Standardization is the cybercrime ecosystem’s efficiency-oriented mentality to the general business ‘threat’ posed by inefficiencies and lack of near real-time capitalization on (fraudulent/malicious) business opportunities. Ever since the first (public) discovery of managed spam appliances back in 2007, it has become evident that cybercriminals are no strangers to basic market penetration/market growth/market development business concepts. Whether it’s the template-ization of malware-serving sites, money mule recruitment, spamming or blackhat SEO, this efficiency-oriented mentality can be observed in virtually each and every market segment of the ecosystem.
In this post, I’ll discuss a recent example of standardization, in particular, a blackhat SEO friendly VPS (Virtual Private Server) that comes with over a dozen multi-blackhat-seo-friendly product licenses from third-party products integrated. It empowers potential customers new to this unethical and potentially fraudulent/malicious practice with everything they need to hijack legitimate traffic from major search engines internationally.
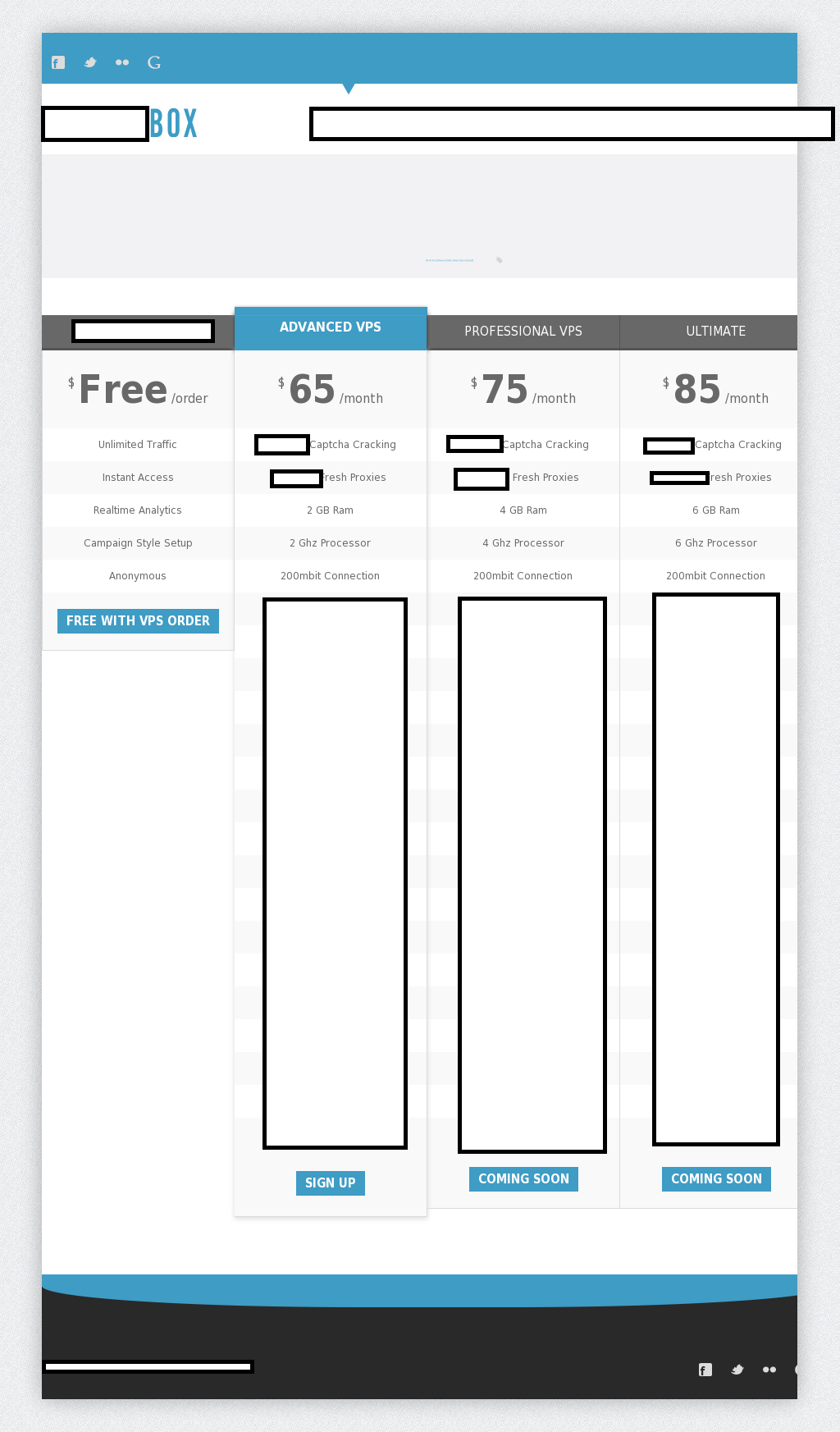
Sample screenshot of the pricing page for the blackhat SEO-friendly service:
Surprisingly, the service offers licenses to BHSEO products targeting the international market, instead of licenses for the market leading Russian-based blackhat SEO ‘products’ typically offered by competing vendors. It also features an “About the Team” page with information about the people behind this unethical business venture. Interestingly, the service is also not pitching itself as a bulletproof hosting provider, presumably due to the fact that a huge percentage of hosting providers for ‘grey and black’ projects explicitly state that they blackhat SEO campaigns hosted and operated through their infrastructure.
Over the last couple of years, we’ve witnessed the emergence of blackhat SEO intersecting with the objectives of fraudulent and malicious actors internationally. Empowering them with access to legitimate hijacked traffic, the cybercriminals conducting it quickly started monetizing it, resulting in widespread campaigns, which on the majority of occasions were used to distributed rogue/fake security software. Moreover, thanks to the once again efficiency-oriented approach when it comes to the mass compromise of tens of thousands of Web sites, and the resulting vibrant marketplace for access to compromised Web shells, in 2013, cybercriminals have virtually everything they need to abuse and hijack legitimate search engine traffic.
Blackhat SEO – just because you don’t see it, it doesn’t mean it’s not there.