Cybercriminals are currently spamvertising two separate campaigns, impersonating Facebook Inc., in an attempt to trick its users into thinking that their Facebook account has been disabled. What these two campaigns have in common is the fact that the client-side exploits serving domains are both parked on the same IP. Once users click on any of the links found in the malicious emails, they’re exposed to the client-side exploits served by the Black Hole Exploit Kit.
More details:
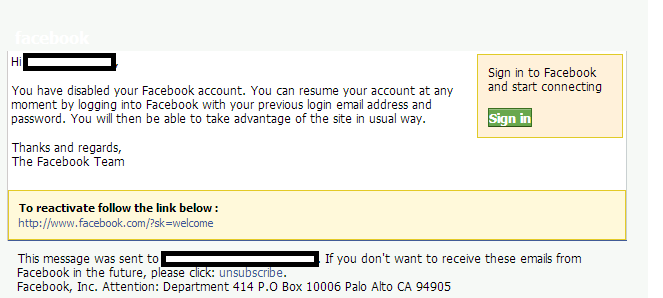
Sample screenshot of the spamvertised campaign:
Sample subjects used in the campaign:
“Someone has left a comment on your status update”
“Most recent events on Facebook”
Sample compromised sites used in the campaign:
hxxp://findlaterfinefoods.com/wp-content/plugins/akismet/fb_resume.html
hxxp://belpress.org/wp-content/plugins/akismet/fb_resume.html
hxxp://floworldonline.com/wp-content/plugins/akismet/fb_resume.html
hxxp://manfraca.com/wp-content/plugins/akismet/fb_resume.html
hxxp://kenko-info.com/wp-content/plugins/akismet/fb_resume.html
hxxp://elegantparkdresses.com/wp-content/plugins/fb_resume.html
hxxp://fiberglascu.com/wp-content/plugins/akismet/fb_resume.html
hxxp://handbags-plus.com/wp-content/plugins/akismet/fb_resume.html
Sample client-side exploits serving URLs:
hxxp://gonita.net/detects/sign_on_to_resume.php
hxxp://able-stock.net/detects/sign_on_to_resume.php
hxxp://capeinn.net/detects/win_units.php
Sample malicious payload dropping URLs:
hxxp://capeinn.net/detects/win_units.php?
ejg=2w:1n:1o:1i:1f&fov=35:3i:3g&pyvc=1m:1f:30:1i:1j:1l:2v:1h:1m:1k:1p:1p:1j:1k:32:2w:1k:1n:1k:1g:1m:1l&llshxtat=1m:1d:1g:1d:1f:1d:1f
hxxp://capeinn.net/detects/win_units.php?wjtp=1m:33:33:1i:1n&ssdxmx=2w:3e:31&dhmf=1m:1f:30:1i:1j:1l:2v:1h:1m:1k&bhs=1k:1d:1g:1d:1f:1d:1f
hxxp://capeinn.net/detects/win_units.php?nntlw=1l:2w:1n:2v:1i&cnwxw=39:31:2w&quc=1m:1f:30:1i:1j:1l:2v:1h:1m:1k&gqgb=1m:1d:1f:1d:1f:1d:1f
hxxp://capeinn.net/detects/win_units.php?sf=1i:1f:32:33:2v&fe=1m:1f:30:1i:1j:1l:2v:1h:1m:1k&s=1f&ma=q&wz=u
Malicious domain names reconnaissance:
gonita.net – 222.238.109.66 – Email: lockwr@rocketmail.com
able-stock.net – 222.238.109.66
capeinn.net – 222.238.109.66; 198.144.191.50 – Email: softonlines@yahoo.com
Name servers used in the campaign:
Name Server: NS1.HTTP-PAGE.NET
Name Server: NS2.HTTP-PAGE.NET
We’ve already seen the same name servers used in the following malicious campaigns:
- Fake ‘FedEx Online Billing – Invoice Prepared to be Paid’ themed emails lead to Black Hole Exploit Kit
- Fake LinkedIn ‘Invitation Notifications’ themed emails lead to client-side exploits and malware
- Bogus ‘Your Paypal Transaction Confirmation’ themed emails lead to Black Hole Exploit Kit
The following malicious domains are also using the same name servers:
ocean-movie.net – Email: lockwr@rocketmail.com
vespaboise.net – Email: blackchromedesign2@ymail.com
duriginal.net – Email: blackchromedesign2@ymail.com
shininghill.net – Email: fxfoto@hotmail.com
euronotedetector.net – Email: blackchromedesign2@ymail.com
Responding to 222.238.109.66 are the following malicious/fraudulent domains:
able-stock.net
africanbeat.net
alphabeticalwin.com
asistyapipressta.com
asmncm.net
asmncm.org
bestwesttest.com
blogfloeslive.com
blogfloeslive.net
briefingslegitimizes.biz
