Can your business stop social engineering attacks?
Social engineering attacks like phishing, baiting and scareware have skyrocketed to take the top spot as the #1 cause of cybersecurity breaches.
So what makes social engineering so effective? When cybercriminals use social engineering tactics, they prey on our natural instinct to help one another. And as it turns out, those instincts are so strong that they can override our sixth sense about cybercrime.
But our urge to help people isn’t the only thing driving social engineering. Criminals are using new methods that target the vulnerabilities of hybrid workforces. These new tactics circumvent single layers of security and are so successful, cybercriminals are using them to target office workers.
Read on to learn how social engineering works, how to spot social engineering and how to stop social engineering.
How does social engineering work?
Social engineering is a type of cyberattack where criminals use deception to trick their victims into voluntarily giving up confidential information.
Here are some common social engineering tactics:
- Using social media to find personal information. Criminals are heading to social media sites liked LinkedIn to find their next victim – and they’re using any personal information they find to craft convincing phishing emails.
- Impersonation. Cybercriminals are taking advantage of the anonymity that comes with hybrid work arrangements to impersonate people. If you’ve never met anyone in your IT department it’s hard to know when someone is impersonating them.
- Targeting personal devices used for work. With the hybrid work boom here to stay, the lines between work and home life are blurring. Employees are now using work devices for personal matters and personal devices to connect to work. The problem? Personal devices often lack robust security.
How to spot social engineering
So how do you spot social engineering scams? Here are some of the tell-take signs you’re being targeted:
- Asking for log-in information. If you get a message asking you for log-in credentials – even if it’s from a trusted source – you’re probably the target of a social engineering attack. There’s no reason why someone else needs your login info, even if it’s your boss or your IT department.
- Urgently asking for money. Along the same lines, there’s almost never a reason why someone – even someone you know – would urgently need money.
- Asking to verify your information. This type of social engineering asks victims to verify their info to win a prize or a windfall. But even if the message is coming from a legitimate organization doesn’t mean it isn’t a scam with criminals spoofing an email or impersonating a business.
How to stop social engineering attacks
Now that you’ve learned the newest tactics and how to spot social engineering, all you need is to learn how to stop it.
Forrester recommends layered defenses for preventing social engineering strategies like phishing.* That’s because most social engineering attacks are so good at getting past single layers of cyber protection.
You and your business can stay safe from social engineering scams by combining Endpoint Protection and Email Security. You gain even more protection if you are able to add on Security Awareness Trainings and DNS Protection.
Each layer you add gives you a better chance of stopping social engineering tactics.
Want to learn more about social engineering and how to stop it?
Girl Scouts and OpenText empower future leaders of tomorrow with cyber resilience
The transition to a digital-first world enables us to connect, work and live in a realm where information is available at our fingertips. The children of today will be working in an environment of tomorrow that is shaped by hyperconnectivity. Operating in this environment means our present and future generations need to understand the importance of being aware of the benefits and risks of an interconnected world. Establishing a cyber resilient mindset is the first step towards navigating and thriving in this digital-first world. Cyber resilience is the continuous access to personal and business information, even in an era of unprecedented cyber threats.
This mindset is especially relevant for children, given their ongoing interaction with the online world through existing and emerging social media platforms, gaming sites and learning avenues. As the usage and reliance on technology to educate and entertain increases, so too does the risk of being exposed to threats. That’s why it’s so important for families to develop good cyber resilience habits while engaging online.
Cyber Resilience patch program
To help instill cyber awareness, the Girl Scouts of Greater Chicago and Northwest Indiana (GSGCNWI) and OpenText have collaborated to create a Cyber Resilience patch program to empower the Girl Scouts of today for leadership in a digital world tomorrow. This partnership will help raise awareness of the dangers that exist online and the importance of becoming cyber resilient.
The Cyber Resilience patch program provides Girl Scouts with the opportunity to engage in fun and educational hands-on activities that ignite awareness and create better online behaviors. The aim of the program is to educate Girl Scouts through lessons that focus on simulations of existing and emerging threats, how to safely preserve important files and memories and what to look out for when browsing online.
