By Dancho Danchev
On a daily basis we process multiple malicious campaigns that, in 95%+ of cases, rely on the market leading Black Hole Exploit Kit. The fact that this Web malware exploitation kit is the kit of choice for the majority of cybercriminals, speaks for its key differentiation factors/infection rate success compared to the competing exploit kits, like, for instance, the Sweet Orange exploit kit or the Nuclear Exploit pack v2.0.
In this post I’ll profile the EgyPack, a Web malware exploitation kit that was originally advertised on invite-only/vetted cybercrime friendly communities between the period of 2009-2011. List its core features, provide exclusive screenshots of its administration panel, and discuss why its business model failed to scale, leading to its virtually non-existent market share.
More details:
Cybercrime ecosystem advertisement of the EgyPack Web malware exploitation kit:
EgyPack is an advanced browser exploit pack that meet all the needs to perform a remote execution attacks via client side using internet browsers by using different Drive-by download exploits on the target operating systems. The main goal of EgyPack is to provide an efficient & easy control to the exploit system and lunch all the exploits in a silent & stealth way with the bypassing to all avs detections.
Main Core Coded in PHP ( OOP ) + Mysql
* Interactive Admin Panel Using Smarty Template Engine ( Can Develop More Than a Skin Later )
* Integrate with New Anti-Bots System ( Detect & Block All Bots, Scanners, Analyzers, Crawlers )
* Unique Filtration System for Traffic with No Duplicates
* Fully Undetected & Flawless JS Encryption for The All Added Exploits
* Payloads Working Smooth & Tested with All OS including Win Vista
* Stable Loader With Success 90% of execution on Loaded Traffic
WebPanel Features & Functions :
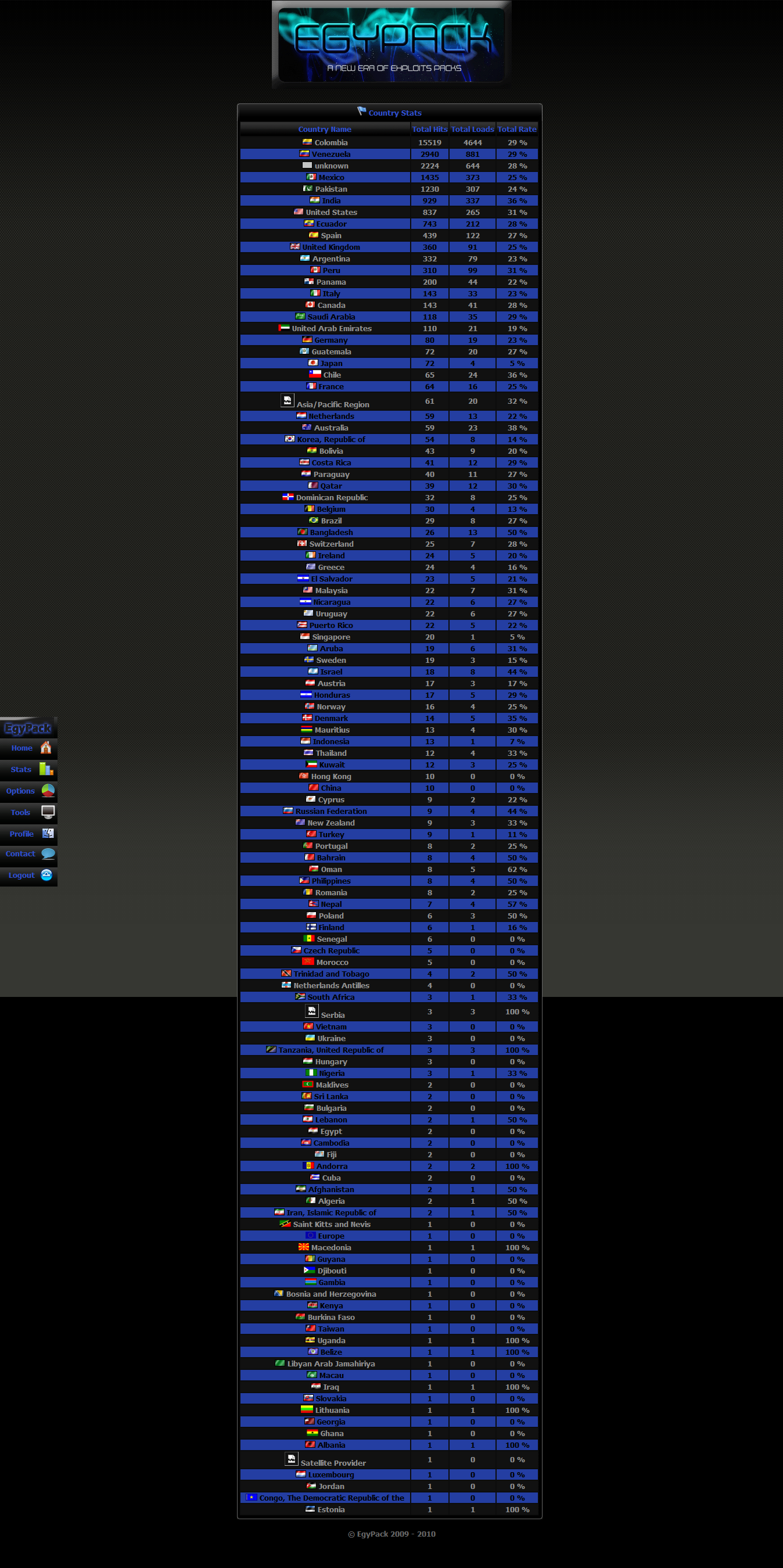
– Statistics :
» OS Statistics
» Browsers Statistics
» Countries Statistics
» Referers Statistics
– Options :
» Countries Rules ( Filter & Allow The Traffic for Exploit depends on Countries )
» Browser Rules ( Filter & Choose Browsers To Exploit On Traffic )
» OS Rules ( Filter & Choose Different Operating Systems to Exploit )
– Tools :
» Undetected & FUD Iframe Generator ( 2 methods of Encryption )
» Update Loader File ( Update From Local Source or Use Remote Server )
– User Control & Update :
» Update The Current User ( Change Admin Panel Password for The user )
» Add New Egypack Admin ( Add new Admin Account to the Admin Panel )
Exploits Added :
* MDAC
* DirectShow
* SpreetSheet
* MS09-002
* IEPeers
* PDF ( Libtiff – Util.printf – Collab.getIcon – Collab.collectEmailInfo – Newplayer )
* HCP ( MS10-042 including wmplayer + realpayer techniques )
* Java ( JSE & JNLP Webstart – Java Calendar – Java Desraialize )
Target & Supported Browsers :
* Internet Explorer ( MSIE 6 – MSIE 7 – MSIE 8 )
* Mozilla Firefox ( FF 1.X – FF 2.X – FF 3.X – FF 4.X )
* Opera Browser ( All Versions )
Target & Supported Operating System:
* Windows 7
* Microsoft Windows Vista
* Microsoft Windows XP
* Microsoft Windows 2003
* Microsoft Windows 98
* Microsoft Windows ME
* Microsoft Windows 95
Browser Conversion Rates From Tests :
* IE6 40%
* IE7 35%
* IE8 20%
* FF 20%
