Helping Organisations Stay Secure In An Unsecure Age
Seemingly every day, we’re reminded that companies need to work harder to stay secure during a time where cybercrime is rampant and many organizations remain vulnerable to attack. I’ve recently been speaking to the press about what can and should be done to mitigate these risks. I hope the following questions and answers will help shed some light on some key problems many organizations face, and help you decide what’s best for your business.
What happens if an organization focuses too much on the technology aspect of security and not enough on people and process?
Unfortunately, an organization is only as strong as its weakest link – and in terms of security, employees are by far the weakest link.
Technology plays an essential role in any defense, but at the same time technologies cannot stop an employee giving their details out over the phone to someone they believe is from the IT department. And it cannot stop an employee using their corporate password for on their favorite social media sites or writing down their hard to remember passwords.
Relying purely on technology as an organization’s only form of defense is extremely short-sighted; failure is inevitable.
How often are companies attacked because of a vulnerability caused by employees or company processes?
It’s hard to put an exact number this. But from experience, I would suggest it’s a very high percentage. Why wouldn’t it be? Cybercriminals spend so much time, effort and money defeating a technology or defense when employees are such an easy target.
In terms of hackers getting in, the most common issues are misuse of social networking, weak passwords and password re-use, privilege creeping, malware and lack of system patching. But the real danger is employees being unaware of internal security policies or the ones that unfortunately do not care enough and are careless and complacent.
How can CIOs and CISOs go about strengthening their strategy around people and process to ensure cyberattacks aren’t successful?
There’s no magic wand. There’s an infinite number of initiatives that can be introduced to help mitigate risk, all at differing costs and complexity. In simple terms, it’s about completing comprehensive risk assessments, creating policies and understanding industry best practices, evaluating possible technologies, and then, implementing a solution. More than anything, the plan needs buy-in at all levels and needs an appropriate budget.
Training should always be at the heart of an organization’s security program as technology alone will not stand up against a motivated attacker. Everyone within the organization should be made responsible for the security of its assets.
It’s also vital that personnel understand the technologies they are asked to manage and monitor. The intelligence gathered by security systems needs to be understood, so when an attack occurs, it is detected at the first possible opportunity with the correct processes and procedures, then followed.
How can CIOs and CISOs approach internal training and education in regard to security?
Employee involvement is crucial for the success of an organization’s security strategy. Creating a security task force whose members rotate so each employee has eventually been part of the task force is a great way to get everyone involved. Each task force could have a ‘security champion’, who would be the person who identifies the most beneficial improvement to current security processes. This system encourages employees to think actively as well as creatively about security to improve the company’s security.
There is often a disconnect between what employees know they should do security-wise, versus what they actually do in practice. This is one of the most challenging parts of cybersecurity training and education. In these cases, businesses need to make sure it is clearly explained what is prohibited and why – using real world examples of the repercussions of not following procedure. What might seem harmless to an employee, like using an unsecure WiFi network, could cause a business serious problems further down the line.
There’s no point just preaching security, it should be made fun. It’s also important to understand if the information given has been taken in. This is where regular security tests play a vital role. Bad security practices should not be tolerated if appropriate training and guidance has been given. At the same time good security practices should be rewarded.
Can you provide an example of an organization that suffered a major cyberattack because their people and process strategy was not up to scratch?
The breach at Target Corp in late 2013 springs to mind for a number of reasons. It is understood the attack initiated at a third party vendor, an air conditioning subcontractor through a phishing email. User education with regards to the opening of emails may have been able to stop such an attack from escalating.
An assessment by security experts at Verizon noted that while Target had a password policy, it was not followed. A file containing valid network credentials was found stored on several servers, with weak or default passwords used on many internal systems.
It was also reported that many systems were found to be unpatched, something a patch management policy should have covered even after Target’s security systems warned of possible issues. No credible incident response plan was in place, as a Target statement at the time highlighted that after the company learned criminals had entered the network, the team decided it did not warrant immediate follow-up.
Do you expect to see people and process strategies around security improving this year?
Security is finally climbing up organizations’ agendas, so hopefully improvements around people and processes will continue to be made.
Communications and information flow between the organization and its employees is vital – the risks and potential consequences need to be understood by employees through continued user education. It’s arguably the most cost effective approach to improving the security posture of any organization.
However, cybercriminals only need to find one hole in the defense, whereas as security professionals, we have to secure all. It’s never going to be an easy task, but sound user education and relevant processes are now more important than ever and should never be underestimated.
What you need to know about the new KeRanger Ransomware.
Palo Alto Networks recently discovered ransomware hidden inside of the torrenting app ‘Transmission’. While this may come as a shock to those that still believe the Mac is a fortress that can’t be broken, the rest of us are not shocked at all. In fact, a few months back I wrote a blog warning Mac users not to dismiss Mac malware. It is time to take Mac security seriously. Apple does a great job for the most part, but in order to secure your information and your devices, you need a good Antivirus product.