capeinn.net
cocolspottersqwery.com
ct-goods.com
discount-on-hotels.net
duriginal.net
ehadnedrlop.com
ensconcedattractively.biz
euronotedetector.net
lloydstsb-offshore.biz
lloydstsb-offshorem.org
lloytdsb-offshore.biz
masterseoprodnew.com
mesagemeans.com
morepowetradersta.com
paralertamastaercet.com
postofficenewsas.com
rebelldagsanet.com
seoseoonwe.com
splatwetts.com
terkamerenbos.net
uminteraktifcozumler.com
utl-premium.com
Responding to 198.144.191.50 are also the following malicious domains:
starsoftgroup.net
We’ve already seen and profiled the same domain used in the following malicious campaign:
Detection rate for the malicious PDF payload:
MD5: e415fbe2bad61491b4314618ae57e2c5 – detected by 25 out of 46 antivirus scanners as Exploit:Win32/Pdfjsc.AEW
MD5: 285b4186a435d80b503da88c922ea214 – detected by 26 out of 44 antivirus scanners as HEUR:Exploit.Script.Generic
MD5: 279bb4ab76ab18c2046c9288afac2e21 – detected by 26 out of 46 antivirus scanners as JS:Pdfka-gen [Expl]
Upon successful client-side exploitation, the campaign drops MD5: a2fe9b8154b28c8b7b7f898924276b8c – detected by 23 out of 46 antivirus scanners as Worm:Win32/Cridex.E.
Upon execution, the sample creates the following process on the affected hosts:
%AppData%kb00121600.exe
It then creates the following Mutexes:
LocalXMM000003F8
LocalXMRFB119394
LocalXMM000005E4
LocalXMM0000009C
LocalXMM000000C8
The following Registry Keys:
REGISTRYUSERS-1-5-21-299502267-926492609-1801674531-500SoftwareMicrosoftWindows NTS9CC20790
REGISTRYUSERS-1-5-21-299502267-926492609-1801674531-500SoftwareMicrosoftWindows NTCBA6D3F36
Once executed, the sample also phones back to the following C&C (command and control servers):
hxxp://88.119.156.20:8080/AJtw/UCyqrDAA/Ud+asDAA/
hxxp://173.201.177.77/J9/vp//EGa+AAAAAA/2MB9vCAAAA/
hxxp://85.94.66.2/J9/vp//EGa+AAAAAA/2MB9vCAAAA/
hxxp://203.114.112.156/asp/intro.php
We’ve already seen the same pseudo-randm C&C communication characters (EGa+AAAAAA), as well as the same C&C server (173.201.177.77) in the following previously profiled campaigns:
- ‘Your Kindle e-book Amazon receipt’ themed emails lead to Black Hole Exploit Kit
- ‘Batch Payment File Declined’ EFTPS themed emails lead to Black Hole Exploit Kit
- Fake ‘ADP Speedy Notifications’ lead to client-side exploits and malware
The following pseudo-random C&C communication characters (UCyqrDAA) have also been profiled in related analyses:
- ‘Your Discover Card Services Blockaded’ themed emails serve client-side exploits and malware
- Malicious ‘Sendspace File Delivery Notifications’ lead to Black Hole Exploit Kit
- Fake ‘Citi Account Alert’ themed emails lead to Black Hole Exploit Kit
- ‘Please confirm your U.S Airways online registration’ themed emails lead to Black Hole Exploit Kit
- Fake Intuit ‘Direct Deposit Service Informer’ themed emails lead to Black Hole Exploit Kit
- Multiple ‘Inter-company’ invoice themed campaigns serve malware and client-side exploits
If you catch a Facebook impersonating email in the wild, please forward it to phish@fb.com to notify Facebook of the attack.
Webroot SecureAnywhere users are proactively protected from this threat.
You can find more about Dancho Danchev at his LinkedIn Profile. You can also follow him on Twitter.







Reblogged this on consumerprivacyus.