By Dancho Danchev
In an attempt to add an additional layer of legitimacy to their malicious software, cybercriminals sometimes simply reposition them as Remote Access Tools, also known as R.A.Ts. What they seem to be forgetting is that no legitimate Remote Access Tool would possess any spreading capabilities, plus, has the capacity to handle tens of thousands of hosts at the same time, or possesses built-in password stealing capabilities. Due to the nature of these programs, they have also become known as Remote Access (or Admin) Trojans.
Pitched by its author as a Remote Access Tool, the DIY (do it yourself) malware that I’ll profile in this post is currently cracked, and available for both novice, and experienced cybercriminals to take advantage of at selected cybercrime-friendly communities.
More details:
The first time we came across the underground market ad promoting the availability of the DIY malware was in June 2012 and offered for sale for $1,000. Then in October 2012, a cracked and fully working version of the DIY malware leaked on multiple cybercrime-friendly communities, potentially undermining the monetization attempted by its author.
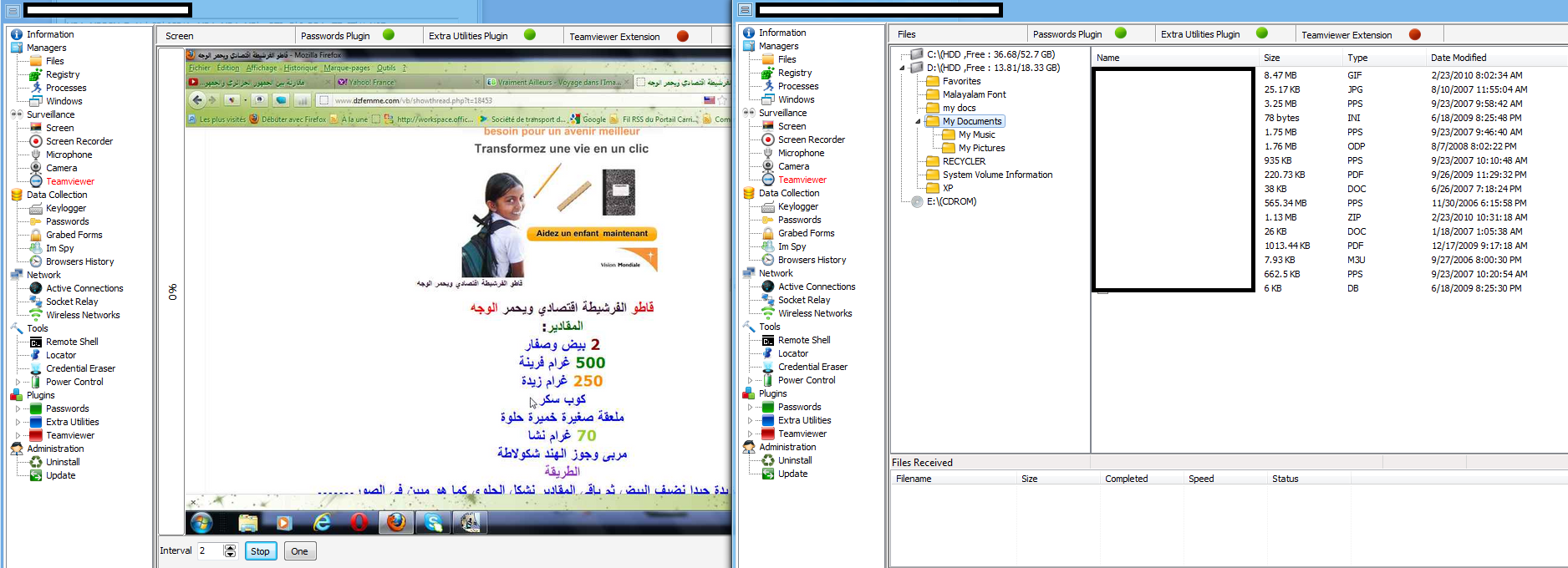
The Web/Client based release has numerous features, presented in a point-and-click fashion, potentially empowering novice cybercriminals with a versatile set of online spying capabilities. Let’s go through some screenshots to demonstrate the capabilities of this particular (cracked) underground market release.
