Have you sent an eFax recently? Watch out for an ongoing malicious spam campaign that tries to convince you that there’s been an unsuccessful fax transmission. Once socially engineered users execute the malicious attachment found in the fake emails, their PCs automatically join the botnet of the cybercriminals behind the campaign.
More details:
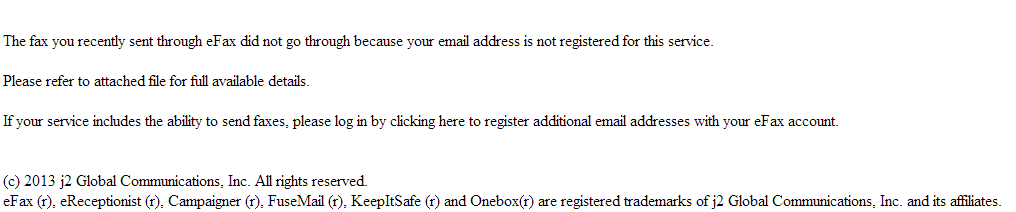
Sample screenshot of the spamvertised email:
Detection rate for the malicious attachment: MD5: 66140a32d7d8047ea93de0a4a419880b – detected by 14 out of 47 antivirus scanners as UDS:DangerousObject.Multi.Generic.
Once executed, the sample starts listening on port 16554.
It then creates the following Mutexes on the affected hosts:
Global{BB67AFC4-9FA5-408A-DBC9-BE58FA349D4A}
Global{2E06BA86-8AE7-D5EB-DBC9-BE58FA349D4A}
Global{B0B9FAFD-CA9C-4B54-DBC9-BE58FA349D4A}
Local{B0B9FAFD-CA9C-4B54-DBC9-BE58FA349D4A}
Global{B0B9FAFC-CA9D-4B54-DBC9-BE58FA349D4A}
Local{B0B9FAFC-CA9D-4B54-DBC9-BE58FA349D4A}
Global{D15F4CEE-7C8F-2AB2-DBC9-BE58FA349D4A}
Local{D15F4CEE-7C8F-2AB2-DBC9-BE58FA349D4A}
Global{D15F4CE9-7C88-2AB2-DBC9-BE58FA349D4A}
Local{D15F4CE9-7C88-2AB2-DBC9-BE58FA349D4A}
Global{0BB5ADEF-9D8E-F058-DBC9-BE58FA349D4A}
Local{0BB5ADEF-9D8E-F058-DBC9-BE58FA349D4A}
Local{911F9FCD-AFAC-6AF2-DBC9-BE58FA349D4A}
Global{6ECDB23F-825E-9520-11EB-B06D3016937F}
Global{6ECDB23F-825E-9520-75EA-B06D5417937F}
Global{6ECDB23F-825E-9520-4DE9-B06D6C14937F}
Global{6ECDB23F-825E-9520-65E9-B06D4414937F}
Global{6ECDB23F-825E-9520-89E9-B06DA814937F}
Global{6ECDB23F-825E-9520-BDE9-B06D9C14937F}
Global{6ECDB23F-825E-9520-51E8-B06D7015937F}
Global{6ECDB23F-825E-9520-81E8-B06DA015937F}
Global{6ECDB23F-825E-9520-FDE8-B06DDC15937F}
Global{6ECDB23F-825E-9520-0DEF-B06D2C12937F}
Global{6ECDB23F-825E-9520-5DEF-B06D7C12937F}
Global{6ECDB23F-825E-9520-95EE-B06DB413937F}
Global{6ECDB23F-825E-9520-F1EE-B06DD013937F}
Global{6ECDB23F-825E-9520-89EB-B06DA816937F}
Global{6ECDB23F-825E-9520-F9EF-B06DD812937F}
Global{6ECDB23F-825E-9520-E5EF-B06DC412937F}
Global{6ECDB23F-825E-9520-0DEE-B06D2C13937F}
Global{6ECDB23F-825E-9520-09ED-B06D2810937F}
Global{6ECDB23F-825E-9520-51EF-B06D7012937F}
Global{6ECDB23F-825E-9520-35EC-B06D1411937F}
Global{6ECDB23F-825E-9520-05EE-B06D2413937F}
Global{6ECDB23F-825E-9520-4DEC-B06D6C11937F}
Global{DDB39BDC-ABBD-265E-DBC9-BE58FA349D4A}
Global{2E1C200D-106C-D5F1-DBC9-BE58FA349D4A}
The sample then phones back to the following C&C server hxxp://lukafalls.com/banners/index.php – 95.154.254.17, as well as to the following C&C IPs:
95.154.254.17
190.179.212.30
65.92.129.196
125.25.82.22
69.235.15.127
108.215.44.142
188.153.47.135
76.226.112.216
78.100.36.98
190.162.42.76
78.99.110.225
118.101.184.54
90.156.118.144
212.182.121.226
99.97.73.189
181.67.50.91
2.87.2.21
108.215.99.94
84.59.222.81
142.136.161.103
178.203.226.84
95.234.169.221
217.41.0.85
71.143.224.43
74.139.10.100
78.38.40.207
