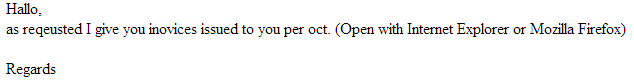Cybercriminals have recently launched yet another massive spam campaign attempting to trick users into clicking on malicious links or executing malicious attachments found in the spamvertised emails.
More details:
Sample screenshot of the spamvertised email:
Sample detection rate for the malicious attachment: MD5: 8b194d05c7e7f96a37b1840388231791 – detected by 39 out of 44 antivirus scanners as Trojan:Win32/Ransom
Sample client-side exploits serving URL: hxxp://forumibiza.ru:8080/forum/links/column.php
Although we couldn’t obtain the actual payload, the gathered intelligence indicates that this is a campaign launched by the same group that we’ve been monitoring for a few weeks now, allowing us to more effectively expose their campaigns and protect Internet users.
Malicious domain name reconnaissance:
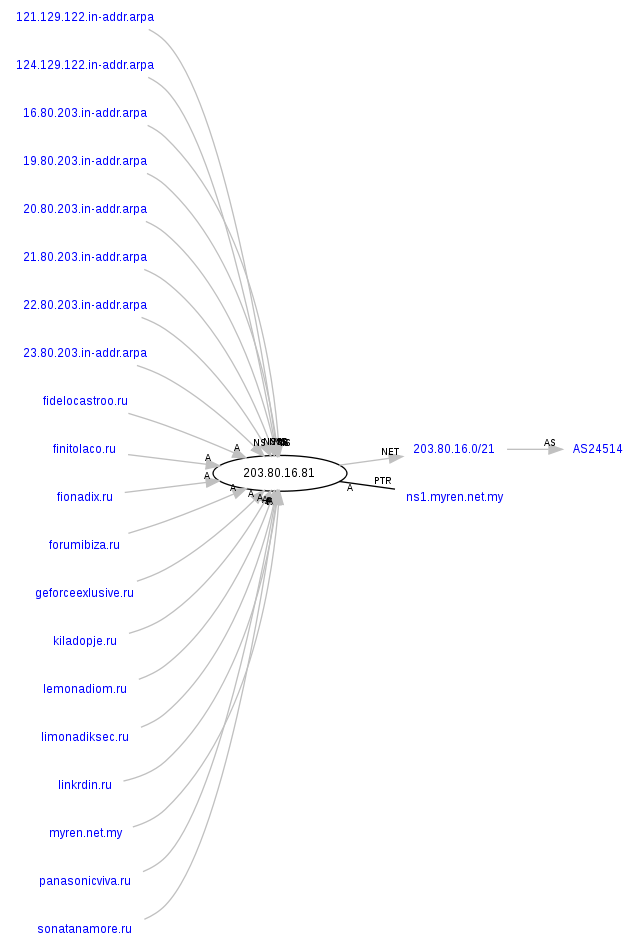
forumibiza.ru – 65.99.223.24, AS30496; 103.6.238.9, AS2.1125; 203.80.16.81, AS24514
Name server: ns1.forumibiza.ru – 62.76.186.190
Name server: ns2.forumibiza.ru – 84.22.100.108
Name server: ns3.forumibiza.ru – 50.22.102.132
Name server: ns4.forumibiza.ru – 213.251.171.30
The following malicious domains also respond to the same IPs (65.99.223.24; 103.6.238.9; 203.80.16.81). We’ve already seen these in several previously profiled malicious campaigns:
limonadiksec.ru – seen in – “‘Regarding your Friendster password’ themed emails lead to Black Hole exploit kit“; “‘Fwd: Scan from a Xerox W. Pro’ themed emails lead to Black Hole Exploit Kit“; “Bogus ‘Intuit Software Order Confirmations’ lead to Black Hole Exploit Kit“.
