
by Blog Staff | May 30, 2012 | Threat Lab
Everyone knows that there’s no such thing as free lunch. The same goes for freely distributed pirated content online.
Recently, Webroot decided to sample malicious activity within some of the most popular Eastern European torrent trackers, based in Bulgaria, Ukraine, and Romania for starters. The results? Countless backdoored key generators and cracks for popular games and software, and most interestingly, monetization of the huge traffic by delivering pop-ups promoting the ubiquitous W32/Casonline adware, which in case you remember was recently spamvertised to millions of end and corporate users.
More details:
(more…)

by Blog Staff | May 30, 2012 | Threat Lab
End and corporate users, and especially CareerBuilder users, beware!
Cybercriminals are currently spamvertising millions of emails impersonating the popular jobs portal CareerBuilder in an attempt to trick users into clicking on client-side exploits serving links.
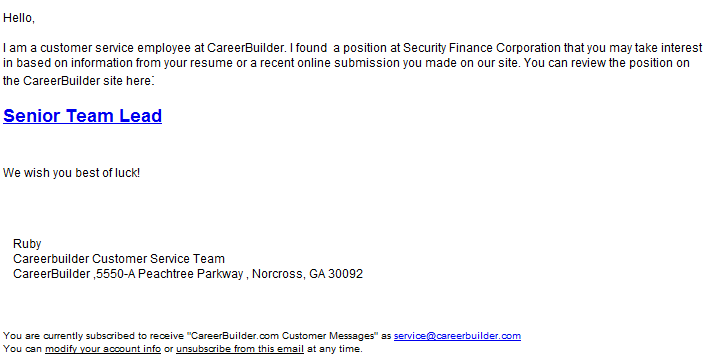
The current campaign, originally circulating in the wild since 26 Apr, 2012, is a great example of a lack of QA (quality assurance) since they’re spamvertising a binary that’s largely detected by the security community.
More details:
(more…)

by Blog Staff | May 29, 2012 | Threat Lab
Increasingly populated by novice cybercriminals thanks to the rise of cybercrime-as-a-service underground market propositions, the cybercrime ecosystem is also a home to a huge variety of underground market players.
This overall availability of managed cybercrime services results in an increasing number of underground market propositions by novice cybercriminals looking for alternative ways to monetize the fraudulently obtained goods. Although their service cannot be compared to the services offered by sophisticated cybercriminals, this niche market segment is becoming increasing common these days.
In this post, I’ll profile yet another recently advertised boutique cybercrime-friendly E-shop, run by novice cybercriminals, offering access to hacked servers.
More details:
(more…)

by Blog Staff | May 23, 2012 | Threat Lab
Just like true marketers interested in improving the click-through rates of their campaign, pharmaceutical scammers are constantly looking for new ways to attract traffic to their fraudulent sites.
From compromised web shells on web sites with high page rank, the impersonation of legitimate brands, to the development of co-branding campaigns, pharmaceutical scammers persistently rotate the traffic acquisition tactics in an attempt to trick more end users into purchasing their counterfeit pharmaceutical items.
In this post, I’ll profile two currently spamvertised campaigns impersonating YouTube and Twitter, ultimately redirecting end users to pharmaceutical scams.
More details:
(more…)

by Blog Staff | May 22, 2012 | Threat Lab
Cybercriminals are currently spamvertising online casino themed emails, which ultimately redirect users to a bogus casino site offering an executable download. Upon deeper examination, it appears that the download is actually adware.