General tips for children and parents
Staying resilient against ongoing threats means adopting important ways of protecting our personal information.
- Password integrity: Develop a password that is difficult to predict. Use a password generator, enable two-factor authentication (2FA) as much as possible and don’t reuse passwords from multiple logins.
- Back up personal data: Your photos and videos are precious. If you don’t secure them, you may lose them. Backing up your files means having a second copy available if something happens to your laptop, tablet or phone.
- Enable a Virtual Private Network (VPN): Protect your connection and location from malicious hackers, targeted ads and others who try to spy and track your every move online.
- Invest in security awareness training: Engaging in real-world simulations will help increase your cyber know-how.
Building a better future through cyber resilience
Creating leaders of tomorrow who are empowered and cyber aware begins with establishing cyber resilience today. Families and children should be working towards a better, more agile understanding of the risks to our personal information. Protecting the photos, videos and files that matter to us is important. Keeping our personal identities safe is vital.
OpenText remains committed to not only helping organizations find value in their data but also bolstering female leadership and diversity. The partnership between OpenText and GSGCNWI will help instill the importance of developing cyber safe behaviors now and for the future.
Cyber threats in gaming—and 3 tips for staying safe
The popularity of online gaming surged during the COVID-19 pandemic—and so did cyberattacks against gamers. If you’re the parent of a gamer, or if you’re a gamer yourself, it’s important to learn about the risks.
Why are cyber threats to gamers on the rise?
It might seem strange that cybercriminals are targeting gamers. But there are some good reasons for this trend:
- The global gaming market is booming—and is expected to reach $219 billion by 2024. Whenever that much money is floating around, bad actors will look for a way to take advantage.
- The average cost of games is rising, making “cracked” or pirated games more of a temptation. Unfortunately, hackers realize this and use the lure of free games to infect people with malware.
- A huge economy has developed within the gaming community: People buy and sell in-game objects, character modifications, and even accounts. This provides an incentive for hackers to steal and resell other people’s digital property.
- Many gamers are unaware of the cybersecurity risks that they face. In addition, many younger people are involved in gaming. This means lots of easy targets for cybercriminals.
Top cyber threats in gaming
There are numerous cyber threats to gamers. But you’ll get the most benefit out of focusing on the following three:
- Malware. Malware threats to gamers are spread through malicious websites, exploited system vulnerabilities, or Trojanized copies of pirated games.
- Account takeovers. Bad actors are always on the lookout for easy-to-breach gaming accounts. Once stolen, they can resell an account or its contents to interested buyers.
- Phishing and social engineering. Gaming is now an online social activity. This gives scammers lots of opportunities to approach unwary gamers and try to trick them into downloading malware, giving up personal details, or handing over login credentials.
Cybersecurity tips for gamers
It’s scary to think that cybercriminals are attacking gamers with greater frequency. But the good news is that taking a few basic precautions can keep you safe:
- Protect your accounts. If you have a gaming account with Steam, Epic, or another large gaming platform, take steps to keep it safe just as you would a banking or social media account. Use a strong, unique password for every account that you have. If possible, enable two-factor authentication (2FA) on your gaming accounts as well.
- Avoid pirated games. We get it, games are expensive and times are tough. But hackers love to sneak malware into those “free” copies of popular games. As such, downloading a pirated game simply isn’t worth the risk.
- Watch for phishing and social engineering. As the saying goes, if you’re online, you’re a target. The best way to stay safe is to be aware of the threat—and learn how to spot phishing and social engineering attacks when you encounter them.
Following these basic cybersecurity tips will help to make your online gaming experience more secure.
For even more protection, explore Webroot’s SecureAnywhere Internet Security Plus antivirus solution. It will keep your system safe from all types of malware threats—and includes access to LastPass®, a reliable and easy-to-use password management tool.
Webroot managed detection and response (MDR) purpose-built for MSPs
The cyber threat landscape keeps evolving at lightning-speed. According to the latest 2022 BrightCloud® Threat Report, small to medium-sized businesses (SMBs) are particularly vulnerable to becoming a victim of a ransomware attack. Cybercriminals also are becoming more selective of the organizations they target. Without human security experts and solutions at their disposable, these businesses remain susceptible to attacks.
