The over-hyped market valuation of the buzzing P2P E-currency, Bitcoin, quickly gained the attention of cybercriminals internationally who promptly adapted to its sky rocketing valuation by releasing commercially available stealth Bitcoin miners, Bitcoin wallet stealing malware, as well as actually starting to offer the source code for their releases in an attempt to monetize their know-how and expertise in this area. Throughout 2013, we profiled several subscription based stealth Bitcoin mining tools, and predicted that it’s only a matter of time before this still developing market segment starts proliferating with more cybercriminals offering their stealth Bitcoin releases to prospective customers. Not only are we continuing to see an increase in terms of the number of tools offered, but also, some cybercriminals are actually starting to offer the source code for their releases, which, as we’ve seen in the past, has resulted in an increase in ‘vallue-added’ releases on behalf of fellow cybercriminals implementing features based on their perceived value, or through interaction with prospective customers.
What are cybercriminals up to in terms of stealth Bitcoin miners these days? Let’s profile several of the (international) underground market share leading commercially available stealth Bitcoin miners, emphasize on their features, as well as just how easy it is to fraudulently mine Bitcoin/Litecoin these days, with the affected user never really knowing what’s taking place on their PC.
Go through previous research — including MD5s — profiling commercially available stealth Bitcoin mining tools, released throughout 2013:
- New commercially available DIY invisible Bitcoin miner spotted in the wild
- New subscription-based ‘stealth Bitcoin miner’ spotted in the wild
- New subscription-based SHA256/Scrypt supporting stealth DIY Bitcoin mining tool spotted in the wild
- Yet another commercially available stealth Bitcoin/Litecoin mining tool spotted in the wild
- Yet another subscription-based stealth Bitcoin mining tool spotted in the wild
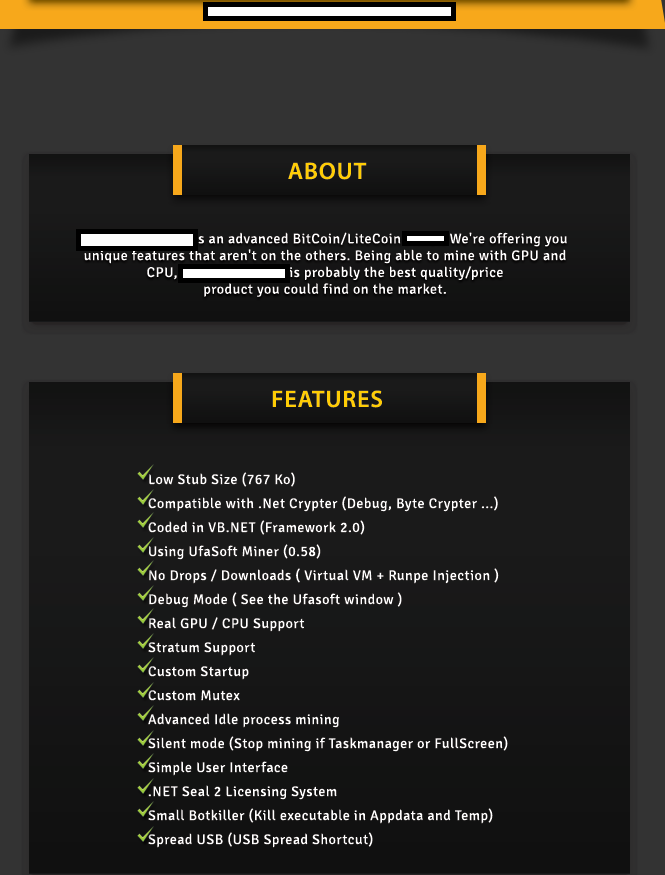