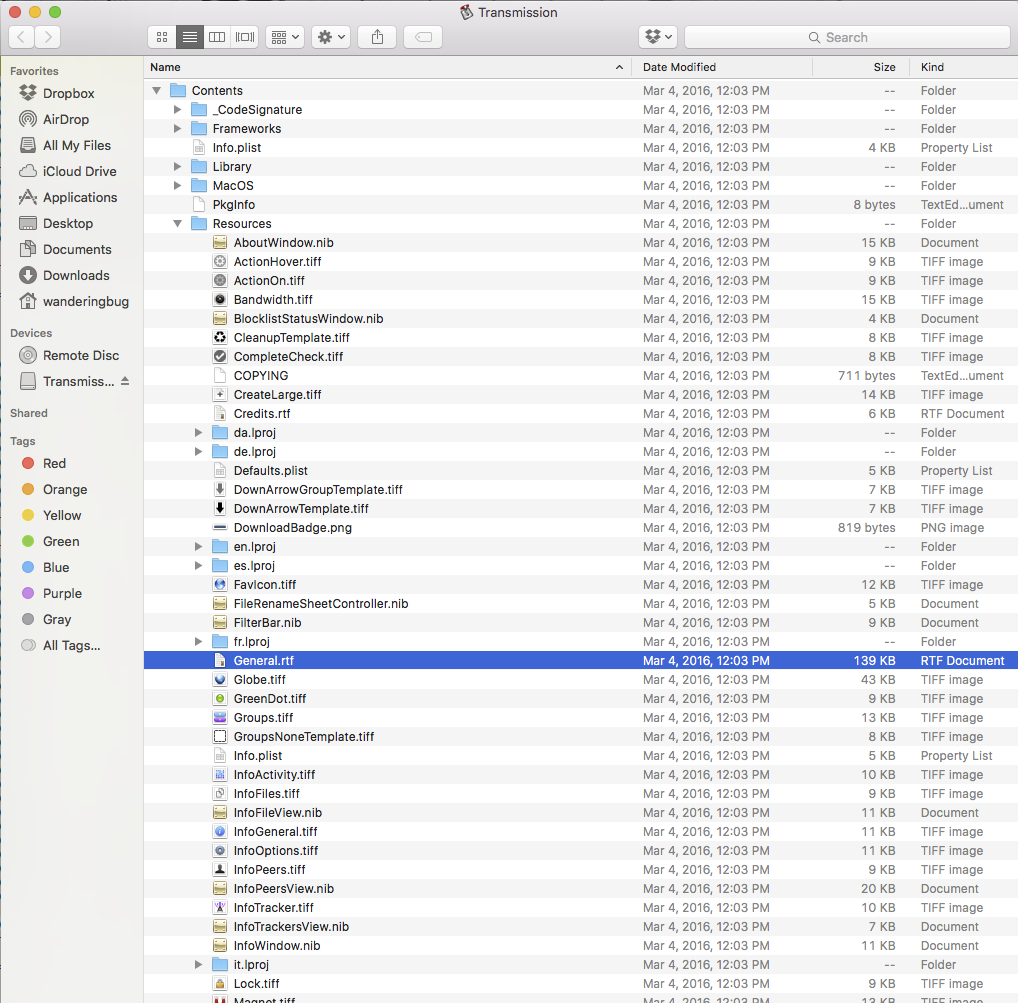
Back to the threat at hand. This ransomware is bundled in with the Transmission Bittorrent client as a file called “General.rtf”. For most, this file looks like a simple real text file. However, it is actually a Mach-O 64-bit executable file that will execute three days after you run Transmission. This helps keep the ransomware hidden so that users wouldn’t suspect the app they are using for torrenting, but rather the torrents that they are pulling down as the source of infection.
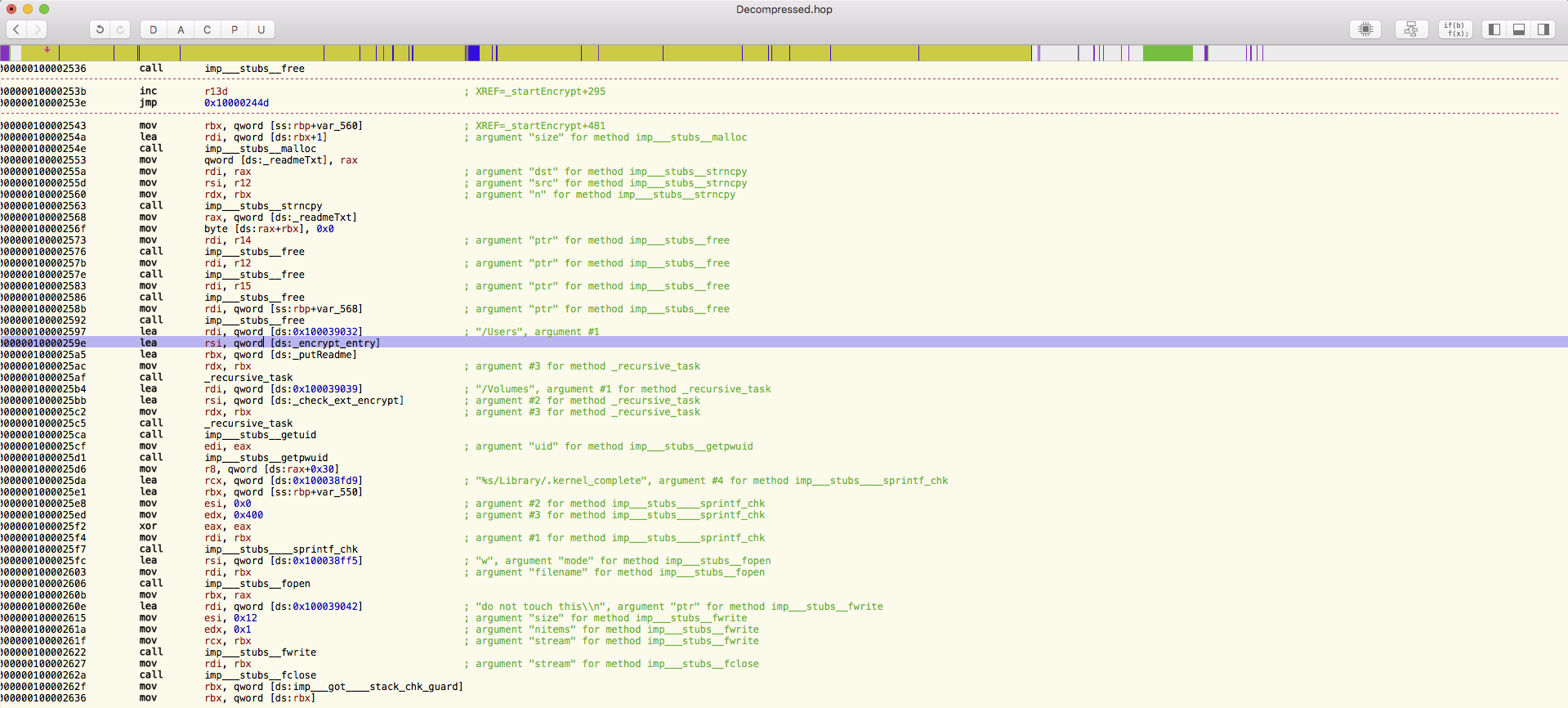
After the three days, the app executes and drops a file called “kernel_service” into the user’s library directory. This process is named in such a way so as to confuse anyone that looks in Activity Monitor into believing that it is a system process. It then drops three more files in the user’s library: “.kernel_pid”, “.kernel_time” and “.kernel_complete”. It will collect the infected Mac’s model name and UUID then upload the information to one of its Command and Control servers.
