by Dancho Danchev
With the even decreasing prices of underground tools and services, thanks to the commoditization of these very same market items, the price for renting a botnet, or purchasing access to already infected hosts, is constantly decreasing.
Although the majority of cybercriminals are actively exploiting end and corporate users while using client-side vulnerabilities in outdated third-party applications and browser plugins, there’s a separate branch of cybercriminals who specialize in delivering their payload using nothing else but good old fashioned social engineering attacks.
Following my previous post Inside a clickjacking/likejacking scam distribution platform for Facebook, in this post I will profile AnonJDB – a Java based malware distribution platform for drive-by downloads.
What exactly is AnonJDB?
Some of its features include:
- Polymorphic HTML Code Infection Page Encryption
- Custom Applet Names, Very Simple to Change
- Polymorphic 100% FUD Jar File
- Polymorphic iFrame Generator
- Polymorphic Spreading File Generator
- (Optional) Dual Infection Via Adobe Flash Update
- Hosted by Our Systems
- Website Cloner
- Guaranteed 100% FUD Jar File
- URL Redirection
- Set File Name to Save As
- Download File From an Alternate Web Server
- Choose Storage Directory Ex: %APPDATA%
- Statistics Page
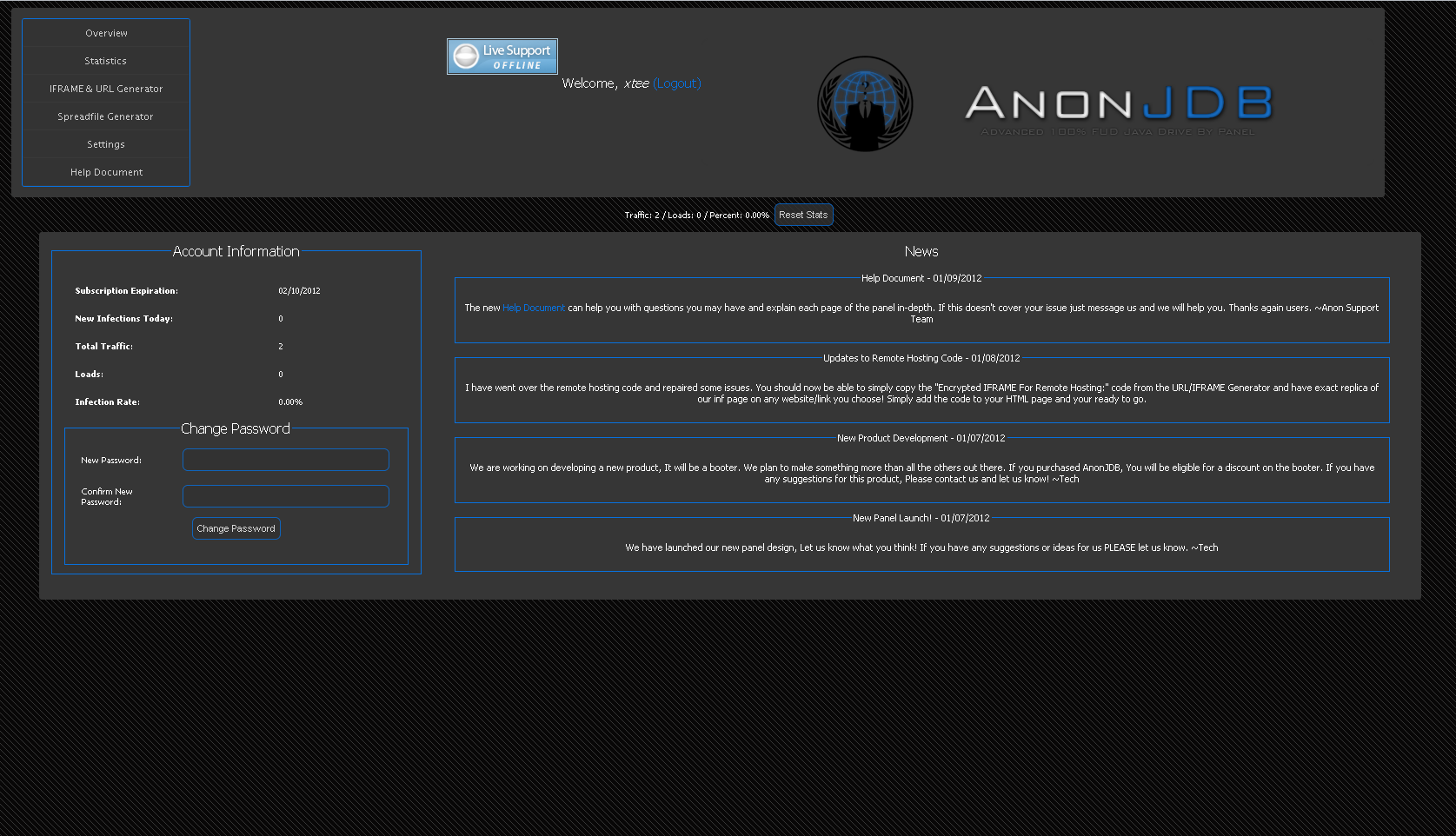
A peek inside AnonJDB’s command and control interface:
Package prices for AnonJDB:
- $10.00 USD – 1 Month
- $20.00 USD – 3 Month
- $35.00 USD – 6 Month
- $50.00 USD – 1 Year
What’s particularly interesting about AnonJDB is its easy-to-manage command and control interface, and the fact that the cybercriminals are offering Dual Infection Via Adobe Flash Update, similar to the fake Adobe Flash Player screen profiled in my previous post Inside a clickjacking/likejacking scam distribution platform for Facebook.
In the past, malicious attackers used to rely on compromised FTP accounts for embedding of malicious iFrames within the compromised domains. Nowadays, the service is outsourced to a vendor offering managed hosting services for the entire platform, including the supply of fully undetected malicious Java applets and executable binaries.
You can find more about Dancho Danchev at his LinkedIn Profile. You can also follow him on Twitter.







Please how can you prove that this is real before i make payment?