Cybercriminals have recently launched a privacy-violating campaign spreading across Facebook in an attempt to trick Facebook’s users into installing a rogue Chrome extension. Once installed, it will have access to all the data on all web sites, as well as access to your tabs and browsing history.
More details:
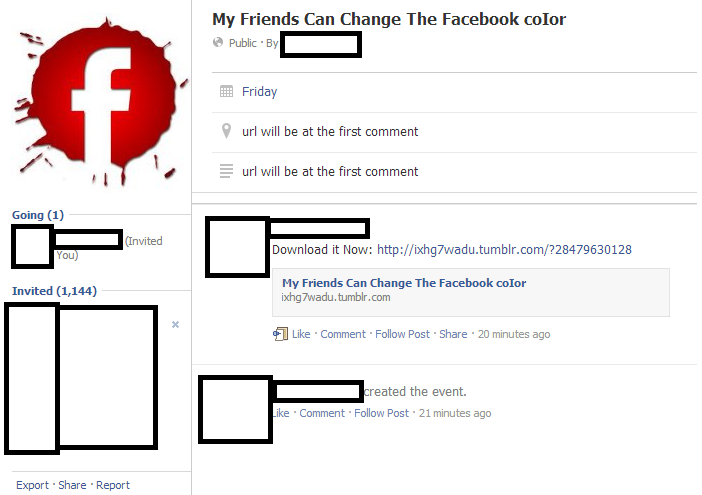
Sample screenshot of one of the few currently active Facebook Events promoting the rogue Chrome extension:
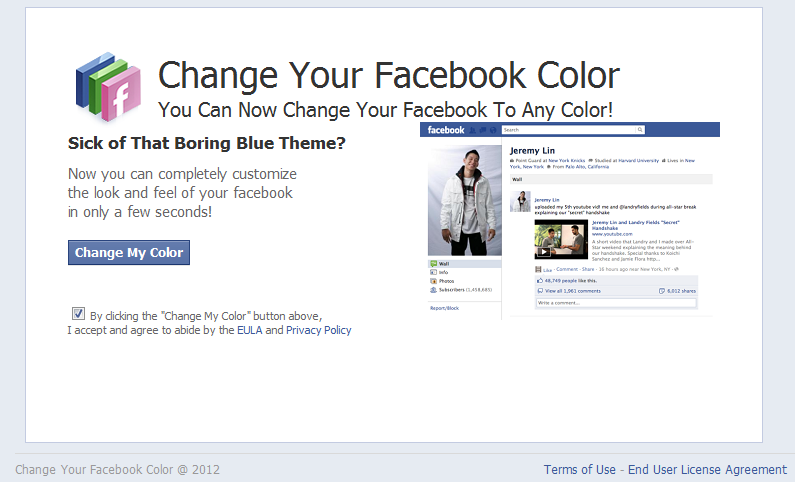
The campaign is relying on automatically registered Tumblr accounts, where the actual redirection takes place. Users are exposed to the following page, enticing them into changing their Facebook color theme:
Once users accept the EULA and Privacy Policy, they will become victims of the privacy-violating Chrome extension:
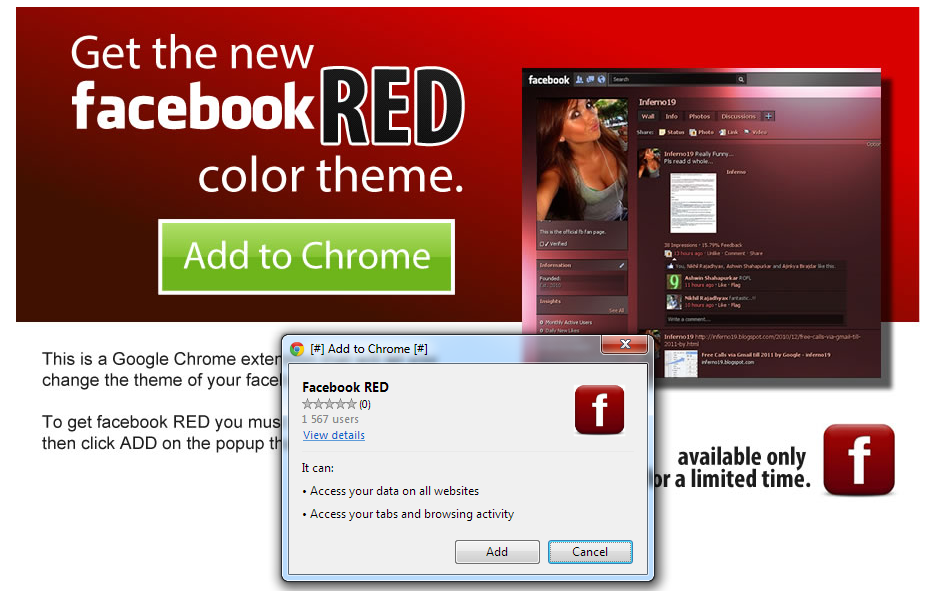
To further improve its legitimacy, and to play by Google’s newly introduced strategy to fight rogue Chrome extensions, the cybercriminals behind the campaign not only hosted it on Amazon’s cloud, they also featured it in Chrome’s Web Store:
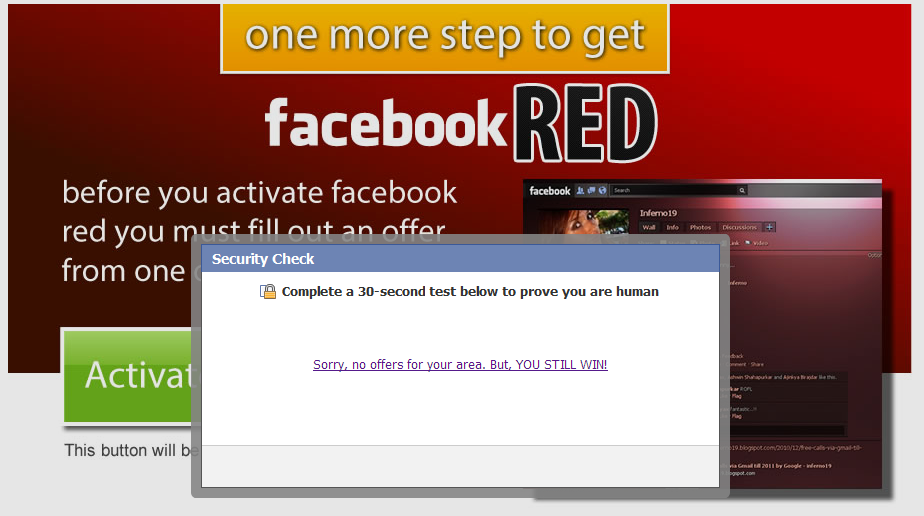
In case users choose not to accept the EULA and the Privacy Policy, the cybercriminals behind the campaign will once again attempt to monetize the hijacked Facebook traffic by asking them to participate in surveys, part of CPA (Cost-Per-Action) affiliate network, earning them money:
Sample Facebook Events spreading the bogus Tumblr URls:
hxxps://www.facebook.com/events/389748451108256/
hxxps://www.facebook.com/events/463366360367776/
hxxps://www.facebook.com/events/479634408745393/
hxxps://www.facebook.com/events/476440942398408/
Sample automatically registered Tumblr accounts participating in the campaign:
hxxp://ixhg7wadu.tumblr.com/?28479630128
hxxp://6upe014h7.tumblr.com/?3411365086213
hxxp://akecnjhpn.tumblr.com/?8892833241261
hxxp://zuodxt5yq.tumblr.com/?5593177247792
hxxp://xr8o8wc2t.tumblr.com/?1936588422396
Redirection takes place through the following IP:
hxxp://50.57.129.34/ping/redirect2.php (AS19994)
Amazon Cloud hosting URL:
hxxp://redf6.s3-website-us-east-1.amazonaws.com/last2.html
Google Chrome Web Store hosting URL:
https://chrome.google.com/webstore/detail/facebook-red/djicdajegmppedmnlgkhgjgejlgeblei
Users are advised to be extra cautious when accepting EULAs and Privacy Policies, in particular when installing browser extensions that have the capacity to access sensitive and personally identifiable data on their PCs.
You can find more about Dancho Danchev at his LinkedIn Profile. You can also follow him on Twitter.








its hacking my computer how to avoid it.
This is another example of “If it’s too good to be true, it probably is.” I saw the “Facebook Red” images come through on my feed, but because I already use a different skin for FB, I ignored it.