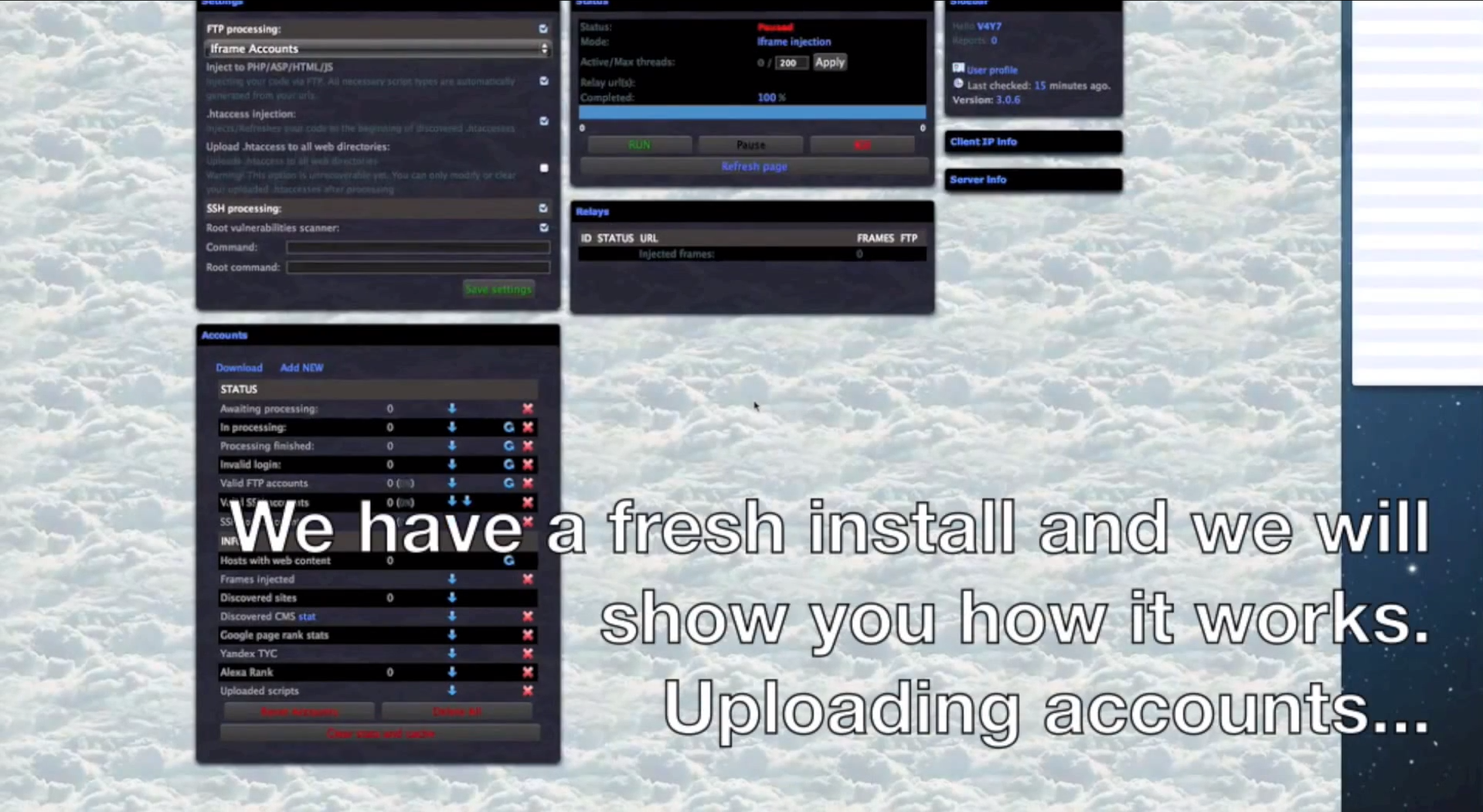
Utilizing the very best in ‘malicious economies of scale’ concepts, cybercriminals have recently released a privilege-escalating Web-controlled mass iFrame embedding platform that’s not just relying on compromised FTP/SSH accounts, but also automatically gains root access on the affected servers in an attempt to target each and every site hosted there. Similar to the stealth Apache 2 module that we profiled back in November, 2012, this platform raises the stakes even