As an MSP, there’s never been a better time to partner with a leading MDR provider to help protect your SMBs against cyberattacks. Minimize business operational disruption, maximize ongoing business continuity and bolster customer confidence with Webroot MDR.
What is MDR?
MDR is an approach to proactively manage threats and malicious activity that empowers organizations to become more cyber resilient. MDR services offer threat detection and response capabilities by augmenting cybersecurity tools with human security intelligence. Leveraging this human security expertise, MDR integrates, synthesizes and contextualizes security and other event information to hunt for, understand and respond to security incidents. This allows MSPs to offer the best combination of human expertise and a robust technology stack to help small businesses defend against future attacks.
Since MDR helps to close the gap between detection and response to threats, SMBs greatly benefit from this solution. As an MSP, you are the trusted advisor to provide your SMBs with an MDR solution to help boost their overall security stack and embrace cyber resilience.
Why should MSPs choose Webroot MDR?
SMBs are often attractive targets for bad actors looking to steal valuable data, extort money from their victims and more. We know there are many MDR solution providers on the market. However, Webroot MDR powered by Blackpoint provides a unique offering in the marketplace.
Here’s what separates Webroot MDR powered by Blackpoint from the competition:
- The fastest time in the industry from threat detection to response in 9 minutes
- A patented SNAP-Defense platform recognized by Gartner
- Best-in-class AI augmented by NSA security experts
- A competitively priced offering with unique threat detection and response capabilities
As an MSP, making the choice to purchase Blackpoint MDR through Webroot gives you:
- Seamless integration between Webroot and Blackpoint agents for quicker event investigation
- Accurate and timely insights from the BrightCloud® Threat Intelligence platform
- One-stop shop for cyber resilience that includes MDR
- Potential to obtain and lower cyber insurance costs
Ransomware, malware and phishing threats keep evolving. Your SMB customers likely don’t have the necessary security staff and tools to protect and respond to these threats. Help your customers avoid becoming a victim of data theft and extortion with industry-leading, reliable threat detection and response from Webroot. Our MDR solution can help reduce the impact of successful attacks.
Ready to discover what Webroot MDR can do for you and customers? Tune into our latest webinar.
Improved functionality and new features to help enhance the user experience
Webroot Console 6.5 is here
To help get us closer to retiring the Endpoint Protection Console, we’ve introduced three new functionality features with Webroot Console 6.5.
Friendly name support
To improve overall user functionality within the existing Endpoint Console, we have introduced a naming convention feature that allows users to assign a device a ‘Friendly Name’ that will replace the original Hostname associated with a device. All devices renamed within the Endpoint Console will see this naming convention reflected in the Management Console, allowing users to manage devices without having to navigate down to the Endpoint Console.
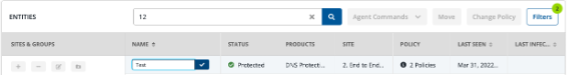
Persistent states
To further improve the user experience, the sites and entities pages has been improved with the introduction of persistent states. This introduction allows filters and searches to persist across a user’s session. Admins can seamlessly navigate away from a page and return to the view they were previously working with. This type of functionality will be introduced across other areas of the console in future releases.
Site only Admin view
This release brings forth a new look and feel for Site Only Admins to help align with the rest of the Webroot Management Console. This view represents the beginning for Site Only Admins. Admins will still have access to the Endpoint Protection Console during the uplift process in upcoming releases.
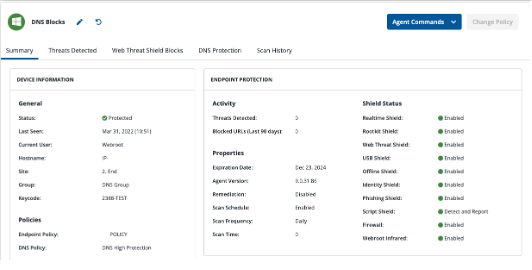
The release of Webroot’s latest console provides users with a simplified and centralized management system, intuitive user experience and enhanced visibility.
