One-stop-shop for spammers offers DKIM-verified SMTP servers, harvested email databases and training to potential customers
In a series of blog posts, we’ve been highlighting the ease, automation, and sophistication of today’s customer-ized managed spam ‘solutions’, setting up the foundations for a successful fraudulent or purely malicious spam campaign, like the ones we intercept and protect against on a daily basis.
From bulletproof spam-friendly SMTP servers, to segmented harvested databases for any given country internationally, managed spamming appliances, to segmented databases of APT-friendly (advanced persistent threat) emails belonging to the U.S government/military, for years, the cybercriminals operating these managed services have been directly contributing to the epidemic dissemination of fraudulent/malicious emails internationally.
We’ve recently spotted a Russian one-stop-shop for spammers offering virtually everything a spammer can ‘vertically integrate’ into, in an attempt to occupy a bigger share of this underground market segment. Let’s take a peek at the service and discuss its unique value proposition (UVP).
More details:
Cybercriminals spamvertise fake ‘O2 U.K MMS’ themed emails, serve malware
British users, watch what you execute on your PCs!
An ongoing malicious spam campaign is impersonating U.K’s O2 mobile carrier, in an attempt to trick its customers into executing a fake ‘MMS message” attachment found in the emails. Once socially engineered users do so, their PCs automatically join the botnet operated by the cybercriminal/gang of cybercriminals whose activities we continue to monitor.
More details:
Malicious Bank of America (BofA) ‘Statement of Expenses’ themed emails lead to client-side exploits and malware
Bank of America (BofA) customers, watch what you click on!
A currently ongoing malicious spam campaigns is attempting to entice BofA customers into clicking on the client-side exploit serving URLs found in legitimate looking ‘Statement of Expenses’ themed emails. Once users with outdated third-party applications and browser plugins click on the link, an infection is installed that automatically converts their PC’s into zombies under the control of the botnet operated by the cybercriminal/gang of cybercriminals behind the campaign.
More details:
Potentially Unwanted Applications and You
 PUA’s (Potentially Unwanted Applications) are often nuisance applications which serve little purpose other than using your computer as a gateway for online advertisements or as a catalyst to deliver annoying applications that may pester you to the point where you want to throw your computer out a window. Anti-Malware companies usually have pretty weak detection of these types of programs and have generally failed to protect their customers’ computers from this sort of bloatware. As a result, countless users have to suffer through agonizing pains of pop-up windows, webpage redirects, search redirects, and sometimes even bluescreens just to try and get their daily TMZ fix.
PUA’s (Potentially Unwanted Applications) are often nuisance applications which serve little purpose other than using your computer as a gateway for online advertisements or as a catalyst to deliver annoying applications that may pester you to the point where you want to throw your computer out a window. Anti-Malware companies usually have pretty weak detection of these types of programs and have generally failed to protect their customers’ computers from this sort of bloatware. As a result, countless users have to suffer through agonizing pains of pop-up windows, webpage redirects, search redirects, and sometimes even bluescreens just to try and get their daily TMZ fix.
The problem from an Anti-Malware point-of-view stems from the fact that many of these types of PUA applications could have legitimate uses for some people who choose to install the software. Some people may enjoy the fact that their Google search results are redirected to some no-name search company (that often still uses Google results anyway) and that advertisements are inserted into their browser window all in exchange of being able to use that email smiley program for free. But the reality is, most people who obtain software in such a way have no interest in all the redirects, pop-up’s and advertisements. They simply want their smileys – which leads to the second problem.
People don’t read what appears on the screen!
If users of such downloaded software would often just read the dialogue windows that appear, they would see that a combination of a few carefully selected ratio boxes would usually allow them to obtain their much-desired smiley program without obtaining all the garbage that comes along with it.
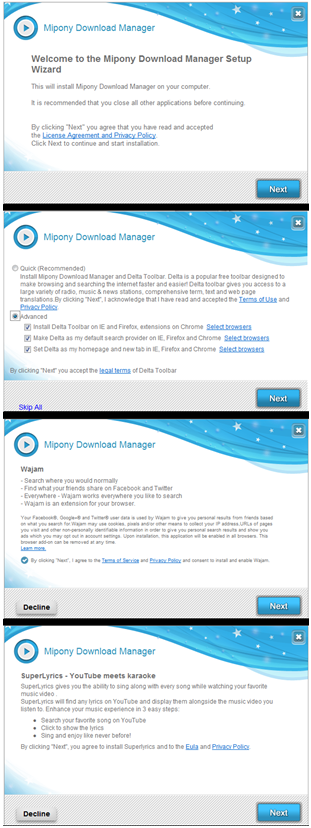
From a malware research perspective, it’s downright impossible to determine the intent of all the users of a software product. If we know that a certain application is being distributed via a deceptive download manager, but also, know some people use that same product for their own personal benefit, it becomes a difficult task in trying to make a determination whether or not to advise removal of the software in question. Many of us grew up in an era where the folk who were knowledgeable with computers would advise novice users to “download a program and just click next, next, next, until it is installed”. People learned the behavior of not reading and just clicking. (SouthPark devoted an entire episode to this exact issue) So I guess it should only be expected that people who have a financial motivation to install software to your computer have capitalized on this fact.