213.215.153.212
We’re also aware of the following malicious MD5s that are known to have phoned back to the same IPs over the last couple of days:
MD5: d8d6329eb2ef7cf138a18fd39c3ca519
MD5: fe4897f0712dfa664b20a7bda9b31c14
MD5: 673f25cdc6a4b6de151aec1a9dc90700
MD5: c39e7f31b06ffd172216a6c2feb84a76
MD5: 6193322ae5b1b4ee1e5a4d59b196a4d9
MD5: 5c5ee058b98588309fb0e04a06f2d8b7
MD5: 9609c6027d81243592c4f45878a60876
MD5: f3b396040af190a913368a2adb1b262a
MD5: b857a14fa537379b7121d4a98c4caafe
MD5: a82895fab5d5c3d7ace0f8d2b34986bb
MD5: 162f8d9218563b13c0c0dda4bf0505a0
MD5: bab6583874e8ea249023fa8dbe390d84
MD5: 691111fe48363cd8b425de4dbcd038fd
MD5: 9ed444e9f124cee1efd5830bbd66d087
MD5: 883f1ad690c8ee5bcfb1ae841d6ac3a3
MD5: ddcc95675ba377e67fdf595420789beb
MD5: e377c045a62deb71ddab9d46942e9cd3
MD5: 18bfe04b02cb15c08089b99daad85fac
MD5: c890459bac4049f7d3a4332d98da54a8
MD5: 6a7cb5082d8ce9c4a2ee7c22708ad5e9
MD5: 3a7fd358b840f4e9c77059d5b95f5a7c
MD5: 01828136ba1c58096d314f612de0042a
MD5: 64f701aec9b22fa587f3de43ab4eba6c
MD5: 8f815f54d04086a5fab181e6de37c39f
MD5: b643e10b90a2a0787d63ea7cb1259a3a
MD5: b0a5b77e9efbff2e8b6e1b03961d2ca2
MD5: a01af9e2c7351ebcac3903f35d75de25
MD5: 88adea70e0fc4e13ff80a311796a7fd7
MD5: c69a7a396bb012a1c282e16140033dfa
MD5: 6ed8cd8bd03b5b52a1790a4b926facbf
MD5: 203d5701fccc7ca62c0def5ee75e855b
MD5: a145fa184e060cb4fdf5c7b87f19d8c2
MD5: 916e0b8e852327f66eebb9e102f5fe25
MD5: d90e6cf92efd7562b0b4f35a89ef1757
MD5: 015c9df3e57507d4d8371ebbc412eef2
MD5: e13d6dcf5cac66ec32dd4c6b6a591005
MD5: 95a8f8a7d84e1b8a135ca2e47a3ee25f
MD5: dc8e8e4444dcd9c2fd8e8d6a2941059b
MD5: 74b3d3403155cfafbe3878dbd2b82415
MD5: aaf61821d1279d2146c8e91d7d6a1c26
MD5: 816efa5cd3f4cdbed7c03008646ae697
MD5: f268c3c7d86187cc043a9c6225a834f3
MD5: c2482b968948de476c3922f003cb8871
MD5: 7f68c5bfe96051ea29e7babecfe8a318
MD5: d44b538fa6c506d50f6bb450d542fb62
MD5: 79e961df194e851398f9724253998448
MD5: 14ada26bec2ec1eadf0811d8621a1577
MD5: bca48dcd06c89618e2ca53583c8f28e0
MD5: 235c379f9c7bb580dfa0e45a4ce41f3d
MD5: 33ea9d9b86f8866c29c8ad5eee5ba63b
MD5: fd834feb5ffd973104d758e3e9596504
MD5: d08c28e39f49c6b9ca2989d7b78d51d7
MD5: 295ac362d7ef3e03d67676f7b3b0ec17
MD5: 2dcfd44fe1884706d83bf8989e4ccb00
MD5: 39f576c4c115100652c57269584d42fc
MD5: a98762b111ca02bf6e9c81085d1fc035
MD5: 8a3892f7294d026e8369edfb68f1c8a7
MD5: b0954c64cd2173506deca42fc932acec
MD5: 949db66511dc9f08f284de85b84b5c5e
MD5: a151ddeedf3e0403b972333b86bd743d
MD5: 1e37151a6f7d13d60c979afbb47ea2ac
MD5: 4136bb424d16b7487c2ac1cb698c7bf5
MD5: 2fe9a8b3564a09d4c73e3973c1a7c3df
MD5: 03517ff539caa30da1df941b7ea405c8
MD5: 70908c6635cb74fbd44012e66db4c0e8
MD5: a4e0888fc717fe1c8060f25f8c033450
MD5: 0d4af8aebcdb7d90fb0461913b3f589b
MD5: e1cd4828ac4c6b716467271012b58d0f
Webroot SecureAnywhere users are proactively protected from these threats.
You can find more about Dancho Danchev at his LinkedIn Profile. You can also follow him on Twitter.