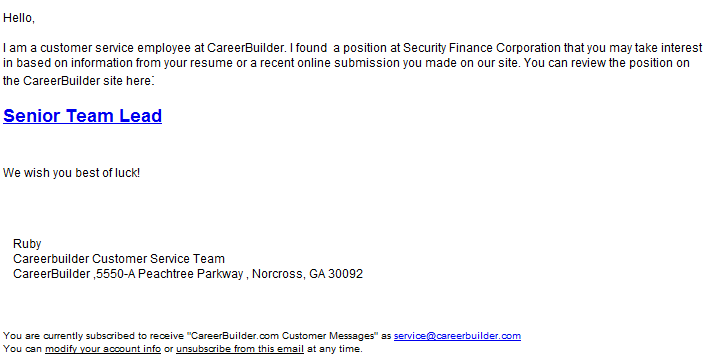
End and corporate users, and especially CareerBuilder users, beware!
Cybercriminals are currently spamvertising millions of emails impersonating the popular jobs portal CareerBuilder in an attempt to trick users into clicking on client-side exploits serving links.
The current campaign, originally circulating in the wild since 26 Apr, 2012, is a great example of a lack of QA (quality assurance) since they’re spamvertising a binary that’s largely detected by the security community.
More details:
Spamvertised URL: hxxp://karigar.in/car.html
Client-side exploits served: CVE-2010-0188 and CVE-2010-1885
Malicious client-side exploitation chain: hxxp://karigar.in/car.html -> hxxp://masterisland.net/main.php?page=975982764ed58ec3 -> hxxp://masterisland.net/data/ap2.php sometimes hxxp://strazdini.net/main.php?page=c6c26a0d2a755294 is also included in the redirection
Upon successful exploitation drops the following MD5: 518648694d3cb7000db916d930adeaaf
Upon execution it phones back to the following URLs/domains:
zorberzorberzu.ru/mev/in/ (146.185.218.122)
prakticalcex.ru – 91.201.4.142
nalezivmordu.in
internetsexcuritee4dummies.ru
Thanks to the overall availability of malware crypting on demand services, we believe that it’s only a matter of time before the cybercriminals behind this campaign realize that they’re spamvertising an already detected executable, crypt it and spamvertise it once again this time successfully slipping it through signatures-based antivirus scanning solutions.
Webroot SecureAnywhere customers are proactively protected from this threat.
You can find more about Dancho Danchev at his LinkedIn Profile. You can also follow him on Twitter.