Yesterday, a relatively unknown group of cybercriminals publicly announced the availability of a new Web malware exploitation kit. What’s so special about it is the fact that its current version is entirely based on Java exploits (CVE-2012-1723 and CVE-2013-0431), naturally, with “more exploits to be introduced any time soon”.
Let’s take a peek at the statistics and infection rates produced by this kit, as well as discuss its potential, or lack thereof, to cause widespread damage to endpoints internationally.
More details:
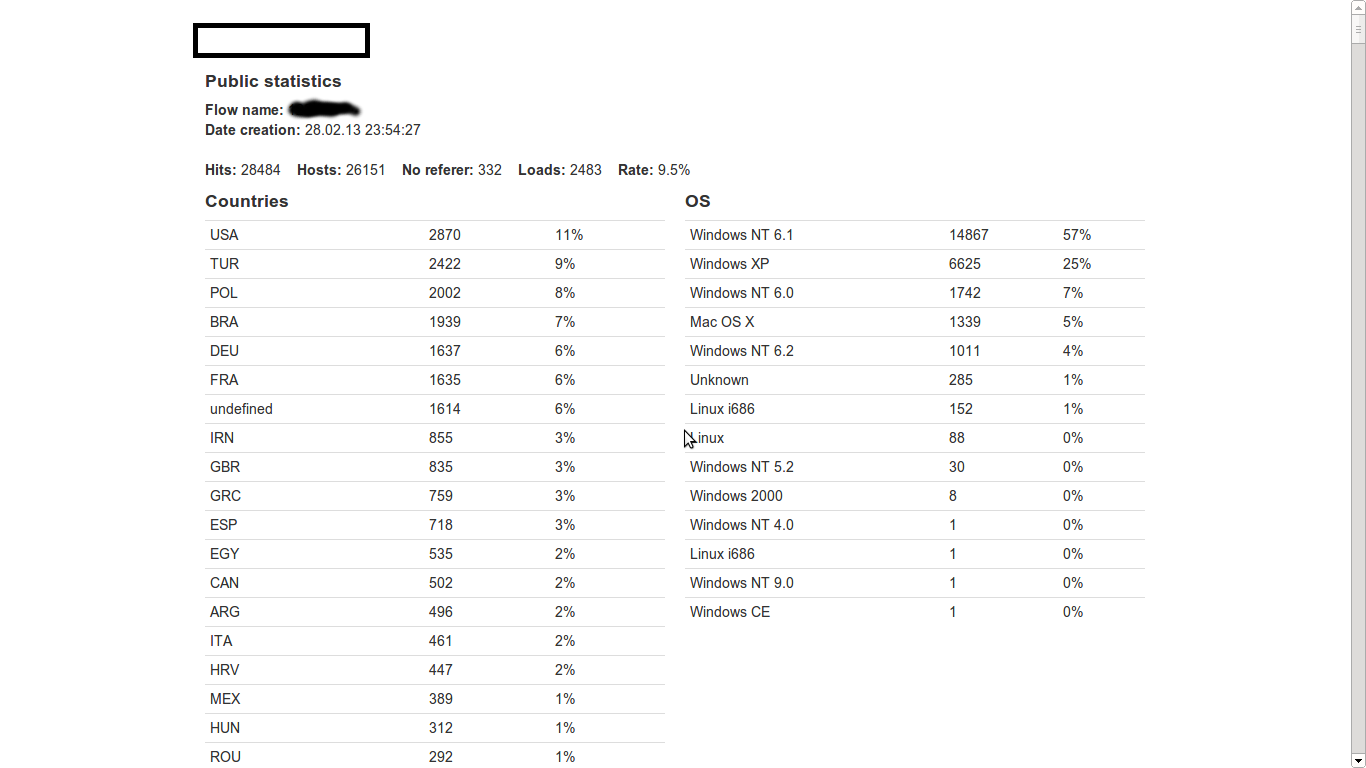
Sample screenshot of the statistics page of the newly released Web malware exploitation kit:
The majority of affected users are U.S.-based hosts, and the majority of infected operating systems are Windows NT 6.1, followed by Windows XP. As you can see, according to the cybercriminals pitching the kit, they’ve also managed to infect some Mac OS X hosts. The overall infection rate for the campaign was 9.5%, a pretty low one taking into consideration the fact that competing Web malware exploitation kits tend to exploit a much more diversified set of client-side vulnerabilities, consequently, achieving higher exploitation rates.
How is the kit differentiating itself from the competition? Is it “innovating”, or is it basically yet another “me too” exploitation kit?
For the time being, customers can choose whether they want to manually rotate the client-side exploits serving domains/IPs, or whether they’d want the cybercriminals selling the kit to do it for them as a managed service. Customers of the exploit kit will also receive notifications one their domains start getting detected by security vendors, through the Domain Check service. Naturally, the cybercriminals behind the exploit kit are outsourcing the entire process instead of building the capability in-house. Also, for the time being, the exploit kit can only be rented on bullet proof servers operated by the cybercriminals pitching it, but if customers want to use it on their own servers, they would have to personally request this from the vendor.
The price for renting the exploit kit? $40 for 24 hours, $150 for a week, $450 for a month.
Would this newly released exploit kit cause any widespread damage internationally? We doubt so, due to the fact that some of the most recent Java vulnerabilities received massive media coverage, prompting enterprises and end users to permanently disable it. Then again, this leads us to a dangerous myopia, where end and corporate users think that disabling Java prevents cybercriminals from establishing exploitation “touch points” with their endpoints. That’s not true, as competing Web malware exploitation kits cover a variety of (patched) client-side vulnerabilities.
In the wake of two recently announced Java zero day vulnerabilities, users are advised to disable Java, as well as to ensure that they’re not running any outdated versions of their third-party software and browser plugins.
You can find more about Dancho Danchev at his LinkedIn Profile. You can also follow him on Twitter.