Take example the image to the left. This particular download manager attempts to install at least 5 different applications (We cut the image by 1 screen for the sake of saving space). After all the applications have been installed, our home page and search results were redirected. Advertisements were inserted to our browser windows and plugins were added to the browsers themselves. Simply reading the screen and clicking the ‘Decline’ button would have thwarted almost all of those unwanted behaviors.
Cases like what are shown above are usually quite easy to make a determination. We’ve previously written about many different campaigns that were distributing Potentially Unwanted Applications.
Other cases are a bit more vague, and making a determination on these types of installations is not so easy. We’re not setting out to write a blog post where we call-out reputable software vendors who bundle software with their products for the sole purpose of trying to earn a few dollars, but we would like to point out a recent example which has come to our attention and which highlights the difficulty we face when trying to make determinations within the PUA category.
We have recently been provided a WinZip installer that we are flagging as PUA.Open.Install. The file in question writes files to the computer system identified as OpenInstall. Users who downloaded this particular Winzip wrapper were not presented with any sort of opt-out mechanism and after installation the users have software related to the security vendor AVG installed to their machine, plus have their homepage redirected without consent or authorization. (Please note that we don’t detect any of the WinZip or AVG files as PUA, simply the download wrapper.)
The MD5 in question can be seen from the following VirusTotal page:
Note the ‘Behavioural information’ tab. The information contained clearly indicates the creation of files related to OpenInstall as well as associated Network traffic:
Opened files
C:DOCUME~1<USER>~1LOCALS~1TempOIC1.tmp (successful)
C:DOCUME~1<USER>~1LOCALS~1Tempoi_WgCsg9bAeBOIAssistWTD.exe (successful)
Written files
C:DOCUME~1<USER>~1LOCALS~1TempOIC1.tmp (successful)
C:DOCUME~1<USER>~1LOCALS~1Tempoi_WgCsg9bAeBOIAssistWTD.exe (successful)
Runtime DLLs
c:docume~1<USER>~1locals~1tempoic1.tmp (successful)
HTTP requests
URL: http://st.cloins.com/
TYPE: POST
USER AGENT: Mozilla/4.0 (compatible; MSIE 6.0; Windows NT 5.1; SV1; OI build 3287)
URL: http://inst.avg.com/serve/getSetup.php?pid=2793661&k=43a9519ed4b5e9c75eb7d683e3d1e09708f9b34a&sid=&pid=2793661&k=43a9519ed4b5e9c75eb7d683e3d1e09708f9b34a&sid=&user_agent=Mozilla%2F5.0+%28compatible%3B+MSIE+10.0%3B+Windows+NT+6.2%3B%29
TYPE: POST
USER AGENT: Mozilla/4.0 (compatible; MSIE 6.0; Windows NT 5.1; SV1; OI build 3287)
DNS requests
st.cloins.com (173.203.98.33)
inst.avg.com (173.203.98.33)
As can be seen, several files relating to OpenInstall (OI) are written to the box and a specialized User Agent string is added to the network connection. Simply Googling the OIAssistWTD.exe file turns up many pages indicating that the software is not a desirable application. Additionally, the results indicate that several of our competitors also have detection criteria for the software, as-well-as being identified as unwanted by a variety of malware-related blogs:
- http://forums.malwarebytes.org/index.php?showtopic=101345
- http://www.microsoft.com/security/portal/threat/encyclopedia/entry.aspx?Name=Adware%3AWin32%2FOpenInstall&ThreatID=157719
- http://home.mcafee.com/VirusInfo/VirusProfile.aspx?key=3420873#none
- http://www.sophos.com/en-us/threat-center/threat-analyses/adware-and-puas/Open%20Install/detailed-analysis.aspx
- http://www.wilderssecurity.com/showthread.php?t=341325
- http://www.scumware.org/report/install.winzip.com
- http://kimletkeman.blogspot.com/2012/11/winzip-and-avg-partner-to-be-worlds.html
- https://news.ycombinator.com/item?id=2914341
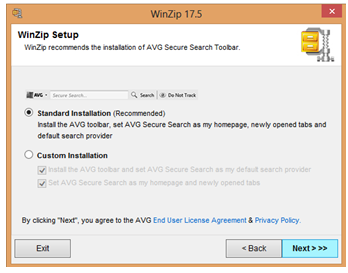
To verify the behavior that we had seen on the submitted file, we downloaded the most recent version of the Winzip file from the Winzip website. On this particular version of the software, there were no disclaimers or warnings advising of the changes. Screenshots have been included below which show the various screens during the install process. Note that none indicated the installation of OpenInstall or AVG products.
