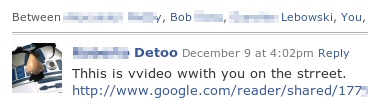
A new variant of the Koobface social networking worm is sending social networkers links that lead to fake videos supposedly posted by the beloved cartoon antihero Spongebob Squarepants. The fake videos only display a popup message labeled “Adobe Flash Player Update” that says “This content requires Adobe Flash Player 10.37. Would you like to install it now?” Clicking anywhere on the page downloads the Koobface installer to the victim’s PC.
A new variant of the Koobface social networking worm is sending social networkers links that lead to fake videos supposedly posted by the beloved cartoon antihero Spongebob Squarepants. The fake videos only display a popup message labeled “Adobe Flash Player Update” that says “This content requires Adobe Flash Player 10.37. Would you like to install it now?” Clicking anywhere on the page downloads the Koobface installer to the victim’s PC.
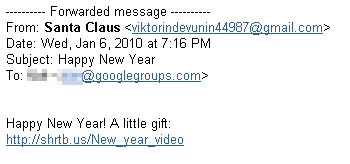
The technique isn’t new, but this is the first sign that the crew behind Koobface is switching from ‘holiday mode’ (when they sent around links to videos that were supposedly posted by Santa Claus) to ‘post-holiday mode.’
 In other ways, the worm features a few small tweaks: Its Captcha tool, which attempts to convince infected users to enter the text of a captcha into a dialog box, has been modified to read and properly display the new ReCaptcha format used by some social network sites. The new format randomly places black circles ‘behind’ the text, and inverts the text of the captcha phrase where the text and black circles intersect.
In other ways, the worm features a few small tweaks: Its Captcha tool, which attempts to convince infected users to enter the text of a captcha into a dialog box, has been modified to read and properly display the new ReCaptcha format used by some social network sites. The new format randomly places black circles ‘behind’ the text, and inverts the text of the captcha phrase where the text and black circles intersect.