 Bootlegged copies of Civilization 5, the highly anticipated, just-released real time strategy game, are already popping up in file sharing services. And, as we’ve come to expect, some of the pirated copies of the game come with that little something special — malicious components.
Bootlegged copies of Civilization 5, the highly anticipated, just-released real time strategy game, are already popping up in file sharing services. And, as we’ve come to expect, some of the pirated copies of the game come with that little something special — malicious components.
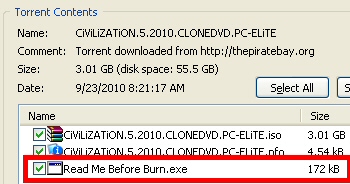
One of our Threat Research Analysts, who also happens to be an avid gamer, started looking for pirated copies of the game Friday morning and, within five minutes of looking, found Trojans in some of the torrents in circulation. I’ve chosen to focus on one of these files, not only because it was the first we saw, but also the most interesting. The Trojan, bundled in a torrent with the ISO image of the Civ 5 installation disc, is called ‘read me before burn.exe‘ (MD5: 2f7ff2ecef4b5cf1c9679f79d9b72518).
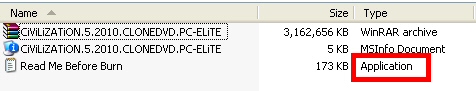
On a typical Windows system, the file appears to be a text document, but only because it uses a file icon of a text document. With the file extension visible, however, it’s clearly an .exe with a mission.
The file, a dropper, is interesting for other reasons as well. As of last night, there were no detections for the file on Virustotal, which means other antivirus companies hadn’t yet pulled it into their systems.
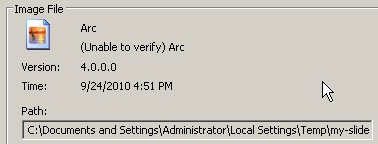
The ‘read me’ dropper drops a program named ‘my-slide-show-picture.exe‘ (MD5: 6cf871199432f0dd9a669427f58155db) into the currently-logged-in-user’s Application DataMicrosoft folder, writes a run key to start up slide-show at reboot (with the value window update), then quits.
Here’s the interesting part: Every time slide-show executes, it writes the entire source code for another payload — a password stealer — onto the infected computer. Slide-show then compiles this dropped source code, using the Visual Basic Compiler,into a program with an eight-random-character filename that’s exactly 136192 bytes in size. This happens every time the computer executes slide-show — upon the initial execution and at every reboot. This breaks AV detection of the compiled payload that relies on a static MD5 hash.
Now for the Stupid Malware Tricks part: When slide-show writes out its source code, which is all embedded in slide-show as base64-encoded text, anyone can read it all. That means we, the malware analysts of the world, can see the full functionality of the program without needing to actually do anything more than open it in a text editor.
The original source appears to have been written by someone who is a native French speaker, because it is heavily commented in French, which is actually quite informative. This helpful malware author, whose name is apparently Albert, tipped us off to useful hints about what he did, with comments like mot de passe (password) and ecrivant un compte MSN Messenger (write out the MSN Messenger account) sprinkled throughout.
For too long, I thought my study of French in college would yield no useful purpose in my malware analysis day job. Thanks, Al, for making it all worthwhile.
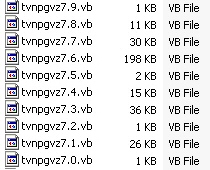
We also can see that the password stealer component is built out of nine separate components, each of which adds different functionality to the end product. Among the functionality is the ability of the program to steal passwords for MSN messenger, stored passwords in the Protected Storage area of Windows, passwords saved to Mozilla Firefox’s password storage, and elsewhere. The file concatenates any stolen information and holds it in anticipation of being able to upload it to the file’s command and control server, which is assigned to two subdomains managed through the No-IP dynamic DNS service. As I write this, the IP address where the payload attempts to communicate is offline, and the account’s been shut down.
We’ve added detection for ‘slide-show’ as well as ‘read me’ to our definitions. What remains to be seen is whether would-be pirates will be dissuaded from bootlegging copies of the game, or if Albert here still ended up with a boatload of stolen credentials. I guess we’ll find out next week.





















Using .NET to write viruses = FAIL 🙂
I accidentally opened that what seems to be txt file in my laptop, is there a solution to get rid of this?
My Kaspersky Internet Security 2010 haven’t detected it yet as of now.
If you open Task Manager and see the same program names of the malware as described in this post, simply kill the process, then delete the files.
That’s why you should make extensions in your file manager visible (they are by default in Total Commander)
I never ever fooled by this in my life.
hi, dude…it’s kinda embarassing to admit it, but I’ve also executed this file (by accident)…the thing is, I’ve executed it as a notepad application. The funny (and sad) thing is: now, all of my applications are being executed as notepad files (and thats really annoying!). I’ve tried to call the process of file by opening the Task Manager but there are no process there! what do I do??
The game itself comes with malware even if you buy it legally spyware.marketscore and Malware.Gen flagged by Malwarebytes
I love civilization 5!