When conducting these very same steps again today (while preparing for this blog entry), we see that the Winzip installer is now providing a disclaimer and ‘opt-out’ functionality prior to initiating the download. This quick change shows the fast-paced and quickly evolving landscape that we find ourselves in, and shows the difficulty we face with Download Managers that are capable of changing their wrapper at a moment’s notice.
So, who is OpenInstall? According to Bloomberg Businessweek, OpenInstall “operates as a cloud based installation company”, and that ‘the company offers CloudInstaller to manage software download and installation for development teams to focus on their core product and for marketing teams to provide input into the conversion funnel for their software’. The overview goes on to state that OpenInstall “provides a management platform to make right offers to right users at the right time”. The overview provides the company web address of www.openinstall.com . Clearly, the Company Overview indicates an advertising agenda. Trying to access the OpenInstall.com website proves to be an act of futility as the site is no longer online. This downed website comes despite the fact that some download locations for the Winzip software still indicate that “By clicking download, you agree to the OpenInstall EULA and Privacy Policy”. Those EULA and Privacy Policy links attempt to direct users to the OpenInstall.com website.
A bit more research into the company turns up this filing with the S.E.C. which indicates that security vendor AVG acquired OpenInstall in January 2012.
I think we can all agree that reputable companies such as Winzip and AVG are not performing activities on computers which would be deemed malicious, but it’s hard not to ignore the fact that the OpenInstall product does write files to the computer (OI related files) and that in at least some cases, a means to opt-out is not provided, and yet that in even more cases, there is not a valid EULA.
As if all the above information isn’t confusing enough, the data produced by the Webroot Security Intelligence Network reveals some interesting information regarding files related to OpenInstall. We would like to highlight some file characteristics which most people won’t have the ability to see on a large scale, but from a Malware Research perspective seem quite suspicious.
In the below view, we have grouped together a partial listing of the OpenInstall files. The following files all share the same internal data-points, meaning they are all files that share a similar code-base. None of the files have ever been seen on more than 1 PC. We have columns for: File Name, Vendor (from the file properties tab), Product Description, Version, and Digital Vendor. Take note of some of the included entries. Several of the files have file names relating to one product, Vendors relating to other products, and then Digital Vendors relating to something totally different. Our Intelligence Network has identified thousands of similar files. Even people who don’t spend their days researching malware must acknowledge that conflicting Filenames, Vendors and Digital Vendors should be a characteristic that stands out as not being normal.

Being presented with all this varying and sometimes conflicting information, what type of determination should a Malware Analysis take on this type of software? At least in some cases, users have no option to opt-out. If they can’t opt-out, users face changes to their search provider as well as a home page reset. The software in question has a dubious reputation among members of the Anti-Malware community, and some of our competitors have detections for this software. From an analysis perspective, we see some interesting (to say the least) aspects with the topical information of files. Search results for the written files (OIAssistWTD.exe) indicate OpenInstall as the owner, yet there is no website information for OpenInstall, and thus no available EULA under that name. It takes a good bit of research to uncover the fact that the OI related files are now owned by AVG.
Considering all of this, how do we not consider the software in question to be Potentially Unwanted?
Maybe others will have a different view. We’re more than willing to entertain a discussion on this topic. If you have a different opinion or viewpoint regarding this issue, we would be more than happy to hear it. Leave your thoughts in the comments section below and we will be sure to read them.
Fake ‘iPhone Picture Snapshot Message’ themed emails lead to malware
We’ve just intercepted a currently circulating malicious spam campaign that’s attempting to trick iPhone owners into thinking that they’ve received a ‘picture snapshot message’. Once users execute the malicious attachment, their PCs automatically join the botnet operated by the cybercriminal/gang of cybercriminals, whose activities we’ve been closely monitoring over the last couple of months.
