Recently we’ve seen a new fake security product running around that has made improvements to the standard rogue. Typical rogues are annoying, but relatively easy to take care of. Previously, all you had to do was boot into safe mode with networking and remove the files and registry entries (or install an antivirus product). Support forums everywhere use safe mode with networking as the “go to” mode for virus removal as non-core components are not loaded at start up and it’s easier to isolate problems. In the vast majority of the rogues we see, they are not loaded in the few modules which start up in safe mode. Antivirus System does, however, and it also applies some new and improved social engineering tactics to fool you into thinking it’s a real program trying to help you.
-
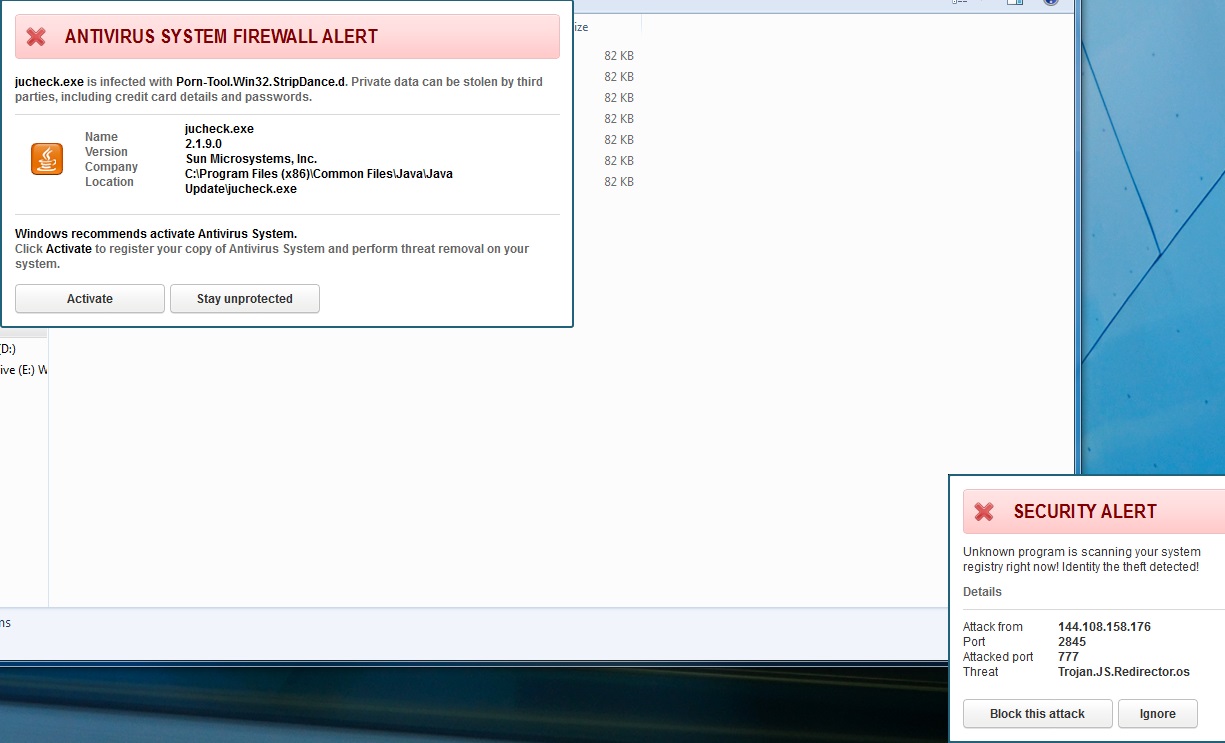
Executable Hijack
-
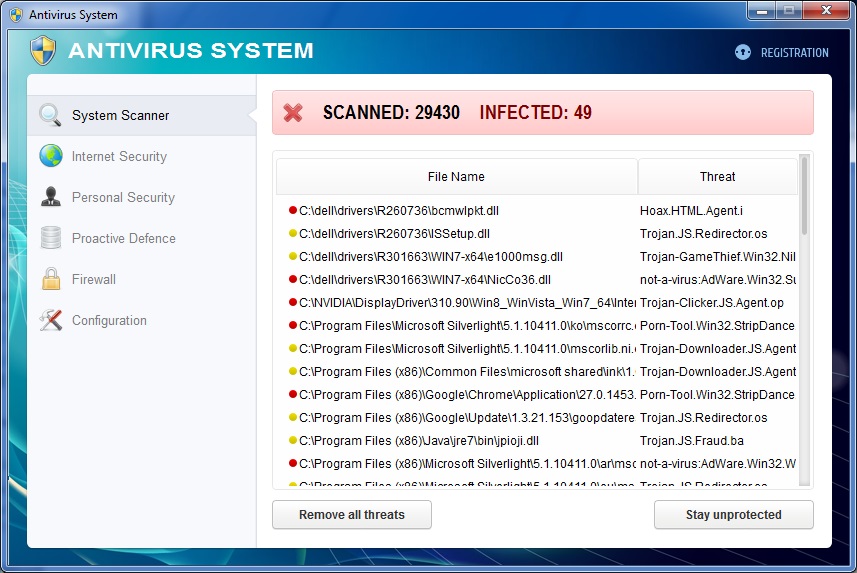
Scanning of real files
-

Proactive Defense
-

Personal Security
-

Internet Security
-

Configuration
