By Dancho Danchev
A currently ongoing malicious email campaign is impersonating ADP in an attempt to trick its customers into thinking that they’ve received a ‘Package Delivery Notification.’ In reality though, once a user clicks on any of the links found in the malicious email, they’re automatically exposed to the client-side exploits served by the Black Hole Exploit Kit.
More details:
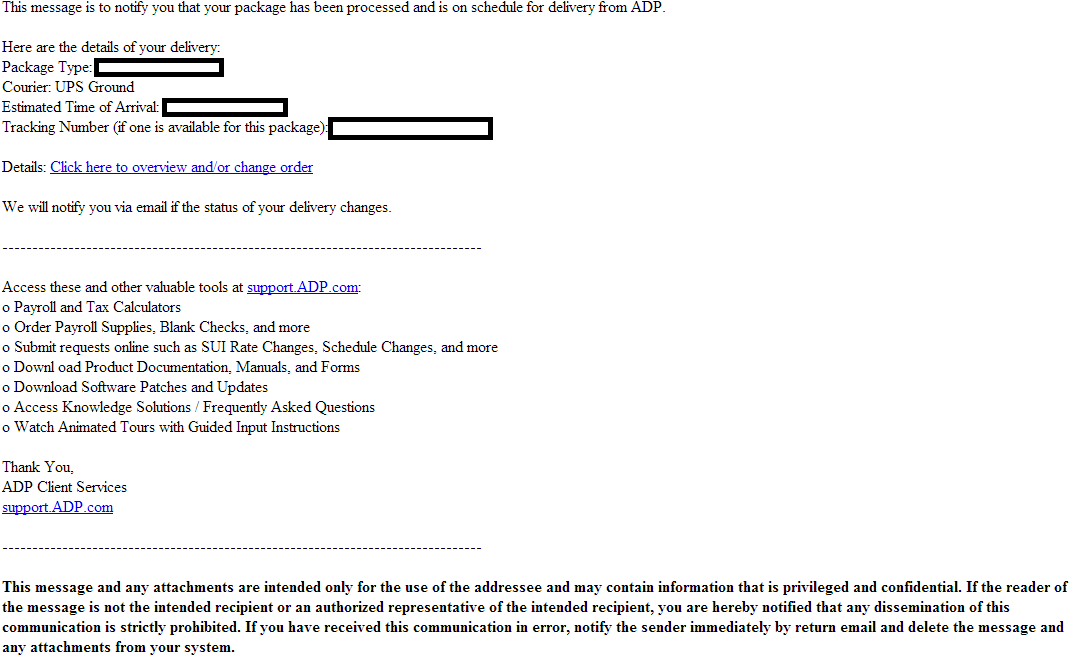
Sample screenshot of the spamvertised email:
Sample compromised URLs used in the campaign:
hxxp://hrampanino.ru/securadp.html
hxxp://gsmstyle.net/securadp.html
hxxp://hello06.com/securadp.html
hxxp://homou.org/securadp.html
hxxp://gwcrc.or.kr/securadp.html
hxxp://huabeipipe.com/securadp.html
hxxp://hohyunworld.com/securadp.html
Sample client-side exploits serving URL: hxxp://picturesofdeath.net/kill/long_fills.php – 24.111.157.113; 58.26.233.175; 155.239.247.247 – Email: boykintool@aol.com
Sample malicious payload dropping URL: hxxp://picturesofdeath.net/kill/long_fills.php?
rsm=1n:33:2v:1l:1h&pnp=37&tmivgdi=1g:1k:2v:1n:32:1o:1i:1i:32:31&fggthdar=1n:1d:1f:1d:1f:1d:1j:1k:1l
Upon successful client-side exploitation the campaign drops MD5: a372939c7134e95f39566dabaede4204 – detected by 5 out of 45 antivirus scanners as Trojan/Win32.Jorik.