These servers will respond with a file named “README_FOR_DECRYPT.txt”, in which it explains how to get the key for decryption and the price for the key in bitcoins. The ransomware is able encrypt around 300 different types of file extensions that it finds in the “/Users/” directory and changes the file extension to end in “.encrypted”. This means that the family pictures that you keep on your Mac will now be labeled “GrandCanyon2010.jpg.encrypted” and cannot be opened.
One of the most important things to note is that the program is still a work in progress. There are many functions that have been found in the code that are not currently being used, like the ability to encrypt your Time Machine backup as well. This of course is the second wall of defense for many people, who believe that because they have a Time Machine backup, they can always just roll back their Mac if something happens.
To add some more context into the expansion of ransomware into the Mac OS, our David Kennerley recently commented in Global Security Mag:
“Given the potential gains for attackers, it’s no surprise that they are now diversifying and targeting OS X – a popular system with a large target base. Add to this the fact that many people believe they are safe from such malware when running OS X, this ransomware has the potential to impact a huge number of people.”
You can locate the full article here.
I’ve said it before and I will say it again: Mac malware is real. Don’t be an Apple user that finds this out the hard way.
Webroot Supports Open Network Insight Project
On Monday of this week, Webroot joined Cloudera, the leading provider of modern data management and analytics systems built on Apache Hadoop, in announcing Open Network Insight (ONI) Project, a database and tools designed specifically for cyber security incident response. ONI will enable security analysts and responders to manipulate the massive amounts of data generated within an enterprise to isolate and investigate both internal and external threats. And because we have years of endpoint-to-cloud experience here at Webroot, we will participate in the project by helping to design the data models for endpoint data.
ONI matches our own Webroot vision of security being an information problem. If you can apply the right data at the right time to decide if you’re being attacked or infiltrated, you can defend yourself. Our SecureAnywhere products put this vision into action by applying massive threat intelligence in the cloud to defeat potential threats on our customers’ desktops and smartphones. ONI will enable an organization to bring together all the relevant data about their network, their users, and their devices in one massive, but easily manipulated database, so they can find and defeat attacks.
Hadoop has been growing rapidly in popularity within the cyber security community, being used in building very large-scale databases of security intelligence data such as network logs, event data, and other data types needed by security analysts. Hadoop combines power, speed, and flexibility, which are the hallmarks of a good data platform. Cloudera has extended the open source base with Cloudera Enterprise, a portfolio of tools to create, manage and analyze large scale databases.
The initial prototype of ONI was created by data scientists at Intel. They created a database which is updated with more than 20 billion network events per day within the Intel corporate network. Then, using proprietary and open source visualization tools, they created a security workbench which allows them to identify and investigate potential threats.
Webroot is excited to be part of Open Network Insight, and excited to be working with Cloudera and Intel to bring this vision to reality. We will update the Blog with our progress.
Threat Recap Week of March 4th
German Hospitals Latest Ransomware Target
In the past week, several German hospitals have reported ransomware attacks on their internal systems. While one of the hospitals was able to minimize the damage by isolating the infected server, Lukas Hospital wasn’t as fortunate, as their system had been encrypted before they could react properly. Fortunately, the hospitals in question were able to restore the lost data using backups that are performed regularly.
https://www.helpnetsecurity.com/2016/02/26/crypto-ransomware-hits-german-hospitals/
China Accused of Hacking Norwegian Companies
Recently, the head of Norwegian Intelligence came out to publicly accuse China/Chinese hackers of accessing highly valuable military information. This accusation is based upon the methodology typically used by Chinese hackers and the evidence showing geolocation of IP addresses, the language used in the coding, and the types of malware that were used. Currently, it is thought that the vulnerability was a targeted spear-phishing attack on several companies, though no official source has confirmed it.
DROWN Attacks Leave HTTPS Servers Defenseless
Researchers have recently discovered a new method for man-in-the-middle attacks between clients and an SSLv2 server, which is no longer up-to-date, but also still widely used. Unfortunately for end users, there is little that can be done if the system admins haven’t ensured the vulnerability is resolved, though discontinuing use of SSLv2 would eliminate this type of threat completely.
Software Updates, The Backdoor To Your System
Every computer runs system or software updates, often without the express consent of the user, but this could have unexpected results. With the proper access to push the update and a way to make it appear authentic, an attacker could send malicious content while seeming to pose no threat to the system. While nearly every operating system has this type of failure point, more and more developers are working towards ensuring updates are only done when they are properly signed.
Wendy’s Breach Affecting Financial Insitutions
It was recently found that several Wendy’s locations had been targeted by a point-of-sale malware attack, used to steal customer credit card information. The breach has been larger in scale than previous attacks, and it appears the money being drained from the accounts is in significantly higher amounts. It is currently unknown how many locations have been affected, but it’s likely to be the stores that are using the older card-swipe method over the improved chip-card reader.
http://krebsonsecurity.com/2016/03/credit-unions-feeling-pinch-in-wendys-breach/
Threat Insights and Trends from the 2016 Threat Brief
Intro from the 2016 Threat Brief:
“2015 was yet another record year for cybercrime, during which more malware, malicious IPs, websites, and mobile apps were discovered than in any previous year. It comes as no surprise that the cybercrime ecosystem continues to thrive, given new innovations and little in the way of risk for those who choose to participate. The continued onslaught of hacks, breaches, and social engineering scams targeting individuals, businesses, and government agencies alike has caused many in the security field to ask if it’s truly possible to defend against a persistent attacker.
…
At Webroot, we believe it is possible to effectively protect enterprises and users, but only by understanding your adversary and the techniques they employ for their attacks.
…
Our approach and security solutions reflect our in-depth understanding of the threat landscape and how attackers think, to provide cutting-edge, proven next-generation protection and real-time detection of threats as they emerge. The Webroot 2016 Threat Brief provides a glimpse into the analysis and discoveries made by the Webroot® Threat Intelligence Platform to provide insights on key trends and risks seen by our users over the past year.”