kiladopje.ru – seen in – “‘Fwd: Scan from a Xerox W. Pro’ themed emails lead to Black Hole Exploit Kit”
fionadix.ru – seen in – “‘Copies of Missing EPLI Policies’ themed emails lead to Black Hole Exploit Kit“; “Bogus ‘Intuit Software Order Confirmations’ lead to Black Hole Exploit Kit”
geforceexlusive.ru – seen in – “‘Fwd: Scan from a Xerox W. Pro’ themed emails lead to Black Hole Exploit Kit“; “‘Copies of Missing EPLI Policies’ themed emails lead to Black Hole Exploit Kit“; “Bogus ‘Intuit Software Order Confirmations’ lead to Black Hole Exploit Kit”
finitolaco.ru – seen in – “‘Fwd: Scan from a Xerox W. Pro’ themed emails lead to Black Hole Exploit Kit“; “Bogus ‘Intuit Software Order Confirmations’ lead to Black Hole Exploit Kit”
fidelocastroo.ru – seen in – “‘Fwd: Scan from a Xerox W. Pro’ themed emails lead to Black Hole Exploit Kit“; “Cybercriminals spamvertise bogus ‘Microsoft License Orders’ serve client-side exploits and malware”
lemonadiom.ru – seen in – “‘Fwd: Scan from a Xerox W. Pro’ themed emails lead to Black Hole Exploit Kit“; “‘Copies of Missing EPLI Policies’ themed emails lead to Black Hole Exploit Kit“; “Bogus ‘Intuit Software Order Confirmations’ lead to Black Hole Exploit Kit”
panasonicviva.ru – seen in – “‘Fwd: Scan from a Xerox W. Pro’ themed emails lead to Black Hole Exploit Kit”
sonatanamore.ru – seen in – “‘Regarding your Friendster password’ themed emails lead to Black Hole exploit kit“; “‘Fwd: Scan from a Xerox W. Pro’ themed emails lead to Black Hole Exploit Kit“; “Bogus ‘Intuit Software Order Confirmations’ lead to Black Hole Exploit Kit”
linkrdin.ru – seen in – “‘Fwd: Scan from a Xerox W. Pro’ themed emails lead to Black Hole Exploit Kit“; “‘Copies of Missing EPLI Policies’ themed emails lead to Black Hole Exploit Kit“; “Cybercriminals spamvertise bogus ‘Microsoft License Orders’ serve client-side exploits and malware“; “Bogus ‘Intuit Software Order Confirmations’ lead to Black Hole Exploit Kit”
donkihotik.ru – seen in – “Bogus ‘Intuit Software Order Confirmations’ lead to Black Hole Exploit Kit”
ponowseniks.ru – seen in – “‘Fwd: Scan from a Xerox W. Pro’ themed emails lead to Black Hole Exploit Kit”
panalkinew.ru – seen in – “‘Fwd: Scan from a Xerox W. Pro’ themed emails lead to Black Hole Exploit Kit”
rusa.skali.com.my
panacealeon.ru
dianadrau.ru
Name servers used in the campaign’s infrastructure:
ns1.limonadiksec.ru – 62.76.46.195
ns2.limonadiksec.ru – 87.120.41.155
ns3.limonadiksec.ru – 132.248.49.112
ns4.limonadiksec.ru – 91.194.122.8
ns5.limonadiksec.ru – 62.76.188.246
ns1.kiladopje.ru – 85.143.166.170
ns2.kiladopje.ru – 132.248.49.112
ns3.kiladopje.ru – 84.22.100.108
ns4.kiladopje.ru – 213.251.171.30
ns1.fionadix.ru – 62.76.186.190
ns2.fionadix.ru – 84.22.100.108
ns3.fionadix.ru – 50.22.102.132
ns4.fionadix.ru – 213.251.171.30
ns1.geforceexlusive.ru – 62.76.47.51
ns2.geforceexlusive.ru – 132.248.49.112
ns3.geforceexlusive.ru – 84.22.100.108
ns4.geforceexlusive.ru – 79.98.27.9
ns1.finitolaco.ru – 85.143.166.170
ns2.finitolaco.ru – 132.248.49.112
ns3.finitolaco.ru – 84.22.100.108
ns4.finitolaco.ru – 213.251.171.30
ns1.fidelocastroo.ru – 85.143.166.170
ns2.fidelocastroo.ru – 132.248.49.112
ns3.fidelocastroo.ru – 84.22.100.108
ns4.fidelocastroo.ru – 213.251.171.30
ns1.lemonadiom.ru – 85.143.166.170
ns2.lemonadiom.ru – 132.248.49.112
ns3.lemonadiom.ru – 84.22.100.108
ns4.lemonadiom.ru – 213.251.171.30
ns1.panasonicviva.ru – 132.248.49.112
ns2.panasonicviva.ru – 84.22.100.108
ns3.panasonicviva.ru – 62.76.47.51
ns1.sonatanamore.ru – 62.76.47.51
ns2.sonatanamore.ru – 132.248.49.112
ns3.sonatanamore.ru – 84.22.100.108
ns1.linkrdin.ru – 85.143.166.170
ns2.linkrdin.ru – 132.248.49.112
ns3.linkrdin.ru – 84.22.100.108
ns4.linkrdin.ru – 79.98.27.9
ns1.donkihotik.ru – 62.76.186.190
ns2.donkihotik.ru – 84.22.100.108
ns3.donkihotik.ru – 50.22.102.132
ns4.donkihotik.ru – 213.251.171.30
ns1.panacealeon.ru – 62.76.186.190
ns2.panacealeon.ru – 84.22.100.108
ns3.panacealeon.ru – 50.22.102.132
ns4.panacealeon.ru – 213.251.171.30
ns1.ponowseniks.ru – 85.143.166.170
ns2.ponowseniks.ru – 132.248.49.112
ns3.ponowseniks.ru – 84.22.100.108
ns4.ponowseniks.ru – 213.251.171.30
ns1.dianadrau.ru – 85.143.166.170
ns2.dianadrau.ru – 132.248.49.112
ns3.dianadrau.ru – 84.22.100.108
ns4.dianadrau.ru – 213.251.171.30
ns1.panalkinew.ru – 62.76.186.190
ns2.panalkinew.ru – 84.22.100.108
ns3.panalkinew.ru – 50.22.102.132
ns4.panalkinew.ru – 213.251.171.30
Webroot SecureAnywhere users are proactively protected from these threats.
You can find more about Dancho Danchev at his LinkedIn Profile. You can also follow him on Twitter.