End and corporate users (and especially Pizza eaters), beware!
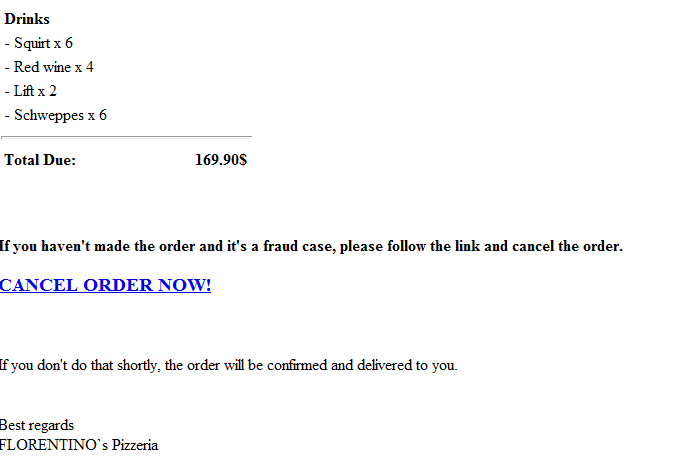
Cybercriminals are currently spamvertising hundreds of thousands of emails, impersonating FLORENTINO`s Pizzeria, and enticing users into clicking on a client-side exploits and malware serving link in order to cancel a $169.90 order that they never really made.
More details:
Once the user clicks on the link, they will be redirected to a compromised site serving client-side exploits and ultimately dropping multiple malicious binaries on their hosts upon a successful infection.
Malicious URL: hxxp://oldsoccer.it/page1.htm?RANDOM_STRINGS
Client-side exploits used: CVE-2010-0188 and CVE-2012-0507
The malicious URL contains a tiny iFrame pointing to the fast-fluxed domain uiwewsecondary.ru:8080/internet/fpkrerflfvd.php where the client-side exploitation takes place.
The redirection chain is as follows:
uiwewsecondary.ru:8080/internet/fpkrerflfvd.php -> uiwewsecondary.ru:8080/internet/itbzewhqgrkv.jar -> uiwewsecondary.ru:8080/internet/xrcnenbmdpfzfpx.jar ->uiwewsecondary.ru:8080/internet/kqbzaubpiqxnbn.pdf -> poluicenotgo.ru:8080/internet/at.php?i=8
The Russian domains are fast-fluxed by the cybercriminals in an attempt to make it harder for security researchers and vendors to take down their campaign. We’ve seen a similar fast-flux technique applied in the following campaign – “Spamvertised ‘Your tax return appeal is declined’ emails serving client-side exploits and malware“.
Upon successful exploitation the campaign drops the following MD5 on the infected hosts: MD5: 03d874abaaca02b090372eee2d090dc0 detected as Trojan.Generic.KDV.602078; Troj/Agent-VSS.
What happens once the dropped MD5 executes? Basically, it phones back to the following domains/URLs:
- dare2dreamz.com/pony/gate.php
- cityweddingguide.com
- dynolite.eu
- abbott.u4ria.co.za
- demircioglubilgisayar.com.tr
It also downloads more malicious binaries from the following compromised URLs:
- dynolite.eu/7U0ASvP9/AZz.exe
- abbott.u4ria.co.za/HGFg1RHz/MkiZMX.exe
- demircioglubilgisayar.com.tr/qy3kMMxv/VgWqQm4k.exe
All the binaries are identical, and have the following MD5, MD5: 97d8f1fa11c86befa069845ffaf818db currently detected as TrojWare.Win32.Kryptik.ADXK by 7 out of 42 antivirus scanners.
Webroot SecureAnywhere customers are proactively protected from this threat.
You can find more about Dancho Danchev at his LinkedIn Profile. You can also follow him on Twitter.







Beware.. Pizza Lovers!!!..
I have shared this in Facebook Internet Security Group so that every security geek should be aware of this…
Also I love your articles on “Blackhat SEO” looking for some more from you Webroot Team..
I’m gone to say to my little brother, that he should also pay a quick visit this weblog on regular basis to obtain updated from latest information.