The brief in its entirety can be found here.
However, in this blog, I want to talk about two sections of the Threat Brief and what I found to be most interesting. The first has to do with new malware discoveries and how often malware ensures it is unique with each new infection. The other has to do with the prevalence and targets of phishing attacks, as well as a tactic to improve your personal online security.
Before I go on, it is first important to talk about the source of this data. With respect to malware and phishing site encounters, these stats are pulled directly from Webroot SecureAnywhere users and their real world encounters with these threats. This is an important distinction as it enables us to calculate how frequently different types of attacks occur and the likeliness that an average user encounters such an attack.
Let’s begin with what was interesting in the malware detection data, mainly the fact that around 97% of the time, malware is unique to the system it infects. That is to say that the specific malicious file is never seen elsewhere. This is intentionally done by malware authors and distributors to make the discovery of their threats more difficult. The technology behind this technique is not new however, and is known as polymorphism. The overwhelming trend is that malware uses polymorphism, either on the server side where the malware is distributed from, or through the malware itself where with each new infection, the samples change. While polymorphic malware has been around for over a decade, it is now the norm for nearly all threats today.
Beyond the polymorphic trend, malware encounter data also showed that Webroot SecureAnywhere users encountered more threats on average than in 2014. The per-user infection rate in 2015 was 1.6 infections per customer, compared to 1.2 in 2014. What this means is that infections are more common and during the course of a year, you will more than likely be exposed to a threat. The good news for Webroot customers is that we’ve protected you from these threats. That said, our users were 25% more likely to encounter threats in 2015 than in 2014.
The last bit I want to talk about with respect to malware, is the speed at which churn between variants occurs. We measure this by counting the number of examples per variant that are discovered, on average, before no new samples show up and a new variant is discovered. In 2015, this number plummeted to 97 examples per variant compared to 2014 where nearly 700 examples were discovered. Ultimately, what this shows is that malware authors and distributors are speeding up their variant release process in their efforts to evade detection. Thankfully, the Webroot model for threat discovery isn’t affected by the speed of new malware development, and instead relies on awareness at each individual endpoint we protect. This ensures that even if the samples per variant drops to one, we are still aware of that individual threat and are able to identify and protect against the infection.
The second threat type I want to talk about is the notorious phishing attack. These are malicious websites that impersonate legitimate websites as they look to steal login credentials and more. The vast majority of phishing URL’s show up in carefully crafted emails that use social engineering techniques to encourage some call to action. A common example is an email claiming your account has been suspended and to log in to restore access.
In 2015, over 4 million phishing URL’s were clicked on by Webroot SecureAnywhere users. The good news is that none of these users had the chance to give away their credentials as SecureAnywhere blocked the URL’s page from loading. The bad news is that that the volume of phishing URL’s has increased considerably over 2014. In 2015, about 50% of WSA users clicked on a phishing URL compared to 30% in 2014. There are a number of factors that are responsible for this increase, but the two main ones are that phishing sites are inexpensive to host and that they are an effective method for collecting credentials. In so long as people can be tricked into clicking on a malicious link, phishing sites aren’t going anywhere.
The other interesting data around phishing site detection surrounds correlating the phishing site to the company or entity that is being impersonated. In the Threat Brief, we break them into two main categories which are financial institutions and technology companies. When looking at all phishing sites discovered in 2015, a little more than 2/3 of sites were targeting a technology company such as Google or Apple. This might sound odd as you might think that breaking into someone’s bank account would be more valuable. However, quite the opposite is true. Google is by far the number one target of phishing attacks because the value of breaking into someone’s primary email account is very high. The reason is that an email account provides information about what other accounts an individual has (including financial accounts), as well as the ability to reset those accounts’ passwords as the password reset option validates through the associated email address.
This brings me to my final point, which is less about phishing and more about email security. The number one tip I recommend to help improve personal online security is to make sure your primary email account password is unique from all other passwords. This ensures that your email is difficult to break into when a password for another site is compromised. This happens all-too-often by no fault of a user, but rather because businesses are often attacked and credential data is compromised. The first thing hackers do with stolen credential data is to see what other accounts can be accessed. If your email password is unique, there is no chance of it being compromised through a collateral attack.
There are many other interesting observations in the full 2016 Threat Brief, and I encourage you to read the full report.
Threat Recap: Week of Feb. 22
A lot happens in the security world and many stories get lost in the mix. In an effort to keep our readers informed and updated, we present the Webroot Threat Recap, highlighting 5 major security news stories of the week.
Linux Distro Compromised
This week, one of the largest Linux distro’s for Mint was targeted by hackers, who were able to successfully alter a PHP script to allow redirection to a Bulgarian-based IP. Additionally, it has been confirmed that usernames and passwords from the Mint forum database have been compromised as well. Fortunately, for most Mint users, you would have needed to install Mint 17.3 in the past week to actually have a chance of becoming infected.
Read more: https://nakedsecurity.sophos.com/2016/02/22/worlds-biggest-linux-distro-infected-with-malware/
Phishing Still A Major Issue for Companies
Spear phishing attacks continue to be on the rise, but it is still surprising how many companies are successfully attacked annually. The main cause for the success of these attacks is the human component: employees, consumers, and management. Using a more precise version of spear phishing, known as BEC or Business Email Compromise, attackers are able to spoof a high-level employee’s email account and request highly sensitive information without much questioning.
Child Tracker Database Exposed
Recently, an independent researcher uncovered a database owned by uKnowKids (a company that provides child monitoring software). Within the information that was accessible online were over 1,700 profiles of children, and many millions of private messages. The researcher was able to contact uKnowKids and inform them of the vulnerability quickly, although it is still unknown how long it was available to the public.
Read more: https://www.helpnetsecurity.com/2016/02/23/sensitive-child-profiles-private-messages-exposed-online/
Nissan’s All-Electric Car Lacks Cloud Security
As electric cars continue their steady rise into the mainstream, it has become quite convenient to have an app that displays details about your car, and can even send basic commands. Unfortunately, this accessibility can come at a cost if it’s not well secured. Nissan’s Leaf has many of these features, including charging capabilites and climate control settings, but currently lacks any authentication, other than the username which is set as your car’s VIN. Without any further authentication, anyone with the app and the VIN can send commands to start/stop charging, or view any previous driving history.