higher, thanks to the automation, intuitive and easy to use interface, and virtually limitless possibilities for monetization of the hijacked traffic.
Let’s take an exclusive look inside the new platform, offer screenshots of the platform in action, discuss its key features, the pricing scheme, and discuss why its release is prone to cause widespread damage internationally, given the obvious adoption that’s beginning to take place.
More details:
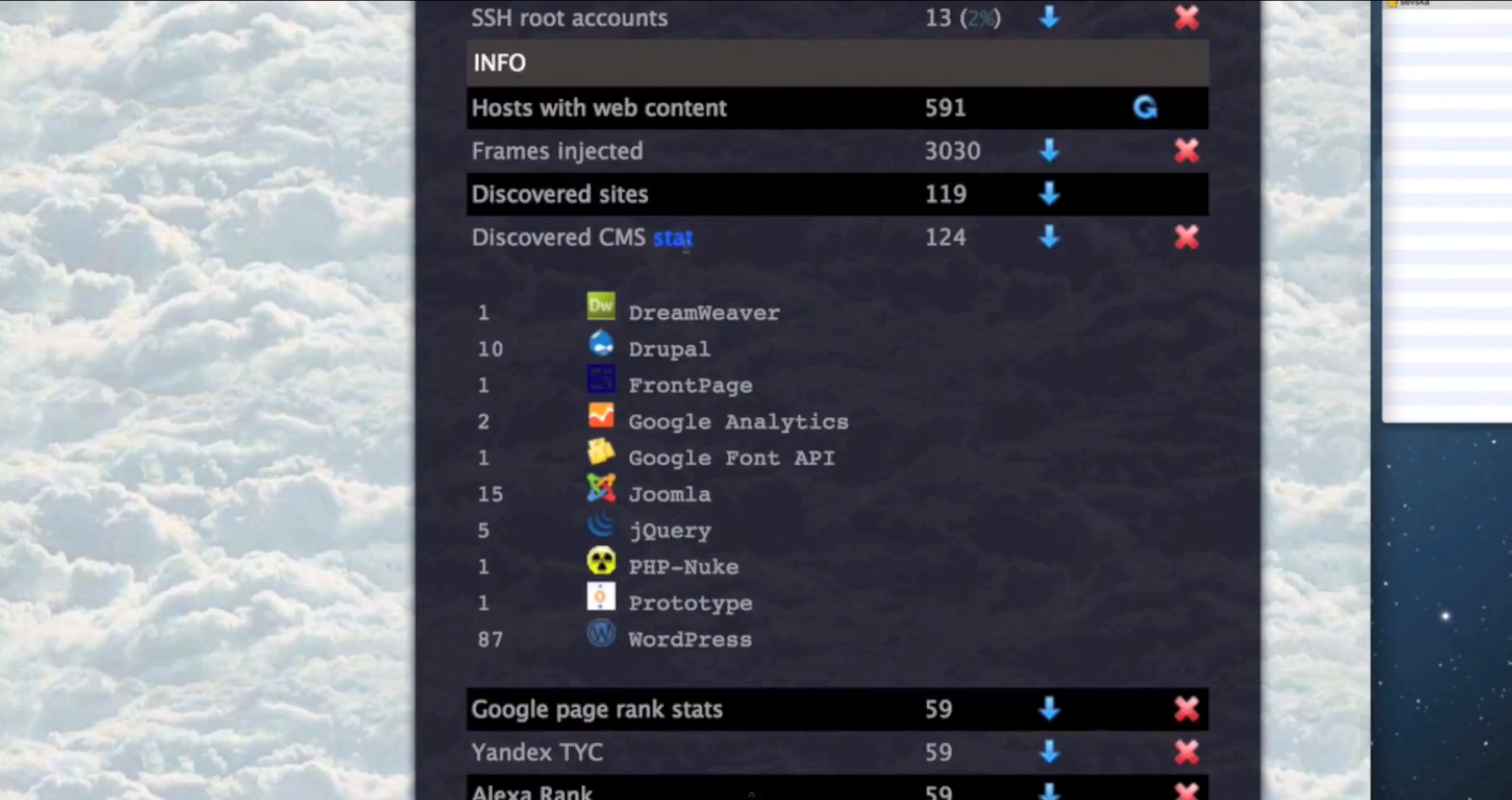