Once loaded onto your system, any executable you try and launch will be stopped and flagged as malicious – pretty standard. Eventually the interface will come up and will start scanning. What’s unique about this variant is it does actually scan your system. I do not mean it removes malware or does anything beneficial, but the infections it reports are real files on your computer. This variant flagged Dell drivers that are exclusive to my laptop model and one of my chrome extensions. This indexing of real files is a big improvement over the transparently fake “scan” buttons on previous rogues that just lead to an animation of a loading bar along with a generic list system files. Antivirus System also has many “features” which appear on most legitimate security applications. It has Internet Security which is similar in description to Webroot’s Web Threat Shield. Their Personal Security attempts to spoof features like Webroot’s Identity Shield, and Proactive Defense fakes features similar to Webroot’s Real Time Protection. This rogue even has configuration settings like “Concede resources to other applications” alluding that it can lower how much of a resource hog it can be – if you pay for it. Of course none of these “features” do anything, and if you try and switch them on you’ll just be presented with their purchase screen.
Removal without Webroot installed
Most experienced users would immediately go into safe mode with networking after seeing this. This won’t work, as the rogue is attached to the explorer shell, which is a module loaded in safe mode, and it will lock you down after you launch any executable (regedit, task manager, standalone virus removal tools, ect.). This is probably the point where most people have run out of options and consider taking their PC to a 3rd party technician where you’ll likely pay double the ransom cost of the Rogue. There is no need to do this as there are plenty more tricks to get around these rogues.
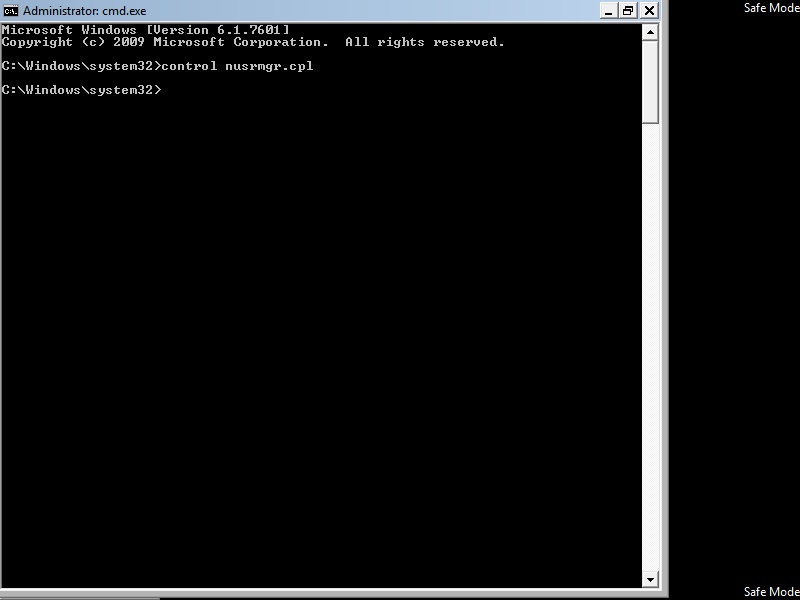
- Boot into Safe mode with Command Prompt (doesn’t launch explorer shell)
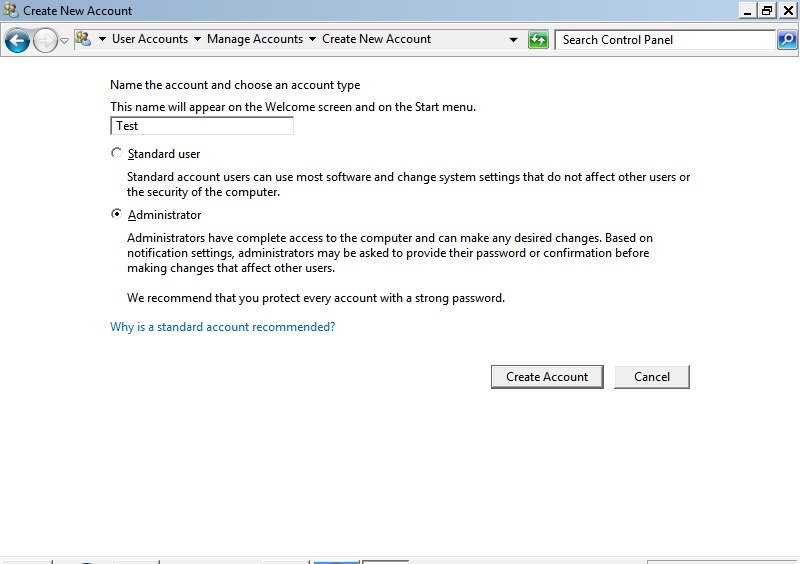
- The first screen that comes up is cmd.exe, type: “control nusrmgr.cpl” to launch the user account screen