Read more: https://nakedsecurity.sophos.com/2016/02/25/nissan-leaf-cloud-security-fail-leaves-drivers-exposed
Sony Hackers Likely Tied to S.E. Asian Attacks
When Sony Pictures was hacked in late 2014, many security companies were brought in to collaborate on discovering how, who, and when. Their research has brought to light a connection with North Korean nation-state hackers who also perpetrated attacks on South Korea and the US going as far back as 2009.
Read more: http://www.reuters.com/article/us-sony-cyber-idUSKCN0VX1IR
Cyber Threat Actors
Cyber threats come from a wide array of sources, but can be grouped into three categories:
Hacktivists
These are tech-savvy individuals who are normally motivated by morality. These individuals are also classed by many (including the FBI) as terrorists. One of the main hactivist groups out there is anonymous. This group rose from one of the most popular image boards on the internet, 4chan, where users could post anonymously. Many of the influential figures in 4chan have now left, including the board founder moot (Christopher Poole). 4chan is no longer the entity it used to be. One of the most infamous attacks conducted by anonymous was Project Chanology, where the group targeted scientology. Famously anonymous retrieved a video of Tom Cruise from the scientology group that was not intended to be seen by the general public: https://www.youtube.com/watch?v=UFBZ_uAbxS0
Cyber Criminals
These are individuals who are motivated by money. These are the people who are responsible for the distribution of ransomware. This is a very lucrative business. It was reported in 2013 that cryptolocker made over $30 million in 100 days. Politcal borders make it appealing for criminals to employ these tactics of making money as it is very hard to prosecute them. The encryption that ransomware hits these machines with is normally unbreakable, with the FBI encrouraging individuals to pay the ransom: http://uk.businessinsider.com/fbi-recommends-paying-ransom-for-infected-computer-2015-10?r=US&IR=T .
It has been observed that some ransomware variants have holes and can be cracked (most notably the linux encoder variant which was targeting web servers). Ransomware isn’t the only tactic cyber criminals employ. Another tactic they employ are botnets. This is where a criminal infects your computer, unknowingly to the individual. The criminal can then take control of the victims computer at any time for whatever purpose they see fit. Normally the attacker will either extract information from the victim, monitor the victim or use the victims computer to attack other systems. A recent case to note in relation to botnets is the arrest of one of the administrators of the Dridex botnet, Andrey Ghinkul. This arrest shows that law enforcement are making a good effort to tackle this problem.
State-Sponsored Threat Actors
These are individuals who are sponsored by a government. They act in political interest of the government sponsoring them. It has been reported by FireEye that China has over 20 APT (advanced persistent threat) groups. APT1 (dubbed by Mandiant) is linked with China’s PLA Unit 61398. It is believed this unit occupies a 12 story building employing hundreds of hackers. These groups pose a particular threat to the US, with the FBI putting some of the people involved on their most wanted list: https://www.fbi.gov/news/news_blog/five-chinese-military-hackers-charged-with-cyber-espionage-against-u.s . China isn’t the only country known for sponsoring cyber attacks. The revelations of Edward Snowden reveals much on the NSA’s antics. Another example of a state sponsored cyber attack is where Turkeys internet servers were attacked a couple of months ago, with the blame being pointed at Russia: http://www.todayszaman.com/anasayfa_political-hackers-suspected-as-turkey-suffers-intense-cyber-attack_407781.html
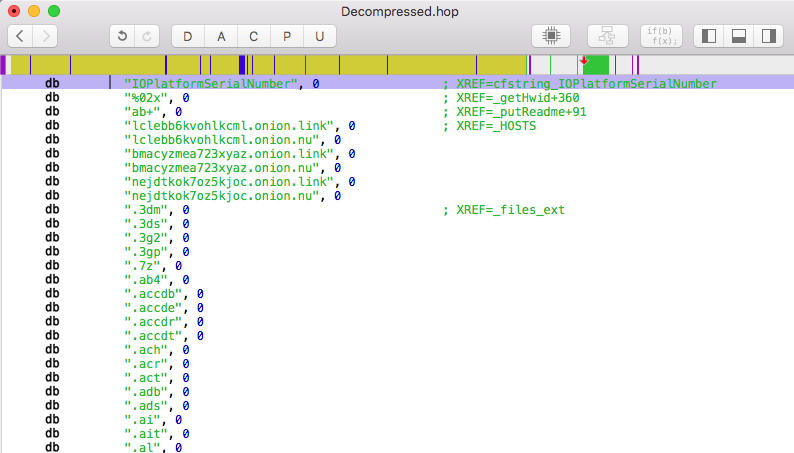
Locky Ransomware
A new form of ransomware has hit the scene, and although this one has a playful nickname it is no fun at all. The bad news is that “Locky” ransomware will encrypt virtually every commonly used file-type and targets not only local drives, but any networked drives it can find, even if they are unmapped. The good news is that Locky is easily preventable because it relies on MS Word Macros to download and execute the actual malware. The only way to infect a computer with Locky ransomware is to open the attached document from a spam e-mail and allow the Word Macro script to run. (For a general overview of this type of execution, see our blog post about Microsoft Word & Excel Macros.)
Locky is most commonly distributed through spam e-mails that have similar subjects and messages. The subject is typically something like “ATTN: Invoice J-123456748” and the message is usually “Please see the attached invoice (Microsoft Word Document) and remit payment according to the terms listed at the bottom of the invoice”. If the victim follows the instructions to enable Macros, the script will download the Locky payload from a remote server and execute it.
The Locky executable will be stored and run from the %Temp% folder and it will immediately create and assign a unique 16-character Hexadecimal name to the victim (something like “A8678FDE2634DB5F”) which is then sent to the remote server for tracking and identification purposes. Once the Locky executable has launched and assigned the victim a unique ID, it will immediately begin scanning drives for files to encrypt. Not only will it encrypt local files, but it will search for any remote drives it can find (even unmapped network shares) and will encrypt their files as well.
