Parents across America face a growing wave of sophisticated online fraud designed to exploit their deepest fears and protective instincts. Americans reported losing more than $12.5 billion to fraud in 2024, representing a 25% increase over the prior year, according to new Federal Trade Commission data.
Parents represent a particularly vulnerable target because scammers understand that nothing motivates faster action than a perceived threat to a child’s safety or wellbeing. These criminals exploit parental love —creating artificial urgency that bypasses normal thinking.
Why scammers target parents
Parents are prime scam targets for several key reasons:
- They often have established credit, making it attractive for scams involving money.
- Easy access to cash that hackers try to tap into.
- Most importantly, parents will go to extraordinary lengths—including financial sacrifice—to protect their children from harm.
Modern technology has made these scams more convincing than ever. Scammers now use artificial intelligence to clone voices, create fake social media profiles, and generate realistic scenarios that seem entirely plausible to worried parents.
The 5 most devastating scams bankrupting parents right now
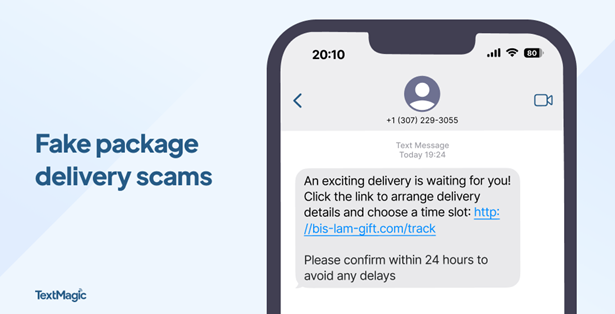
1. Family emergency scams
The most emotionally devastating scam targeting parents involves fake emergencies. Scammers use AI to clone the voice of a child in distress, calling parents with scenarios like car accidents, jail time, or medical emergencies. The caller, sounding exactly like their child, beg for immediate money transfer while pleading for secrecy.
These scams create powerful emotional responses that override logical thinking. Parents hear their child’s voice saying, “Don’t tell Dad” or “I’m scared,” and immediately spring into action without verification.
“Pause and verify” protocol: Teach your entire family the 24-hour rule for any urgent financial requests. No legitimate emergency requires immediate wire transfers or gift card payments. Always hang up and call back using a known phone number to verify any emergency claims.
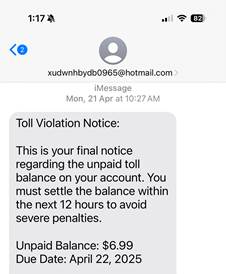
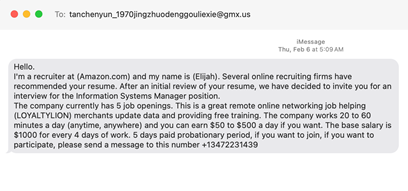
2. School-related fraud
Cybercriminals pose as school officials, coaches, or administrators claiming children owe money for equipment, field trips, or disciplinary issues. They demand immediate payment via wire transfer, gift cards, or cryptocurrency to avoid serious consequences like suspension or criminal charges.
These scams work because parents want to protect their children’s academic and social standing. The fraudsters create artificial deadlines and threaten embarrassment or legal action if parents don’t act quickly.
Verify information: Hang up and contact the school or organization directly using their official phone number or website to confirm its authenticity.
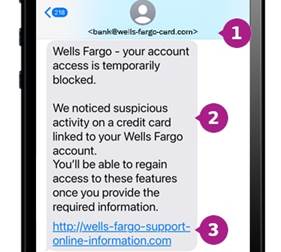
3. Social media kidnapping hoaxes
In virtual kidnapping scams, fraudsters monitor children’s social media activity to gather personal information. They then call parents claiming to have kidnapped their child, demanding ransom money. Meanwhile, the child is simply unavailable—perhaps in class, at practice, or with friends.
These schemes rely on the parent’s inability to immediately reach their child for confirmation. The scammers use publicly available information from social media posts to make their demands seem legitimate.