More details:
(more…)

by Blog Staff | May 22, 2012 | Threat Lab
Remember the ‘LinkedIn Invitations’ themed malware campaign which I profiled in March, 2012?
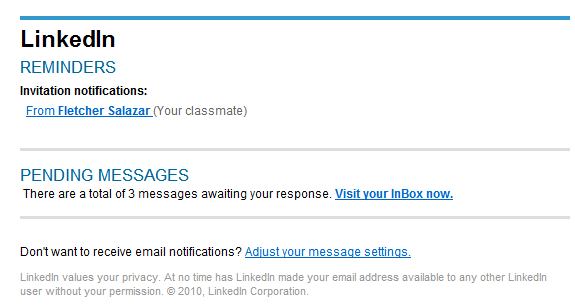
A few hours, ago, the cybercriminals behind it launched another round of malicious emails to millions of end and corporate users.
More details:
(more…)

by Blog Staff | May 17, 2012 | Threat Lab
Just how easy is it to become a spammer in 2012? Too easy to be true.
Especially in times when everything needed to become a spammer, starting for a managed spam appliance, DIY email harvesters, and millions of harvested emails, are available for sale within the cybercrime ecosystem. Despite the numerous botnet take downs we’ve seen in recent years, spam and phishing attacks continue plaguing millions of end and corporate users, potentially exposing them to malicious links, malicious payloads and fraudulent propositions.
In this post, I’ll profile a Russian managed spam service that’s been in operation for 5 years, allowing novice cybercriminals an easy entry into the world of spamming.
More details:
(more…)

by Blog Staff | May 15, 2012 | Threat Lab
Last night, a friend of mine surprisingly messaged me at 6:33 AM on Skype, with a message pointing to what appeared to be a photo site with the message “hahahahaha foto” and a link to hxxp://random_subdomain.photalbum.org
What was particularly interesting is that he created a group, and was basically sending the same message to all of his contacts. Needless to say, the time has come for me to take a deeper look, and analyze what appeared to be a newly launched malware campaign using Skype as propagation vector.
More details:
(more…)

by Blog Staff | May 11, 2012 | Threat Lab
End and corporate users (and especially Pizza eaters), beware!
Cybercriminals are currently spamvertising hundreds of thousands of emails, impersonating FLORENTINO`s Pizzeria, and enticing users into clicking on a client-side exploits and malware serving link in order to cancel a $169.90 order that they never really made.
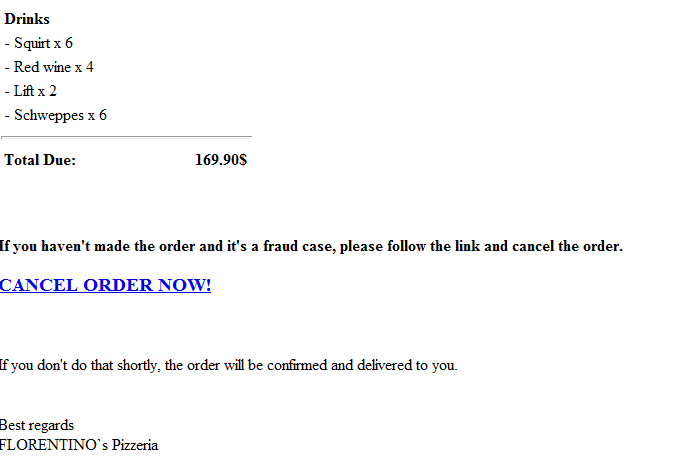
More details:
(more…)

by Blog Staff | May 10, 2012 | Threat Lab
From DIY (do-it-yourself) exploit generating tools, to efficient platforms for exploitation of end and corporate users, today’s efficiency-oriented cybercriminals are constantly looking for ways to monetize hijacked web traffic. In order to do so, they periodically introduce new features in the exploit kits, initiate new partnerships with managed malware/script crypting services, and do their best to stay ahead of the security industry.
What are some of the latest developments in this field?
Meet Sweet Orange, one of the most recently released web malware exploitation kits, available for sale at selected invite-only cybercrime-friendly communities.
What’s so special about Sweet Orange? Does it come with customer support? What client-side exploits is it serving? How are the Russian cybercriminals behind it differentiating their underground market proposition in comparison with competing kits, such as the market leading Black Hole web malware exploitation kit?
Let’s find out.
(more…)