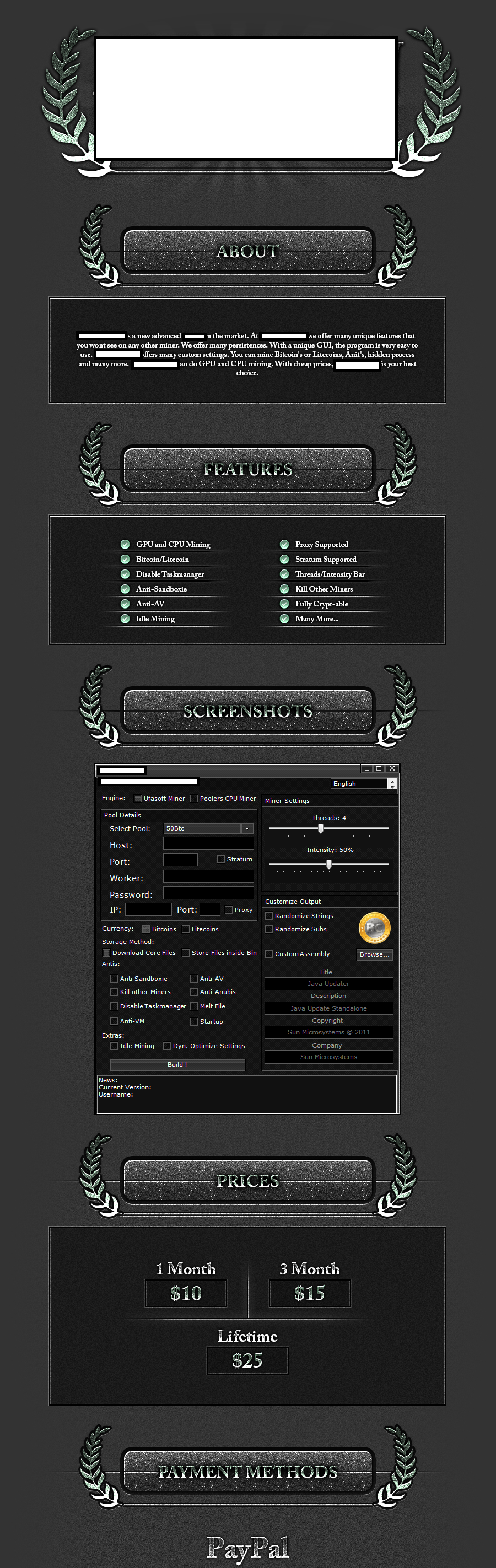
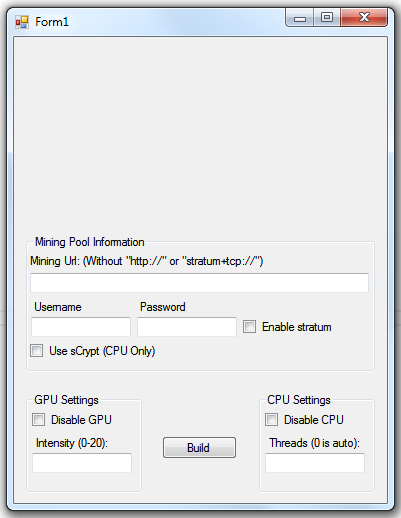
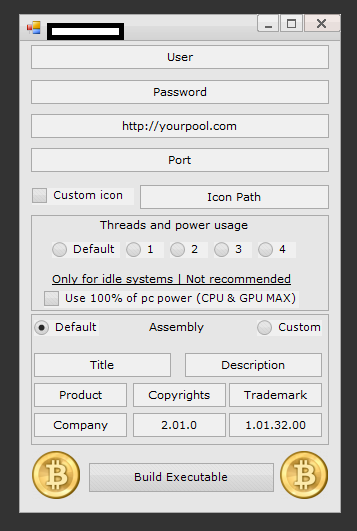
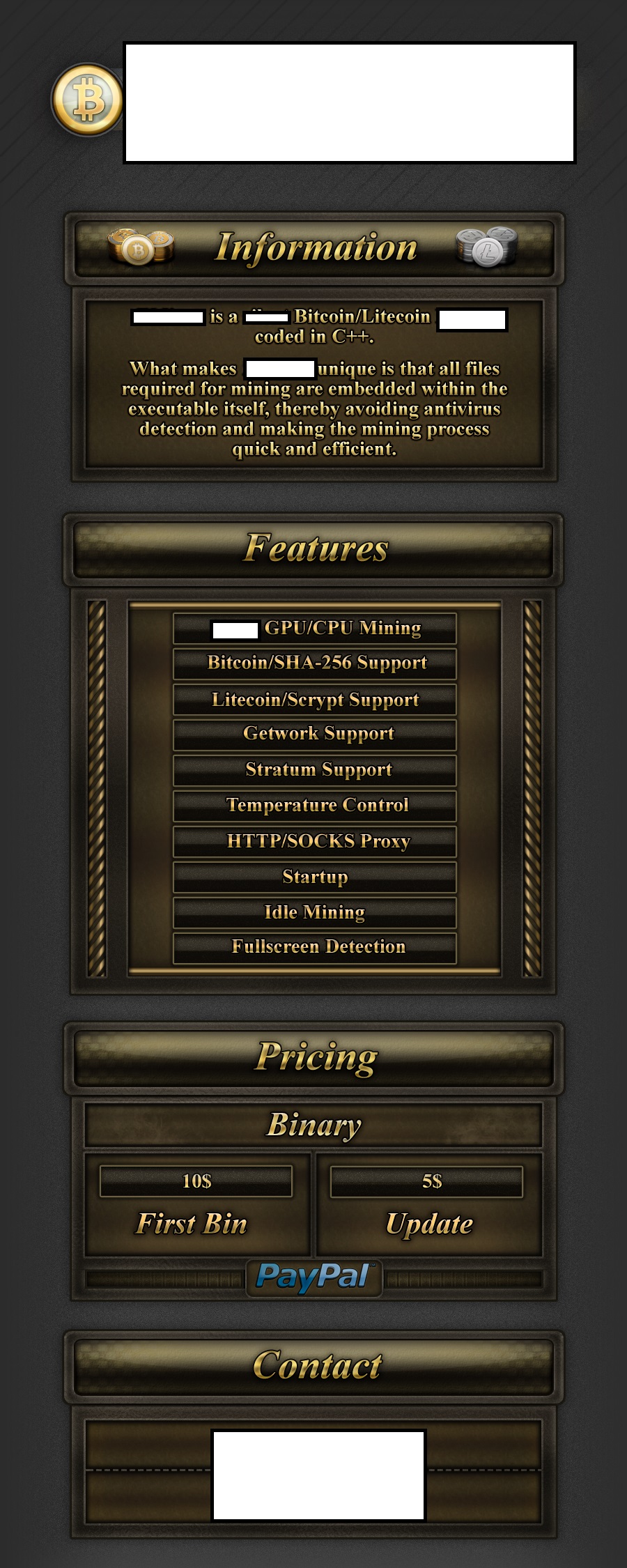
Sample commercially available stealth Bitcoin/Litecoin mining tool 01:
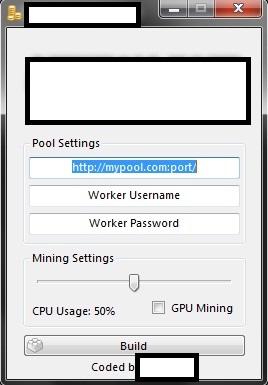
Sample commercially available stealth Bitcoin/Litecoin mining tool 02:
Sample commercially available stealth Bitcoin/Litecoin mining tool 03:
Sample commercially available stealth Bitcoin/Litecoin mining tool 04:
Sample commercially available stealth Bitcoin/Litecoin mining tool 05:
Sample commercially available stealth Bitcoin/Litecoin mining tool 06:
Sample commercially available stealth Bitcoin/Litecoin mining tool 07:
Sample commercially available stealth Bitcoin/Litecoin mining tool 08:
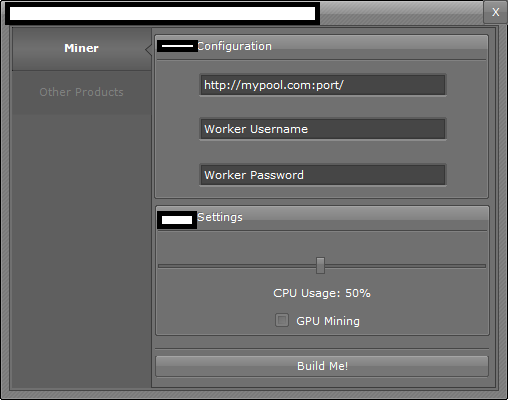
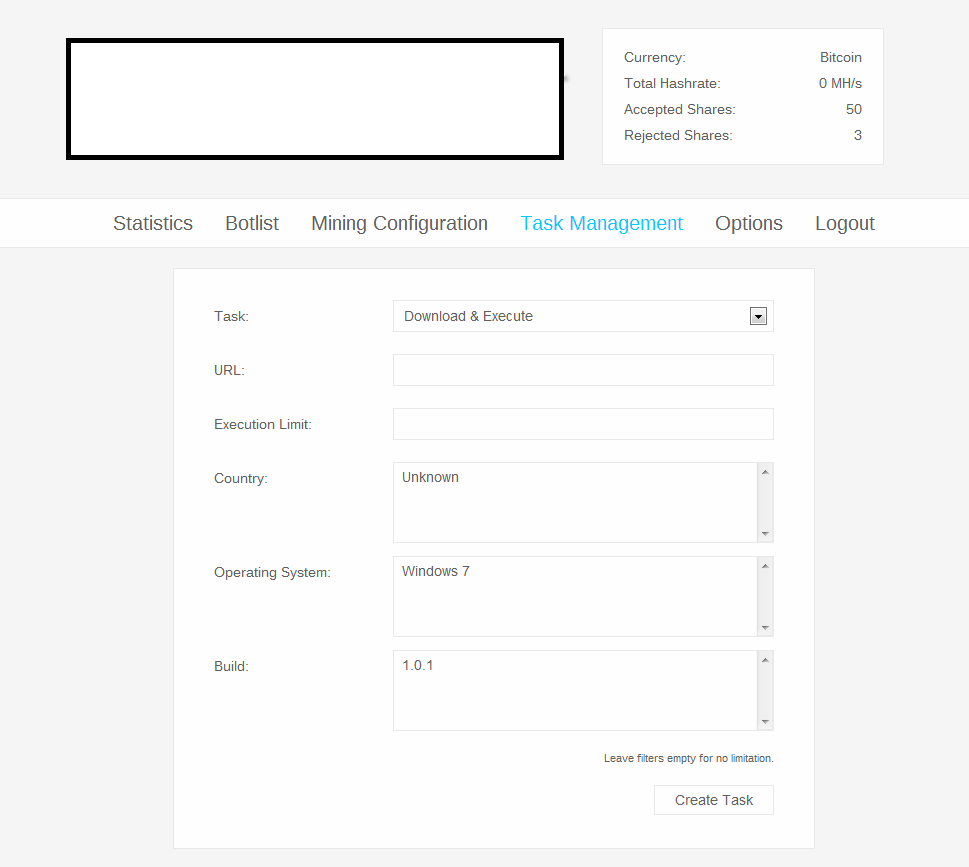
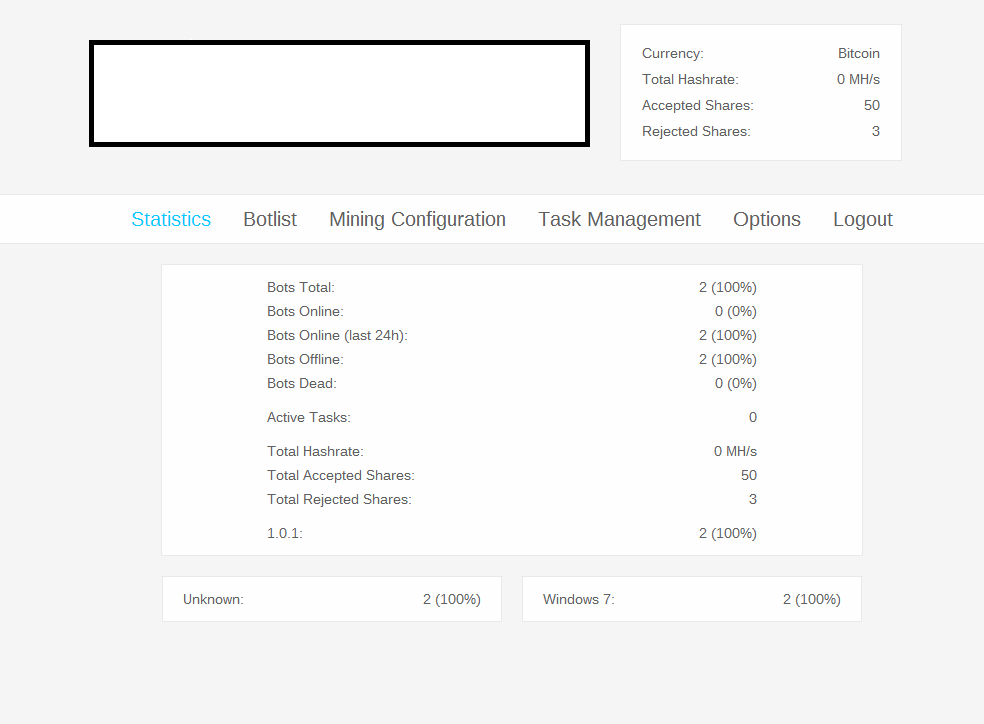
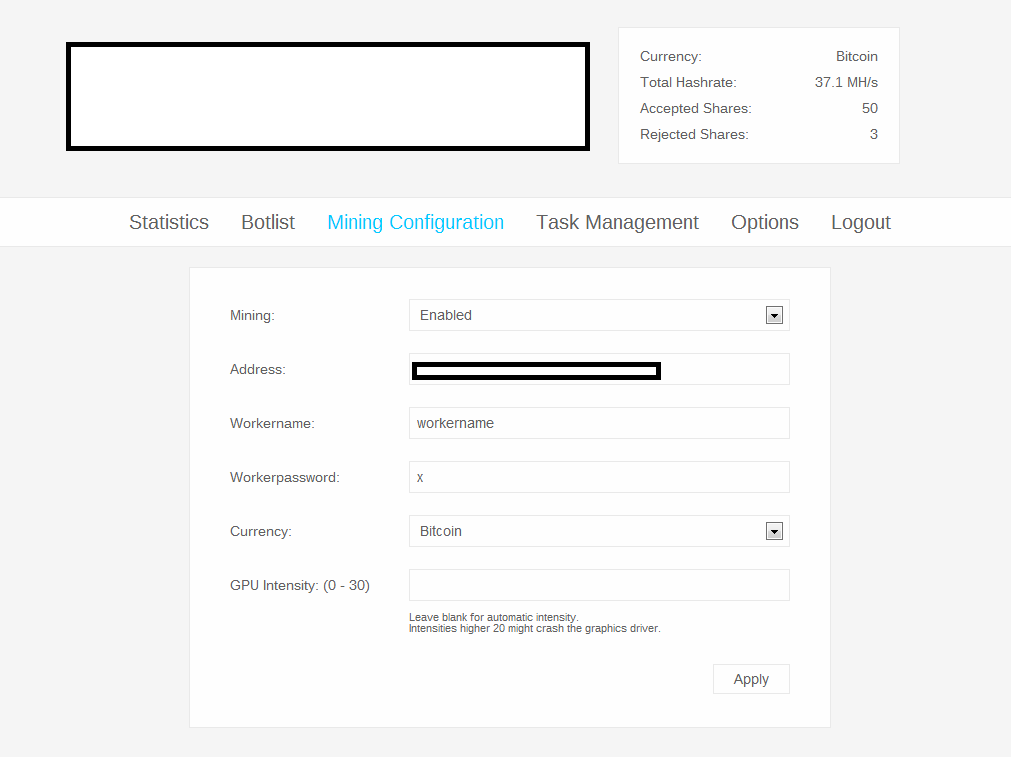
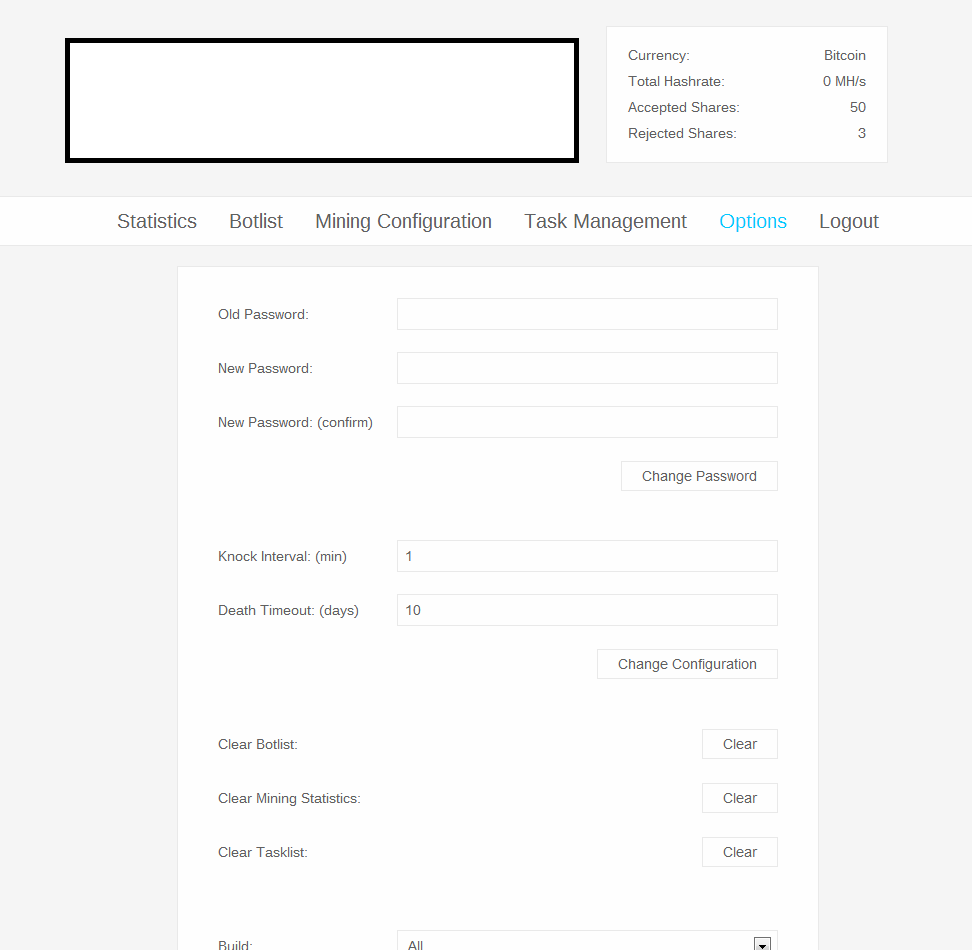
A peek inside the administration panel of a sampled stealth Bitcoin/Litecoin mining tool:
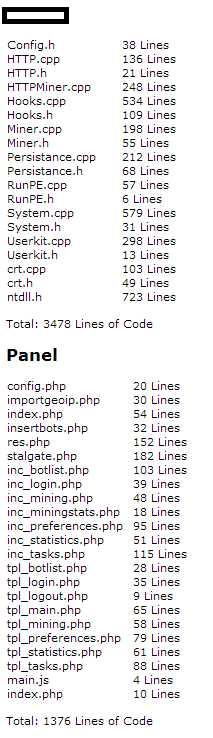
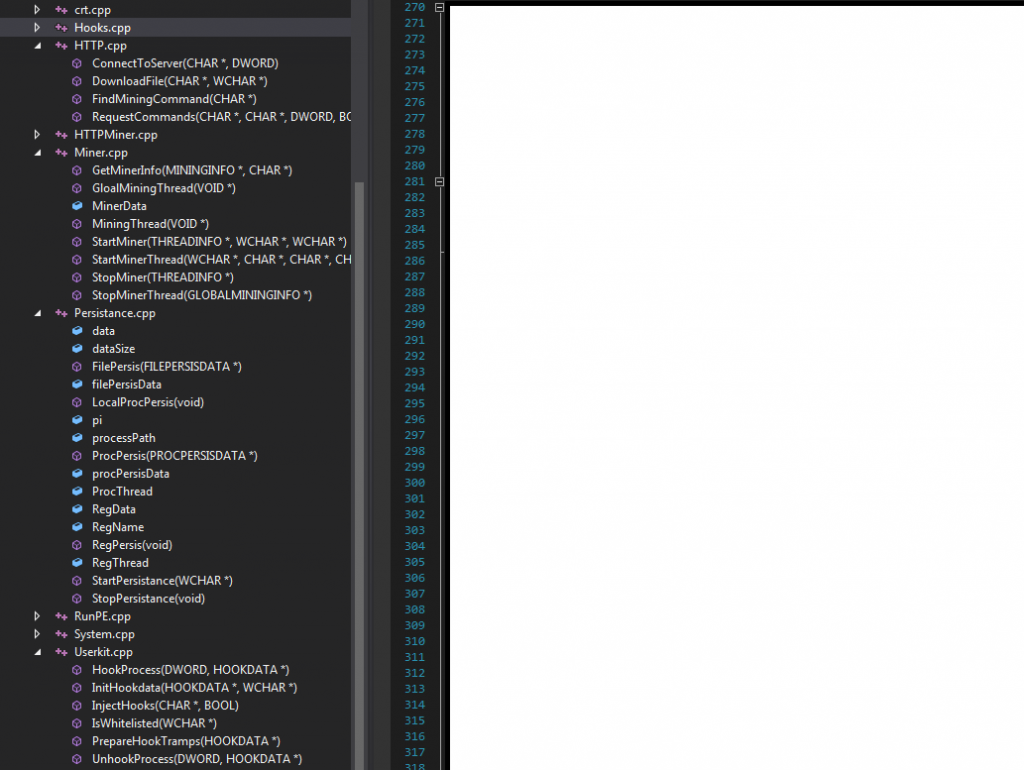
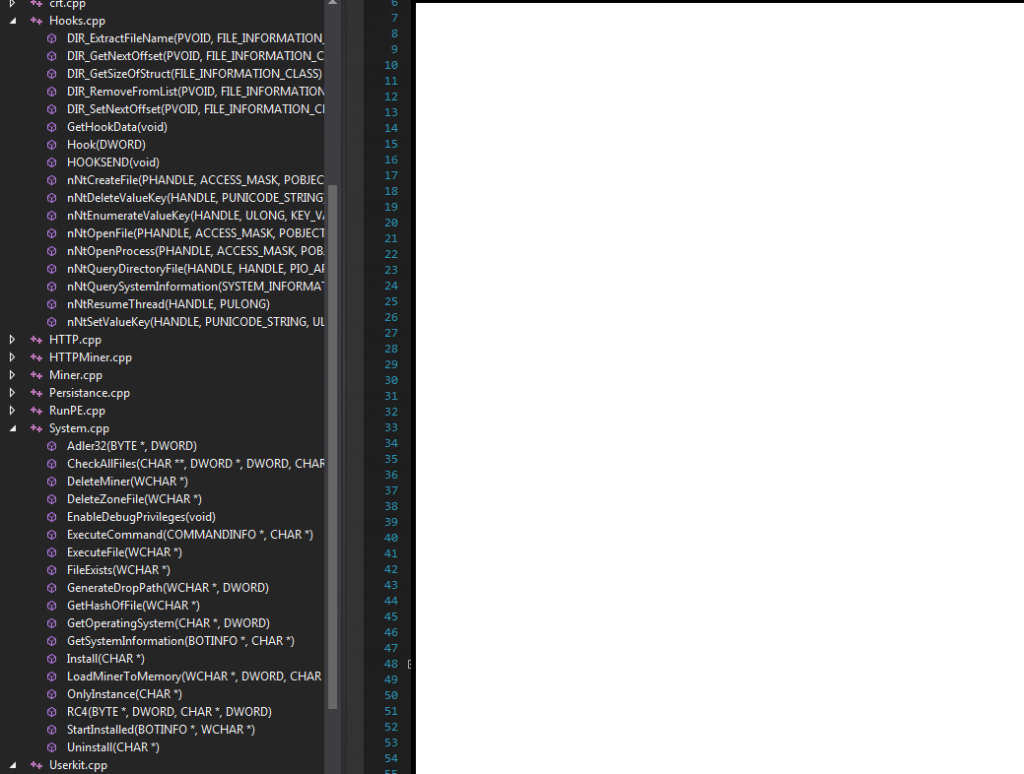
Sample screenshots of commercially available source code for stealth Bitcoin/Litecoin mining tools:
Sample screenshots of a Bitcoin/Litecoin stealing tool:
Throughout all of 2013, we continued to observe an increase in subscription based stealth Bitcoin/Litecoin mining applications with the vendors behind them emphasizing on the value-added services such as, for instance, maintaining the QA (Quality Assurance) process as well as ensuring that the latest builds of the mining applications remain undetected by antivirus scanners. Evasive tactics that aim to make it harder to analyze these samples, including the detection of Virtual Machines, and other researcher/analyst’s virtual environments, also proliferated. Moreover, a decent percentage of these commercially available stealth mining applications include the ability to remove competing mining applications, indicating that the vendors are not just aware of each other’s existence — international underground market transparency — but also, that they’re trying to gain market share by removing competing mining tools from the affected hosts. Not surprisingly, we’re also aware of commercially available source code for stealth mining tools that’s currently being offered, naturally acting as force-multiplier for more upcoming releases, now that the source code has been publicly offered.
We’ll continue monitoring this developing market segment, and post updates as soon as new developments take place.









I use this site for cryptocurrency trade https://www.google.com/url?q=https://indacoin.com/&sa=D&usg=ALhdy2_Max3zRPu_MjP94UkGsdeuQ50bJQ