
by Blog Staff | Jun 7, 2012 | Industry Intel, Threat Lab
 In yesterday’s Firefox 13 release, Mozilla has fixed seven critical security vulnerabilities, four of which are critical. The majority of these vulnerabilities are also fixed in the latest Thunderbird 13 release.
In yesterday’s Firefox 13 release, Mozilla has fixed seven critical security vulnerabilities, four of which are critical. The majority of these vulnerabilities are also fixed in the latest Thunderbird 13 release.
More details on the vulnerabilities:
(more…)

by Blog Staff | Jun 7, 2012 | Industry Intel, Threat Lab
Think you received a package? Think again. Cybercriminals are currently spamvertising millions of emails impersonating UPS (United Parcel Service) in an attempt to trick users into downloading the viewing the malicious .html attachment.
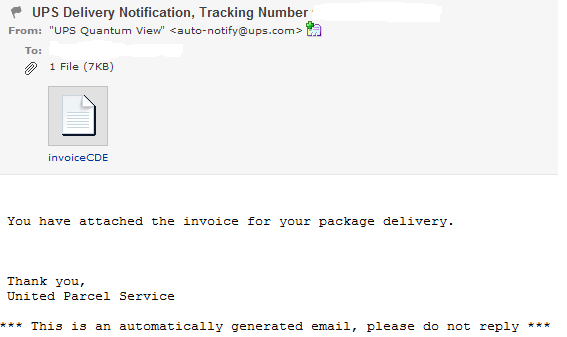
More details:
(more…)

by Blog Staff | Jun 6, 2012 | Industry Intel, Threat Lab
The Electronic Frontier Foundation (EFF) is reporting on a recently intercepted malicious documents distributed over Skype, apparently targeting Syrian activists.
Upon viewing the document, it drops additional files on the infected hosts, and opens a backdoor allowing the cyber spies behind the campaign access to the infected PC.
Webroot has obtained a copy of the malware and analyzed its malicious payload.
More details:
(more…)

by Blog Staff | Jun 6, 2012 | Industry Intel, Threat Lab
Thanks to the increasing availability of custom coded DDoS modules within popular malware and crimeware releases, opportunistic cybercriminals are easily developing managed DDoS for hire, also known as “rent a botnet” services, next to orchestrating largely under-reported DDoS extortion campaigns against financial institutions and online gambling web sites.
In this post, I’ll profile a managed DDoS for hire service, offering to “take down your competitor’s web sites offline in a cost-effective manner”.
More details:
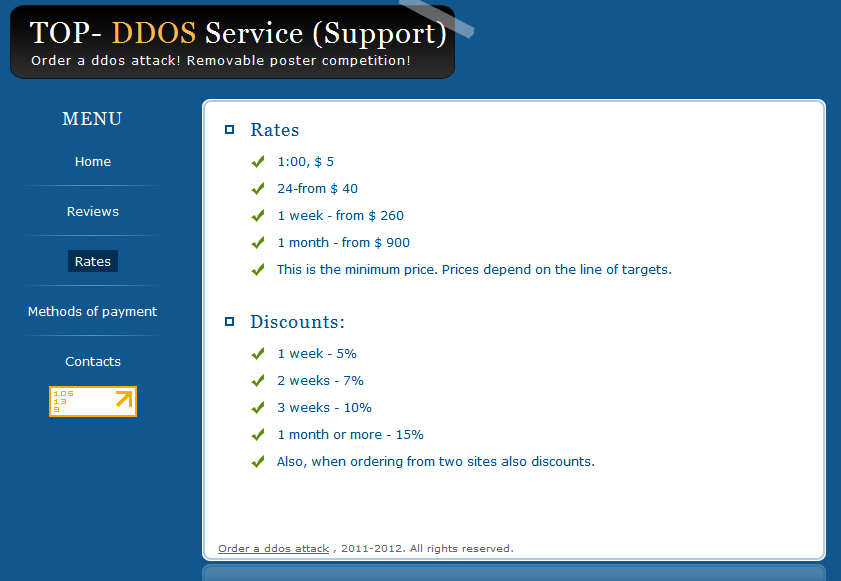
Screenshots of the DDoS for hire/Rent a botnet service:
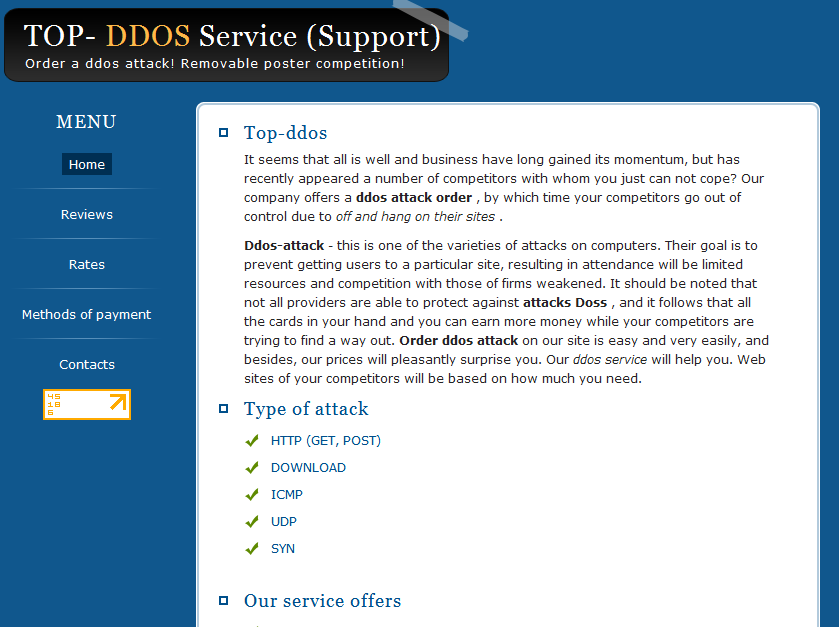

