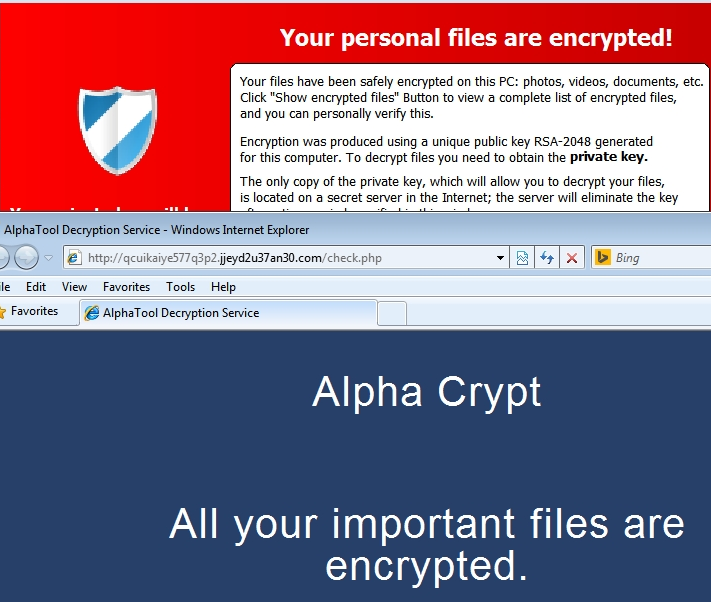
We’ve encountered yet another encrypting ransomware variant and at this point it’s expected since the scam has exploaded in popularity since it’s inception in late 2013. This one has a GUI that is almost identical to TeslaCrypt.
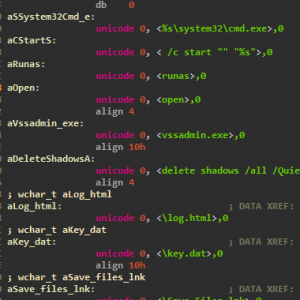
While this may look identical to TeslaCrypt it does have some improvements like deleting the VSS to make sure you aren’t saved by your shadow volume. Take a look at the below strings from an unpacked memory dump.
We can very clearly see that it opens up a command prompt and runs the command “vssadmin.exe delete shadows /all /Quiet” This will ensure that all shadow copies are deleted and the /Quiet will make sure that the command does not display messages to the user while its running.
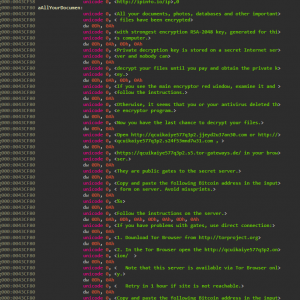
Payment is similar to recent variants – bitcoin through layered tor browsing. Not using a money mule like ukash or moneypak allows the authors to maximize thier earning power and anonymity. They can just take the full ransom amount and put through a bitcoin mixer that will use sophisticated algorithms to scramble it through millions of addresses and completely “clean” the money.
A more convenient feature this variant of encrypting ransomware has is that you are not immediately forced to use install the tor browser and will instead try and use URLs that use public gates to the secret server through your current installed browser. However, these don’t always work so the backup option is to install Tor like we’ve seen previously. See the entire ransom notice below.
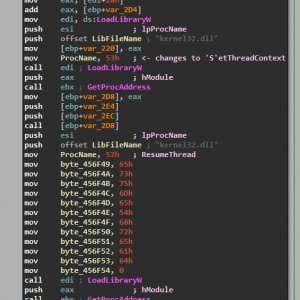
The volatitlity of this variant is quite high since it creates new instances of common windows processes to do the encryption routine to try and be as covert as possible and is extremely similar to how Cryptowall 3.0 opertates. Below is the final bit of unpacking, where it sets the child process context and resumes the thread.
MD5 analysed: 1C71D29BEDE55F34C9B17E24BD6A2A31
Aditional MD5 seen: 6B19E4AE0FA5B90C7F0620219131A12D
Webroot will catch this specific variant in real time and heuristically before any encryption takes place. We’re always on the look out for more, but just in case of new zero day variants, remember that with encrypting ransomware the best protection is going to be a good backup solution. This can be either through the cloud or offline external storage. Keeping it up to date is key so as not to lose productivity. Webroot has backup features built into our consumer product that allow you to have directories constantly synced to the cloud. If you were to get infected by a zero day variant of encrypting ransomware you can just restore your files back as we save a snapshot history for each of your files up to ten previous copies. Please see our community post on best practices for securing your environment against encrypting ransomware.







Note – The identical Playtech studio dealers are also offered at
Bet Victor Casino, along with 3 further live casino studios,
such as the very regarded Evolution games, and NetEnt Studios, and their own custom rooms.