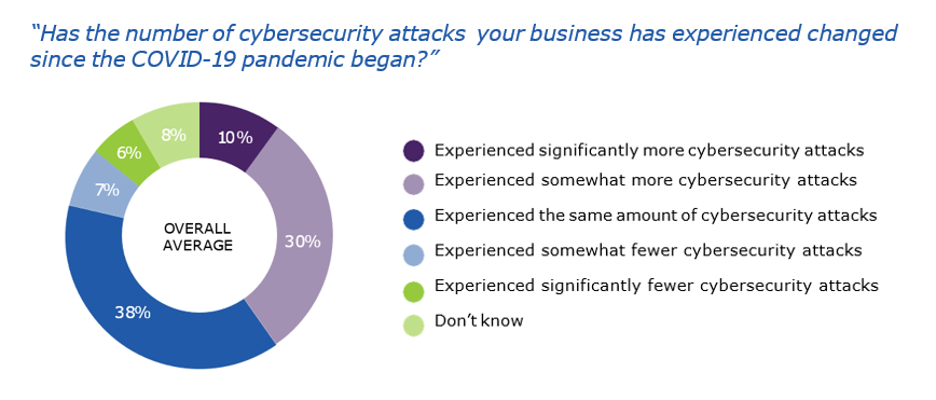
The cyber threat landscape keeps evolving at lightning-speed. According to the latest 2022 BrightCloud® Threat Report, small to medium-sized businesses (SMBs) are particularly vulnerable to becoming a victim of a ransomware attack. Cybercriminals also are becoming more selective of the organizations they target. Without human security experts and solutions at their disposable, these businesses remain susceptible to attacks.
As an MSP, there’s never been a better time to partner with a leading MDR provider to help protect your SMBs against cyberattacks. Minimize business operational disruption, maximize ongoing business continuity and bolster customer confidence with Webroot MDR.
What is MDR?
MDR is an approach to proactively manage threats and malicious activity that empowers organizations to become more cyber resilient. MDR services offer threat detection and response capabilities by augmenting cybersecurity tools with human security intelligence. Leveraging this human security expertise, MDR integrates, synthesizes and contextualizes security and other event information to hunt for, understand and respond to security incidents. This allows MSPs to offer the best combination of human expertise and a robust technology stack to help small businesses defend against future attacks.
Since MDR helps to close the gap between detection and response to threats, SMBs greatly benefit from this solution. As an MSP, you are the trusted advisor to provide your SMBs with an MDR solution to help boost their overall security stack and embrace cyber resilience.
Why should MSPs choose Webroot MDR?
SMBs are often attractive targets for bad actors looking to steal valuable data, extort money from their victims and more. We know there are many MDR solution providers on the market. However, Webroot MDR powered by Blackpoint provides a unique offering in the marketplace.
Here’s what separates Webroot MDR powered by Blackpoint from the competition:
- The fastest time in the industry from threat detection to response in 9 minutes
- A patented SNAP-Defense platform recognized by Gartner
- Best-in-class AI augmented by NSA security experts
- A competitively priced offering with unique threat detection and response capabilities
As an MSP, making the choice to purchase Blackpoint MDR through Webroot gives you:
- Seamless integration between Webroot and Blackpoint agents for quicker event investigation
- Accurate and timely insights from the BrightCloud® Threat Intelligence platform
- One-stop shop for cyber resilience that includes MDR
- Potential to obtain and lower cyber insurance costs
Ransomware, malware and phishing threats keep evolving. Your SMB customers likely don’t have the necessary security staff and tools to protect and respond to these threats. Help your customers avoid becoming a victim of data theft and extortion with industry-leading, reliable threat detection and response from Webroot. Our MDR solution can help reduce the impact of successful attacks.
Ready to discover what Webroot MDR can do for you and customers? Tune into our latest webinar.