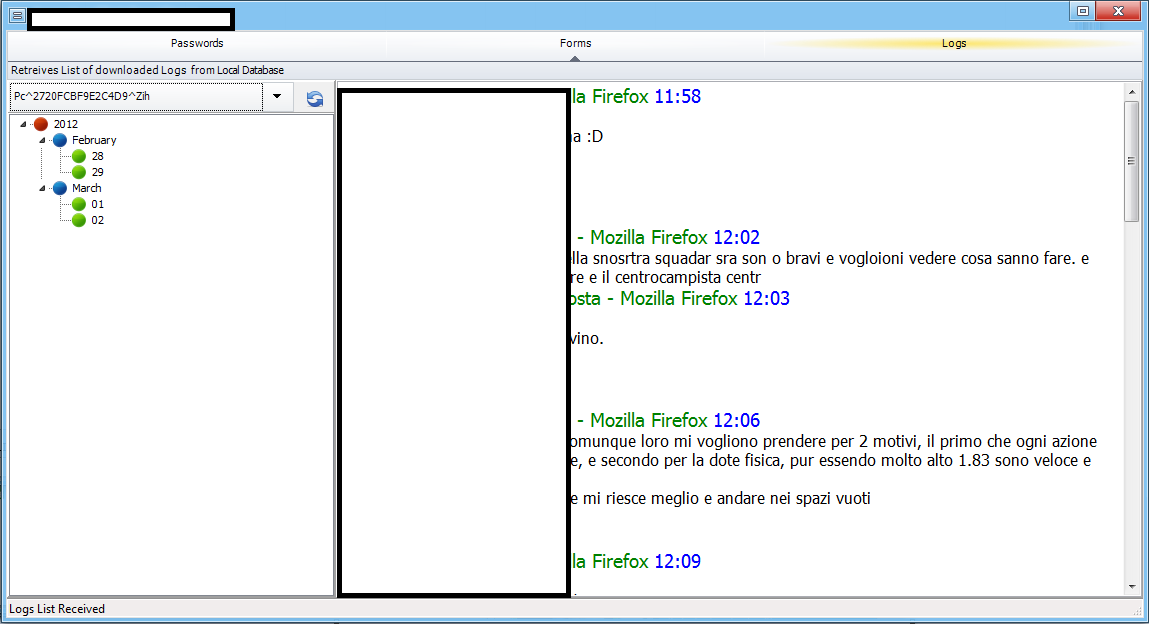
Sample screenshot of the DIY Web/Client based malware:
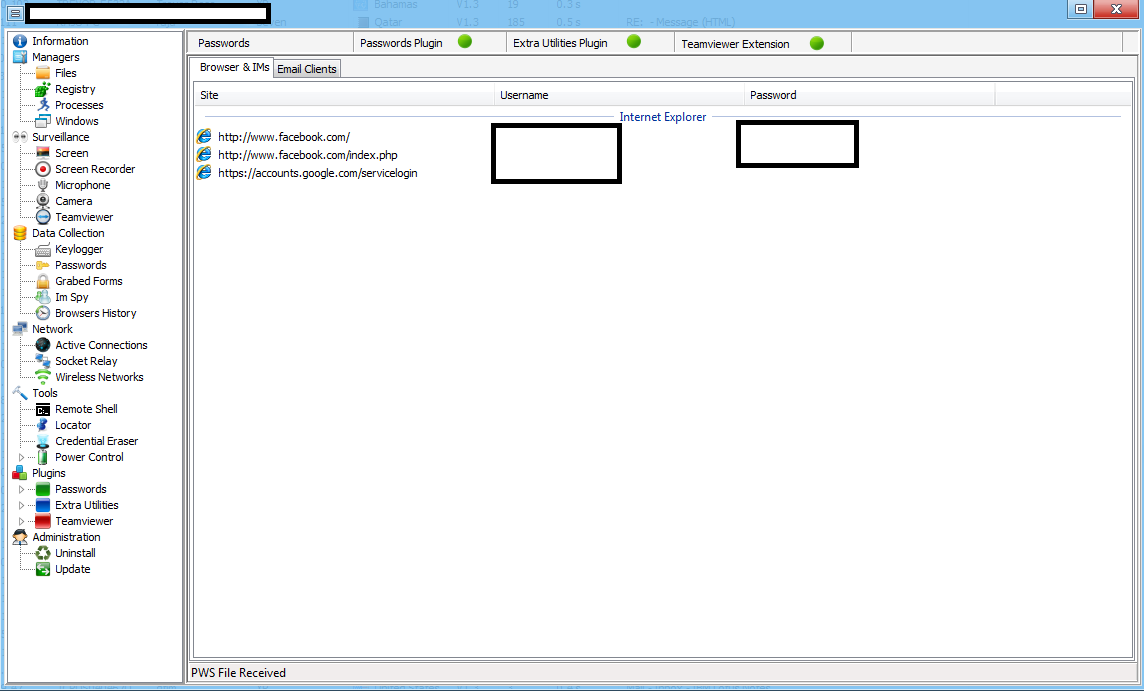
Sample screenshot of the DIY Web/Client based malware:
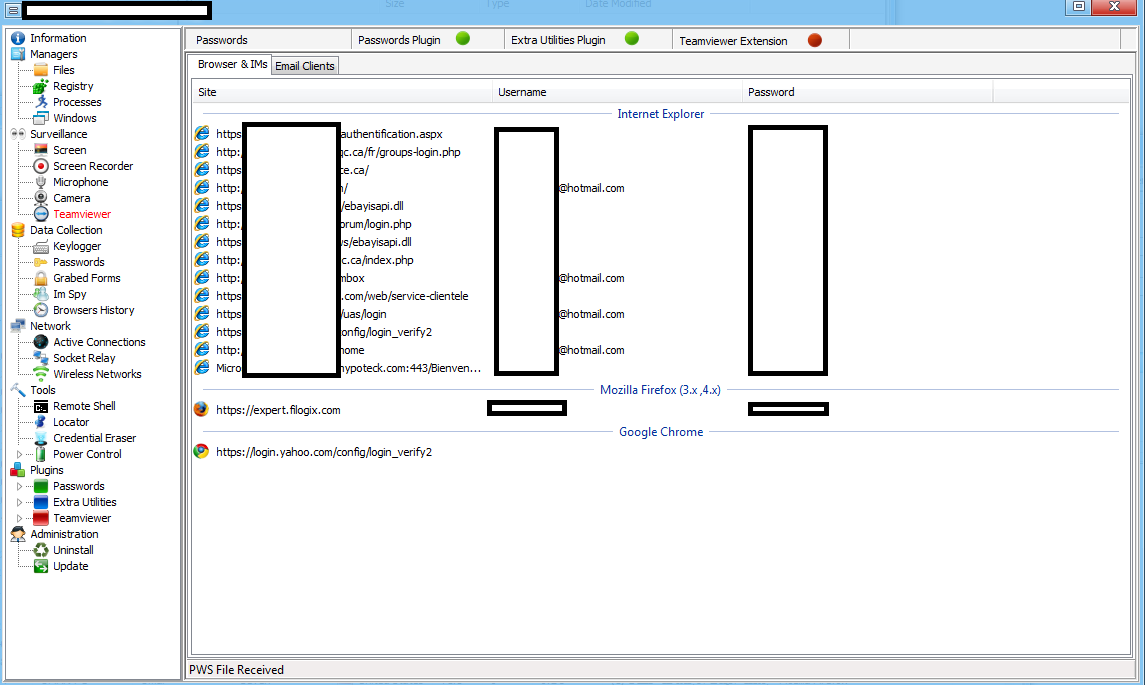
Sample screenshot of the DIY Web/Client based malware:
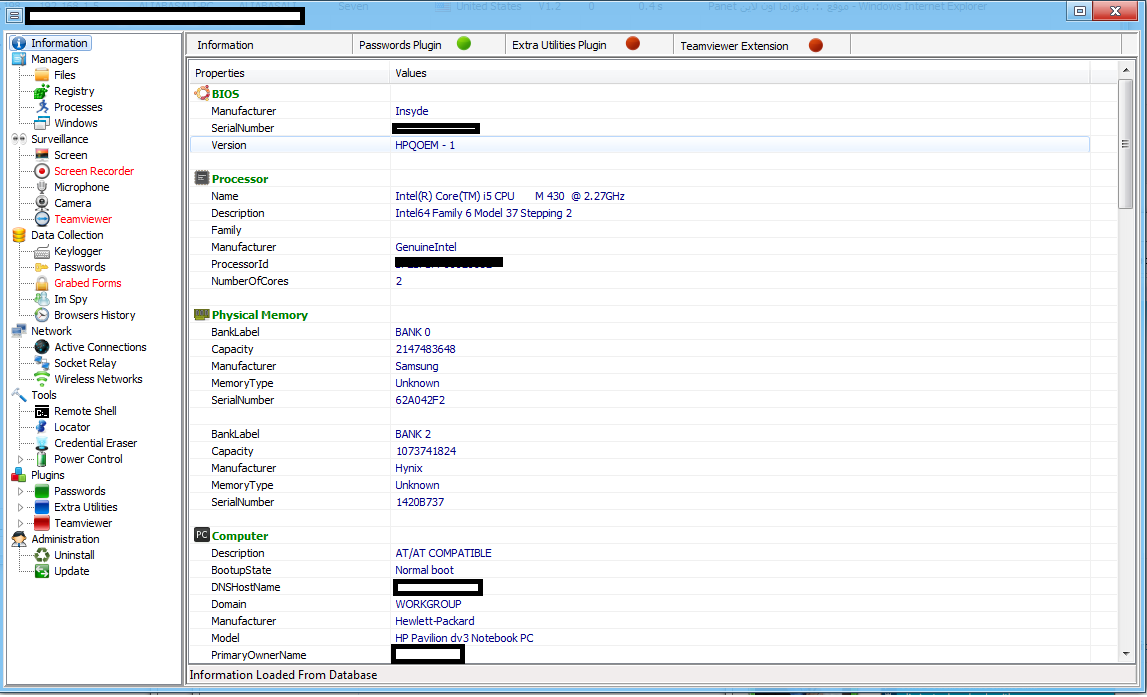
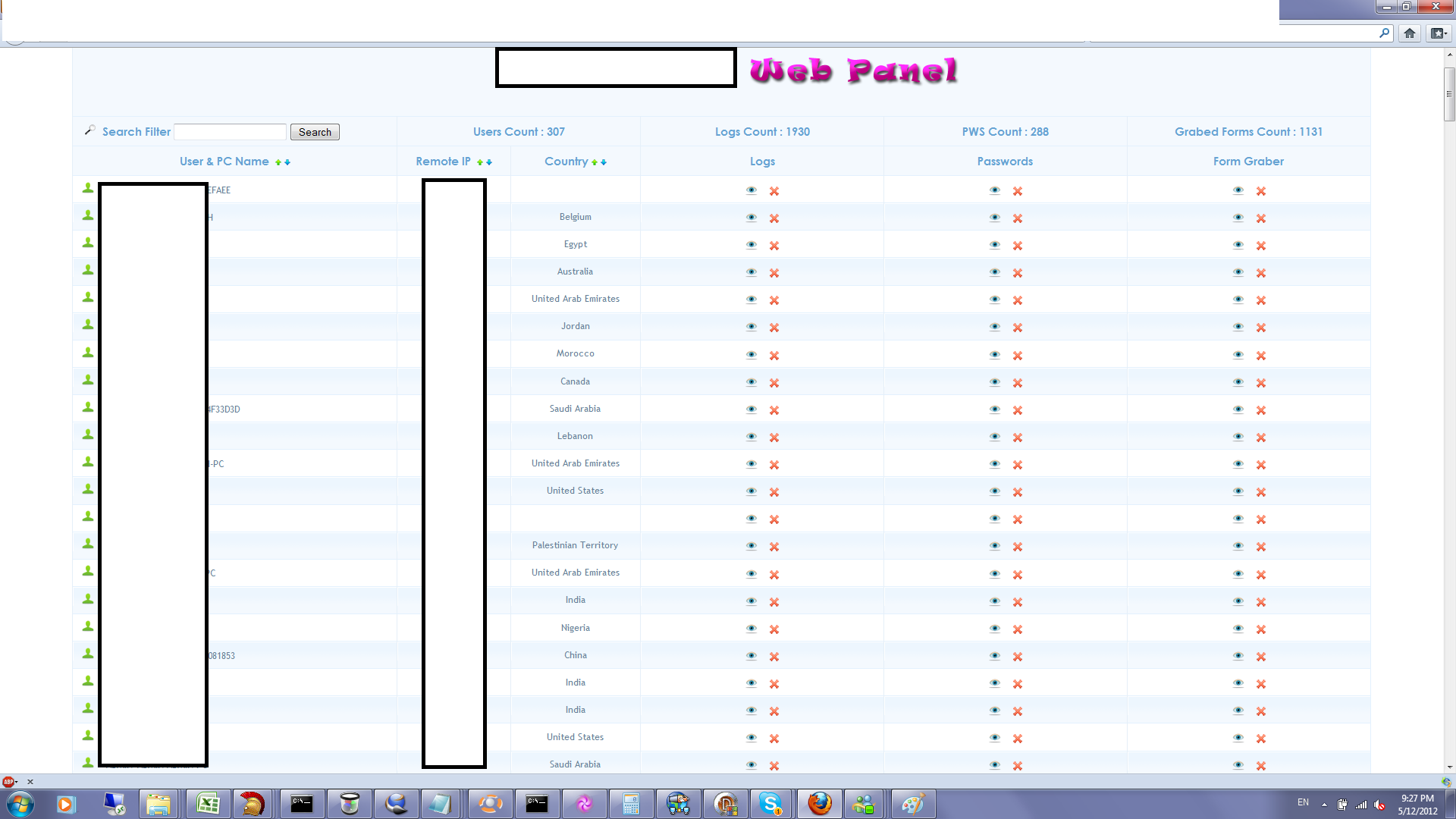
Sample screenshot of the DIY Web/Client based malware:
Sample screenshot of the DIY Web/Client based malware:
Sample screenshot of the DIY Web/Client based malware:
Sample screenshot of the DIY Web/Client based malware:
Sample screenshot of the DIY Web/Client based malware:
Sample screenshot of the DIY Web/Client based malware:
Sample screenshot of the DIY Web/Client based malware:
Sample screenshot of the DIY Web/Client based malware:
Sample screenshot of the DIY Web/Client based malware:
Sample screenshot of the DIY Web/Client based malware:
Sample screenshot of the DIY Web/Client based malware:
Sample screenshot of the DIY Web/Client based malware:
Sample screenshot of the DIY Web/Client based malware:
Sample screenshot of the DIY Web/Client based malware:
Sample screenshot of the DIY Web/Client based malware:
Sample screenshot of the DIY Web/Client based malware:
Sample screenshot of the DIY Web/Client based malware:
Sample screenshot of the DIY Web/Client based malware:
Cracked malware releases either cease to exist since the cybercriminal behind them has failed to monetize his release in the initial phrase, continue being developed as private releases, or become adopted by novice cybercriminals taking advantage of today’s managed malware crypting services to ensure that the actual payload remains undetected before it is distributed to the intended target(s).
We’ll continue monitoring the development of this RAT software/DIY malware, in particular, whether or not its developer will continue working on it, now that there are leaked versions of it available online.
You can find more about Dancho Danchev at his LinkedIn Profile. You can also follow him on Twitter.






















http://accountsforbrazzers.com/