The paid DDoS service is currently offering HTTP (GET, POST), Download, ICMP, UDP, and SYN flooding features, using what they’re pitching as private tools operated by expert staff members. Before a potential customer is interested in purchasing a DDoS attack for hire, the service if offering a 15 minute test to the customer in order to prove its effectiveness.
How much do these DDoS for Hire services cost?
- The price for 1 hour or DDoS attack is $5
- The price for 24 hours of DDoS attack is $40
- The price for 1 week of persistent DDoS attack is $260
- The price for 1 month of persistent DDoS attack is $900
The service is also offering 5%, 7%, 10% and 15% discounts to prospective customers, with a return policy based on the remaining time from the originally purchased package.
The service profiled in this post, is the tip of the iceberg when it comes to the overall availability of DDoS for hire managed services within the cybercrime ecosystem. This fierce competition prompts for unique client acquisition tactics, such as offering complete anonymity throughout the purchasing and post-purchasing process in order to ensure that anyone can request any target, including high profile ones, to be attacked.
Moreover, although the service is undermining the OPSEC (operational security) of the proposition by advertising on public forums, the business model of the competition is often driven by invite-only sales, where prospective customers are trusted and verified as hardcore cybercriminals with a significant credibility within the cybercrime ecosystem. These competing services even offer the possibility to a target government or law enforcement web sites, despite the fact that their botnet’s activity will be easily spotted by security vendors and law enforcement agencies.
Instead of exposing their main botnets and potentially risking their exposure, the cybercriminals behind these campaigns have been developing the
“aggregate-and-forget” botnet model for years. These botnets that never make the news, are specifically aggregated for every customer’s campaign in order to prevent the security community from properly attributing the source for the attack, taking into consideration the historical malicious activity performed by an already monitored botnet.
Webroot will continue monitoring the development of the DDoS for hire service profiled in this post.
You can find more about Dancho Danchev at his LinkedIn Profile. You can also follow him on Twitter.

by Blog Staff | Jun 5, 2012 | Industry Intel, Threat Lab
Over the past few months, I’ve been witnessing an increase in underground market propositions advertised by what appears to be novice cybercriminals. The trend, largely driven by the increasing supply of cybercrime-as-a-service underground market propositions, results in an increasing number of newly launched cybercrime-friendly E-shops attempting to monetize fraudulently obtained accounting data.

In this post, I’ll profile yet another currently spamvertised cybercrime-friendly E-shop, offering access to accounts purchased using stolen credit cards as well as highlight the ways in which cybercriminals obtain the account info in the first place.
More details:
(more…)

by Blog Staff | Jun 4, 2012 | Industry Intel, Threat Lab
Next to commodity underground goods and services such as managed spam, harvested email databases, boutique cybercrime-friendly services, services offering access to hacked PCs, managed malware crypting on demand, and managed email hacking as a service, the cybercrime ecosystem is also a thriving marketplace for stolen intellectual property, such as music releases.
In this post I’ll profile a recently launched affiliate network for pirated music, offering up to 35% revenue sharing schemes with the cybercriminals that start reselling the stolen releases which undercut the official music marketplaces prices in an attempt to increase their profits.
More details:
(more…)

 In yesterday’s Firefox 13 release, Mozilla has fixed seven critical security vulnerabilities, four of which are critical. The majority of these vulnerabilities are also fixed in the latest Thunderbird 13 release.
In yesterday’s Firefox 13 release, Mozilla has fixed seven critical security vulnerabilities, four of which are critical. The majority of these vulnerabilities are also fixed in the latest Thunderbird 13 release.










