Malware authors must have a soft spot in their hearts for the long-maligned South African vuvuzela, because once again, the most annoying noisemaker in World Cup history is driving people to Web sites which push infections down to their computers. This time, people are retweeting the malicious links attached to a message that reads “OMG! Vuvuzela banned!” along with the hashtags #worldcup and #vuvuzelabanned. At last check in Google, references to the malicious links number over 16,000.
Malware authors must have a soft spot in their hearts for the long-maligned South African vuvuzela, because once again, the most annoying noisemaker in World Cup history is driving people to Web sites which push infections down to their computers. This time, people are retweeting the malicious links attached to a message that reads “OMG! Vuvuzela banned!” along with the hashtags #worldcup and #vuvuzelabanned. At last check in Google, references to the malicious links number over 16,000.
The tweets use a variety of different link shortening services (including bit.ly, tinyurl.com, is.gd, and dr.tl) to mask the fact that their destination is actually a bogus image hosting website hosted on the .in top-level domain (supposedly used by Web sites registered in the country of India, but these sites are all hosted elsewhere). The Web site you eventually land on calls itself Image Sheep, while in the background, your PC is being herded into a botnet.
As an aside, there is a real image hosting service by the same name, but the real Image Sheep is registered elsewhere and hosted in an entirely different network than these fake Image Sheep clones.
Once the victim’s browser loads the fake Image Sheep page, it pushes a Java “image viewer” applet, named target.jar, down to the browser. It’s easy to pick apart the contents of this file, which contains additional Java applets and PHP scripts that push the malicious file (named IMG12523.jpg.exe) down to the victim’s computer. The file itself is a downloader component of an adversary we’ve seen before: Trojan-Backdoor-Protard (aka Gootkit), which retrieves additional malware and retrieves complex instructions.
As we’ve seen in our earlier Protard infections, the malware distributors behind Protard write small, simplistic malware executables, and use complex Web based scripting as instructions, to control the malware’s behavior. That seems to be the case in this instance, as well.
Once executed, the initial payload begins a process where it downloads several payloads, including the pernicious adware known as Virtumonde, from bts.microsoftupdateserver.org, a site hosted in Russia. Some of those payloads are downloaders, as well.
The file then receives batches of 25 stolen credentials, in the forms of email addresses and passwords, from the command and control server…
…and with those credentials, the tool begins to attempt to log into Twitter, MySpace, and Facebook, methodically testing each email/password combination to see if it successfully logs into the service, as shown in this screen taken from a packet capturing tool.
This behavior is similar to how the spy tested stolen FTP credentials the last time we looked at it.
The JAR file that’s used to draw down the initial infection also contains scripting that adds an entry with details about the victim’s computer into a MySQL database running on the malicious web server. Looking at the SQL commands in use in the script, it’s clear the malware distributors are closely monitoring the effectiveness of the infection: It’s reporting back the number of infected users, the rate at which people infect themselves, and the clicks to various parts of the page.
Oh yeah, and this is where the plain old ‘tard meets the Protard: They’ve left their SQL server root password blank. Thanks, fellas.
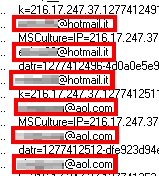
That’s important because, at last check, the malware distributors have registered only a small number of sites, but are using lots of different shortened URLs to link to those sites.
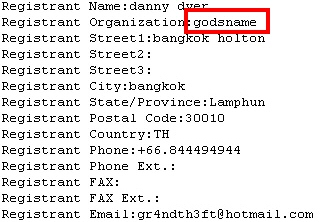
In addition, the WHOIS information for the domains used to host the fake Image Sheep pages all reference the word godsname as the Registrant Organization.
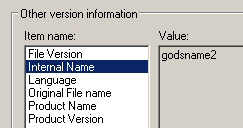
The Protard malware file’s properties refer to the Product Name of the malware as godsname2, which probably isn’t a coincidence.
Bottom line, don’t click the malicious shortlinks in these tweets, and make sure your browser and the Java plug-in installed on your computer are both up to date. We’re blocking the domains involved in the attack, and our customers can expect that we’ll have added detections for the malware to our next definition release.