Websites Hosting Android Trojans
By Armando Orozco and Nathan Collier
Rogue Android apps are making their way into alternative markets. Yes, we’ve seen some malicious apps trickle through and they can be elusive. But we’re now seeing markets that are only hosting malware. These rogues are of the premium rate SMS variety and request the user to send a bounty if they want the app. The interesting thing is that the websites they’re hosted on are very well put together and you can see that a great deal of time was put into creating them.
The Websites
These well-crafted websites follow a similar layout; they have device reviews, app descriptions with screenshots, QR Codes and FAQs. So far, we’ve only found these websites aimed at Russian users, with the web pages written in Russian. The descriptions are similar to those in the Android Market and the screenshots appear to be taken from the market. We are discovering that this network of SMS Trojans is fairly large.
| Click to see full size images |
The Threat
We’re calling these Trojans Android.SMS.FakeInst. We’ve found multiple variants but they all have the same objective. The Trojan informs the user that if they want to download the app, they must first agree to sending three premium rate text messages. In most cases the user will get the app they wanted but for a fee. Rates vary depending on country and carrier, but typically the three messages will go to different numbers with each charging a different fee.The screenshots below show examples of the screen when you first run the app and the rules you must agree to.
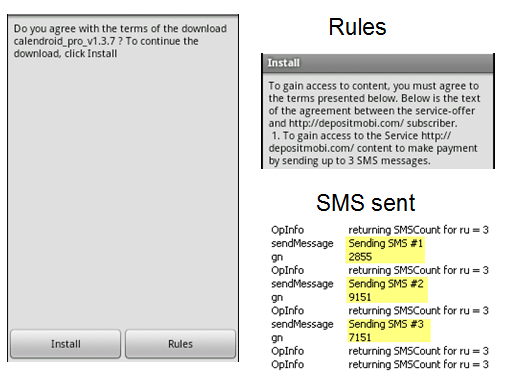 Using the premium numbers shown in the screenshots, the fees would be:
Using the premium numbers shown in the screenshots, the fees would be:
- # 7151 range of 33.87-40.00 rub US $1.10-1.30
- # 9151 range of 101.60-140.42 rub US $3.30-4.56
- # 2855 range of 170.00-203.20 rub US $5.52-6.60
Total cost
- 137.17-383.62 rubles US $9.92-12.46
As you can see, that’s a pretty steep fee for an app you can get for free from the Google Marketplace. Even if it’s a paid app, the price is steeper than most and there’s no guarantee it will work correctly.
The permissions these apps typically request are READ_PHONE_STATE, SEND_SMS, RECEIVE_SMS and INTERNET; however, we have seen a few more sophisticated apps that request the same permission as the app they are impersonating.
It’s known that most Android malware is distrusted through alternative markets, but this is a whole new level. Choose your apps wisely and download from a trusted source. Check reviews, research the developer and verify permissions requested before downloading.







Why would someone even give these apps the right to send SMS? Sounds like they completely deserve it.
Sometimes its a matter of people not checking before they install what they are allowing apps to do.