Known to have responded to 24.111.157.113 are also the following client-side exploits serving URLs, part of related campaigns:
hxxp://buyersusaremote.net/kill/towards_crashed_turns.php – Email: calnroam@yahoo.com
hxxp://cyberage-poker.net/kill/loading_requested_profile.php
hxxp://teenlocal.net/kill/force-vision.php
Known to have responded to 24.111.157.113; 58.26.233.175; 155.239.247.247 are also the following malicious domains:
secureaction120.com – Email: markovochn@yandex.ru – the same email has already been profiled
secureaction150.com – Email: markovochn@yandex.ru
fenvid.com – 58.26.233.175; 155.239.247.247 – Email: carlini@fenvid.com
hotels-guru.net – Email: lendsnak@hotmail.com
openhouseexpert.net – 58.26.233.175; 155.239.247.247
gatovskiedelishki.ru – 77.241.198.65; 80.241.211.26; 83.255.90.5; 103.14.8.20; 190.30.219.85
advarcheskiedela.ru
porftechasgorupd.ru
sawlexmicroupdates.ru
arhangelpetrov.ru
Name servers part of the infrastructure of these campaigns:
Name Server: NS1.STREETCRY.NET – 93.186.171.133 – Email: webclipradio@aol.com – email has already been profiled
Name Server: NS2.STREETCRY.NET – 15.214.13.118
Name Server: ns1.ampesosac.net – Email: calnroam@yahoo.com
Name Server: ns1.miss-erika.net – Email: lemonwire@iname.com
Name Server: NS1.LETSGOFIT.NET – 94.76.243.95 – Email: weryrebel@live.com – email has already been profiled
Name Server: NS1.BLACKRAGNAROK.NET – 209.140.18.37 – Email: onetoo@gmx.com – email has already been profiled
Name Server: NS2.BLACKRAGNAROK.NET – 6.20.13.25
Name Server: NS1.LINGUAAPE.NET – 209.140.18.37 – Email: outfor23@live.com
Name Server: NS2.LINGUAAPE.NET – 173.1.12.57
Name Server: ns1.english-professional.net – 94.76.243.95
Name Server: ns2.english-professional.net – 1.185.151.43
Name Server: NS1.E-ELEVES.NET – 199.59.166.108
Name Server: NS2.E-ELEVES.NET – 199.59.166.108
Name Server: NS2.LETSGOFIT.NET – 11.3.51.158
Name Server: ns1.basicprinters.net
Name Server: ns1.torpedosgratiz.net
Once executed, the sample creates the following Registry Keys:
[HKEY_CURRENT_USERSoftwareMicrosoftWindows NTCFBDC89D4
[HKEY_CURRENT_USERSoftwareMicrosoftWindows NTS25BC2D7B
And the following Registry Values:
[HKEY_CURRENT_USERSoftwareMicrosoftWindowsCurrentVersionRun] -> KB00121600.exe = “”%AppData%KB00121600.exe””
As well as the following Mutexes:
LocalXMM000003F8
LocalXMI000003F8
LocalXMRFB119394
LocalXMM000005E4
LocalXMI000005E4
LocalXMM0000009C
LocalXMI0000009C
LocalXMM000000C8
LocalXMI000000C8
It then phones back to 212.68.63.82:8080/AJtw/UCyqrDAA/Ud+asDAA/
We’ve alrady seen the same pseudo-random C&C communication characters used in the following previously profiled campaigns, indicating that these campaigns are related:
- ‘Your Discover Card Services Blockaded’ themed emails serve client-side exploits and malware
- Malicious ‘Sendspace File Delivery Notifications’ lead to Black Hole Exploit Kit
- ‘Please confirm your U.S Airways online registration’ themed emails lead to Black Hole Exploit Kit
- Fake ‘Citi Account Alert’ themed emails lead to Black Hole Exploit Kit
- Fake ‘You’ve blocked/disabled your Facebook account’ themed emails serve client-side exploits and malware
- Fake Intuit ‘Direct Deposit Service Informer’ themed emails lead to Black Hole Exploit Kit
- Multiple ‘Inter-company’ invoice themed campaigns serve malware and client-side exploits
Webroot SecureAnywhere users are proactively protected from this threat.
You can find more about Dancho Danchev at his LinkedIn Profile. You can also follow him on Twitter.