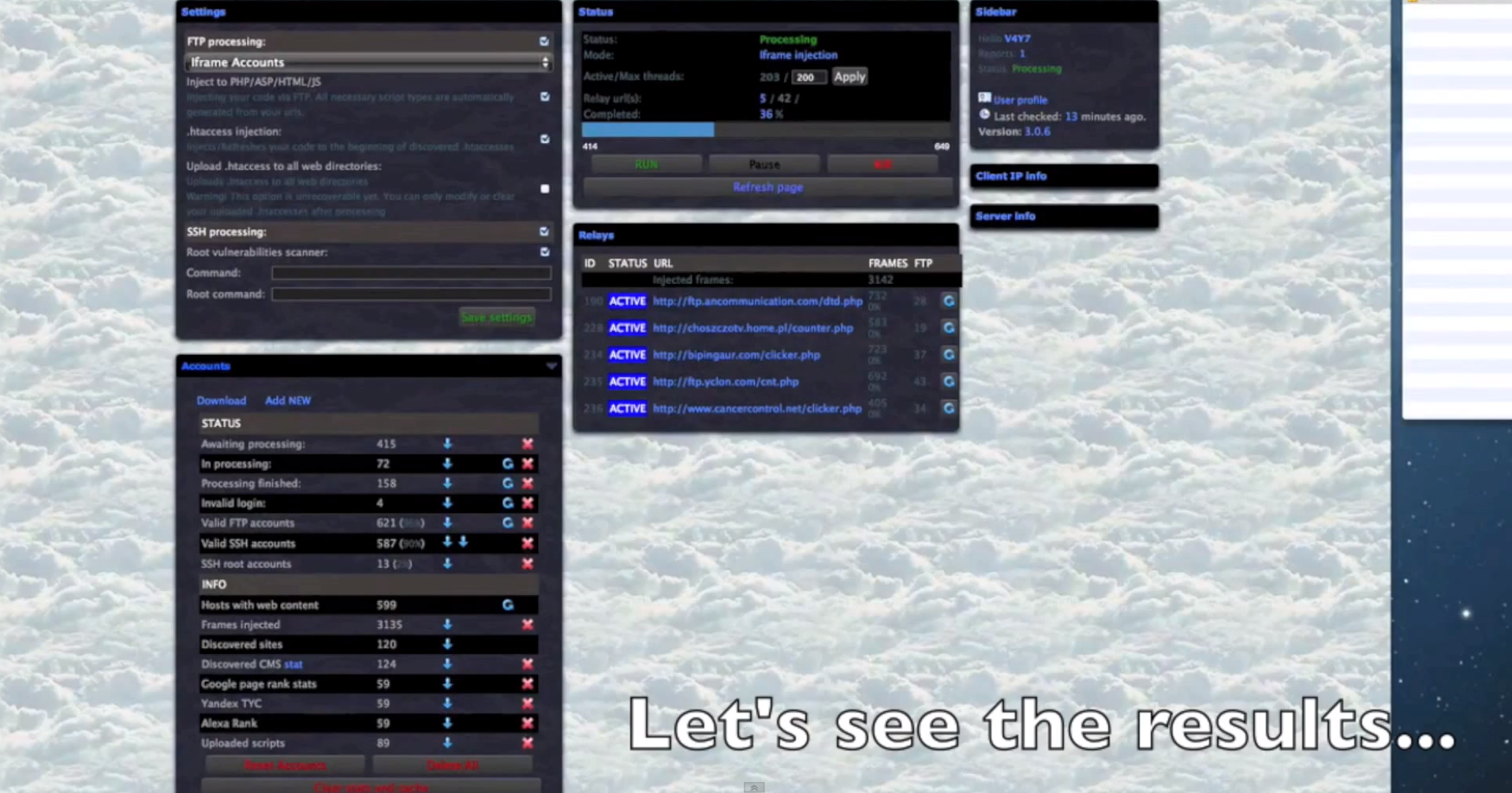
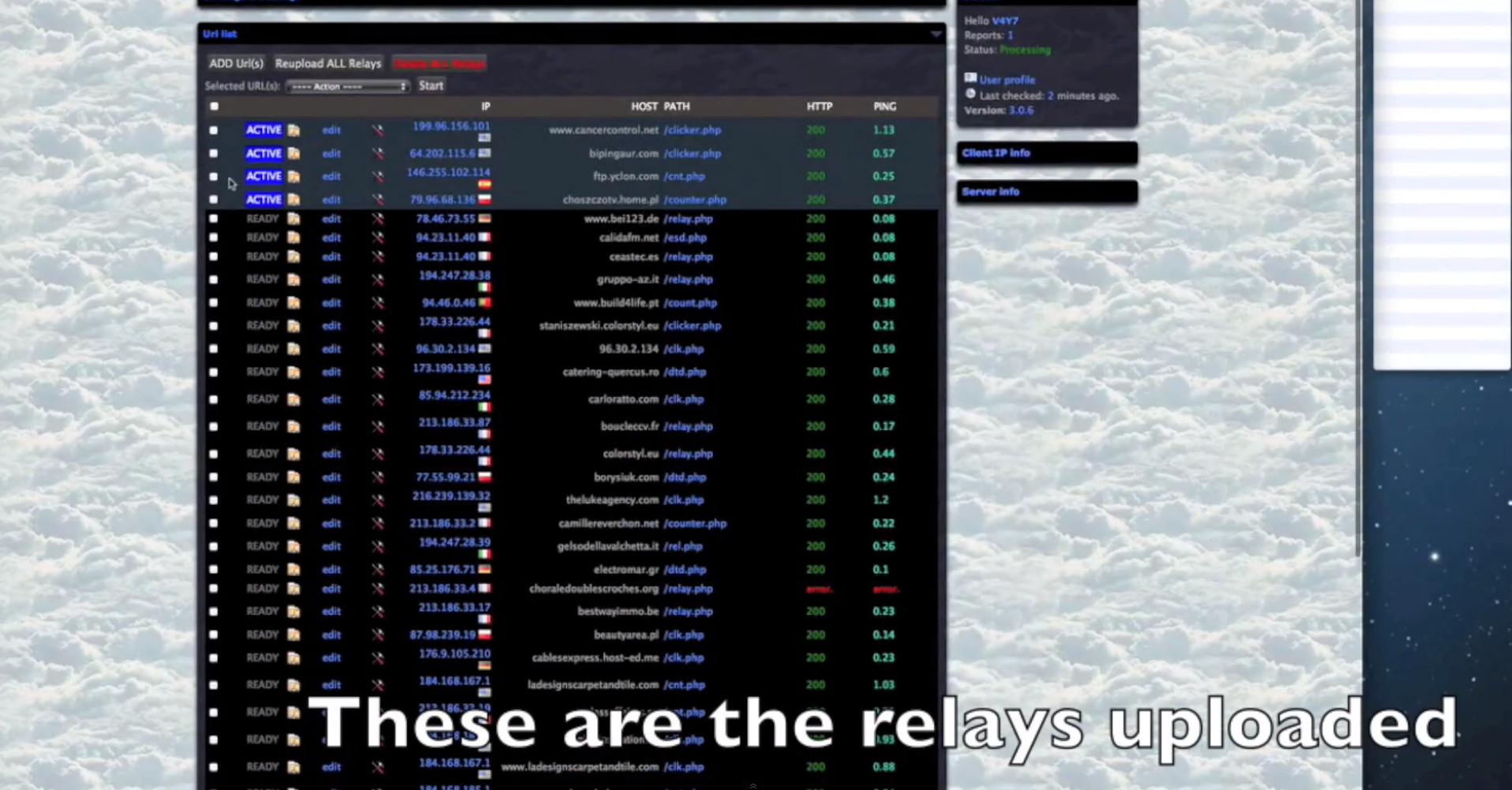
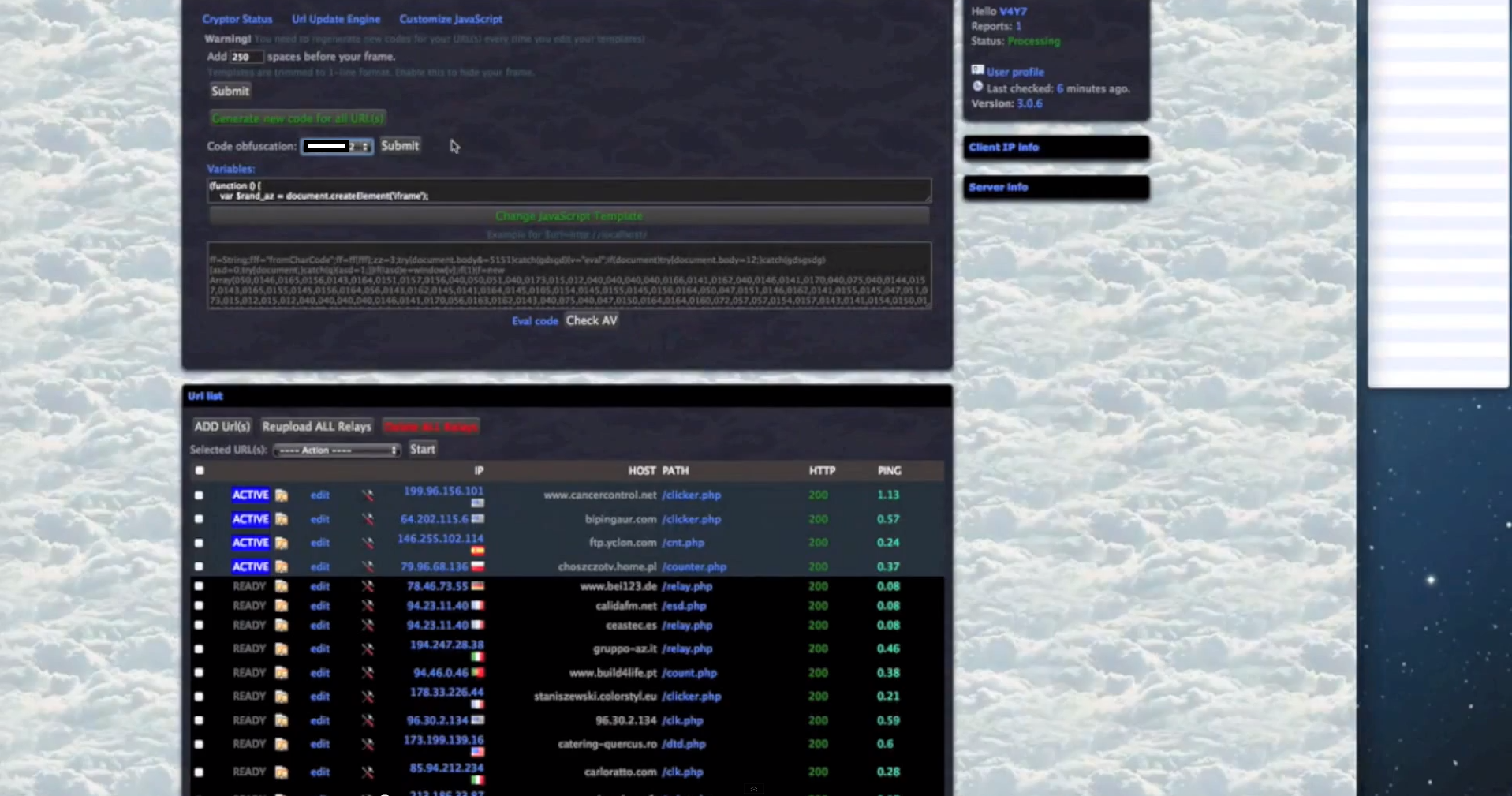
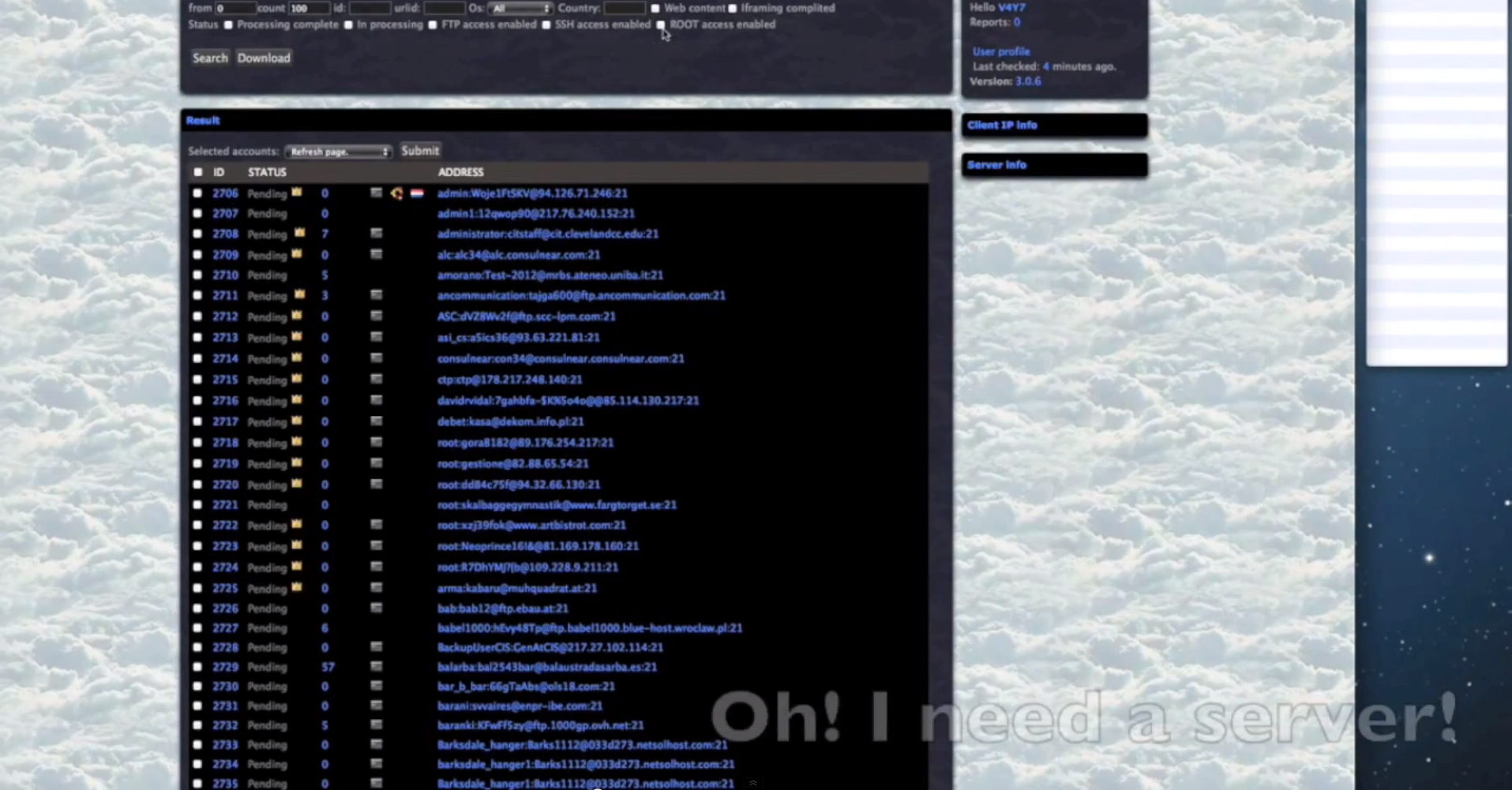
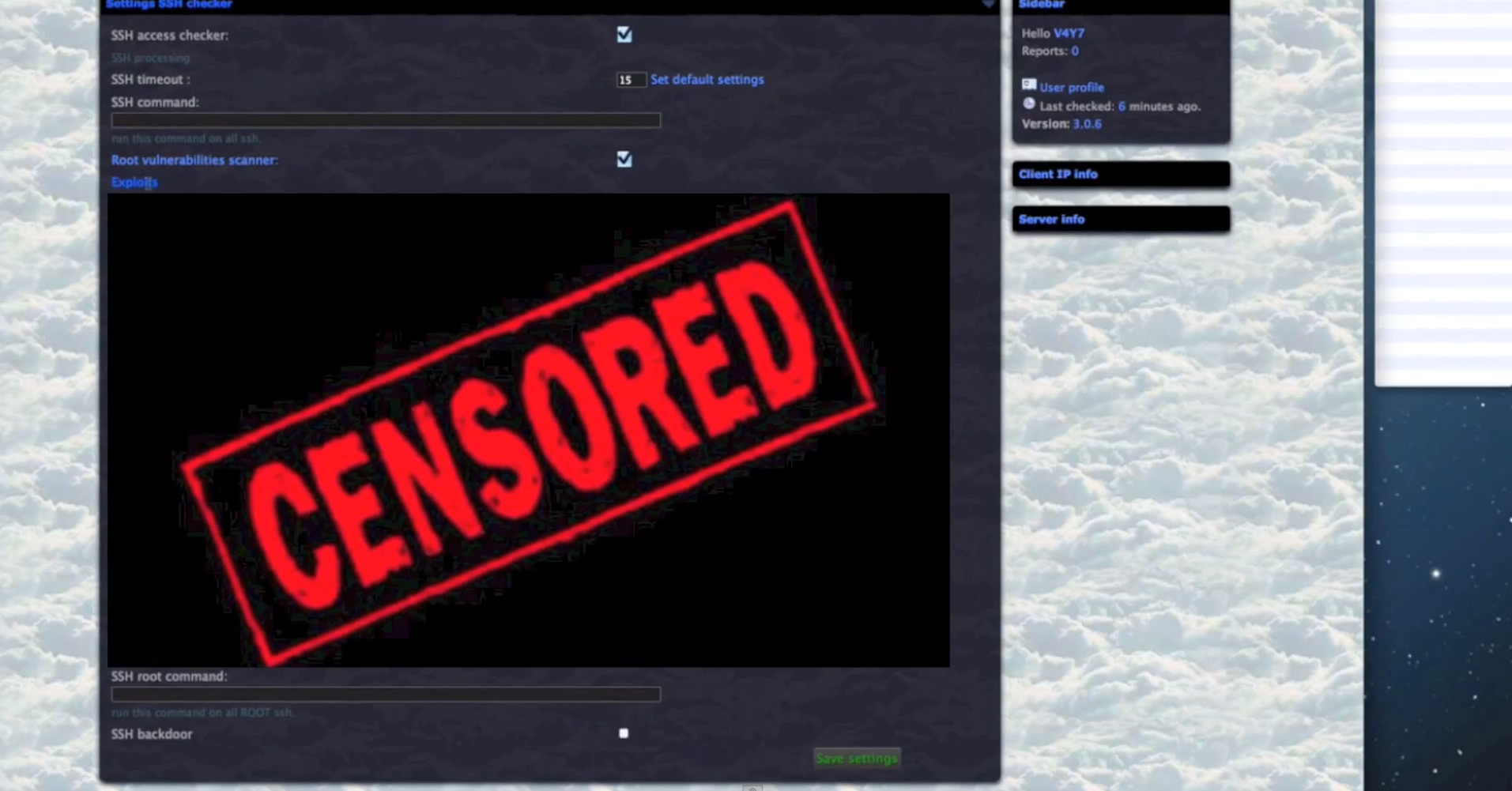
Some of the core features of the malicious platform include:
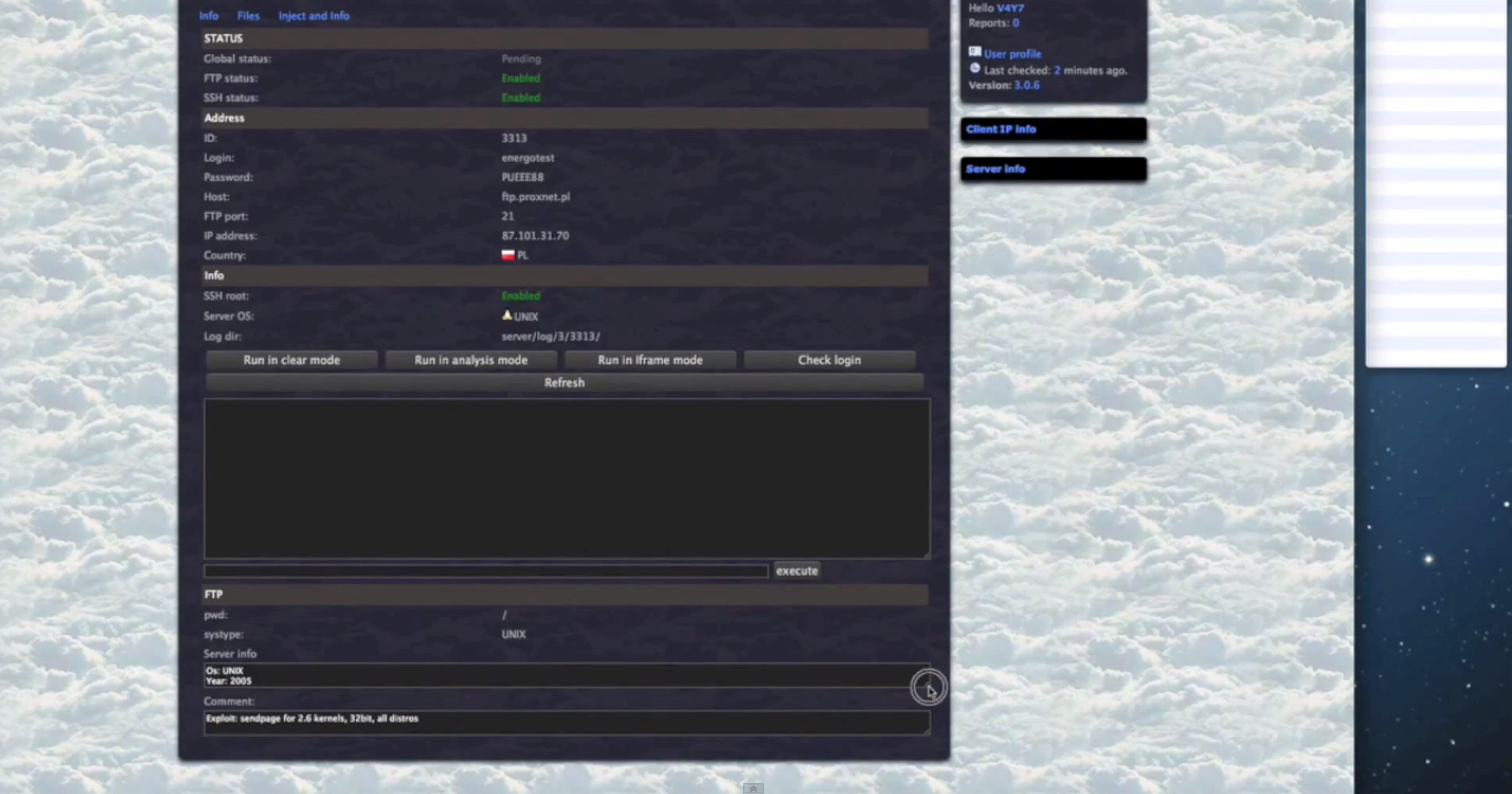
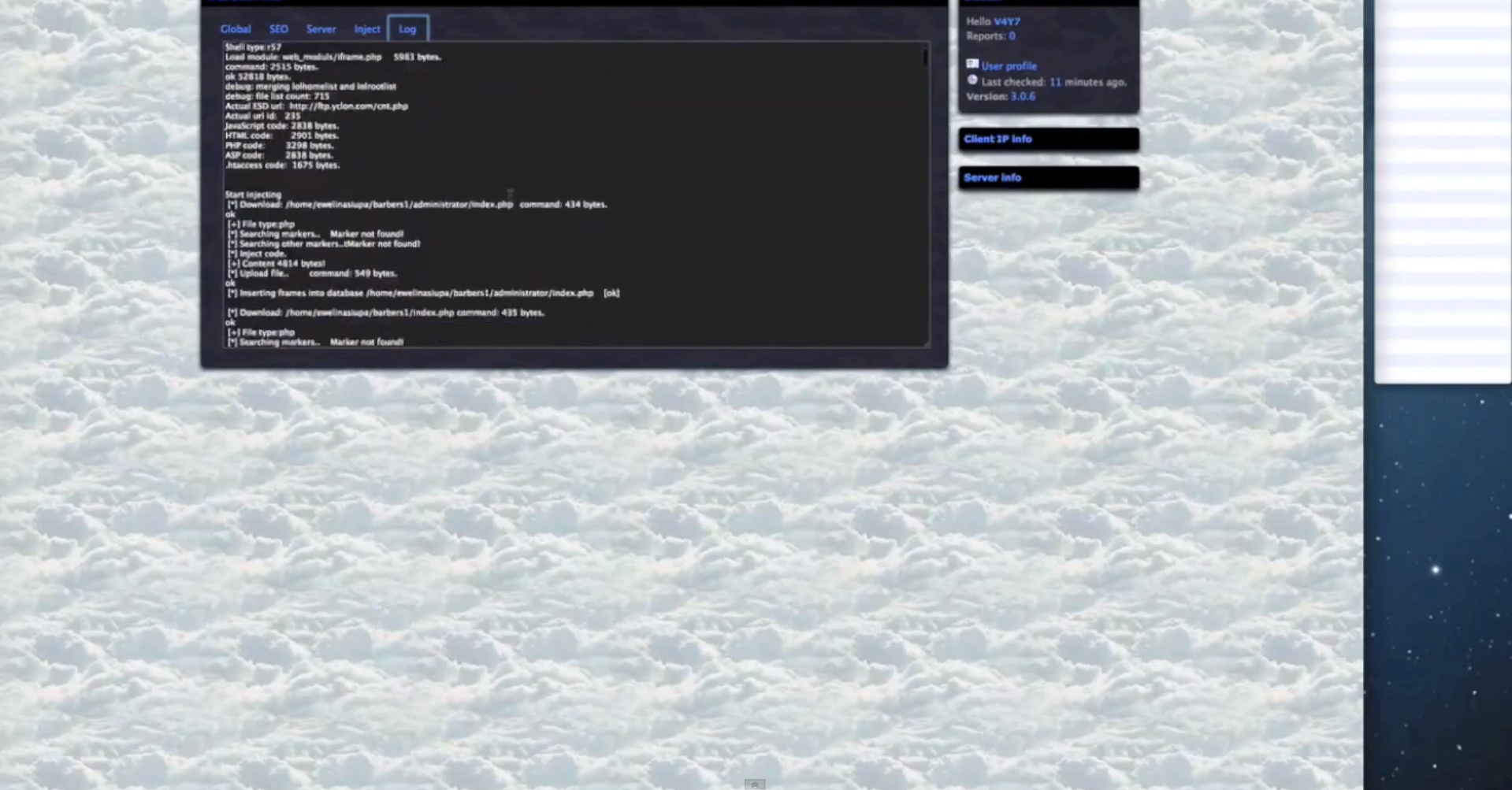
- Since the cybercriminals using the platform are escalating their privileges, once they obtain root access on the servers, they have complete access to the databases hosted there.