More details:
New ‘Hacked shells as a service’ empowers cybercriminals with access to high page rank-ed Web sites
Whether it’s abusing the ‘Long Tail’ of the Web by systematically and efficiently exploiting tens of thousands of legitimate Web sites, or the quest to compromise few, but high-trafficked, high page rank empowered Web sites, compromised shell accounts are an inseparable part of the cybercrime ecosystem.
Aiming to fill in a niche in the market segment for compromised/hacked shells, a newly launched service is offering a self-service type of underground market proposition, whose inventory is currently listing over 6000 compromised/hacked shells internationally.
More details:
‘Malware-infected hosts as stepping stones’ service offers access to hundreds of compromised U.S based hosts
Malware-infected hosts with clean IP reputation have always been a desirable underground market item. On the majority of occasions, they will either be abused as distribution/infection vector, used as cash cows, or as ‘stepping stones’, risk-forwarding the responsibility, and distorting the attribution process, as well as adding an additional OPSEC (Operational Security) layer to the campaign of the malicious attacker.
A newly launched ‘malware-infected hosts as stepping stones’ service, is offering access to Socks5-enabled malware hosts, located primarily in the United States, allowing virtually anyone to route their fraudulent/malicious traffic through these hosts.
More details:
DIY commercially-available ‘automatic Web site hacking as a service’ spotted in the wild
A newly launched underground market service, aims to automate the unethical penetration testing process, by empowering virtually all of its (paying) customers with what they claim is ‘private exploitation techniques’ capable of compromising any Web site.
More details:
Custom USB sticks bypassing Windows 7/8’s AutoRun protection measure going mainstream
When Microsoft disabled AutoRun on XP and Vista back in February, 2011, everyone thought this was game over for the bad guys who were abusing the removable media distribution/infection vector in particular. However, pragmatic and market demand-driven opportunistic cybercrime-friendly vendors quickly realized that this has opened up a new business opportunity, that is, if they ever manage to find a way to bypass Microsoft’s AutoRun protection measures.
Apparently, they seem to have a found a way to bypass the protection measure by tricking Windows into thinking that the connected USB memory stick is actually a ‘Human Interface Device’ (keyboard for instance), allowing them to (physically) execute custom scripts within 30/40 seconds of connecting the custom USB memory stick to the targeted PC.
From theory into practice, let’s profile their international underground market propositions and discuss the impact these USB sticks could have in today’s bring your own device (BYOD) corporate environment.
More details:
How much does it cost to buy one thousand Russian/Eastern European based malware-infected hosts?
By Dancho Danchev
For years, many of the primary and market-share leading ‘malware-infected hosts as a service’ providers have become used to selling exclusive access to hosts from virtually the entire World, excluding the sale and actual infection of Russian and Eastern European based hosts. This sociocultural trend was then disrupted by the Carberp gang, which started targeting Russian and Eastern European users, demonstrating that greed knows no boundaries and which ultimately led Russian and Ukrainian law enforcement to the group.
What’s the probability that Russian/Eastern European cybercriminals will continue targeting their own fellow citizens in an attempt to monetize the access to their PCs in the most efficient and profitable way possible? Huge.
In this post, I’ll profile a recently launched ‘malware-infected hosts as a service’ type of underground market service proposition selling access to Eastern European based hosts, discuss the pricing scheme used, as well as emphasize on the long-term perspective of these services. All during a time where novice cybercriminals have access to sophisticated DIY (do it yourself) malware generating tools.
More details:
Rogue ads lead to the ‘Free Player’ Win32/Somoto Potentially Unwanted Application (PUA)
Remember the Win32/Somoto.BetterInstaller Potentially Unwanted Application (PUA)? We’ve just intercepted the latest rogue ad-campaign launched by a participant in their affiliate network, potentially exposing socially engineered users to privacy-invading risks without their knowledge.
More details:
Fake ‘Copy of Vodafone U.K Contract/Your Monthly Vodafone Bill is Ready/New MMS Received’ themed emails lead to malware
Cybercriminals continue targeting U.K based Internet users in an attempt to trick them into thinking that they’ve received a legitimate email from Vodafone U.K. We’ve intercepted two, currently circulating, malicious spam campaign that once again impersonate Vodafone U.K, this time relying on a bogus “Copy of Vodafone U.K” themed messages, the ubiquitous ‘MMS Message Received‘ campaign, as well as the most recent ‘Your Monthly Vondafone Bill is Ready‘ theme.
More details:









