Over the past few months, I’ve been witnessing an increase in underground market propositions advertised by what appears to be novice cybercriminals. The trend, largely driven by the increasing supply of cybercrime-as-a-service underground market propositions, results in an increasing number of newly launched cybercrime-friendly E-shops attempting to monetize fraudulently obtained accounting data.
In this post, I’ll profile yet another currently spamvertised cybercrime-friendly E-shop, offering access to accounts purchased using stolen credit cards as well as highlight the ways in which cybercriminals obtain the account info in the first place.
More details:
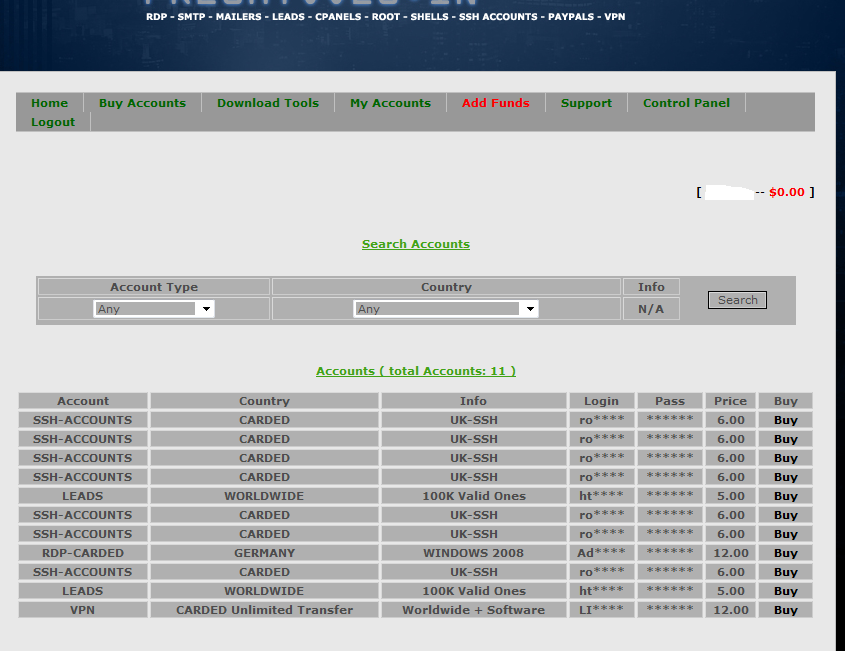
Screenshots of the boutique cybercrime-friendly E-shop:
Although the shop is pitching itself as a cybercrime-friendly shop for RDP, SMTP, Leads, CPanels, Root, Shells, SSH Accounts, PayPal accounts, VPN, it currently offers only carded SSH accounts, Leads and one carded VPN account. Using stolen credit cards, the cybercriminal behind the service is basically reselling access to these accounts. The price for a carded SSH account is $6, 100,000 international leads for possible spam and phishing campaigns go for $5, a carded RDP account based in Germany goes for $12, and a carded VPN account with unlimited transfer goes for $12.
Next to carding, how are the cybercriminal obtaining the stolen accounting data in the first place? There are several scenarios worth considering.
- Data mining botnets for accounting details – This is perhaps one of the most popular ways to supply such cybercrime-friendly E-shops with the goods necessary to make them work. Once a cybercriminal has access to a botnet, he could easily data mine it for accounting data by sniffing for accounting details and then resell them through boutique cybercrime-friendly E-shops like the one profiled in this post. The process is fairly easy to accomplish thanks to modules available in modern malware, allowing a smooth data mining process for any kind of accounting data.
- Reselling already purchased accounting data at a higher price – Informed buyers within the cybercrime ecosystem would be able to easily differentiate market propositions made by novice cybercriminals and sophisticated cybercriminals, ultimately leading to a market-sound purchase of a particular good or service. Misinformed buyers, however, don’t know how to take advantage of the underground market transparency, and therefore purchase goods and items without being aware of the actual market-driven price for the selected item. Novice cybercriminals naturally benefit from misinformed buyers, who are often unknowingly paying a premium price for a particular item, since they don’t have access to the competitor’s proposition. This is one of the many ways in which novice cybercriminals earn profits from misinformed buyers within the cybercrime ecosystem.
- Collecting accounting data through phishing campaigns – In cases where the novice cybercriminal doesn’t have access to a botnet, or doesn’t know where to purchase accounting data which he will later resell to prospective buyers, he turns to good old fashioned phishing campaingns in an attempt to collect valid accounting data from legitimate customers. Thanks to the overall availability of harvested email databases, managed spam services, and phishing site templates for the most popular brands in the financial sector, a novice cybercriminal can easily launch phishing campaigns in an attempt to build an inventory he will later start offering through his boutique cybercrime-friendly E-shop operation.
Webroot will continue monitoring the development of the boutique cybercrime-friendly operation.
You can find more about Dancho Danchev at his LinkedIn Profile. You can also follow him on Twitter.








I am seeing the same trends, it will be interesting to see where it all ends up.
A good reason to have a strong risk policy in place.