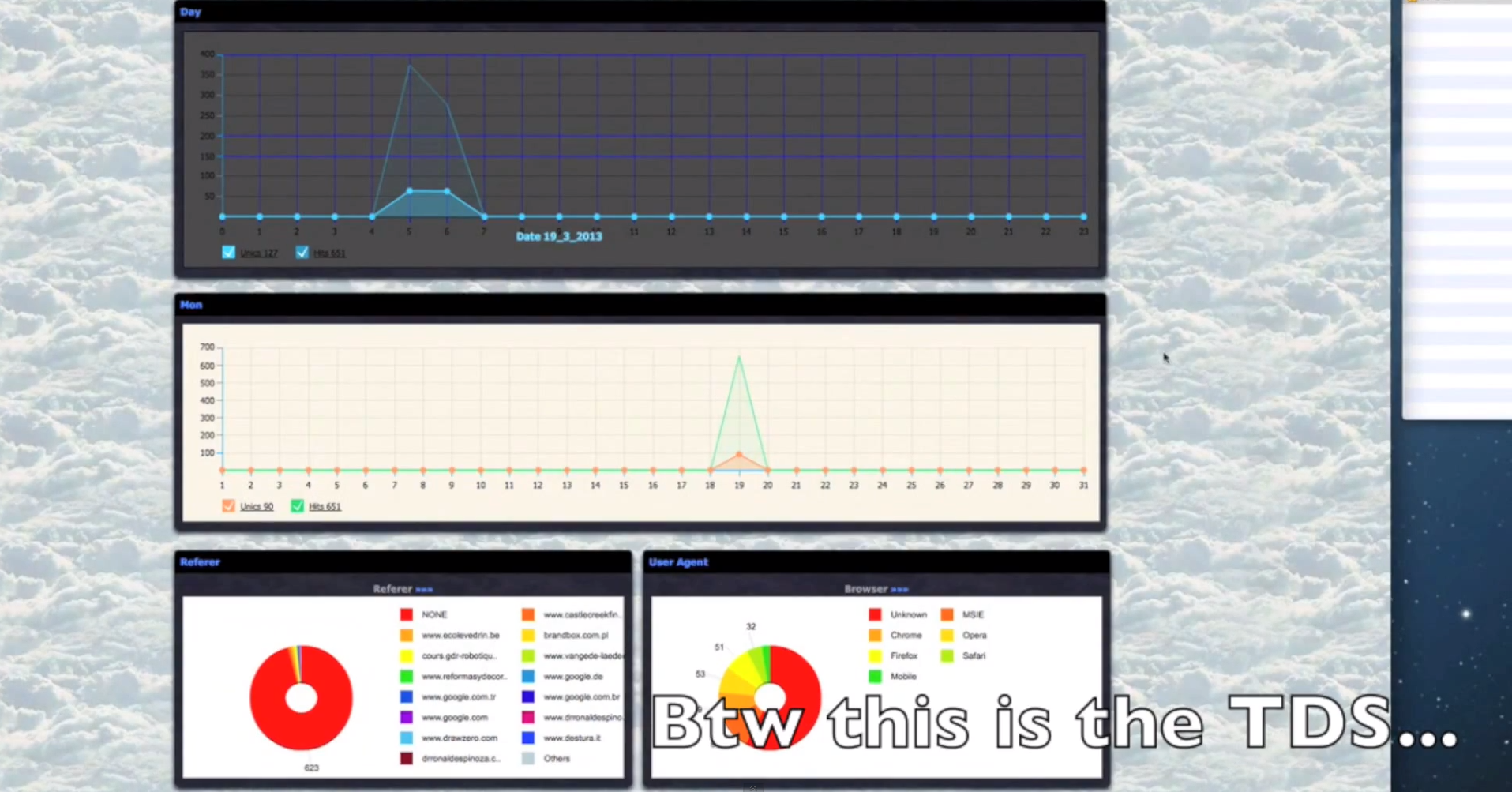
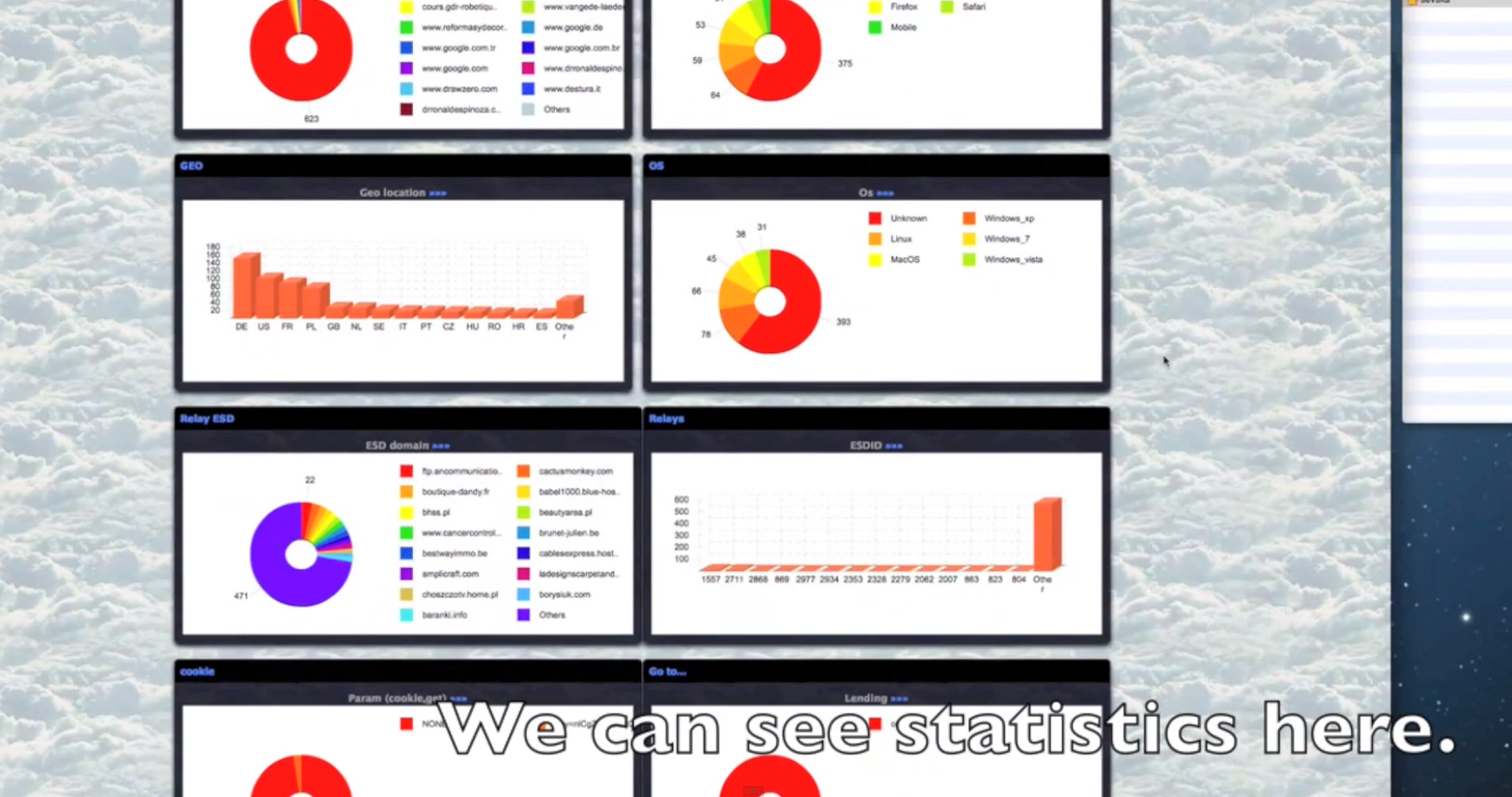
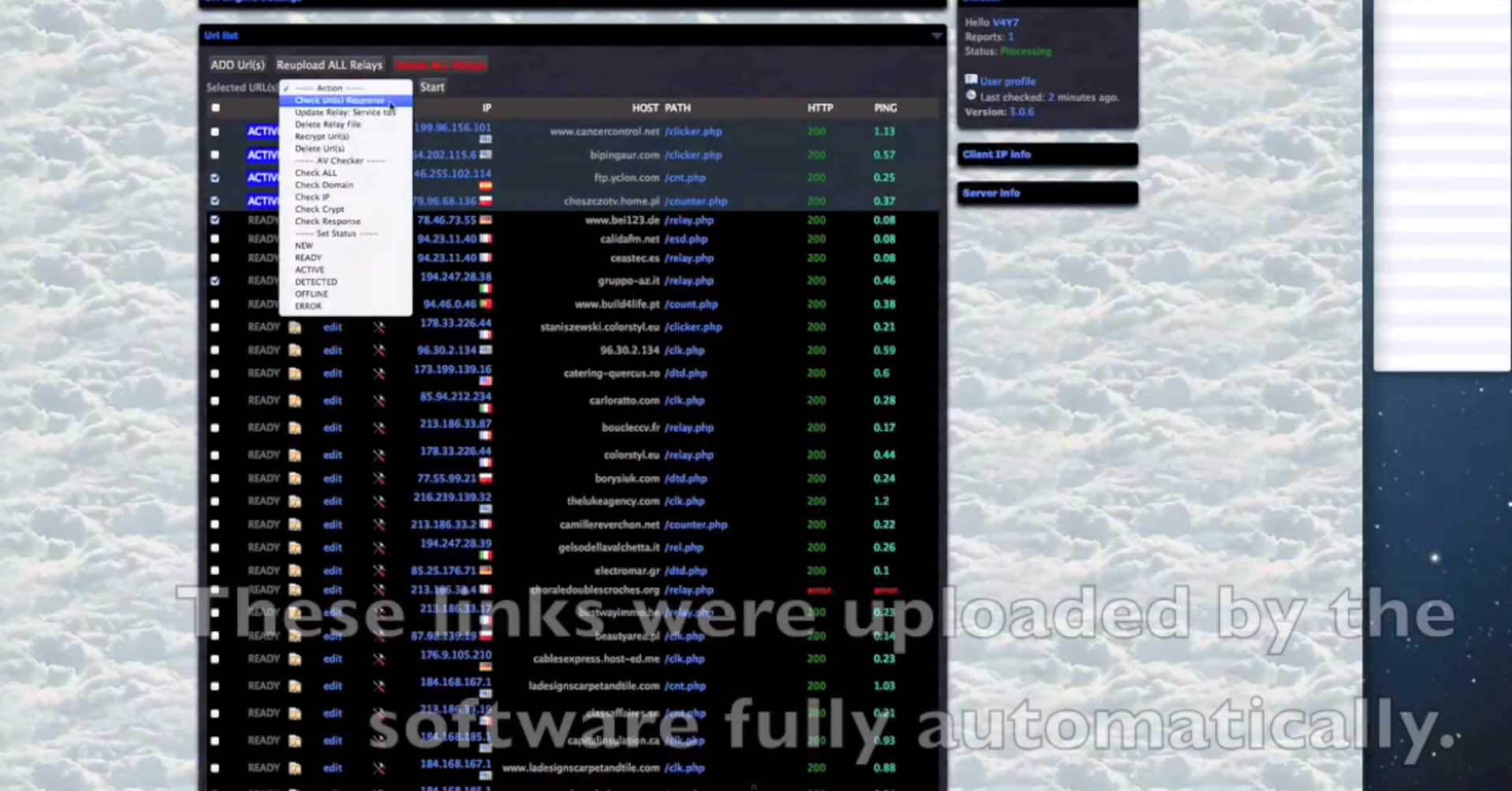
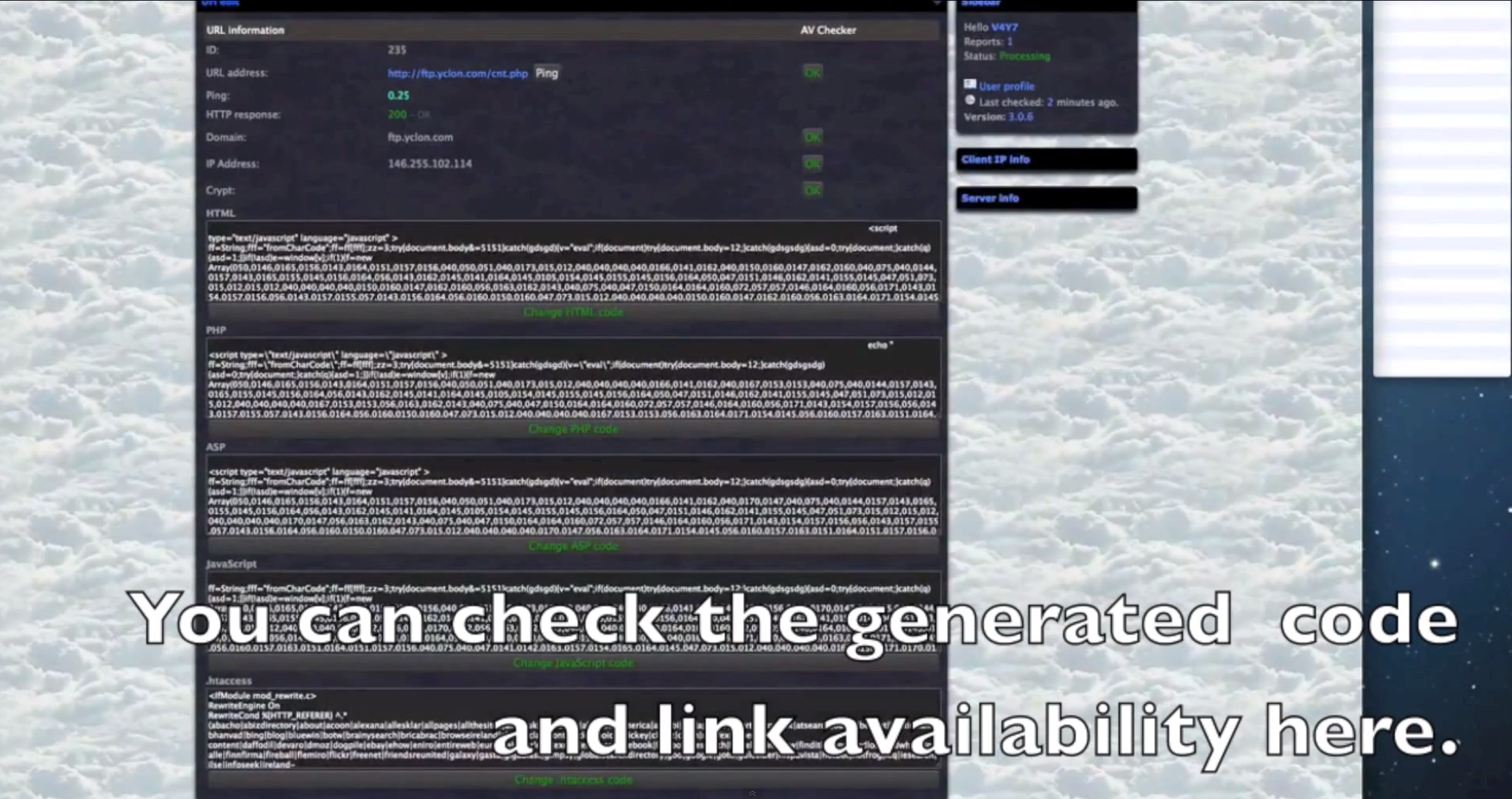