Locky will use the AES encryption algorithm to encrypt all files with the following extensions:
.mid, .wma, .flv, .mkv, .mov, .avi, .asf, .mpeg, .vob, .mpg, .wmv, .fla, .swf, .wav, .qcow2, .vdi, .vmdk, .vmx, .gpg, .aes, .ARC, .PAQ, .tar.bz2, .tbk, .bak, .tar, .tgz, .rar, .zip, .djv, .djvu, .svg, .bmp, .png, .gif, .raw, .cgm, .jpeg, .jpg, .tif, .tiff, .NEF, .psd, .cmd, .bat, .class, .jar, .java, .asp, .brd, .sch, .dch, .dip, .vbs, .asm, .pas, .cpp, .php, .ldf, .mdf, .ibd, .MYI, .MYD, .frm, .odb, .dbf, .mdb, .sql, .SQLITEDB, .SQLITE3, .asc, .lay6, .lay, .ms11 (Security copy), .sldm, .sldx, .ppsm, .ppsx, .ppam, .docb, .mml, .sxm, .otg, .odg, .uop, .potx, .potm, .pptx, .pptm, .std, .sxd, .pot, .pps, .sti, .sxi, .otp, .odp, .wks, .xltx, .xltm, .xlsx, .xlsm, .xlsb, .slk, .xlw, .xlt, .xlm, .xlc, .dif, .stc, .sxc, .ots, .ods, .hwp, .dotm, .dotx, .docm, .docx, .DOT, .max, .xml, .txt, .CSV, .uot, .RTF, .pdf, .XLS, .PPT, .stw, .sxw, .ott, .odt, .DOC, .pem, .csr, .crt, .key, wallet.dat
However, Locky will not encrypt any files where the full Pathname and Filename contain one of the following strings:
tmp, winnt, Application Data, AppData, Program Files (x86), Program Files, temp, thumbs.db, $Recycle.Bin, System Volume Information, Boot, Windows
Like the CryptoWall ransomware that has been seen in the past year, Locky also changes the names of the encrypted files in order to make it more difficult for victims to restore the correct data. Locky uses the naming format of “[unique_id][identifier].locky” for encrypted files. For example, if Locky assigns the victim a unique name of “A8678FDE2634DB5F” and it encrypts a file like “example.doc”, the file may be renamed something like “A8678FDE2634DB5F0123456789ABCDEF.locky” . In addition to obscuring the original file names, Locky takes the extra step of deleting all Shadow Volume copies on the machine in order to prevent the victim from simply rolling back or restoring their files.
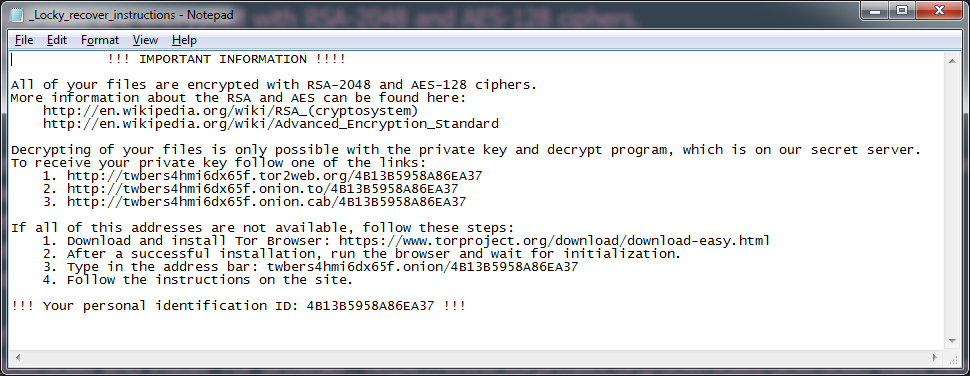
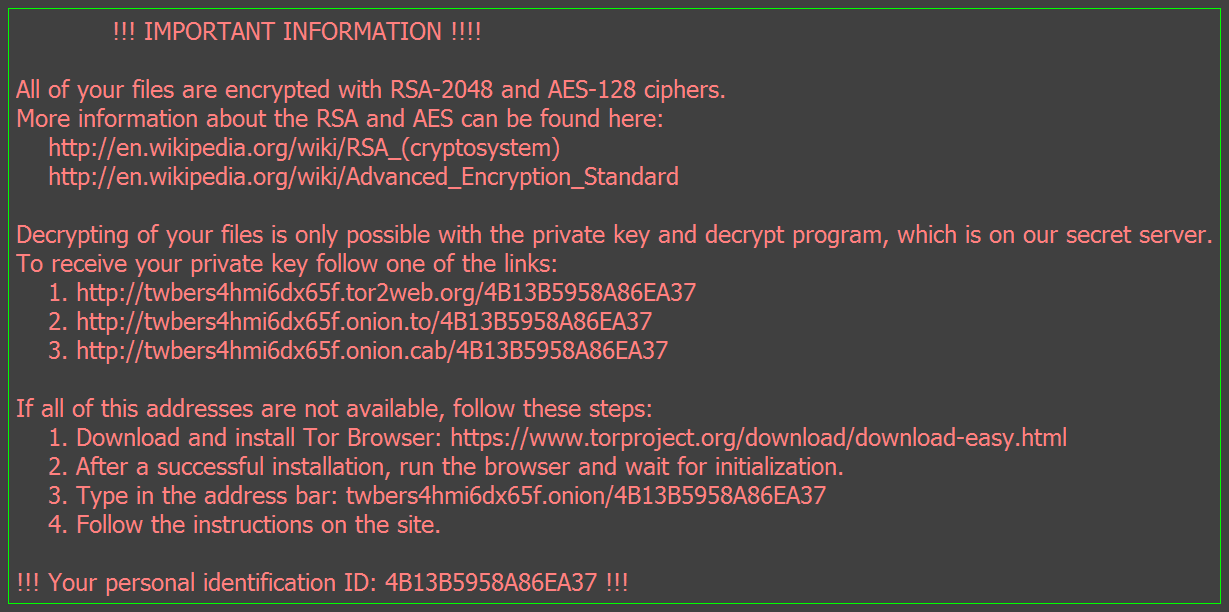
Since the main purpose of Locky is to coerce the victim into paying a ransom to retrieve/decrypt their data, Locky helpfully places recovery instructions in several places on the victim’s drive. Text files named “_Locky_recover_instructions.txt” will be dropped in every folder where files have been encrypted, and the Windows Wallpaper will be changed to “%UserpProfile%\Desktop\_Locky_recover_instructions.bmp”, which contains the same instructions as the text files.
