Over the past 24 hours, cybercriminals have launched yet another massive spam campaign, this time impersonating both eBay and PayPal, in an attempt to trick their users into clicking on the client-side exploits and malware serving links found in the malicious emails.
More details:
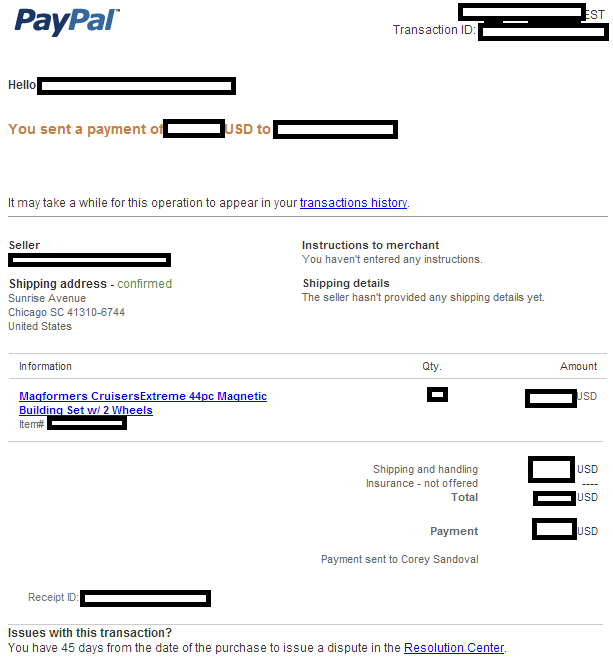
Sample screenshot of the spamvertised email:
Sample compromised URLs used in the campaign:
hxxp://idrapidleech.com/components/com_ag_google_analytics2/purhcoverview.html
hxxp://apartistanbul.com/components/com_ag_google_analytics2/purchaseinfo.html
hxxp://setpersianstyle.com/components/com_ag_google_analytics2/purchaseinfo.html
hxxp://lasienwater.com/components/com_ag_google_analytics2/purchaseinfo.html
hxxp://spadanastone.com/components/com_ag_google_analytics2/purchaseinfo.html
hxxp://adpalmaseca.com/components/com_ag_google_analytics2/purchaseinfo.html
hxxp://ustradework.com/components/com_ag_google_analytics2/purchaseinfo.html
hxxp://archerscluboffa.com/components/com_ag_google_analytics2/purchaseinfo.html
hxxp://odiwohng.com/components/com_ag_google_analytics2/purchaseinfo.html
hxxp://softouchsystem.com/components/com_ag_google_analytics2/purchaseinfo.html
hxxp://fairwaterconsultants.com/components/com_ag_google_analytics2/purchaseinfo.html
hxxp://popularesalhama.com/components/com_ag_google_analytics2/purchaseinfo.html
hxxp://adpalmaseca.com/components/com_ag_google_analytics2/purchaseinfo.html
Sample client-side exploits serving domains:
hxxp://litefragmented.pro/detects/telling-purchase-checks.php
hxxp://ibertomoralles.com/detects/slowly_apply.php
Malicious domain names reconnaissance:
litefragmented.pro – 59.64.144.239 – Email: kee_mckibben0869@macfreak.com
Name Server: NS1.CHELSEAFUN.NET
Name Server: NS2.CHELSEAFUN.NET
We’ve already seen and profiled the same email (kee_mckibben0869@macfreak.com) in the following analyses – “Cybercriminals spamvertise millions of FDIC ‘Your activity is discontinued’ themed emails, serve client-side exploits and malware“; “Cybercriminals resume spamvertising ‘Payroll Account Cancelled by Intuit’ themed emails, serve client-side exploits and malware“.
We’ve also seen the same name servers used in the following previously profiled malicious campaigns:
- ‘Your Discover Card Services Blockaded’ themed emails serve client-side exploits and malware
- ‘PayPal Account Modified’ themed emails lead to Black Hole Exploit Kit
- Cybercriminals resume spamvertising ‘Payroll Account Cancelled by Intuit’ themed emails, serve client-side exploits and malware
- Cybercriminals spamvertise millions of FDIC ‘Your activity is discontinued’ themed emails, serve client-side exploits and malware
- ‘Payroll Account Holded by Intuit’ themed emails lead to Black Hole Exploit Kit
ibertomoralles.com – 59.57.247.185 – Email: rick.baxter@costcontrolsoftware.com
Name Server: NS1.SOFTVIK.NET – 84.32.116.189 – Email: farbonite@hotmail.com
Name Server: NS2.SOFTVIK.NET – 15.209.33.133 – Email: farbonite@hotmail.com
Responding to 59.57.247.185 are also the following malicious domains:
roketlauncherskiy.org
moid.pl
securityday.pl
icobag.com
proscitomash.com
labpr.com
shopgreatvideonax.com
codemark.net
zindt.net
hfeitu.net
naky.net
svictrorymedia.ru
ygsecured.ru
winterskyserf.ru
romoviebabenki.ru
addon.su
robertokarlosskiy.su
We’ve already seen and profiled the same IP in the following malicious campaigns: “Fake ‘Citi Account Alert’ themed emails lead to Black Hole Exploit Kit“; “Spamvertised ‘Your Recent eBill from Verizon Wireless’ themed emails serve client-side exploits and malware“; “Fake BBB (Better Business Bureau) Notifications lead to Black Hole Exploit Kit“.
We’ll continue monitoring the activities of this cybercriminal/gang of cybercriminals and post updates as soon as new campaigns are launched.
Webroot SecureAnywhere users are proactively protected from these threats.
You can find more about Dancho Danchev at his LinkedIn Profile. You can also follow him on Twitter.