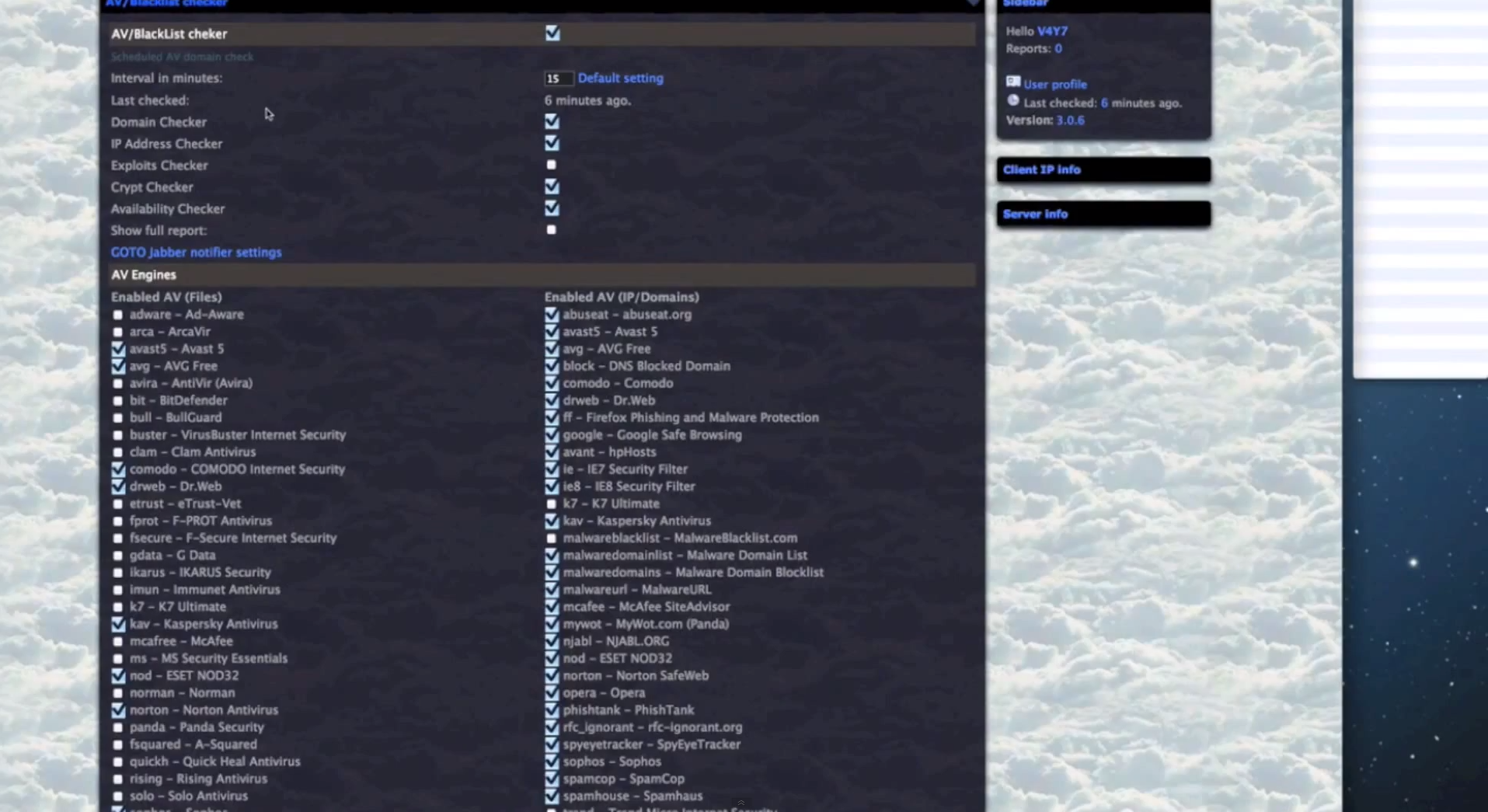
- Extremely diversified set of anti-virus iFrame reputation checking capabilities, all done in an automated fashion.
