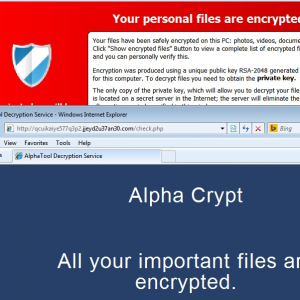
After seeing a great presentation on newly discovered biometrics/fingerprint vulnerabilities (“Fingerprints On Mobile Devices: Abusing And Leaking”, by Tao Wei and Yulong Zhang) at Blackhat 2015, I have to wonder why we are even using a lone fingerprint as a password. Wouldn’t fingerprints be better implemented as a username?
When your fingerprint is compromised, it is compromised forever. We’re talking about something associated with criminal records, banking, and other fairly-critical segments of one’s identity. It only makes sense your fingerprint remain part of your identity and not some password you hope to remain secret for the rest of your life. You can’t change them. Not easily, anyways… As your username, it would simply remain a part of your identity, unable to be used against you without the secrets you can more easily hide and change: passwords, pins, etc.
 Fingerprints would normally need to be physically gathered, dusting for prints and all that, making their compromise a less-than-likely situation. The issues outlined in the presentation I saw, however, showed it could be possible for their digital counterparts to be gathered remotely and en masse. Imagine if a fingerprint wasn’t the password, but only the login. That wouldn’t be that big of a deal anymore. So they know your username, so what? They still can’t log in. Email addresses are scraped up off the internet all the time. Someone’s email address is bound to be in many places they don’t want it to be, but the threat of compromise is still extremely low if they’re securing their account properly. In reality, a leaked fingerprint is a big deal because you can do things like pay someone via PayPal with it. The fingerprint is the password and the username can be gotten easily (they’re almost always stored insecurely and most of the time it’s just an email address anyways).
Fingerprints would normally need to be physically gathered, dusting for prints and all that, making their compromise a less-than-likely situation. The issues outlined in the presentation I saw, however, showed it could be possible for their digital counterparts to be gathered remotely and en masse. Imagine if a fingerprint wasn’t the password, but only the login. That wouldn’t be that big of a deal anymore. So they know your username, so what? They still can’t log in. Email addresses are scraped up off the internet all the time. Someone’s email address is bound to be in many places they don’t want it to be, but the threat of compromise is still extremely low if they’re securing their account properly. In reality, a leaked fingerprint is a big deal because you can do things like pay someone via PayPal with it. The fingerprint is the password and the username can be gotten easily (they’re almost always stored insecurely and most of the time it’s just an email address anyways).
Other situations and issues involving fingerprints being used as a mix authentication and authorization – depending on what app you’re in – are outlined in the presentation as well. In one example, they showed malicious actors’ ability to snag fingerprints in the background, causing you to authorize a payment when unlocking your phone, for instance. Yet another situation where, if the print was your username, there wouldn’t be an issue.
At the very least, there clearly needs to be better security standards around fingerprint data and sensors. Still, making them less powerful (read: not the sole password used to access banking information) would be the best way to go.











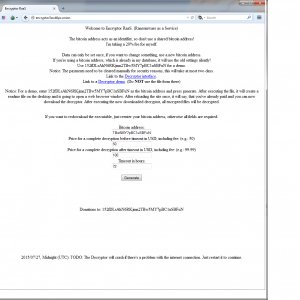


 It just doesn’t seem to end with all the exploits being revealed by the Hacking Team dump earlier this month. This vulnerability could allow remote code execution if a user opens a specially crafted document or visits an untrusted webpage that contains embedded OpenType fonts. The Adobe Type Manager module contains a memory corruption vulnerability, which can allow an attacker to obtain system privileges on an affected Windows system.
It just doesn’t seem to end with all the exploits being revealed by the Hacking Team dump earlier this month. This vulnerability could allow remote code execution if a user opens a specially crafted document or visits an untrusted webpage that contains embedded OpenType fonts. The Adobe Type Manager module contains a memory corruption vulnerability, which can allow an attacker to obtain system privileges on an affected Windows system.