Seeking financial liquidity for their fraudulently obtained assets, novice cybercriminals continue launching new DIY cybercrime-friendly e-shops offering access to compromised accounts, harvested email databases, and accounts that have been purchased using stolen credit card data, in an attempt to diversify their portfolio and, consequently, increase the probability of a successful purchase from their shops.
In this post, I’ll profile one of the most recently launched cybercrime-friendly e-shops, continuing the “A peek inside a boutique cybercrime-friendly E-shop” series.
More details:
Entry page for the cybercrime-friendly E-shop:
Welcome page for the cybercrime-friendly e-shop:
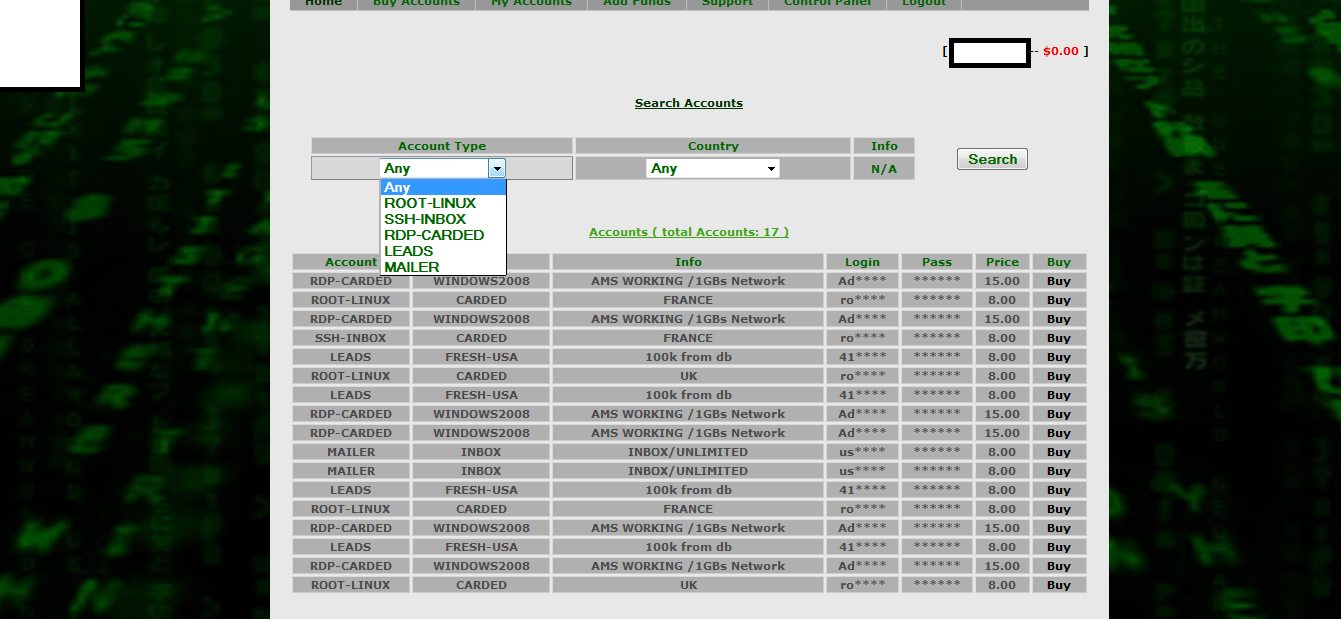
Sample inventory of fraudulently obtained accounting assets:
The E-shop currently offers RDP, Root and SSH accounting data, as well as DIY Spam Mailers and “marketing leads”, namely, harvested databases of email addresses, with the prices varying between $8-$15. Thanks to the overall availability of DIY crimeware and malware loaders, next to stolen credit card details available for purchase, we expect to see more of these E-shops, with the novice cybercriminals behind them continuing to rely on basic market development practices such as penetration pricing, in an attempt to steal market share from sophisticated cybercriminals offering the same fraudulently obtained assets, as theirs.
Go through previous post profiling the activities of related e-shops:
- A peek inside a boutique cybercrime-friendly E-shop
- A peek inside a boutique cybercrime-friendly E-shop – part two
- A peek inside a boutique cybercrime-friendly E-shop – part three
- A peek inside a boutique cybercrime-friendly E-shop – part four
We’ll continue monitoring this emerging trend within the cybercrime ecosystem, and post new updates as soon as new boutique cybercrime-friendly e-shops get launched.
You can find more about Dancho Danchev at his LinkedIn Profile. You can also follow him on Twitter.







No honor among thieves.