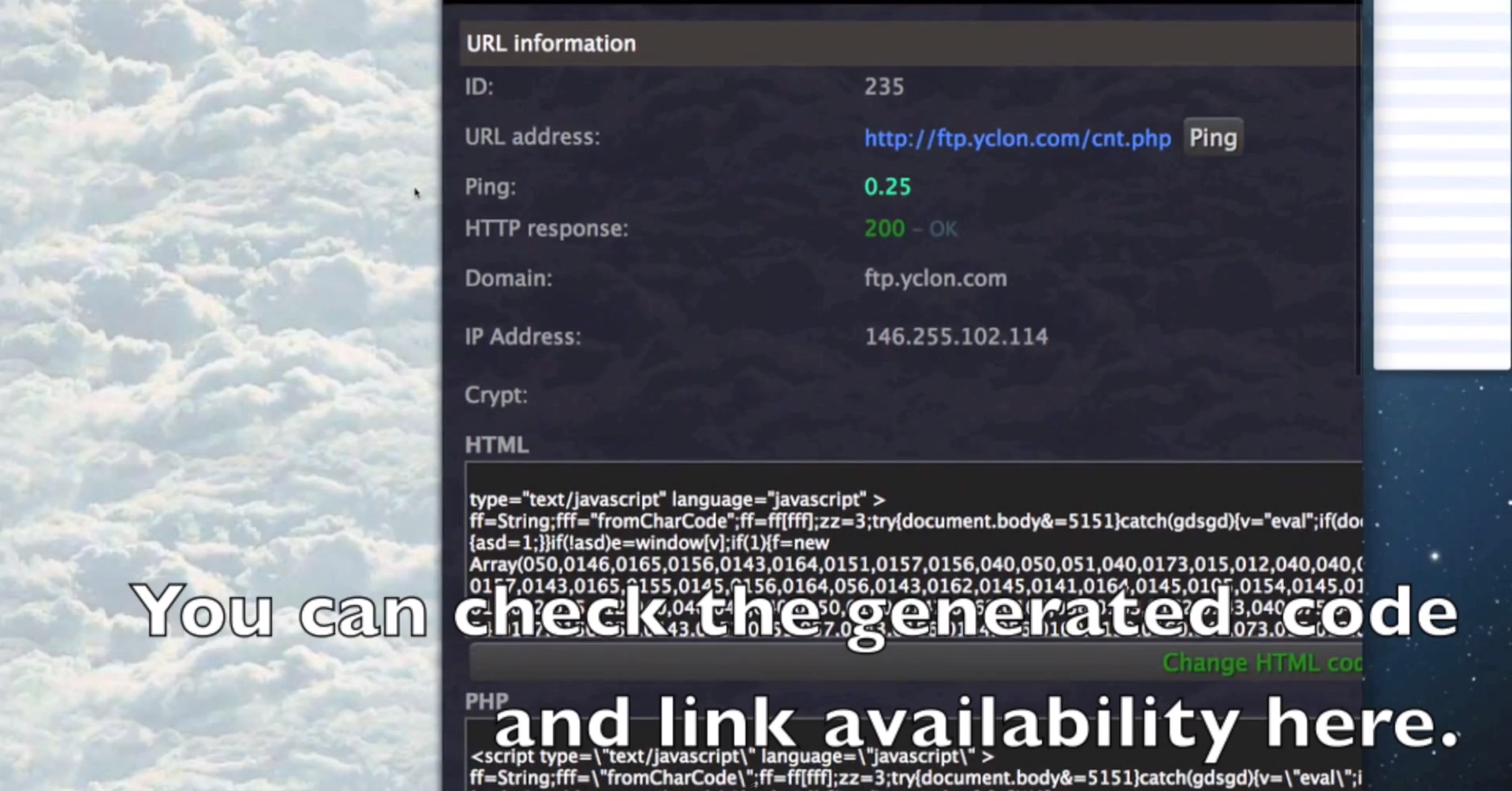
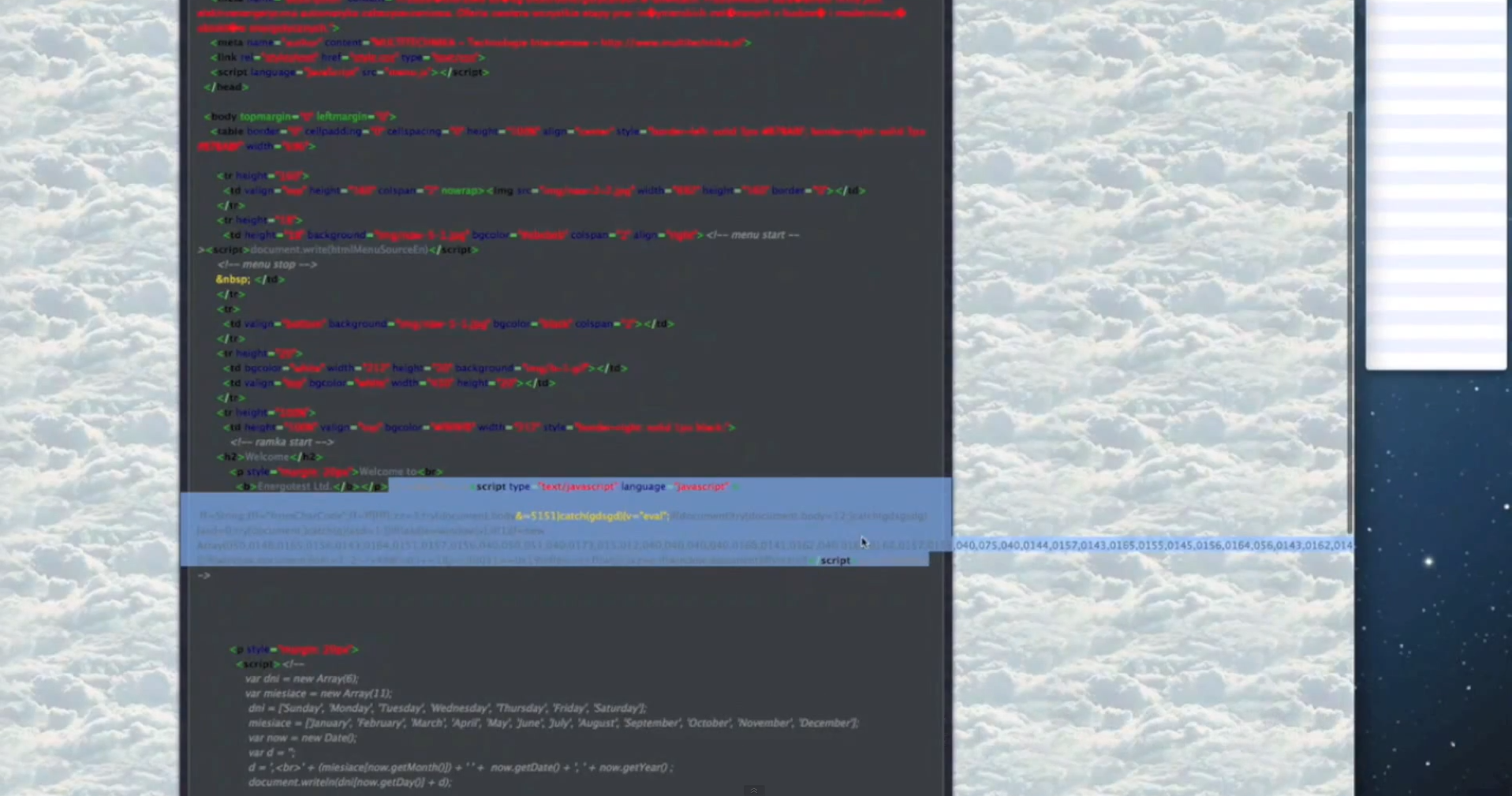
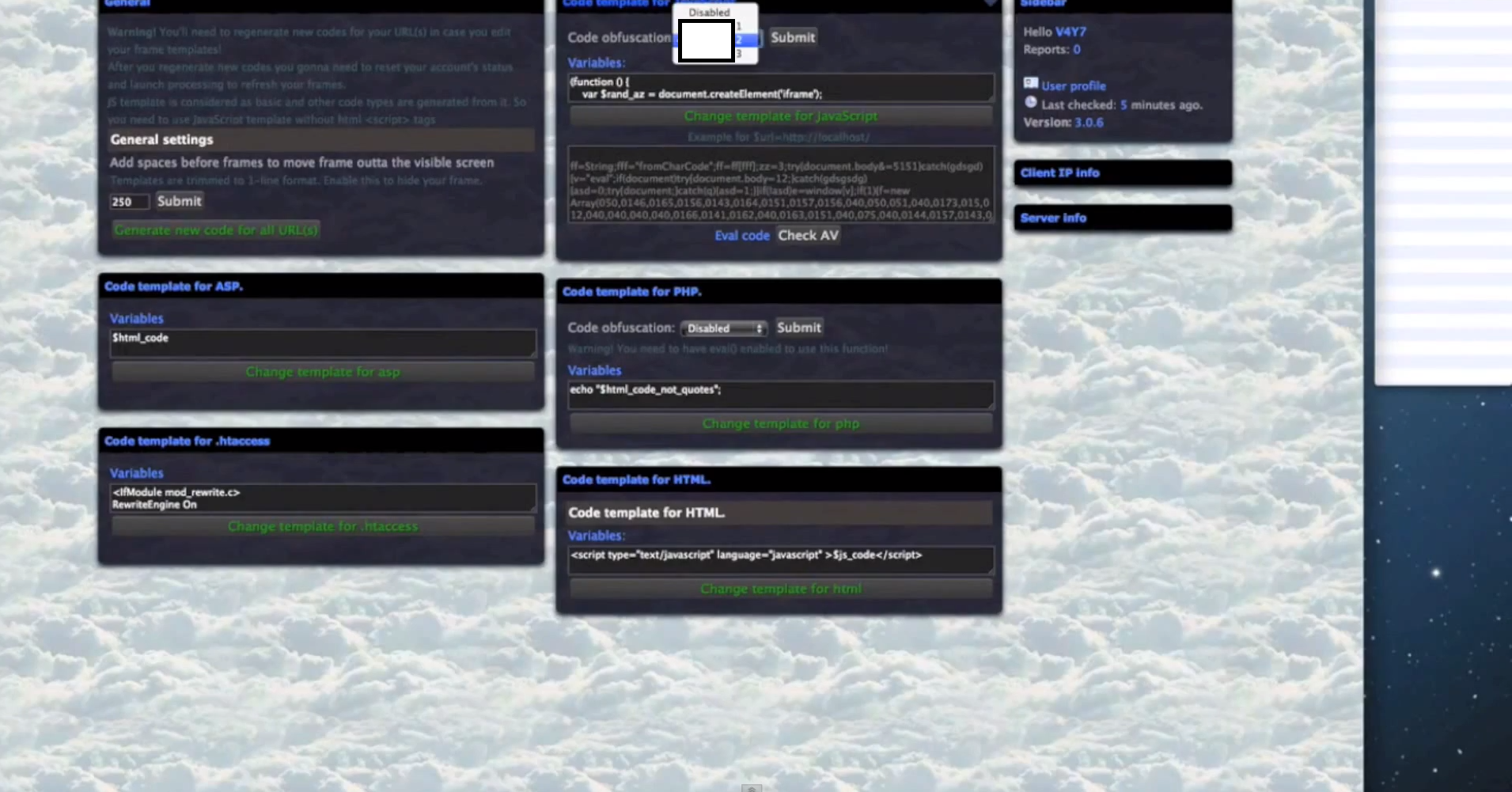
- The iFrames are obfuscated on the fly using Paunch’s (author of the Black Hole Exploit Kit) iFrame obfuscating service, further demonstrating the existence of an ecosystem, rather than a basic market with sellers and buyers.
- Despite the use of Paunch’s script obfuscation server, as well as the use of the Black Hole Exploit Kit in the demonistration, the author of the iFrame embedding platform is offering commercial access to the CritXpack.