Multi-Factor Authentication (MFA): Enable two-factor authentication on all family accounts, especially email, banking, and social media. This simple step blocks 99% of automated attacks, even if passwords are compromised. Show your children how to use authenticator apps rather than SMS authentication when possible. Additionally, It’s critical for parents to set their children’s social media accounts to private, use parental controls, and monitor their child’s social media habits.
4. Financial Sextortion of Minors
The FBI has identified “financial sextortion” of teens as a “rapidly escalating threat”. Criminals trick minors into sharing explicit images, then blackmail both the child and parents for payment. These predators target children through gaming platforms, social media, and messaging apps.
A study found approximately 5% of U.S. students reported that they had been the victim of sextortion. With 1 in 7 youth victims (15%) saying they harmed themselves in response to sextortion. Parents often discover these crimes only when their children’s demeanor changes or exhibit severe behavioral changes. The psychological damage extends far beyond the financial cost.
Social media privacy settings: Regularly audit your family’s social media accounts together. Scammers harvest information from public posts to make their schemes more convincing. Teach children to never post real-time locations, vacation plans, personal details that criminals can exploit or share personal and explicit photos.
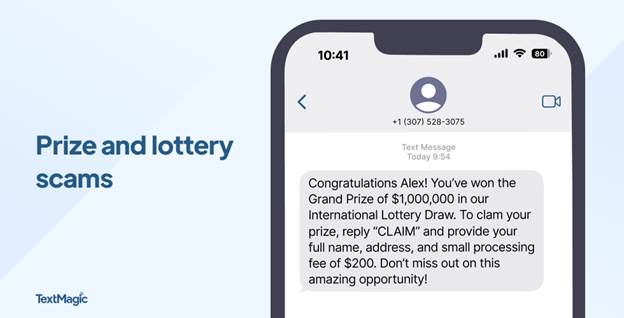
5. College and scholarship scams
As college costs soar, scammers target parents desperate to secure educational funding for their children. They offer fake scholarships, guaranteed admissions, or student loan forgiveness programs that require upfront fees or personal financial information.
These scams often impersonate legitimate organizations and use official-sounding language to appear credible. Parents, stressed about their children’s futures, may overlook red flags in their eagerness to secure opportunities.
Email security awareness: Practice identifying phishing emails with your children using the “STOP, LOOK, THINK” method:
- STOP: Don’t click links or attachments immediately.
- LOOK: Check sender addresses carefully for misspellings or suspicious domains.
- THINK: Ask yourself if the request makes sense and verify independently.
Your 5-step defense plan: stop scammers before they strike
- Real-time threat detection: Webroot’s advanced algorithms identify and block malicious websites, phishing attempts, and dangerous downloads before they can compromise family devices or data.
- Identity protection services: Comprehensive monitoring of identity, credit, and financial accounts helps detect fraud early, with up to $1 million in fraud expense and stolen funds reimbursement.
- Secure family browsing: Webroot automatically warns users about suspicious websites and blocks access to known scam sites, protecting curious children and busy parents from accidentally accessing dangerous content.
- Dark Web monitoring: This crucial feature monitors family members’ personal information and sends alerts if data appears in breaches or on criminal marketplaces.
- Password security: Strong password management ensures that all family accounts remain protected with unique, complex passwords that children and parents can easily access when needed. Never reuse passwords across accounts and use a password manager to track them all.
Don’t let criminals exploit your parental instincts
- Establish clear communication protocols with your children.
- Create unique code words or security questions that only family members know.
- Practice scenarios where children should verify requests through multiple channels before sharing information or money. Have regular family discussions about online safety to help children understand current threats without creating excessive fear.
- Participate in school, community centers, and parent organizations cybersecurity workshops specifically designed for families.
- Combine street-smart awareness with enterprise-level cybersecurity solutions like Webroot to create an impenetrable defense against parent-targeting criminals.
With October being Cybersecurity Awareness Month now is the perfect time to put your cybersecurity family game plan into place. The criminals betting on your parental panic are about to learn that informed, protected parents don’t make easy targets.