fake money on videogames they already own.How these people aren’t getting slapped with copyright lawsuits just proves the gamemakers are aware of the problem and just don’t care.
please verify my understanding of this warning. I receive emails from Hilton Hotels inviting me to shop at other retail stores. In outlood in order to see the entire offer I always get click here to see pictures (sometimes it says it may be a phishing sceem) With belonging to Hilton Honors I have been trusting them, should I not?