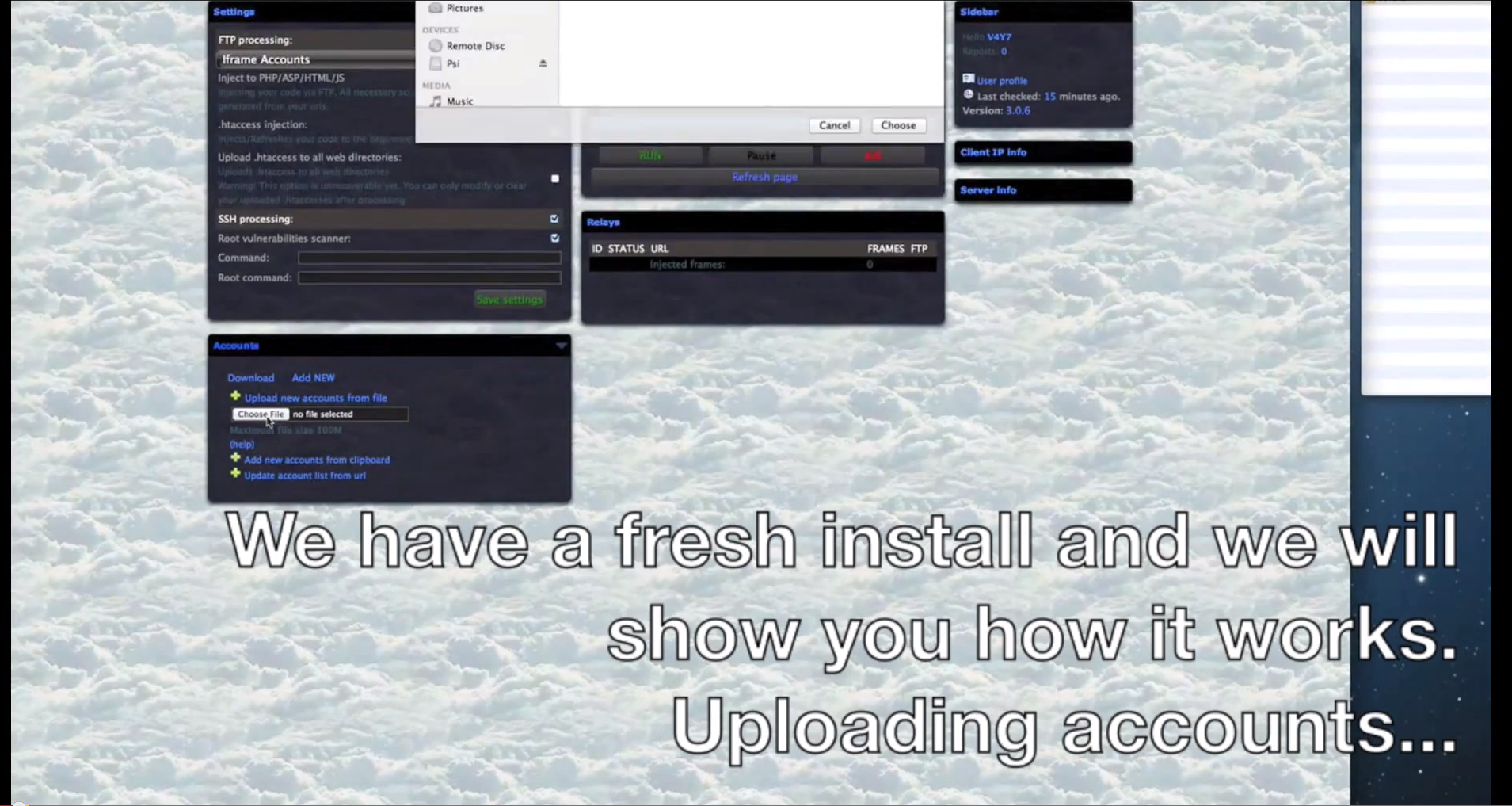
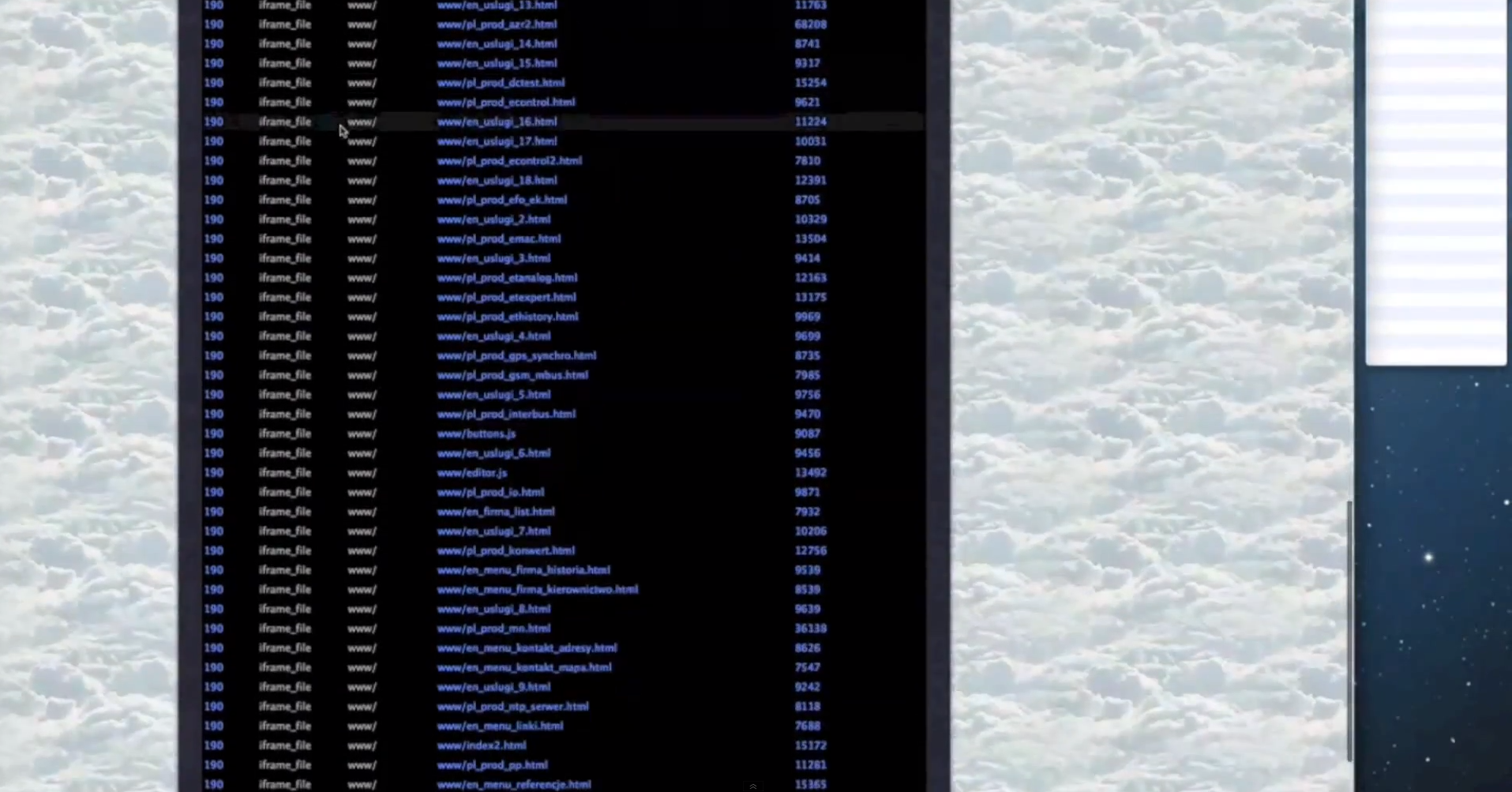
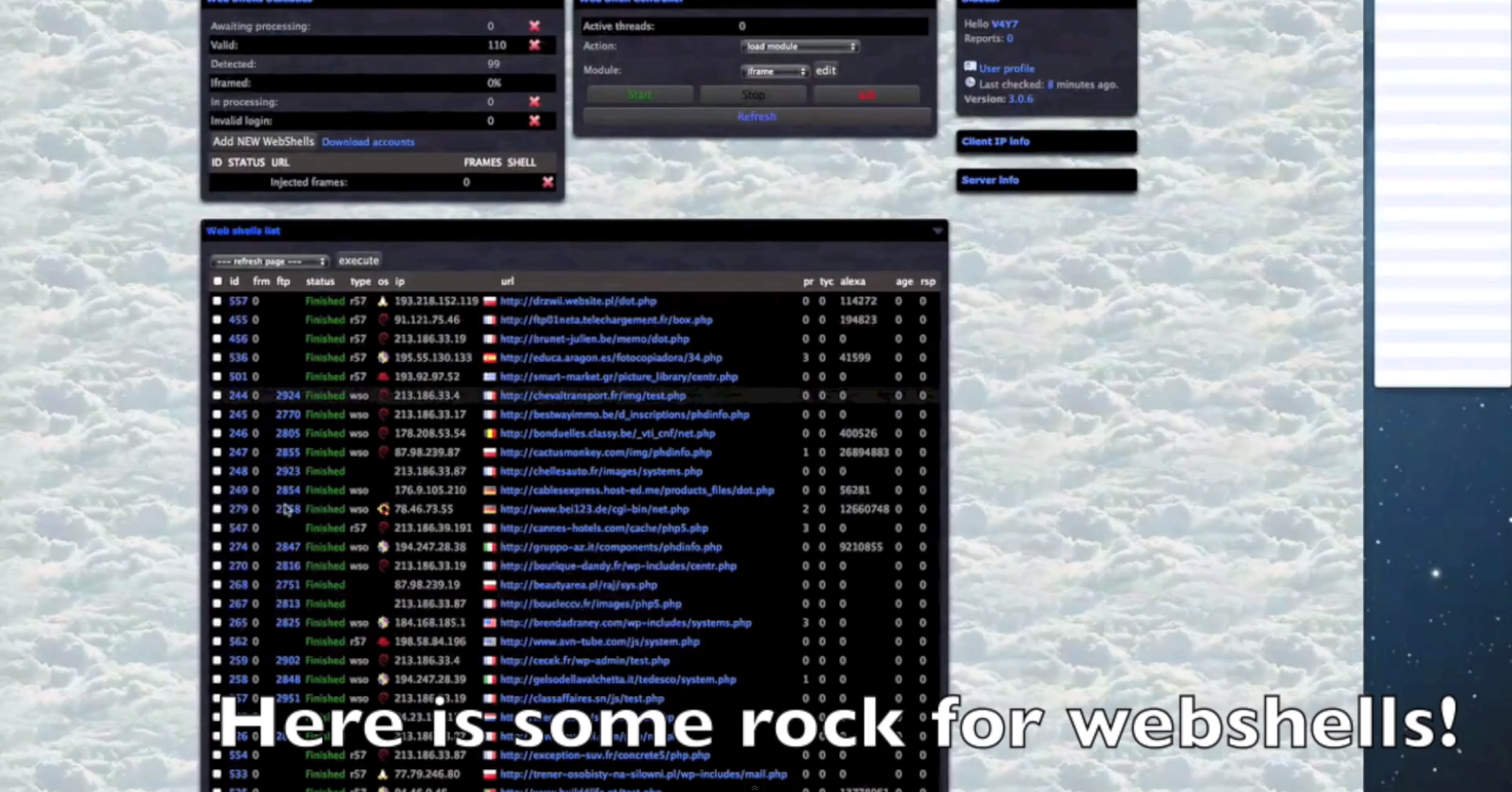
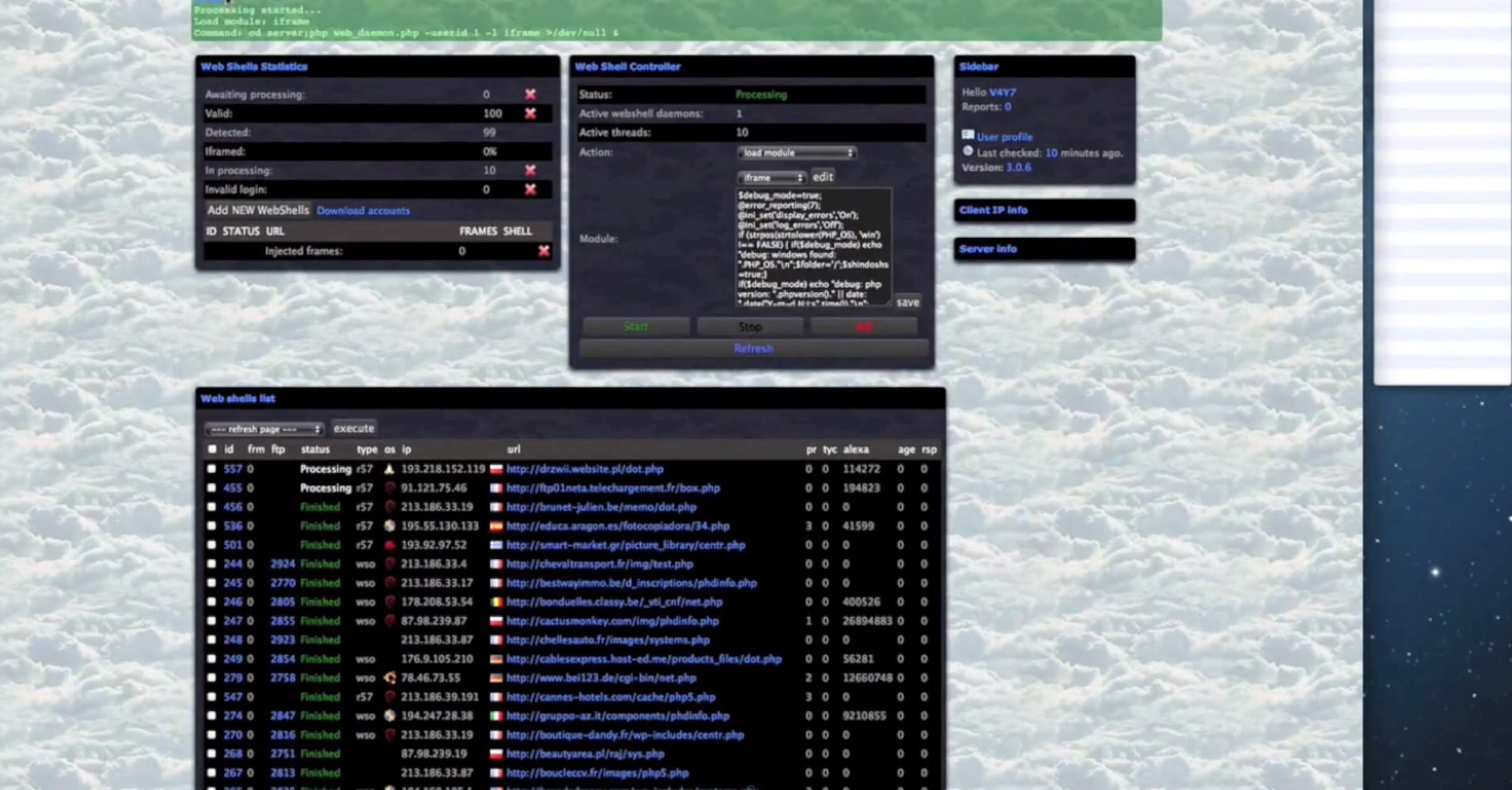
