
by Blog Staff | May 8, 2012 | Threat Lab
The vibrant cybercrime ecosystem is populated by a diverse set of market players. From sellers, to buyers and vendors, sophisticated cybercriminals next to novice cybercriminals, everyone is persistently looking for ways to monetize their assets and increase their revenue.
Over the past two years, the industry witnessed the maturing business models in use by cybercriminals, and the rise of the so called cybercrime-as-a-service underground market propositions. Cybercriminals of all kinds have realized that managed services are the future that offer an efficient revenue generating platform for everyone to take advantage of.
In this post, I’ll profile a recently advertised boutique cybercrime-friendly E-shop, operated by what appears to be a novice cybercriminal looking for ways to monetize his fraudulently obtained assets.
(more…)

by Blog Staff | May 7, 2012 | Threat Lab
Are you receiving SMS spam? According to the latest reports, millions of mobile users do.
The trend is largely driven by what Webroot is observing as an increase in underground market propositions offering managed SMS spamming services to new market entrants not interested in building and maintaining the spamming infrastructure on their own.
In this post, I’ll profile a recently advertised managed service offering SMS spamming capabilities to potential customers, discuss the latest innovations in this field, their impact to mobile security, and what are some of the key factors contributing to the growth of SMS spam.
More details:
(more…)

by Blog Staff | May 3, 2012 | Threat Lab
by Nathan Collier
Recently we found new apps in alternative Chinese markets that we are considering a Potentially Unwanted Application (PUA). We are calling these apps Android.PUA.SMS.QuickPay. Lets look at a sample of this app. The sample we will look at is an app called “Screen Detection” which is an app that helps find dead pixels on your screen by displaying the colors red, green, blue, black, and white making it easy to see the dead pixel in contrast to these colors. Pretty simple app. Within a few seconds of opening the app this message pops up:
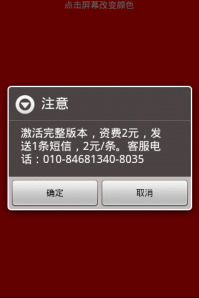
“Activate the full version, charges 2 Yuan, sending an SMS, 2 /. Customer Service Phone :010 -84681340-8035”
This app has limited functionality before requesting a premium SMS be sent for the full version, and that limited functionality only lasts a few seconds. If you do not agree to sending the premium SMS the app will just keep asking you to activate the full version whenever you click. Once you agree to the message it turns on your Wifi if not already on (Okay, that’s a little fishy), and sends a premium text message. After that the app works. Two Yuan is about 32 US cents, so people may just pay the small fee instead of spending the time to find a free version; which with a simple app that only shows four different colors as it’s functionality you would think there is something out there in the Chinese android market that will do the same for free.
It may not seem like much, but two Yuan at a time these guys are making a fortune off of apps that should be free. This is only one sample, there are several more very simple apps that we found that do various things, but all ask for a payment for it to function. Although there are legitimate Android Box apps out there, these apps are different in that they have very limited functionality, are signed by a different developer, and exploits simple apps that should be free by requesting payment for full versions before you even have a chance to see what it does.
Remember to always download from apps from a trusted source and be weary of messages asking to pay money for the full version so quick on the draw.
by Blog Staff | May 3, 2012 | Threat Lab
As many of you know, Webroot attended London’s annual security event — Europe’s largest 3 day security show — last week.
The show was a blast! Countless number of new partnerships being formed, dozens of press briefings on a daily basis, daily presentations on “Current and Emerging Trend Within the Cybercrime Ecosystem”, and best of all – many new users of the industry’s leading endpoint protection – Webroot SecureAnywhere Complete.
Taking into consideration the fact that a picture is worth a thousand words, consider going through the photos from London’s InfoSec 2012 event that we’ve prepared for you, to get an inside view of the event, and Webroot’s stand.
(more…)

by Blog Staff | Apr 23, 2012 | Threat Lab
Dear blog readers, are you going to this year’s InfoSec 2012, event in London?
If so, don’t forget to stop by Webroot’s stand G90, where I’ll be briefing our visitors on “Current and Emerging Trends Within the Cybercrime Ecosystem” on the 24th of April to 26th of April.

More details:
(more…)

by Blog Staff | Apr 16, 2012 | Threat Lab
In order for cybercriminals to launch, spam, phishing and targeted attacks, they would first have to obtain access to a “touch point”, in this case, your valid email address, IM screen name, or social networking account.
Throughout the years, they’ve been experimenting with multiple techniques to obtain usernames (YouTube user names, IM screen names, Hotmail email addresses) and valid email addresses from unsuspecting end and corporate users.
In this post we’ll profile a recently released Russian DIY email harvester, and emphasize on the difference between notice and experienced cybercriminals in the context of the tactics and techniques they use to obtain a potential victim’s email address.
More details:
(more…)

by Blog Staff | Apr 14, 2012 | Threat Lab
Earlier this week, HP’s Software Security Response Team issued a security bulletin, alerting users that certain HP ProCurve 5400 zl switches were shipped with malware installed on the associated compact flash cards. No details were given about the type of malware shipped to unaware customers.

More details on the affected switches, including their serial numbers:
(more…)

by Blog Staff | Apr 13, 2012 | Threat Lab
On Tuesday, Adobe released a security bulletin, warning users of several vulnerabilities which could give a remote attacker access to the targeted PC.
The update affects Adobe Reader X (10.1.2) and earlier versions for Windows and Macintosh, Adobe Reader 9.4.6 and earlier 9.x versions for Linux, and Adobe Acrobat X (10.1.2).
More details:
(more…)

by Blog Staff | Apr 12, 2012 | Threat Lab
On Tuesday, Microsoft issued 6 security bulletins, 4 of them critical, and 2 important updates. The bulletins fix a total of 11 vulnerabilities in Windows, Microsoft Office, and Internet Explorer.
According to Microsoft, the company has already observed targeted malware attacks taking advantage of the MS12-027 vulnerability. In order to mitigate the risks posed by these currently circulating targeted attacks, the company is advising users to disable the ActiveX controls via the Trust Center Settings > ActiveX Settings, option.
More details:
(more…)

by Blog Staff | Apr 6, 2012 | Threat Lab
 According to the latest prenotification security advisory from Adobe, next week, the company plans to issue a ‘security update’ for Adobe Reader X (10.1.2) running on Windows, Linux and Macintosh.
According to the latest prenotification security advisory from Adobe, next week, the company plans to issue a ‘security update’ for Adobe Reader X (10.1.2) running on Windows, Linux and Macintosh.
Adobe’s products are under permanent fire from malicious cybercriminals, exploiting known vulnerabilities in Adobe’s products, who succeed, primarily relying on the fact that end and corporate users are not patching in a timely manner.
More details:
(more…)