Visit our portal to get the latest Webroot updates in real-time.
Browse the status of product updates and enable delivery notifications.
World Password Day and the importance of password integrity
Passwords have become a common way to access and manage our digital lives. Think of all the accounts you have with different providers. Having a password allows you to securely access your information, pay bills or connect with friends and family on various platforms. However, having a password alone is not enough. Your password for each of your accounts needs to be difficult to guess and unpredictable. Your passwords also need to be managed and protected. With World Password Day around the corner, it’s important to take a moment and reflect on the importance of strengthening our digital hygiene beginning with our passwords.
When it comes generating a password, most of us rely on things that we can remember. A birth date, a pet’s name or our favorite sports team. While these options make it easier for us to recall our passwords, it also makes it far simpler for a cybercriminal to uncover them too. With all of the information we are freely sharing online through our social media platforms, a cybercriminal can easily spend a very small amount of time researching our habits, connections and other elements of our lives to guess potential passwords and gain access to our information. That’s why maintaining password integrity helps protect our online lives and reduces the risk of becoming a victim of identity theft or data loss.
What is password integrity?
Think of the foundation of a building. To prevent the building from collapsing in the future causing serious harm, it needs to be built with certain principles in mind. Password integrity involves the same concept. Passwords are the foundation of our digital lives. If they aren’t secure or properly managed, we run the risk of falling victim to cybercriminals who are eager to access our personal data.
Predicable passwords are problematic for several reasons. If your passwords follow the standard guidelines offered by most sites that require a single capital letter, at least 6 charters, numbers and one special character, hackers can easily make a series of attempts to try and gain access.
Without proper password integrity, personal information and business data may be at risk. The impacts for businesses and consumers are enormous. The average cost of a data breach in 2021 rose to over 4 million dollars, increasing 10% from 2020. For some small to medium-sized (SMBs) businesses, this means incurring a financial hit that could mean closing up shop. For consumers, dealing with identity theft can involve a world of headache. From freezing credit cards and assets to contacting all of the companies you regularly interact with, recovering from identity theft can be difficult and time consuming.
How to develop password integrity
The best way to prevent unauthorized access to your accounts is to protect and manage them. While avoiding duplication of passwords for multiple accounts and enabling two-way authentication can help, using a password manager is another way to help manage all of your account passwords seamlessly.
Included in Webroot’s SecureAnywhere Internet Security Plus antivirus solution is access to LastPass®, a reliable and secure password management tool. LastPass is the most trusted name in secure password management. It encrypts all username, password and credit card information to help keep you safe online. LastPass gives you access to a password vault to store and access all of your passwords from any device.
Securing your digital life means protecting and managing your information. Having a reliable password management tool can help you effortlessly manage all of your passwords. As World Password Day approaches, take a step back and assess your digital hygiene beginning with your passwords. As cybercriminals develop more sophisticated ways to steal our information or identity, maintaining our own password integrity becomes key.
Discover Webroot’s antivirus solutions and learn more about LastPass.
Soaring ransomware payments, consistent infections, deceptive URLs and more in this year’s 2022 BrightCloud® Threat Report
Cyber threats are becoming increasingly difficult to detect. Cybercriminals are also becoming experts in deception. What does this mean for your business? How can you keep your family members safe online and reassure your customers you are protecting their data?
Our threat research analysts have complied the latest threat intelligence data to bring you the most cutting-edge and insightful information about the most recent cyber threats and what they mean for you.
Below is a summary and sneak peek from the full report.
Malware
Whether you operate a business or spend time online surfing the web, malware remains a concern. In the last year, 86% of malware remained unique to a PC, which has been consistent for the past few years. This implies attackers are obtaining a level of consistency in what they do to avoid being caught.
While the goal of spreading infection is top of mind for a bad actor, infection rates are not equal. When we examined the trends between businesses and consumers, there are some marked differences:
- 53% of consumer PCs were infected more than once, but businesses lag behind migrating from Windows 7, leaving them more suspectable to infection.