OS Conversion Rates From Tests :
* Windows Xp 27%
* Windows Vista 20%
* Windows 2000/2003 17%
Countries Conversion Rates From Tests:
* US / GB / CA from 25% – 30%
* Asian / Arab / Other Countries rates from 35% and up
* Mixed Traffics with Most of USA / GB varies from 20% ~ 25%
Unique & New Features on Egypack:
– Anti-Bots System that is using a different & new techniques to detect and block all Scanners & Analyzers from detecting EgyPack and get your domain flagged as attack & unsafe site on Firefox or MSIE.
– Tests for the Anti-Bots System proof the success of it’s work which made domains stayed for more than 3 weeks of continues of Iframing for big sites which makes more than 100k visits / day without any reports or block for domains or getting detections for the exploits from any avs .
-Unique Filtration System with No Duplicates for Traffic using techniques for checking for each unique visitor using cookies with mutex being updated when you clear the stats and checking for ip address .
The price? Between $1,000/1,500, with the idea to make it look like as if the core purpose of its existence is to be exclusively coded for members of this particular invite-only/vetted cybercrime-friendly community. Let’s take a peek inside the command and control interface.
Sample screenshot of the EgyPack Web malware exploitation kit’s administration panel:
Second screenshot of the EgyPack Web malware exploitation kit’s administration panel:
Third screenshot of the EgyPack Web malware exploitation kit’s administration panel:
Fourth screenshot of the EgyPack Web malware exploitation kit’s administration panel:
Fifth screenshot of the EgyPack Web malware exploitation kit’s administration panel:
Sixth screenshot of the EgyPack Web malware exploitation kit’s administration panel:
Seventh screenshot of the EgyPack Web malware exploitation kit’s administration panel:
Eight screenshot of the EgyPack Web malware exploitation kit’s administration panel:
Ninth screenshot of the EgyPack Web malware exploitation kit’s administration panel:
Tenth screenshot of the EgyPack Web malware exploitation kit’s administration panel:
The EgyPack is an example of an OPSEC-aware cybercriminal who has never sacrificed security for the sake of attracting new customers thru advertising his Web malware exploitation kit at publicly accessible cybercrime-friendly communities. Hence, the low market share, which may prove to be irrelevant in this specific case, as this is exactly what the cybercriminal behind it wanted to accomplish in the context of enriching the experience of the members of the invite-only/vetted cybercrime-friendly community.
As the exploit kit remains under development, we’ll continue monitoring the activities of the cybercriminal behind it, and post updates as soon as he introduces new features/exploits. Meanwhile, user are advised to ensure that they’re running the latest versions of their third-party software, and browser plugins in an attempt to mitigate a certain percentage of the risk posed by the fact that on a large-scale, cybercriminals tend to exploit known and already patched client-side vulnerabilities.
You can find more about Dancho Danchev at his LinkedIn Profile. You can also follow him on Twitter.