Cybercriminals continue spamvertising tens of thousands of malicious emails on their way to socially engineer gullible end users, ultimately increasing their botnet’s infected population through the systematic and persistent rotation of popular brands.
We’ve recently intercepted a currently circulating malicious campaign enticing users into executing the fake attachment.
More details:
Detection rate for a sampled malware: MD5: 8b54dedf5acc19a4e9060f0be384c74d – detected by 43 out of 54 antivirus scanners as Backdoor.Win32.Androm.elwa
Once executed, the sample starts listening on port 30073.
It then creates the following Mutexes on the affected hosts:
Local\{6FC54A61-D264-7CF8-D58B-19468FF29DE4}
Local\{21D28140-1945-32EF-D58B-19468FF29DE4}
Local\{3C2F38F1-A0F4-2F12-D58B-19468FF29DE4}
Global\{29B0195A-815F-3A8D-D58B-19468FF29DE4}
Global\{1D55DC30-4435-0E68-D58B-19468FF29DE4}
Global\{B9D945F4-DDF1-AAE4-1BA9-177341D093D1}
Global\{B9D945F4-DDF1-AAE4-1FA9-177345D093D1}
Global\{B9D945F4-DDF1-AAE4-7BA8-177321D193D1}
Global\{B9D945F4-DDF1-AAE4-43AB-177319D293D1}
Global\{B9D945F4-DDF1-AAE4-6BAB-177331D293D1}
Global\{B9D945F4-DDF1-AAE4-87AB-1773DDD293D1}
Global\{B9D945F4-DDF1-AAE4-B3AB-1773E9D293D1}
Global\{B9D945F4-DDF1-AAE4-5FAA-177305D393D1}
Global\{B9D945F4-DDF1-AAE4-8FAA-1773D5D393D1}
Global\{B9D945F4-DDF1-AAE4-F7AA-1773ADD393D1}
Global\{B9D945F4-DDF1-AAE4-3BAD-177361D493D1}
Global\{B9D945F4-DDF1-AAE4-5FAD-177305D493D1}
Global\{B9D945F4-DDF1-AAE4-9FAC-1773C5D593D1}
Global\{B9D945F4-DDF1-AAE4-F3AC-1773A9D593D1}
Global\{B9D945F4-DDF1-AAE4-D3A9-177389D093D1}
Global\{B9D945F4-DDF1-AAE4-FFAD-1773A5D493D1}
Global\{B9D945F4-DDF1-AAE4-03AC-177359D593D1}
Global\{B9D945F4-DDF1-AAE4-1BAC-177341D593D1}
Global\{B9D945F4-DDF1-AAE4-E7AD-1773BDD493D1}
Global\{5E86DCC0-44C5-4DBB-D58B-19468FF29DE4}
Global\{32526B1B-F31E-216F-D58B-19468FF29DE4}
Global\{68DA68FA-F0FF-7BE7-D58B-19468FF29DE4}
Global\{24816566-FD63-37BC-D58B-19468FF29DE4}
Global\{B9D945F4-DDF1-AAE4-5BAB-177301D293D1}
Global\{4E6EC1F5-59F0-5D53-D58B-19468FF29DE4}
Once executed MD5: 8b54dedf5acc19a4e9060f0be384c74d also drops the following malicious MD5 on the affected hosts – MD5: 59916e7de4064548c9901e8fdf83b283
It then phones back to the following C&C servers:
hxxp://62.76.189.58:8080/dron/ge.php
hxxp://62.76.41.73:8080/tst/b_cr.exe
62.76.41.73
62.76.185.30
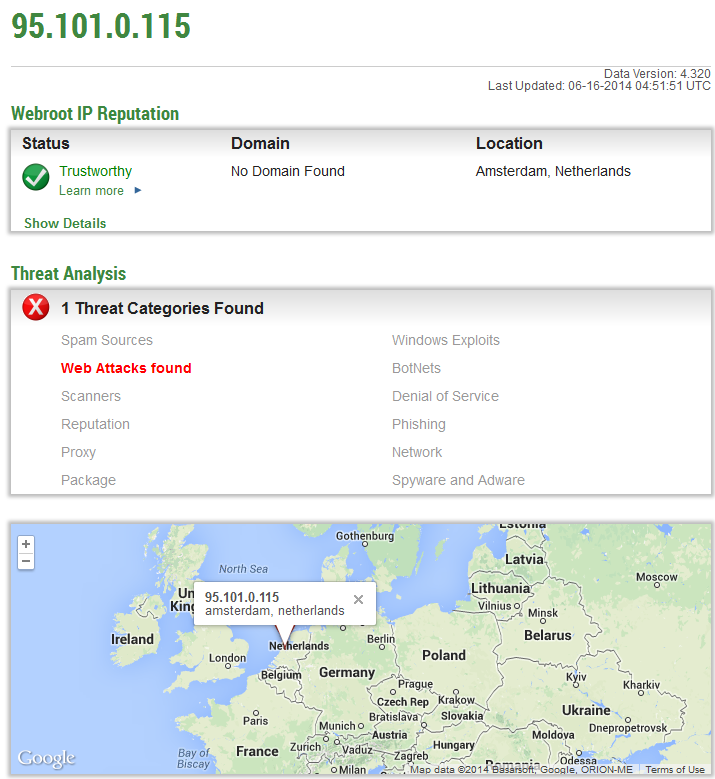
95.101.0.115
Detection rate for the dropped sample: MD5: 596ba17393b18b8432cd14a127d7c6e2 – detected by 36 out of 54 antivirus scanners as Trojan-Spy.Win32.Zbot.tfdc
Related malicious MD5s known to have phoned back to the same C&C server (62.76.41.73):
MD5: 0993f88c5d0c8b0a16100165b897525b
MD5: f9da502e4780be34b9ec0fcc359926f2
MD5: 90e92050ab83f1cf2dd99cc26e793d96
MD5: b33bc727daca6c91c172e121adaecd92
Related malicious MD5s known to have phoned back to the same C&C server (95.101.0.115):
MD5: afbc1eb2875f7dc386553eaf80f63b99
MD5: 50aa21c411f3e661a938cd7896b8218b
MD5: aceed785393c5e4bcebe40326c21acee
MD5: 0161b531593d5201e17b5883c658035c
MD5: 9e1d9d0244eca8cb954eab4165ed666b
MD5: f0a0f7c19b515bd68f5e897d6d34a880
Webroot SecureAnywhere users are proactively protected from these threats.