- For medium-sized organizations (21 to 100 licensed PCs) infection rates are just over one-third (34%), infecting nine PCs on average.
- The manufacturing, public administration and information sectors experienced higher-than-average infection rates.
If your business falls within these industries or if you’re concerned your personal PC could be prone to infection, read the complete section on malware in the 2022 BrightCloud® Threat Report. It’s chock full of insights into the differences in infection rates by type of PC, region and industry.
Skyrocketing ransomware payments will cost more than just your revenue
If you’re a small business owner, you don’t need to be told that you’ve suffered immensely throughout the pandemic. Exposure to ransomware is just another element you’ve had to consider. Ransomware continues to plague small to medium-sized businesses (SMBs). While this is not a new revelation, the smallest organizations, those with 100 employees or less, accounted for 44% of ransomware victims last year.
That’s nearly half.
Why do cybercriminals focus on SMBs? Attacks on larger enterprises and state-owned entities bring a level of publicity and attention that makes it harder for bad actors to achieve their goal of a financial payout. SMBs, given the lack of resources to respond, are more likely to pay and pay a lot. The year-end average for 2021 more than doubled the 2020 average, reaching $322,168. With limited resources at their disposal, the smallest of organizations are faced with tough decisions ahead when it comes to making ransomware payments and disclosing their decision to do so.
Law enforcement agencies are starting to gain headway on ransomware gangs. To learn how countries are banding together to shutdown notorious groups like REvil and DarkSide, check out the ransomware section of the full report.
High-risk URLs are phishing for your data in the most benign of locations
We discovered four million new high-risk URLs were in existence in 2021. To make matters worse, almost 66% of them involved phishing. Cybercriminals look to certain times of the year to execute their attacks. They are also keen to impersonate well-known brands to lure you into clicking on malicious links. Our complete list of top brands that are most impersonated is available in the phishing section of our full report.
Thwarting cyber threats through cyber resilience
“Businesses’ ability to prepare for and recover from threats will increase as they integrate cyber resilience into their technologies, processes, and people,” said Mark J. Barrenechea, OpenText CEO & CTO. “With security risks escalating worldwide and a persistent state of ‘unprecedented’ threats, compromises are inevitable. This year’s findings reiterate the need for organizations to deploy strong multi-layered security defenses to help them remain at the heart of cyber resilience and circumvent even the most creative cybercriminals.”
Our full report helps you uncover the latest cyber trends powered by our BrightCloud® Threat Intelligence platform.
To learn more and empower your cyber know-how, download the 2022 BrightCloud® Threat Report.
World Backup Day reminds us all just how precious our data is
Think of all the important files sitting on your computer right now. If your computer crashed tomorrow, would you be able to retrieve your important files? Would your business suffer as a result? As more and more of our daily activities incorporate digital and online files, it’s important for businesses and consumers to back up their data.
What is backup?
Simply put, backup is a copy of your files. Think of your family photos, home videos, tax information and other important documents. Typically we compile these files on our computer. Without backing these files up, they can get lost or stolen.
Why backup?
Backup enables you to keep your data accessible and secure. There are so many ways your personal files or business documents could experience data loss. It could simply be a result of human error. Data loss can also occur as a result of falling victim to ransomware, malware or phishing. According to the 2022 BrightCloud® Threat Report, medium-sized organizations (21 to 100 licensed PCs) experienced malware infection rates that affected nine PCs on average last year. To make matters worse, BrightCloud® Threat Intelligence also revealed four million new high-risk URLs were in existence in 2021 and almost 66% of them involved phishing. Whether you have important files stored on your personal or business computers, your data remains at risk.
“The possibility of data loss and theft should be top of mind for individuals and businesses. Our increased reliance on digital files, the rise in cyber attacks, human error and natural disasters are just a few examples of how your data remains highly vulnerable,” says Tyler Moffitt, senior security analyst at Carbonite + Webroot, OpenText Security Solutions.