- On the user account screen click on “Manage another account”
- On the Manage Account screen click on “Create new account”
- Call this account whatever you want and then create the account (just make sure it has administrator privileges)
- Reboot the computer and then log into that new account (safe mode or normal mode)
- This new account won’t have those policies the virus created and you should be able to use this account freely You can install Webroot to scan and remove the virus, or you can just delete the files and registry entries associated:
- DELETE:
C:UsersAll Userspavsdata
C:UsersAll Userspavsdata21.4.exe
C:UsersAll Userspavsdataapp.ico
C:UsersAll Userspavsdatacache.bin
C:UsersAll Userspavsdatasupport.ico
C:UsersAll Userspavsdatauninst.ico
C:UsersAll Userspavsdatavl.bin
C:ProgramDatapavsdata
C:ProgramDatapavsdata21.4.exe
C:ProgramDatapavsdataapp.ico
C:ProgramDatapavsdatacache.bin
C:ProgramDatapavsdatasupport.ico
C:ProgramDatapavsdatauninst.ico
C:ProgramDatapavsdatavl.bin
HKEY_CURRENT_USERSoftwareMicrosoftWindowsCurrentVersionRun “avsdsvc” = “%CommonAppData%pavsdata21.4.exe /min” - MODIFY:
[HKEY_CLASSES_ROOT.exeshellopencommand]
Default=”C:\ProgramData\pavsdata\21.4.exe” /ex “%1″ %*
to
[HKEY_CLASSES_ROOT.exeshellopencommand]
Default=”%1” %*
Removal with Webroot installed
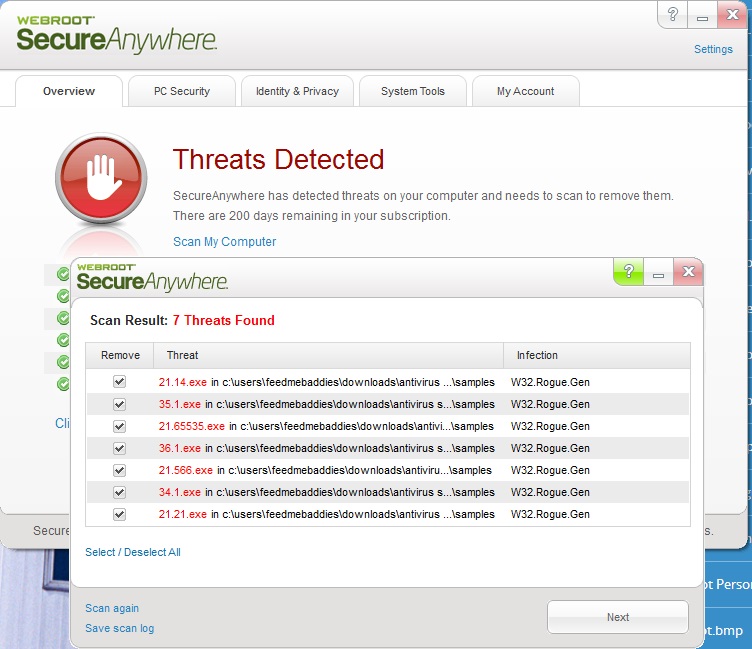
If you already have Webroot installed, then you shouldn’t even have to scan as we should block this in real time. If you happen to come across a new zero-day signature that doesn’t yet have a determination, then you should know about Webroot’s ability to remediate infections without a database determination. All you have to do is open your client, click the “System Tools” tab, and then click “Start” under Control Active Processes. You’ll then be presented with the screen below, which shows all the active processes that are running:
-
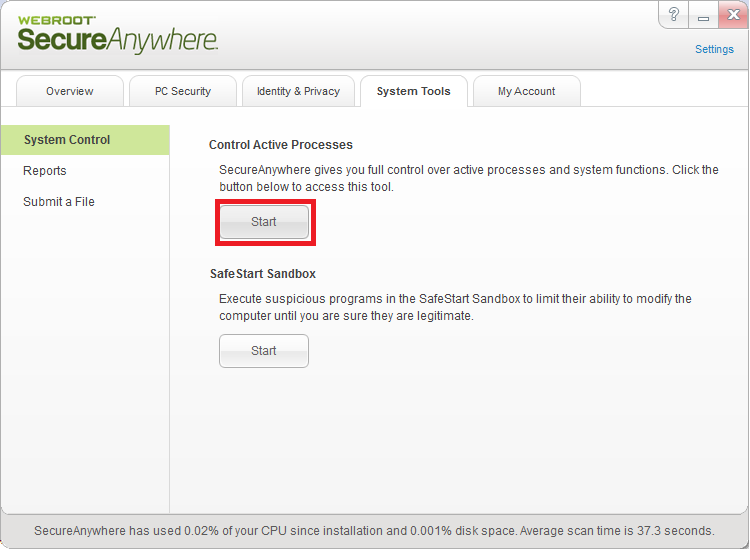
Start Control Active Processes
-
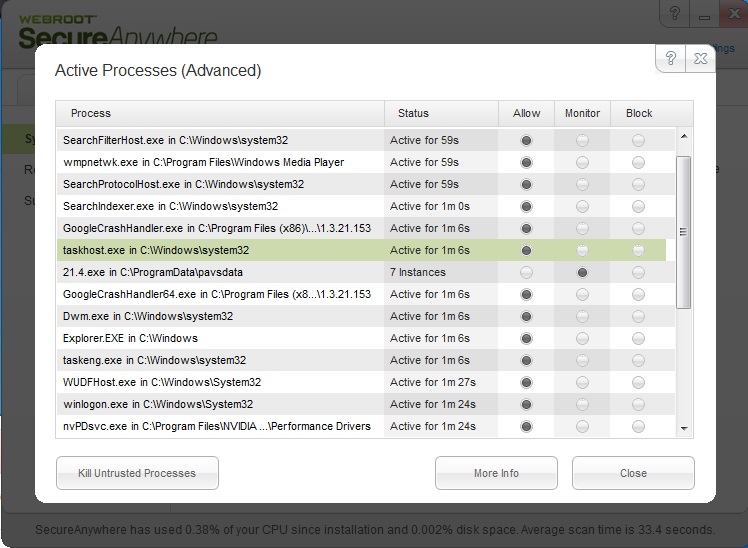
The virus is already being monitored
-
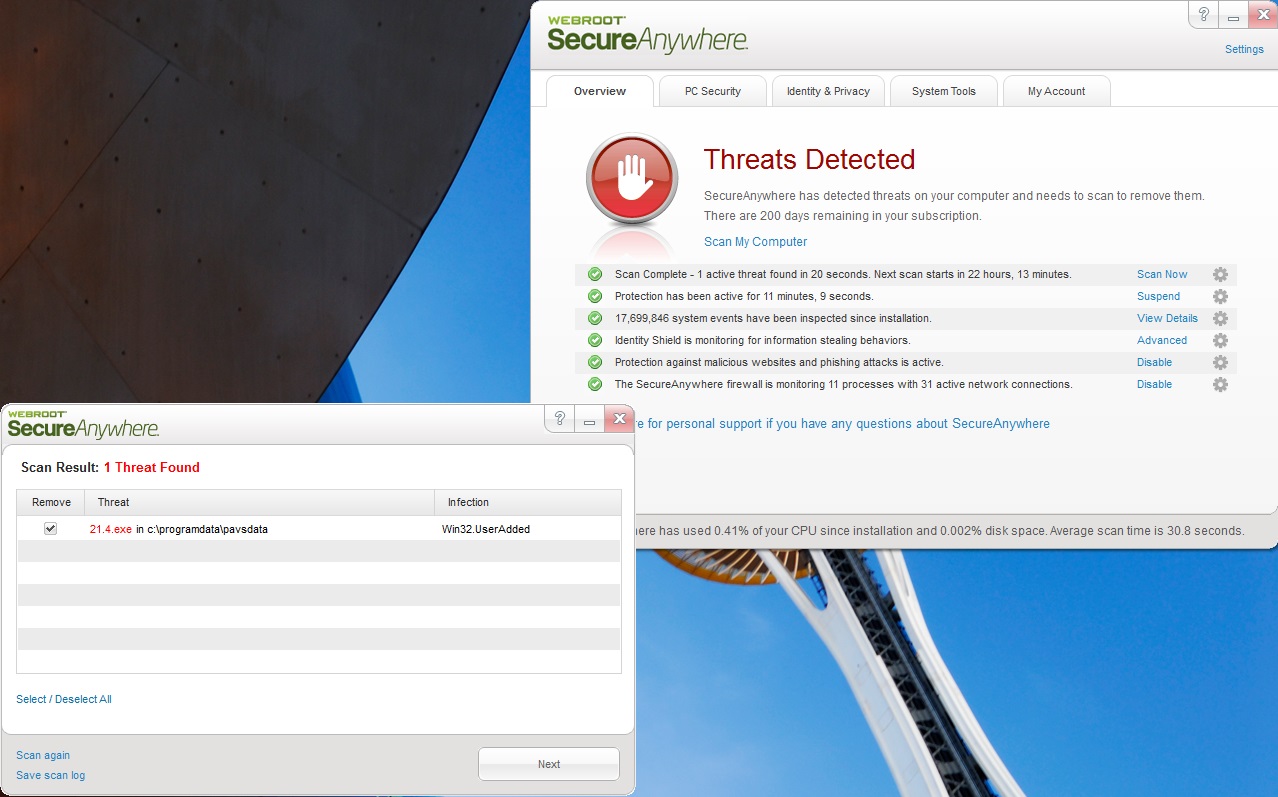
After you block and scan, Webroot will remove it