The instructions that Locky provides contain links to a Tor site called the Locky Decrypter Page. The URL for this site is “6dtxgqam4crv6rr6.onion” , and it walks the the victim through the process of paying the ransom and retrieving their data. Details included: the amount of Bitcoins to send as payment, how to purchase Bitcoins, the Bitcoin address to submit payment, and a link to the Decrypter once payment is made.
Text Instructions
Desktop Background Instructions
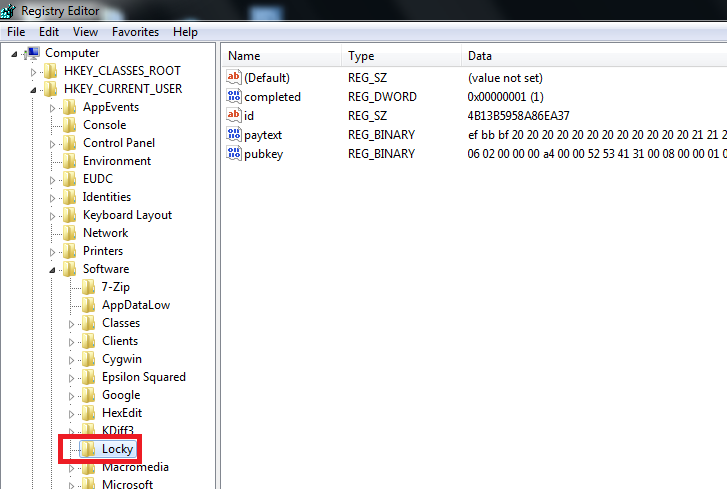
Locky will also store various information in the Windows Registry under these keys:
HKCU\Software\Locky\id – Unique ID assigned to the victim
HKCU\Software\Locky\pubkey – RSA Public Key
HKCU\Software\Locky\paytext – Ransom Note Text
HKCU\Software\Locky\completed – Whether or not the ransomware finished encrypting all available files
HKCU\Control Panel\Desktop\Wallpaper (“%UserProfile%\Desktop\_Locky_recover_instructions.bmp”)
Because the Locky ransomware can encrypt all network drives, it is critically important to lock down the permissions on any available network shares. As always, it is also important to perform regularly scheduled backups of all important data, and to have the backup drive stored off-network when not in use. At this time, there is no known way to decrypt files encrypted by Locky (unless ransom is paid), and its deletion of the Shadow Volume copies makes this even harder to circumvent. It has been reported that Locky victims have been successful in retrieving their data after payment is made, but it is never advisable to pay cyber-criminals their requested ransom. With due diligence and good security habits, everyone should be able to avoid being infected by Locky.
Threat Recap Week of Feb. 15
A lot happens in the security world, some big and some small, and many stories get lost in the mix. In an effort to keep our readers informed and updated, we present the Webroot Threat Recap, highlighting 5 major security news stories of the week.
Samsung Smart TV’s, Too Smart?
Recently, it has come to attention that Samsung Smart TV’s and their remotes have the capability to record and transmit any spoken words to a third-party company for use in providing voice recognition functionality. Samsung has updated their EULA in response to the questionable section regarding consumers not talking about sensitive, personal information near the TV, as it will be recorded and sent off for analyzing.
Cybersecurity Insurance Leading to Rise in Ransom Payouts
With ransomware becoming ever more prevalent, cybersecurity insurance has taken on ransom coverage as well, but also leads to more companies merely accepting the ransom and paying it. While nearly a quarter of companies would be willing to pay the ransom, and having cyber insurance raises that amount, the expected payout may still not cover the total cost of the attack; especially the loss of the company’s reputation in the marketplace.
L.A. Hospital Hit With Ransomware
In the last week, the Hollywood Presbyterian Medical Center was the target of a ransomware attack, in which the hospital ended up paying $17,000 in bitcoins to reassume control of their systems. They are still unsure of the origin of the attack, although officials claim no patient data was compromised.
High Cost of Spear Phishing Attacks
Opening an email is now one of the most dangerous tasks many companies face every day. As the prevalence of spear phishing grows, the majority of U.S. companies have been targeted at some point in the last year, with the average cost of $1.6 million in financial damages. While email filtering can be effective, the real problem comes down to the employees who lack sufficient training in spotting these types of attacks
Read More: http://www.infosecurity-magazine.com/news/spear-phishing-incident-average/
Using VoIP Phones Could Prove Risky
Many companies use VoIP phones in their offices, connected to their internal networks, but lacking any security greater than the default settings. Without increasing these settings from their factory-sent state, it can leave a significant gap in protection for unwanted attackers. Unfortunately, many phone companies don’t require any authentication when using the phones, nor do they require consumers to create strong passwords.
Read More: https://www.helpnetsecurity.com/2016/02/16/voip-phones-can-turned-spying-money-making-tools/
Building a secure IoT Gateway using Threat Intelligence
Part 1 and Part 2 of this series provided an overview of Threat Intelligence and hopefully offered some understanding as to what role it can play in helping secure an IoT infrastructure. For those familiar with cybersecurity and how to implement Threat Intelligence in traditional network appliances, the jump to securing an IoT Gateway is fairly straightforward. For those new to the space, trying to put a plan together for integrating Threat Intelligence may seem a bit daunting. This blog is intended to be a guide of questions to start the process.
The first question that should be addressed when building an IoT Gateway is, “What is your audience?” For example, if the given environment in which the gateway will be implemented is closed, meaning no interconnectivity with the Internet, then traditional IP reputation or URL Categorization won’t provide much help. These technologies are built around the expectation that a malicious actor will attack from, or ex-filtrate data to, locations on the Internet. Therefore, with no connection to the Internet these technologies provide little in the way of additional security to an appliance manufacturer. That being said, by definition an IoT Gateway should provide connectivity to the Internet, so the rest of this blog will assume that is the case.