Take control of your data through backup
Beginning the backup process can be daunting. Whether you’re looking to back up your family’s documents or your mission-critical business files, it’s important to consider:
- Where will you back up your data? There are a number of backup options. From external hard drive to the cloud, there are many ways to prevent loss. It’s important to find a solution that fits your needs.
- What is your retention policy? A retention policy allows you to keep certain backups for a longer period of time. For instance, a business may decide it’s necessary to keep daily backups for a total of 30 days, but a family may choose to hold onto all their family photos for months before archiving.
Say goodbye to data loss with Carbonite
Even though there are many ways to back up your data, not all options are created equal. For instance, storing your personal files on an external drive can backfire if the drive becomes corrupt or lost. As more of our data exists online, it’s important to consider cloud-based options.
Many vendors in the market offer cloud backup solutions for your home or business. But it’s important to find a reliable and trusted provider. Carbonite is an award-winning, industry leader with reliable backup solutions. Over one million people trust Carbonite to protect their digital lives. Carbonite offers automatic, dependable and convenient backup for all of your devices and hard drive files.
Make data backup a priority
World Backup Day is an important reminder to preserve our data. As the threat landscape continues to evolve, backing up your files becomes part of a larger cyber resilience strategy. Cyber resilience is a defense in depth strategy that helps ensure continuous access to your personal and business data no matter what happens.
Carbonite offers solutions for consumers and businesses. Discover which of our plans is right for you.
Own a small business and need data backup? Discover Carbonite Safe® for professionals.
Kick start your backup journey today. To understand your backup needs, begin with our quick assessment. We’ll help you pinpoint the level of backup you need. We’ll also give you an opportunity to experience it without commitment.
Start a free trial today and discover for yourself how simple it is to back up your data with Carbonite.
Protect From Cyberattacks With These 6 Steps For Cyber Resilience
Making the case
The pros behind Carbonite + Webroot joined forces with industry leading researchers at IDC to develop an easy-to-understand framework for fighting back against cybercrime. The results? A 6-step plan for adopting a cyber resilience strategy meant to keep businesses safe.
IDC looked into the data and past the alarming headlines with million-dollar ransom payments and crippling supply chain attacks.
The facts they found are eye-opening and underline why cyber resilience is the best strategy:
- less than 2% of full-time staff at SMBs are dedicated to tech
- 30% of companies that paid a ransom forked over between $100,000 and $1 million
- 56% of ransomware victims suffered at least a few days or a week of downtime
Of course, the best strategies can’t help anyone who doesn’t adopt them. So IDC also compiled tips for communicating with businesses. Whether you’re an MSP, an IT pro or just a friend, you can use these tips to help convince the underprepared that they need a cyber resilience strategy.
The 4 reasons why cyber resilience makes sense
IDC researchers make an iron-clad case for cyber resilience by looking at the current state of cybercrime. The found 4 main reasons why businesses need a cyber resilience framework:
- Crippling cyberattacks are on the rise. Evolving methods and sophisticated tactics make cybercrime a booming business for criminals.
- A distributed IT footprint brings greater risk. The onset of hybrid work opens new pathways ready to be exploited. And let’s face it, the average home WiFi doesn’t have the right kind of security.
- IT departments are stretched thin. Less than 2% of SMBs’ total employee base is dedicated to full-time IT staff.*
- Consequences of an attack remain dire. Attacks continue to reverberate past the day of a breach, with 55% of ransomware victims suffering a few days to a week of costly downtime.**
The right tools can fight back
But it’s not all bad news. Adopting the right strategy and the right tools sets you on the road to protecting your business. The headlines are scary and the stats are alarming, but they’re not prophecy. Businesses don’t have to live in fear of falling victim to cyberattacks.
From framework to action
IDC goes in depth for the steps businesses can take to adopt cyber resilience. Here’s a quick preview of the framework:
- Identify. You can’t protect what you haven’t first identified.
- Protect. Employees and their devices are cybercriminals’ first targets. Protect them and start a systematic file and backup system.
- Detect. Threat intelligence and experience-based detection can thwart even the most sophisticated attackers.
- Respond. It’s imperative to stop attackers’ advances before real harm occurs.
- Recover. Clean up infected devices, close backdoors and have a plan to recover damaged or out-of-commission assets.
- Educate. Empower your employees to form a citizen army of cybersecurity checkpoints.
Combining powers to form the best defense
IDC also suggests the best ways that businesses can take action to protect themselves. By combining the powers of outside help with in-house know how, businesses benefit from the best of two worlds.
Ready to start protecting yourself and your business? Explore how Carbonite + Webroot provide a full range of cyber resilience solutions.
* IDC’s Worldwide Small and Medium Business Survey, 2020
** IDC, Future Enterprise Resiliency & Spending Survey Wave 6, July 2021, IDC’s 2021 Ransomware Study: Where You Are Matters!
Strengthening cyber resilience in the UK through managed service providers
The UK government has released a National Cyber Strategy to help guide the country’s strategic approach to combating the proliferation of cyber threats. As part of this strategy, the UK government is looking to expand its regulations under the Network and Information Systems (NIS) to include managed service providers (MSPs). The government’s efforts follow a string of supply chain attacks targeting SolarWinds, Microsoft Exchange Servers and the Colonial Pipeline. The UK government has highlighted a number of barriers to proper management of supply chain risks, including low risk recognition, limited visibility and insufficient expertise and tools to evaluate suppliers.
This strategic move by the UK government involves widening the scope of the NIS regulations to include MSPs. Original NIS regulations came into effect in 2018 to optimize cybersecurity offerings provided by companies within the essential services industries – water, energy, transport, healthcare and digital infrastructure. Expansion of the NIS regulations to include MSPs informs part of the UK government’s broader strategy to improve the country’s overall cyber resilience.
MSPs provide critical digital outsourcing services for IT departments and manage key business processes for many organizations. As such, MSPs play a vital role in promoting a digital-first economy. The UK government wants to ensure MSPs are fully prepared to manage ongoing cyber threats and protect the data integrity of their customers.
As the UK government moves forward with its plans, part of its proposal involves defining what an MSP does, from a commercial perspective. Under the proposed regulations, MSPs could be required to enact reasonable and proportionate security measures to protect their network and proactively manage the risks associated with services provided to customers. As of late, the NIS regulations that are being proposed could carry reporting requirements and heavy fines for those MSPs that don’t comply.
Embrace regulatory shifts with ease
We know adapting to these new and evolving requirements can be overwhelming.
Carbonite + Webroot are here to help. We offer a suite of business solutions to help keep your customers secure with reliable always-on protection, backup and recovery solutions designed to fit your needs.
Find the best solution for your business.
Social engineering: Cybercrime meets human hacking
According to the latest ISACA State of Security 2021 report, social engineering is the leading cause of compromises experienced by organizations. Findings from the Verizon 2021 Data Breach Investigations Report also point to social engineering as the most common data breach attack method.
Social engineering is a term used to describe the actions a cybercriminal takes to exploit human behavior in order to gain access to confidential information or infiltrate access to unauthorized systems and data.
What does social engineering look like?
Social engineering can take many forms. Some malicious actors might trick you into giving your password or financial information away. They may also try and convince you to provide remote access to your computer or mobile devices. Cybercriminals are looking for ways to gain your trust and take advantage of your curiosity by sending messaging that contains malicious links or downloads.
“One method of attack bad actors use quite frequently involves spoofing legitimate vendor support centers. Cybercriminals will pretend to represent these organizations by posting sponsored ads online or through promoted search results. They will offer assistance and sell expired or stolen products of the vendor they have impersonated. These cybercriminals prey on unsuspecting individuals who offer up their personal and financial information because they believe they are in contact with the real vendor,” says Tyler Moffitt, senior security analyst at Carbonite + Webroot, OpenText companies.
Some common social engineering tactics include:
- Impersonating someone. An urgent request from a ‘friend’ or person you may know is a common tactic used by bad actors to compromise your information by attempting to gain your trust.
- A legitimate-seeming request from a trusted source. A phisher may send an email, message or text that appears to be from a legitimate organization you interact with. According to the latest IDG report, phishing attacks are on the rise.
