For years, cybercriminals have been building ‘hit lists’of potential targets through automated and efficiency-oriented reconnaissance TTPs (tactics, techniques and procedures). The aim is to fraudulently/maliciously capitalize on these databases consisting of both corporate and government users. Seeking a positive return on their fraudulent/malicious activities, cybercriminals also actively apply basic QA (Quality Assurance) processes, standardization, systematic releasing of DIY (do-it-yourself) cybercrime-friendly applications – all to further ensure a profitable outcome for their campaigns. Thanks to the active implementation of these TTPs, in 2014, the market segments for spam-ready managed services/blackhat SEO (search engine optimization) continue to flourish with experienced vendors starting to ‘vertically integrate’ within the cybercrime ecosystem which is an indication of an understanding of basic business/economic processes/theories.
We’ve recently spotted a cybercrime-friendly service that’s offering commercial access to 50M+ ccTLD zone transfer domains whose availability could lead to a widespread mass abuse. Let’s profile the service and discuss its relevance/potential for abuse in the overall threat landscape.
More details:
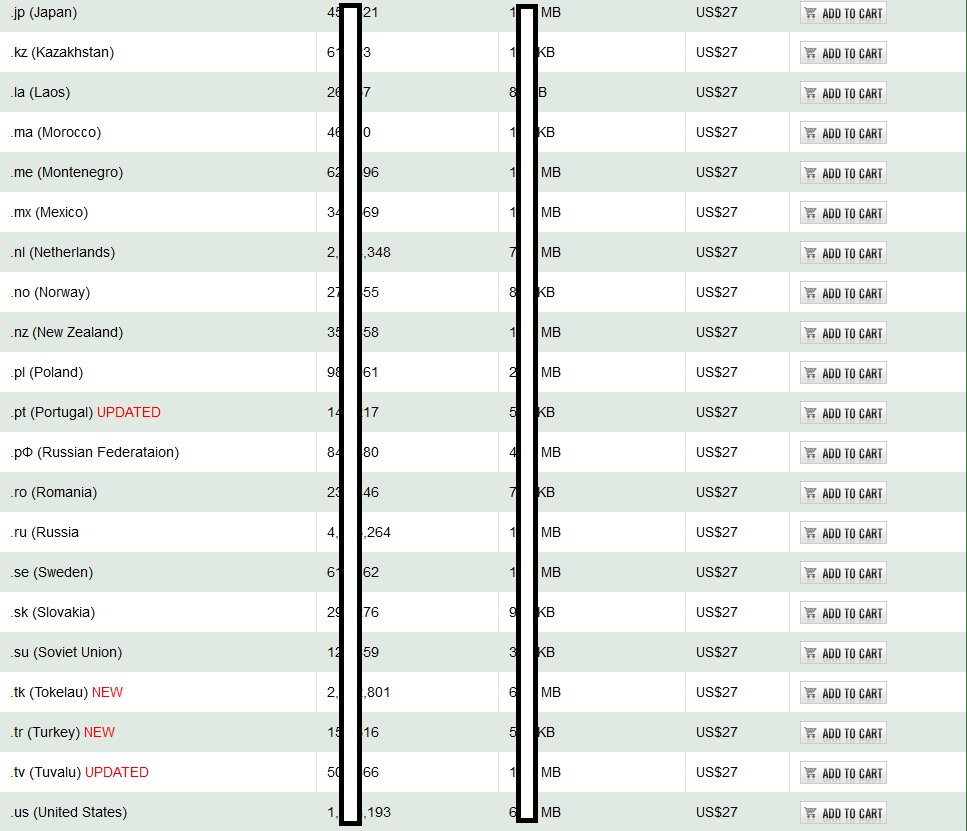
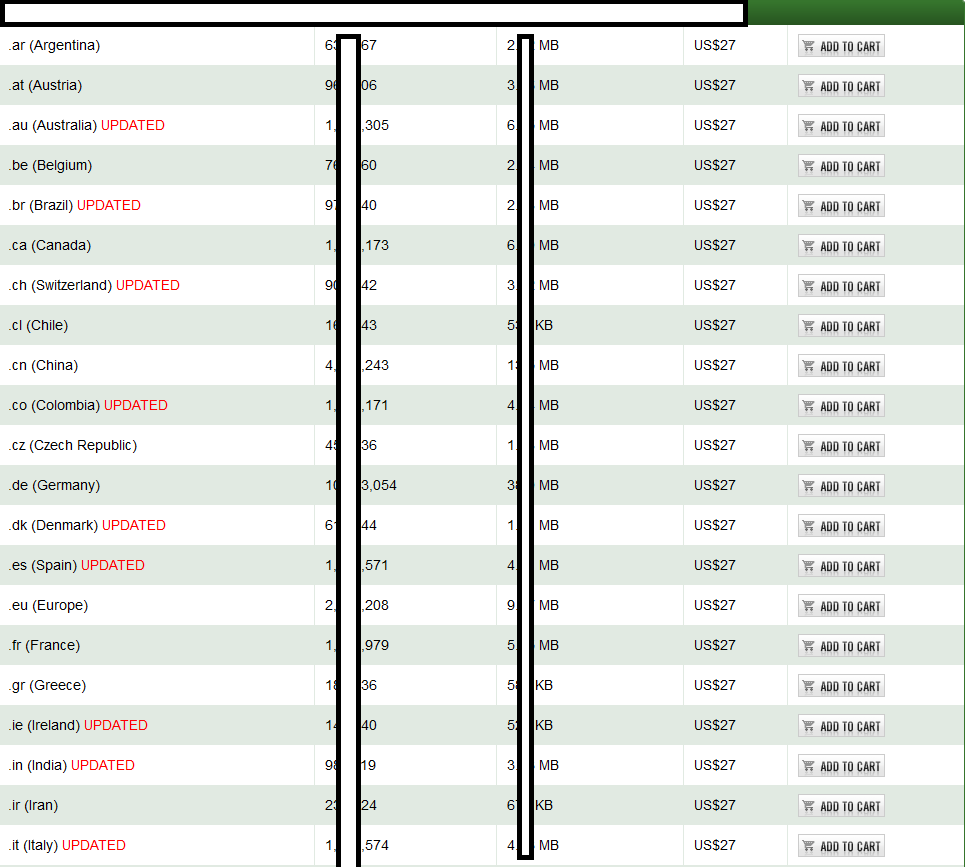
Sample screenshots of the commercial database of 50M+ ccTLZ done transfer domains, spotted in the wild:
The commercially available database currently consists of 52M+ international ccTLD zone transfer domains, empowering cybercriminals with the necessary ‘touch points’ for launching dictionary attacks, active email and phone number harvesting campaigns, ultimately leading to segmented email/domain/phone databases, resulting in, both, targeted/mass Web site hacking campaigns. Next to the potential for data mining these databases, leading to a higher probability for launching successful APT (advanced persistent threat) type of campaign, potential cybercriminals are also perfectly positioned to exploit the mass reconnaissances process for the purpose of embedding malicious scripts/Web shells/anonymity based gateways, through basic Web server/CMS fingerprinting.
For years, cybercriminals have been actively abusing their (fraudulently) obtained access to compromised/hacked databases, successfully exfiltrating sensitive content, further resulting in the evident rise of services directly contributing to the overall growth of the cybercrime ecosystem. According to Verion’s most recent ‘2013 Data Breach Investigations Report‘, the use of stolen credentials, next to malware campaigns, resulted in the majority of data breaches for the organization’s participating in their sample.
We’ll continue monitoring the development of the service and post updates as soon as new developments/market competitors take place/enter the market.