We’re regularly asked about phone calls from “Microsoft” claiming that your computer is infected, and whether or not it is a scam – it is. Sometimes it’s a call from another “tech support” company, or a warning message on your screen. The truth is that Microsoft and other companies will not contact you to tell you that you have a computer problem through a phone call, email, or a pop-up warning message.
These scams are nothing new. We blogged about this previously in April of 2013 and a lot has changed in the malware world since then, but these scams continue. That we’re bringing these scams up again tells you one thing though – people continue to fall for them – don’t let yourself become a victim of one of these scammers.
If you’re contacted by one of these scammers, hang up, don’t click that link, and don’t call that number. Usually they’ll try to get them to let you access your computer remotely – don’t let them, and certainly don’t give them any personal information or a credit card number.
As long as you don’t let them log on to your computer remotely or download and install any software because of these scams you probably don’t have anything to worry about. These scammers don’t typically install malware on your computer; the scam is to get you to pay for tech support that you don’t actually need.
More information can be found on scams using the Microsoft name at the following links:
http://www.microsoft.com/security/online-privacy/msname.aspx
http://www.microsoft.com/security/online-privacy/avoid-phone-scams.aspx
http://www.microsoft.com/security/online-privacy/avoid-phone-scams.aspx











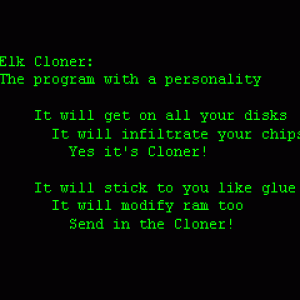 1982 – The first threat that occurred was the Elk Cloner (this however did not actually affect the Mac) which would cause the Apple II to boot up with a poem:
1982 – The first threat that occurred was the Elk Cloner (this however did not actually affect the Mac) which would cause the Apple II to boot up with a poem: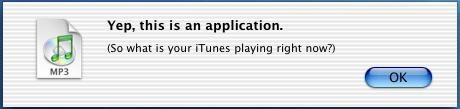 2004– Amphimix a program which is also a MP3 file. When launched it displays a dialog box which reads “Yep, this is an application. (So what is your iTunes playing now?)” It then loads itself into iTunes as an MP3 file called “Wild Laugh”, playing four seconds laughter.
2004– Amphimix a program which is also a MP3 file. When launched it displays a dialog box which reads “Yep, this is an application. (So what is your iTunes playing now?)” It then loads itself into iTunes as an MP3 file called “Wild Laugh”, playing four seconds laughter.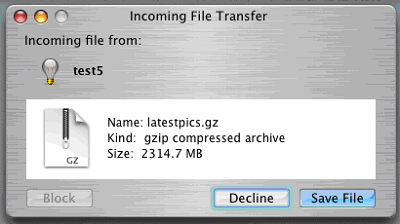 2006 – Leap is widely considered to be the original Mac Trojan. Leap used iChat to spread itself; forwarding itself as a latestpics.tgz file to the contacts on the machine. Inside the Gzipped Tar File (.tgz) was an executable file masked as a JPEG. When executed, it infected all Cocoa applications.
2006 – Leap is widely considered to be the original Mac Trojan. Leap used iChat to spread itself; forwarding itself as a latestpics.tgz file to the contacts on the machine. Inside the Gzipped Tar File (.tgz) was an executable file masked as a JPEG. When executed, it infected all Cocoa applications.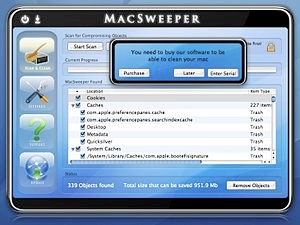 2008 – MacSweeper, Mac’s first ‘rogue’ application (a fake antivirus misleading users by reporting infections that doesn’t exists). When the infected user tried to remove the “infections”, MacSweeper asked to provide credit card details and pay $39.99 for a “lifetime subscription serial key.”
2008 – MacSweeper, Mac’s first ‘rogue’ application (a fake antivirus misleading users by reporting infections that doesn’t exists). When the infected user tried to remove the “infections”, MacSweeper asked to provide credit card details and pay $39.99 for a “lifetime subscription serial key.”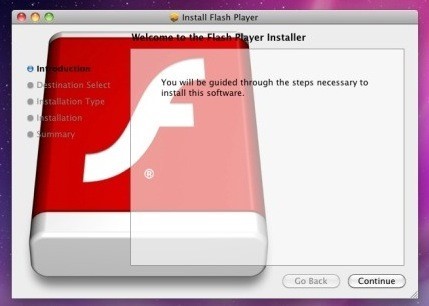 2011/2012 – Flashback was disguised as a Flash player download and targets a Java vulnerability on Mac OS X. The system is infected after the user is redirected to a compromised bogus site, where JavaScript code causes an applet containing an exploit to load. The Flashback malware was the largest attack to date, hitting more than 600,000 Mac computers.
2011/2012 – Flashback was disguised as a Flash player download and targets a Java vulnerability on Mac OS X. The system is infected after the user is redirected to a compromised bogus site, where JavaScript code causes an applet containing an exploit to load. The Flashback malware was the largest attack to date, hitting more than 600,000 Mac computers.









 The researchers then decided they would need to look at ALL the USB drivers available from Windows Update as a means of testing exploits. They used a beaglebone to emulate all the USB drivers with bruteforce vendor and product IDs along with microsoft update catalog. They scraped for all USB drivers available from Windows Update and while there were tens of thousands of duplicates they ended up with 2,284 unique USB drivers. They then installed all of these drivers while recording all details of before and after driver install.
The researchers then decided they would need to look at ALL the USB drivers available from Windows Update as a means of testing exploits. They used a beaglebone to emulate all the USB drivers with bruteforce vendor and product IDs along with microsoft update catalog. They scraped for all USB drivers available from Windows Update and while there were tens of thousands of duplicates they ended up with 2,284 unique USB drivers. They then installed all of these drivers while recording all details of before and after driver install.