- Oversharing personal information online. Some cybercriminals will gather intel through social networking sites like Twitter or Instagram and use that information to spoof various services or places you visit.
“Oversharing personal information online is especially dangerous for public figures or prominent employees. Cybercriminals conduct research online through a user’s social media channels to determine where a person visits and what activities a person participates in. Cybercriminals will then spoof their target with seemingly legitimate messages from that vendor with attractive offers. All they need is a click,” says Moffitt.
Avoid becoming a victim
To outwit social engineering attacks:
- Slow down and remain in control. If you receive a message that conveys a sense of urgency to act, carefully consider whether you should respond.
- Beware of what you download. Use a reputable web browser and remain conscious of what links you are accessing before clicking on them. Avoid downloading free applications that may possess remote access trojans that can compromise your device.
- Delete any requests to provide financial information or passwords and report them as spam. Avoid responding to requests for help or offers to assist from individuals you don’t know.
- Invest in security awareness training. Prevent your devices from becoming compromised by common attack vectors by investing in security awareness training. Testing yourself regularly with phishing campaigns can help you learn what to avoid.
As cybercriminals continue to exploit human behavior and take great strides to make their attack vectors appear harmless, it’s important to remain vigilant of how cyber threats continue to evolve.
Webroot offers a number of solutions to help you tackle these ongoing cyber threats. Experience powerful and reliable protection from Webroot that won’t slow you down. Whether it’s updating your antivirus software or learning to spot phishing traps with security awareness training, Webroot has you covered.
Considering cloning? Combat data bloat with file transfers instead.
If you own a computer that seems to have slowed to a crawl, you may be thinking about replacing it. But what about all the files on your old dinosaur? You may be thinking about transferring them to an external hard drive, a time-consuming and tedious process, or you may have heard of the far simpler process known as “cloning.”
Cloning is the act of creating a direct, one-to-one copy of a hard drive. Like the term suggests, cloning a computer will leave you with an identical copy of all the particular apps, files and settings on the device, which a user can then install onto a new one or keep as a backup in case something disastrous happens to the original.
Cloning is a pretty simple procedure and there are a lot of free tools to help you do it. But one problem it won’t help you solve is data bloat. Bloat is unwanted data that slows down a computer. This unwanted data can come in all types of different forms. It could be music, photos, games and apps, spreadsheets or text documents. One specific type of bloat, known as “software bloat,” occurs from successive updates to a computer program as they’re layered over one another time after time.
Generally, bloat is the result of the steady accumulation of more and more data as it’s added to your computer. Bloat eats away at the available memory on your hard drive and can lead to performance issues, most notably, slowing it down. If you’re experiencing frequent crashes, it may also be a problem with a corrupted file trying to execute.
You can’t clone the bloat away
Here’s where the problem with cloning comes in. Since a slow computer is a common reason for getting a new one, and cloning simply replicates all the data already stored on a device, it may not be the best strategy for getting existing files from an older computer onto a new one. Given that you’ve also probably updated your hardware, it won’t slam the breaks on your processing speeds immediately, but it’s an added burden right out of the gate.
An alternative strategy is to back up your old device to the cloud and migrating files to the new one as needed. When done this way, all the old and unnecessary files you don’t think to update yourself aren’t taking up space on your shiny new laptop. When automatic cloud backup is installed, all the latest files from the initial computer exist online, ready to be pulled down to your device whenever a local copy is needed.
Transferring data piecemeal can also help identify anything problematic that’s causing a device to crash. Once isolated, it can be easier to uninstall or delete.
By storing the majority of your files in the cloud, you ensure free space remains on your hard drive log into the future. It’s less taxing on your device, and you’ll notice better performance as a result. There are also organizational benefits to having old files stored in one convenient location. If you’re combing for tax documents from previous years, for instance, you know where to grab them from your old drive. Without having to having to watch an old laptop inch along.
So, when it comes time to replace an old computer, think twice about cloning. Choosing cloud backup from Carbonite could help extend the life and improve the performance of that new device.