On daily basis, hundreds of thousands of legitimate accounts across multiple social networks get compromised, to be later on abused as a platform for launching related cyber attacks and social engineering attempts.
Recently, I came across a new Russian service offering access to compromised accounts across multiple social networks such as Vkontakte, Twitter, Facebook, LiveJournal, and last but not least, compromised email accounts. What’s particularly interesting about this service is the fact that it’s exclusively targeting Russian and Ukrainian users.
More details:
Screenshots of the service selling compromised accounts of social networking users:
Sample inventory of compromised accounts offered for sale by the service:
Sample prices for compromised Vkontakte.ru — Russia’s most popular social network — accounts:
As you can see in the attached screenshots, 50 Vkontakte.ru accounts go for 90 rubles ($2.75). According to details, 95% of the accounts belong to active Russian users. Next to Russia-based accounts, the service is also offering “verified over the phone” Vkontakte.ru accounts for Ukrainian users.
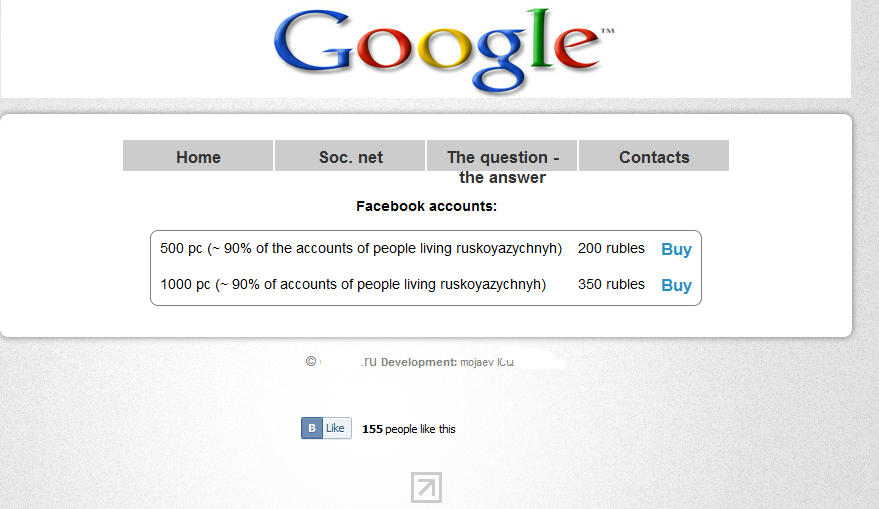
Sample prices for compromised Facebook accounts:
The price for 500 compromised Facebook accounts belonging to Russian users is 200 rubles ($6.11).
Sample prices for compromised Twitter accounts:
The prices for 500 compromised Twitter accounts belonging to Russian users is 250 rubles ($7.64).
Sample prices for compromised Russia-based email accounts:
Next to compromised social networking accounts, the service is also offering compromised email accounts for sale, targeting Mail.ru, Rambler.ru, Yandex.ru and qip.ru. According to the details, they managed to obtain access to these accounts through social engineering and brute-forcing. Not necessarily surprising given the fact that a huge percentage of Internet users continue using easy-to-guess passwords and easily recoverable Security Questions.
How is the service getting access to these compromised credentials in the first place? Next to social engineering attacks and brute-forcing, on a daily basis cybercriminals persistently data mine botnets for stolen email, social network, VPN, FTP and SSH accounting data in an attempt to further abuse it by launching additional attacks on the top of it.
What this service offers is an easy entry into the world of cybercrime for average cybercriminals looking for fresh platforms to further disseminate their social engineering campaigns attempting to trick users into interacting with their fraudulent scheme. Once a compromised accounts gets resold, the new owner will abuse the ‘chain of trust’ and attempt to serve malware and launch social engineering attacks such as, for instance, phishing knowing that users are more likely to trust a message or a Wall post from a trusted friend. That’s their way of achieving a positive ROI (return on investment) on their initial purchase.
Webroot will continue monitoring the development of this service.
You can find more about Dancho Danchev at his LinkedIn Profile. You can also follow him on Twitter.