SAN JOSE, CA. - February 24, 2016
Lynx Software Technologies unveiled the LynxSecure 5.3 Separation Kernel Hypervisor at Embedded World, Nuremberg, and announced a powerful new capability that extends the principle of domain separation to the network connection. At the same time, in partnership with Webroot, they revealed real time cloud-based threat detection for guest operating systems hosted by LynxSecure. LynxSecure 5.3 is being demonstrated in the Lynx booth at both the Embedded World Conference in Nuremberg, Germany from February 23rd to 25th (hall 4A, booth 338) and at the RSA Conference in San Francisco, USA from February 29th to March 3rd (south hall, booth 732)
Commenting, Robert Day, Vice President, Marketing at Lynx Software Technologies, said, “The success of connected cars, connected infrastructure and other safety-critical IoT applications rests on the resolution of two key security challenges. The first is the robust protection of not only the gateways and endpoints, but also the lines of communication between them, and then from the gateway out over the Internet. The second is real time threat detection, as well as containment. With today’s announcement, we are delivering both – opening the path to a new generation of connected vehicles, a vast array of safety critical infrastructure and for further industrial and mainstream IT deployments.”
LynxSecure 5.3
LynxSecure 5.3 is a DoD certified secure virtualization solution based on separation kernel technology. When deployed in an IoT gateway, LynxSecure implements the robust separation of domains, ensuring that the Operational Technology (OT) network hosting the IoT endpoints is securely isolated from the wider Information Technology (IT) network. With a tiny trusted code-base, LynxSecure provides IoT endpoints and gateways with the protection they need by reducing the attack surface exploitable by malicious agents to an absolute minimum, and securely controlling any communications between the OT and IT domains.
LSA.connect
LynxSecure 5.3 is the enabling platform for LSA.connect, a secure network encryption component built using LynxSecure bare metal applications (LSAs). In its simplest configuration, LSA.Connect can be used to encrypt network traffic without exposing a large attack surface to malicious agents by housing the network encryption algorithms in their own secure domain, away from both the operating system connected to the internet and the encryption keys themselves. In a more sophisticated configuration, LSA.connect can be used to extend the principle of domain separation to the network, by supporting multiple isolated encryption tunnels over a single physical network connection, again each housed in their own isolated domains (see Figure 1).
Will Keegan, Director of Software Security at Lynx, said, “The large attack surfaces present in monolithic operating systems such as Linux expose both the connected IoT devices and also the network encryption algorithms to the potential for exploitation by malicious agents. The combination of LynxSecure and LSA.connect offer isolated domains for each network, and separate bare-metal encryption which changes the connected IoT gateway from being a point of attack to a point of defence. As an example of multi-stream communications, a connected car could take advantage of separate domains to implement firmware updates, the communication of telematics data, and the transfer of downloadable content for in-vehicle infotainment (IVI), all using dedicated secure encryption tunnels.”
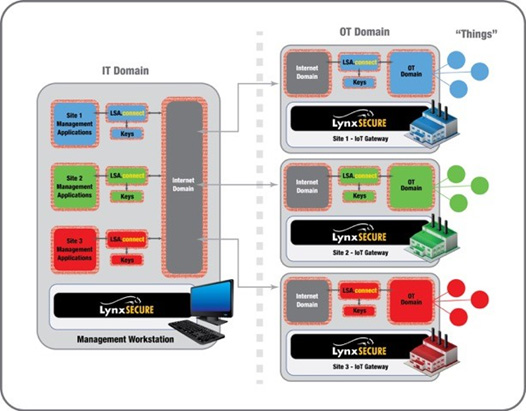
Figure 1- Bare Metal Encryption offers multi-stream secure IoT communication
Advanced Cloud-based Threat detection
Lynx is also partnering with Webroot® and combining its IoT Security Toolkit with LynxSecure to provide real-time threat intelligence services and intelligent cybersecurity device agents for the protection of critical IoT and IIoT systems against rootkits and other Advanced Persistent Threats (APT). By embedding components of the Webroot IoT Security Toolkit inside their own domain on LynxSecure, threats can be detected, identified and removed without the constraints or risks inherent in running solutions at the operating system level.
John Sirianni, Vice President, Strategic Partnerships, IoT, at Webroot, commented “Combining LynxSecure with our IoT Security Toolkit linked to our Webroot Threat Intelligence Platform can address the ‘detection gap’ where malicious attacks can remain invisible for months after first infection. Our real-time detection technology, housed in its own isolated LynxSecure domain, identifies the moment the threat first enters a system, and allows security teams and security systems to quickly assess the threat, and analyse it before it can do any damage.”
Conference papers
Both the secure communication and the threat detection technologies are being extensively discussed at the Embedded World conference programme. On Tuesday, 23 February at 12.00 Robert Day together with Dan Isaacs of Xilinx will be addressing secure communications in a paper called “Architecting Cybersecure IoT Systems Using New Programmable SoC Multi-layer Security”. On Thursday 25 February, at 10.00, Will Keegan of Lynx will be talking about “The Connected Embedded Devices of the IoT: A Playground for Malicious Agents, or an Opportunity for Manufacturers to Innovate?”
David Dufour of Webroot will take the detection gap as his theme in a paper on Tuesday at 10.30 about “Securing IoT Devices Using Big Data and Contextual Analytics”. At 13.30 on Thursday, Robert Day and David Dufour will follow up with a paper on “Securing the IoT - Combining Platform Protection with Cloud-based Threat Intelligence“.
Device support
LynxSecure 5.3 is already available on the Intel Architecture and will be released on ARM platforms in 2016.
