Deceptive ads continue to represent the primary distribution vector for the vast majority of Potentially Unwanted Applications (PUAs) that we track. Primarily relying on ‘visual social engineering’ tactics, gullible end users fall victims to these privacy-violating applications, largely due to the fact that they instantaneously agree to the terms in the End User’s Agreement presented to them.
We’ve recently spotted yet another variant of the InstallBrain family of Potentially Unwanted Applications (PUA’s), tricking users into installing a bogus PC performance boosting application. Let’s assess this campaign and provide actionable intelligence on the domains/IPs and related privacy-violating MD5s known to have shared the same infrastructure as the initial PUA profiled in this post.
More details:
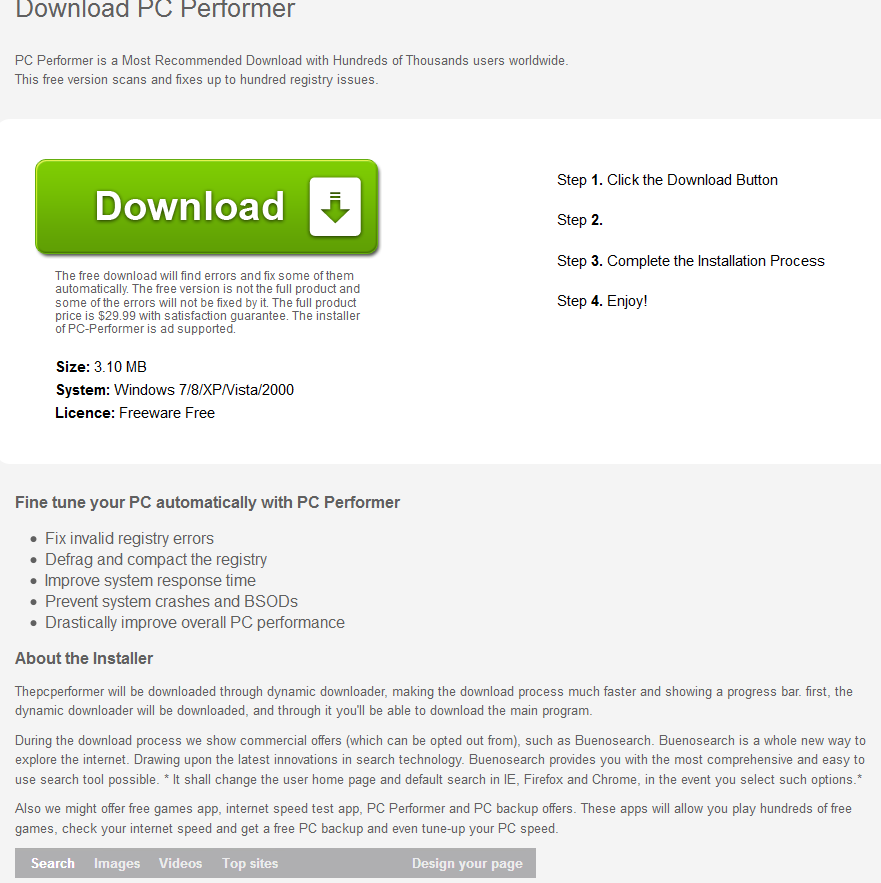
Sample screenshot of the landing page:
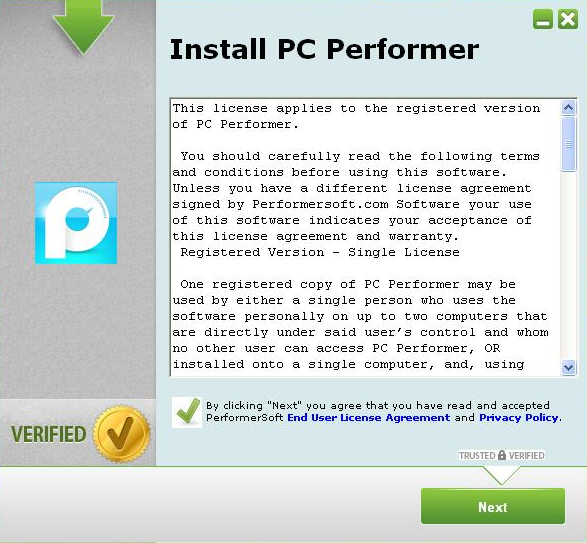
Sample detection rate for PurpleTech Software Inc’s PC Performer:
MD5: f85a9d94027c2d44f33c153b22a86473 – detected by 10 out of 50 antivirus scanners as PUA.InstallBrain!
Once executed, the sample phones back to:
hxxp://inststats-1582571262.us-east-1.elb.amazonaws.com – 23.21.180.138
hxxp://api.ibario.com – 50.22.175.81
hxxp://107.20.142.228/service/stats.php?sv=1
hxxp://174.36.241.169/events
Domain name reconnaissance:
api.ibario.com – 50.22.175.81; 96.45.82.133; 96.45.82.197; 96.45.82.69; 96.45.82.5
thepcperformer.com – 96.45.82.5; 96.45.82.69; 96.45.82.133; 96.45.82.197
Certificate Serial Number: 043990240F90A4
Known to have responded to the same C&C server (23.21.180.138) are also the following MD5s:
MD5: b800f82c629071204f3b6269d1e0035f
MD5: f52f3aaa4a2110703fb07a116b776500
MD5: 8447db94f58e177f639947498a57d4c5
MD5: 696e77da62c46b21569f44029b32d5e4
MD5: a05d4b59b78754343ea44e10cd8f033c
MD5: d9519e08fce5e4676a18ab8d967e5637
MD5: b2cd692bb0850a9c90686d6268b515fb
MD5: d9519e08fce5e4676a18ab8d967e5637
Known to have phoned back to the same IP (50.22.175.81) are also the following MD5s:
MD5: 929e73980f38e888cd8a6fc8bf47ec27
MD5: 7995c42bb868b2bcf8ba5741a1cb108d
MD5: f9a72d16d8cb4490b3bed9e2559b96da
MD5: 34bfa81f4aee300f64a42e3ff310139f
MD5: 28644086db2b113585e9ed4105913f28
MD5: 414da62a25283c6c970eb9e37d708297
MD5: 790e98e29fa4170a9fe1de7d2379212a
MD5: cf5891ce42879fb3576c2c93513f8ae4
MD5: bd4607cef78cb092752889ea6597dc15
MD5: 0aa60ccb65c57ef4766b653680641c15
MD5: 56ae3dfd1ae0ecfaa439d4e9e87212d1
MD5: fe0aa2dc1038b249da0fd84aa6ab90b6
MD5: 7644a2d6b142417bbc4b7dca8549f408
Webroot SecureAnywhere users are proactively protected from these threats.