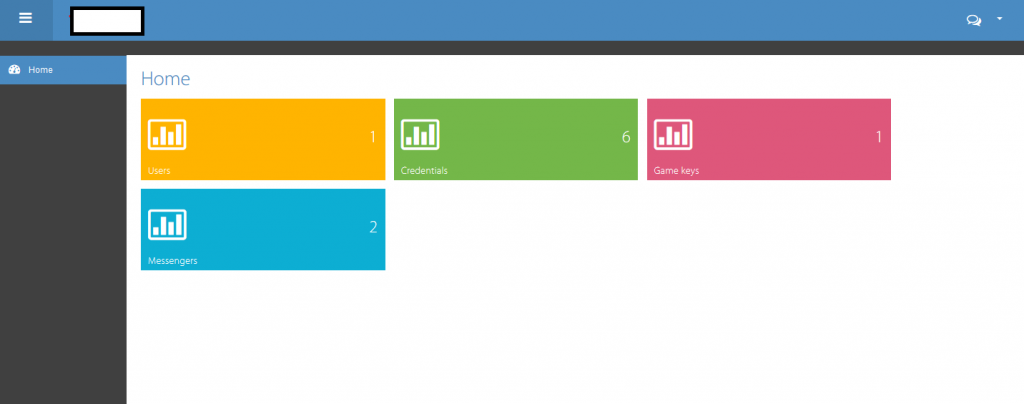
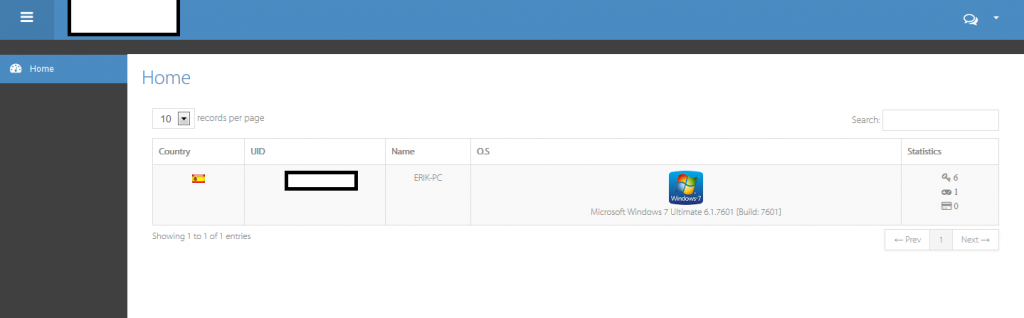
First official working week of 2014 and cybercriminals are already busy pushing new releases into the underground marketplace. The goal? Setting up the foundation for successful monetization schemes to be offered through cybercrime-friendly boutique E-shops known for selling access to compromised accounting data obtained through the use of DIY (do-it-yourself) type of services. In this post, I’ll discuss a newly released passwords/game keys stealing tool whose Web-based command and control interface is successfully mimicking Windows 8’s Home Screen, and some of the most common ways through which this very same stolen accounting data would eventually be monetized.
Sample screenshots of the Web based admin interface:
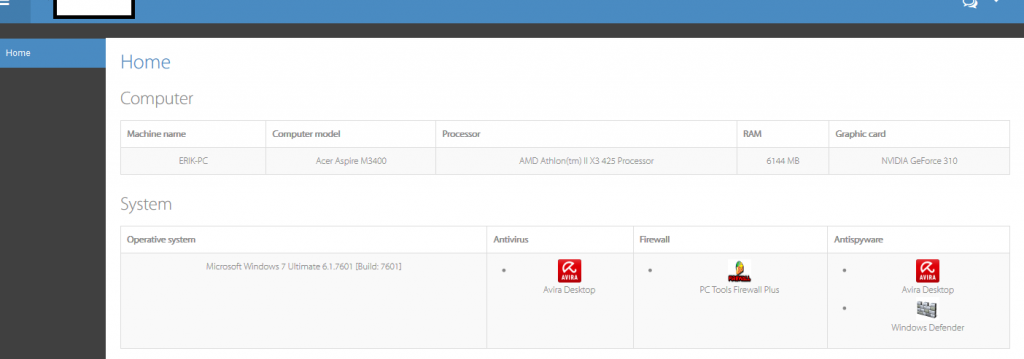
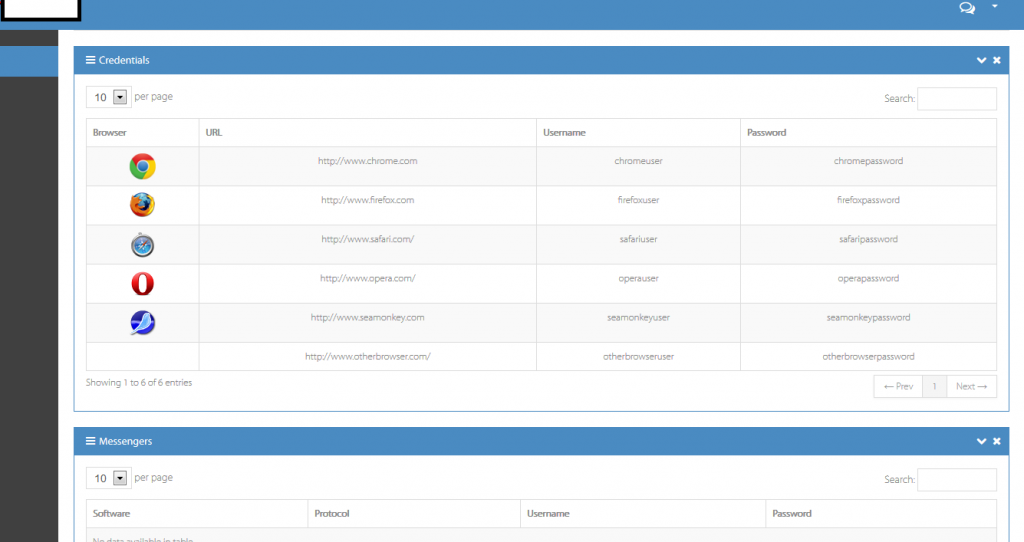
The tool has a handy — from a cybercriminal’s perspective — metrics kind of option, allowing the adversary to assess the security measures in place on the affected victim’s host, such as, for instance, the presence of antivirus/antispyware and host-based firewalls. A logical question emerges. What would a cybercriminal do with all the stolen accounting data? Thanks to the general/commercial availability of standardized E-shops for stolen accounting data, achieving a timely ‘stolen assets liquidity’ — getting rid/monetizing the data before the victim becomes aware of the compromise, thereby undermining its value — is often the most lucrative option a cybercriminal would pursue. Case in point – in a series of blog posts over the last two years, we’ve been successfully profiling the rise of these boutique E-shops for compromised accounting data, in particular ones, exclusively selling access to compromised platform-specific gaming accounting data, leading us to believe that with or without the evident standardization, the scheme is trending.
As always, we’ll be keeping an eye on the future development of the stealing application, and post updates as soon as new developments emerge.