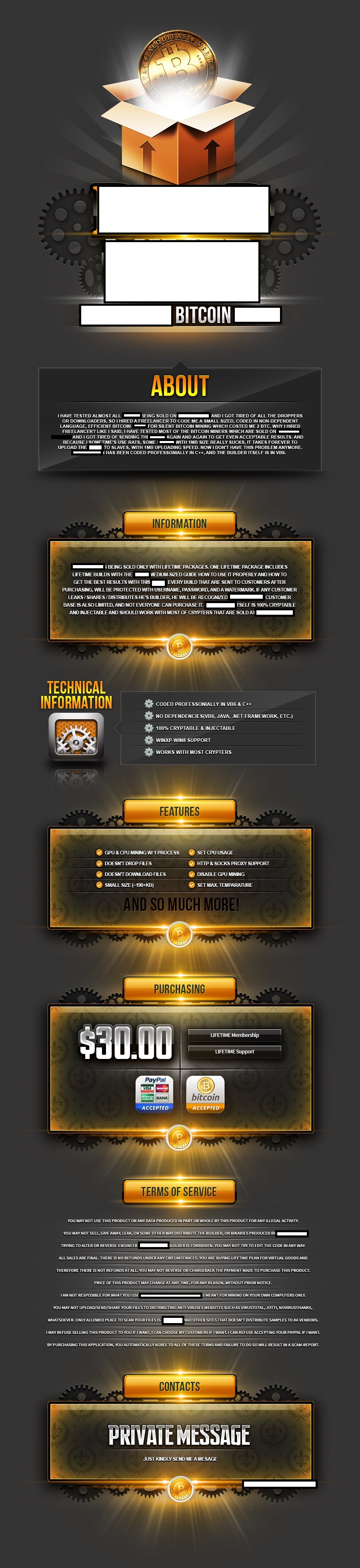
As we anticipated in our series of blog posts highlighting the growing use of DIY/subscription based stealth Bitcoin miners, cybercriminals continue populating this newly emerged market segment, with new, undetected, cryptor-friendly stealth Bitcoin mining tools. This is being done to empower fellow cybercriminals with the necessary tools to help them monetize the malware-infected hosts that they either already have access to, or intend to purchase through one of the, ubiquitous for the cybercrime ecosystem, malware-infected hosts as a service type of underground market propositions.
In post, I’ll discuss the existence of yet another DIY stealth Bitcoin mining tool, in particular how the cybercriminal behind it is attempting to strike a balance between pitching it to fellow cybercriminals — through Terms of Service — in a way that supposedly makes it illegal to install it on PCs without the knowledge of their owners.
Sample screenshot of (international) underground marketplace proposition:
The subscription based stealth Bitcoin mining tool comes with support for HTTP/Socks4/Socks5 malware-infected hosts to be used as proxies, doesn’t drop or download additional files, and supports Windows 8. Potential customers would have their builder copies ‘watermarked’ in an attempt by the vendor to detect eventual leaks of the builder in the hands of the security community.
The tool is a great example of a trend that we’ve been observing for a while, namely, the utilization of ToS (Terms of Service) issued by cybercrime-facilitating vendors. However, on their way to strike a balance in pitching their cybercrime-friendly product/service to potential cybercriminals, in between ensuring that they legally forward the abuse of the product/service to the final customer, they usually tend to portray the product/service as a legitimate one on public communities while revealing its true nature on vetted/invite-only/closed cybercrime-friendly communities. Case in point – the vendor of the stealth Bitcoin mining tool is explicitly forbidding the use of the mining tool on a PC without the knowledge of the owner, in between actually complaining that while using a Remote Access Tool (RAT), he’s constantly facing a problem with large size mining tools.
We’ll continue monitoring this market segment, and post updates as soon as new releases becoming publicly/commercially available.