So, what is needed to build an IoT Gateway?
Obviously, there is the interconnectivity that bridges a proprietary physical layer and converts it to TCP/IP traffic. This blog won’t help much with that aspect of the appliance as the respective vendors would know best how to achieve this part of the solution. However, once data has been converted to Internet compatible protocols, building a basic gateway with IP blocking and URL categorization requires: 1) IP packet inspection to extrapolate incoming IP addresses or outgoing URLs, 2) a Threat Intelligence module that allows for the scoring of an IP or URL, and 3) a user interface to manage the policies. Here is a breakdown of each component:
- Deep Packet Inspection (DPI): Simply put, this is examining each data packet as it comes through the appliance, stripping out header information that contains the IP address for inbound traffic or the outbound URL. There are robust open source solutions such as nDPI from ntop that do a very good job analyzing traffic, but partnering with a provider such as Qosmos might be the right approach for those new to security. The problem isn’t in the ability to inspect packets but rather the ability to do it at line speeds. Those who aren’t experts or who are looking to go to market quickly would do well to find a partner in this space.
- Threat Intelligence Module: There are several considerations in terms on selecting a provider, how best to implement a solution and how to implement Threat Intelligence in such a way that it becomes a differentiator rather than an “also have”. Take the time to become educated on cost to performance aspects a Threat Intelligence provider offers and understand the ramifications of the level of false positives and uncategorized lookups that a solution will have on the overall implementation of the final product.
- Policy Management: Nearly as important as the Threat Intelligence itself is the ability for appliance administrators to configure and manage policies. Will there be a need to manage based on region, user, device type or some other granular method specific to an industry? Can the individual device management be done through a cloud-based interface allowing for quicker deployment and lower appliance resource requirements or will it need to be built into the operating system for a given appliance to be managed locally? Taking the time to ask these and other questions around the user interface is key to building a successful solution.
The intent of this post is to identify key considerations that must be addressed to successfully build a secure IoT Gateway. It is a complicated process with issues not limited to traffic management, threat identification at line speeds and the potential for complex policy and usage configurations. As daunting as this may appear, traditional appliance manufacturers have been addressing this need for Information Technology ecosystem for many years and bringing that technology to the Operational landscape is fairly straightforward. Part 4 of this series will push the edge of what is possible by walking through some theoretical configurations that bring Threat Intelligence down from the network appliance to the actual edge device.
New Ransomware PadCrypt: The first with Live Chat Support
A new ransomware has been discovered and what sets apart this variant from the rest is its implementation of a chat interface embedded into the product.

That link for “Live Chat” will prompt the window for live support. The window should look like this and will allow you to talk directly with the cyber criminal.

Currently the Command and Control servers are down so currently there is no encryption being performed and we were unable to chat with any “developer” to see what they would say. However, we presume it’s just to aid in the process of getting a bitcoin wallet address, filling it with coins, and sending the payment securely. This task can be complicated to unsavvy users so we suspect this feature was created to add a more human element to the aid of receiving the ransom.

These are the standard instructions that also are available if you click “decrypt help” and can be a daunting task for those not familiar with the process. This is why we suspect the chat feature was added. Also, for the first time that we’ve seen on any ransomware sample – it comes with a uninstaller. Located in %AppData%\PadCrypt\unistl.exe it will remove all files and registry entries associated with the infection. However, it will still leave all your files encrypted.
The rest of the drill with this ransomware is pretty standard – “.pdf.scr” extension on the encrypted files, Volume Shadow service is deleted, decryptor tool is provided to decrypt your files after paying ransom.
PadCrypt infection samples: From ZeroBin
MD5 8616f6c19a3cbf4059719c993f08b526 (C2: cloudnet.online)
MD5 aface93f4d6a193c612ea747eaa61eaa (C2: annaflowersweb.com)
Dropped files:
17822a81505e56b8b695b537a42a7583 (package.pdcr)
7d2822aedddd634900a4c009ef0791a9 (unistl.pdcr)
Webroot will catch this specific variant in real time before any encryption takes place. We’re always on the lookout for more, but just in case of new zero day variants, remember that with encrypting ransomware the best protection is going to be a good backup solution. This can be either through the cloud or offline external storage. Keeping it up to date is key so as not to lose productivity. Webroot has backup features built into our consumer product that allow you to have directories constantly synced to the cloud. If you were to get infected by a zero-day variant of encrypting ransomware you can just restore your files back as we save a snapshot history for each of your files up to ten previous copies. Please see our community post on best practices for securing your environment against encrypting ransomware.
Why Webroot is Proven Next-Generation Endpoint Security
Within the last several years, online threats have continued to evolve at disturbingly high rates, and are more robust than ever before. According to the data we’ve seen across the Webroot Threat Intelligence Platform, many new attacks are targeted, adaptive (polymorphic) malware variants that appear suddenly in several points across a targeted company’s network and then may never be seen in the same way again. When so many threats are tailor-made and can even be purchased as a service in the criminal networks, traditional, reactive cybersecurity just won’t cut it.
At Webroot, we know the only way to protect businesses and individuals is by understanding our adversary and predicting their next move. That’s why we’ve continued to expand our threat intelligence and integrate it more deeply with our endpoint protection solutions so that new, unknown threats are detected and destroyed as soon as they appear within the networks of any of our customers. This unique, collective protection means that all Webroot customers protect one another. It’s a community of cybersecurity. Our cloud-based threat intelligence is derived from millions of sensors and real-world endpoints around the world to provide proven next-generation endpoint security that can predict, prevent, detect, and respond to threats in real time. With 87,000 business customers (and counting) and partnerships with 40 of the industry’s top security vendors, Webroot is the proven choice for defending against modern malware. If you would like to learn more about out Threat Intelligence Platform, see our website.
In view of the tactics modern malware writers and other cybercriminals have adopted, we invite you to join us at the 2016 RSA conference to find out how our next-generation endpoint security solutions protect businesses and individuals in a connected world. To schedule a meeting with us at RSAC, visit www.webroot.com.