Anything running under the “monitor” column should be scrutinized. If you find anything randomly named under AppData or ProgramData, then you would set it to “block” and run a scan. Upon finishing the scan, Webroot will remove the file and roll back any changes made by the malware.
Webroot support is always more than happy to help with removal and any questions regarding infections.







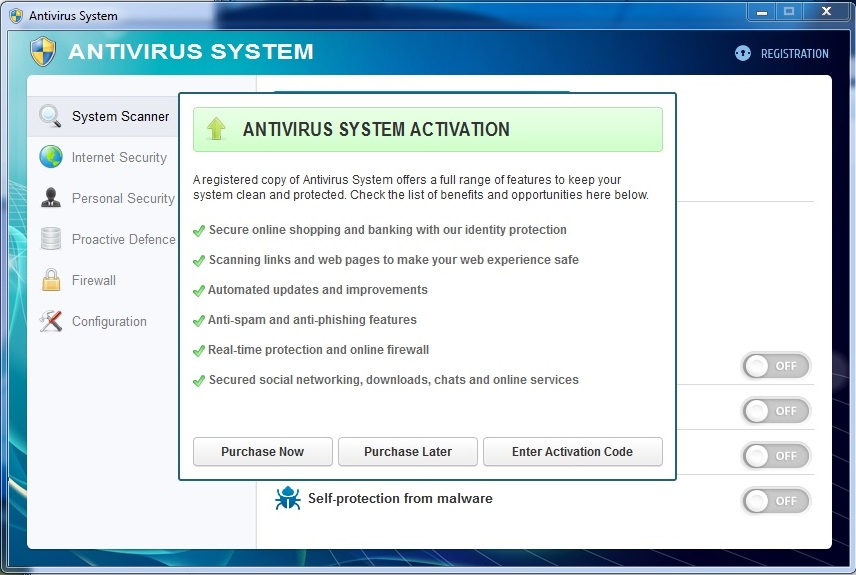
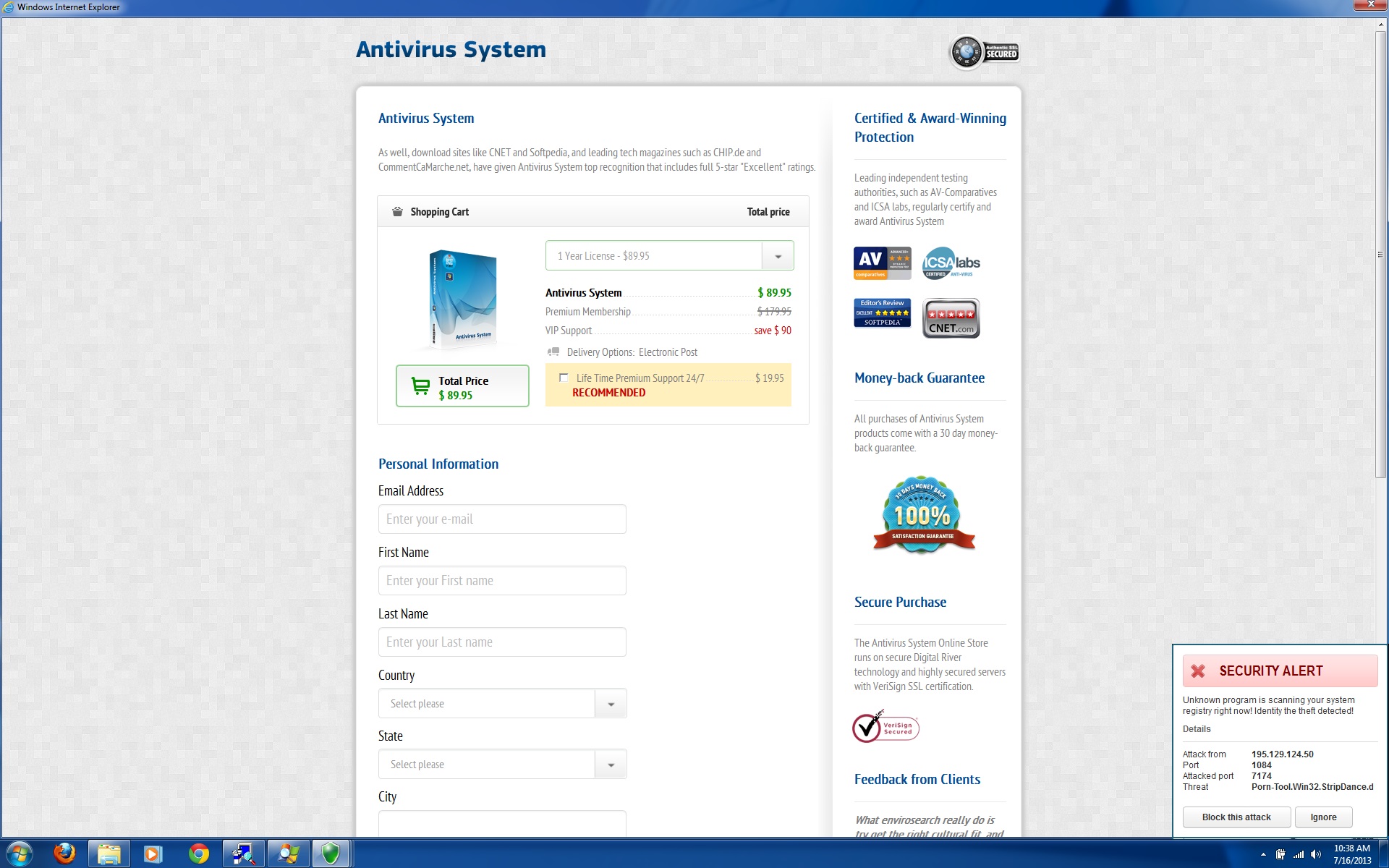
I performed the first steps of setting up another administrator account, but when I log in I still get the windows activator screen. This occurs even in Safe Mode. I did set the new account up as an administrator account. What can I do now?
Sheryl, there are certain types of infections that can cause this activation issue after creating a new Administrator account.
It is advisable for you to reach out to our Support Team directly to determine whether this issue is being caused by an infection on your System:
Support Number: 1-866-612-4227 M-F 7am−6pm MT
Send us a Support Ticket: https://detail.webrootanywhere.com/servicewelcome.asp
Regards,
Josh P.
Webroot Community Support