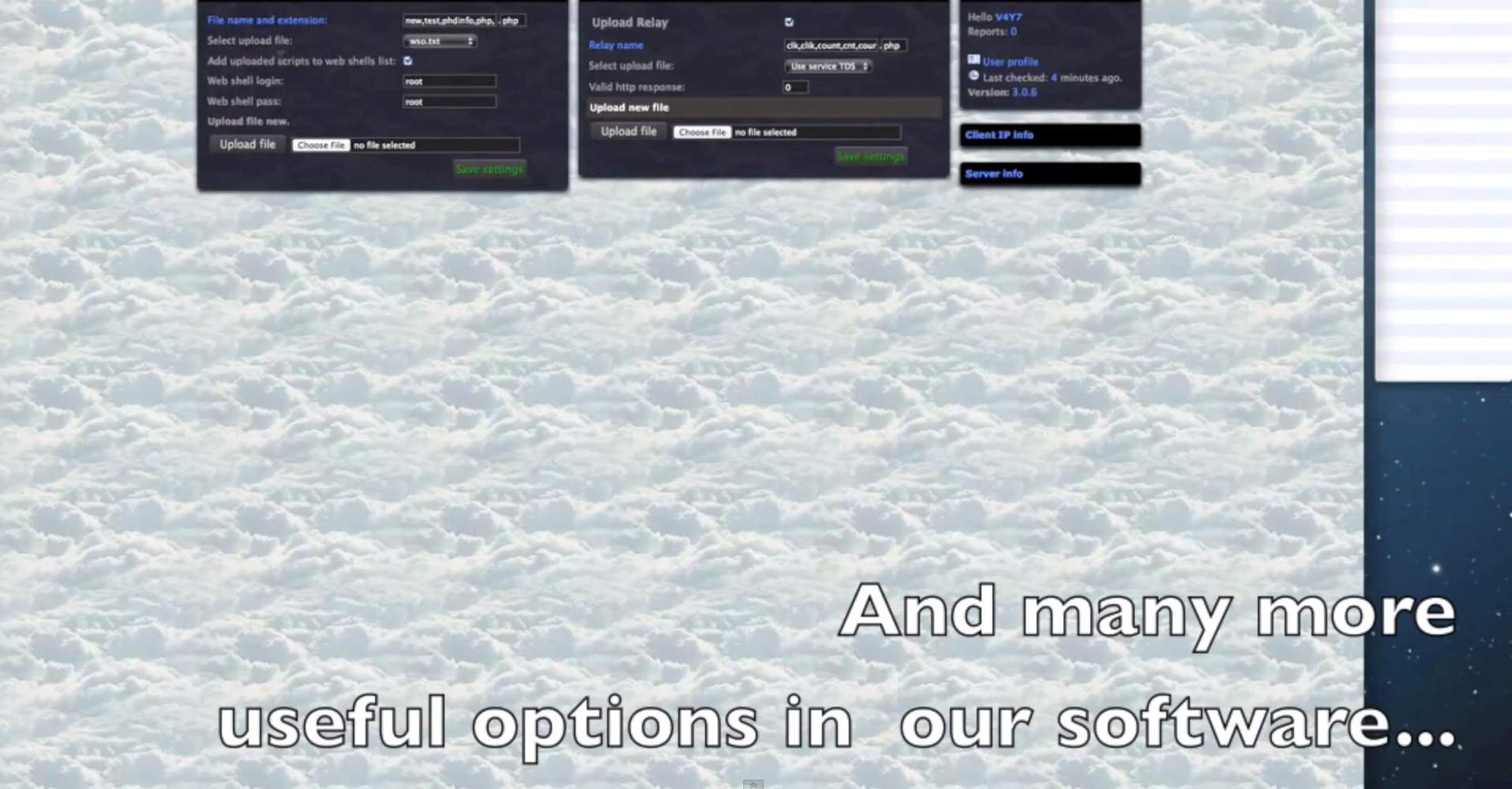
- The platform can embedd iFrames to PHP/ASP/HTML/JS/SWF files.
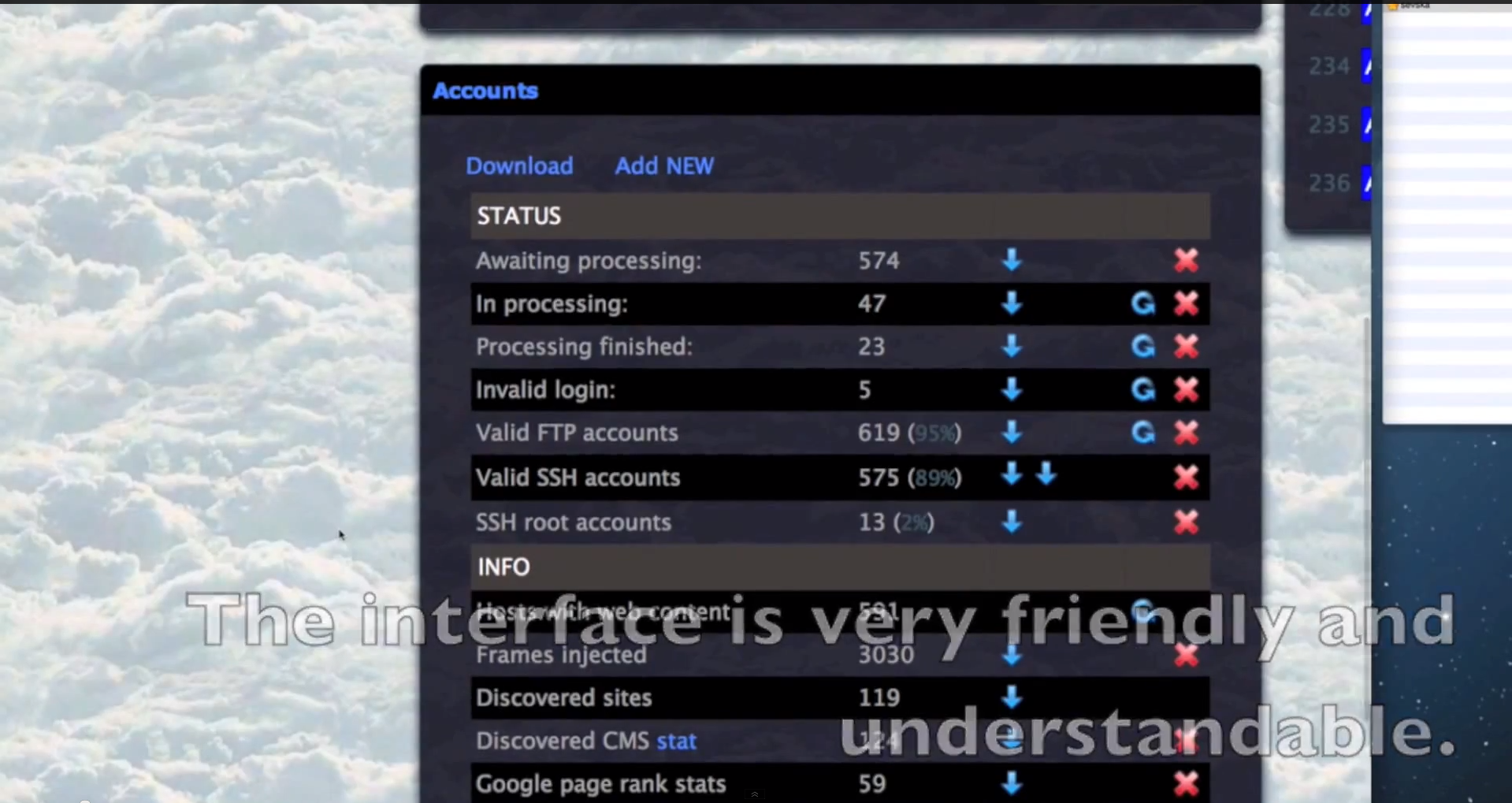
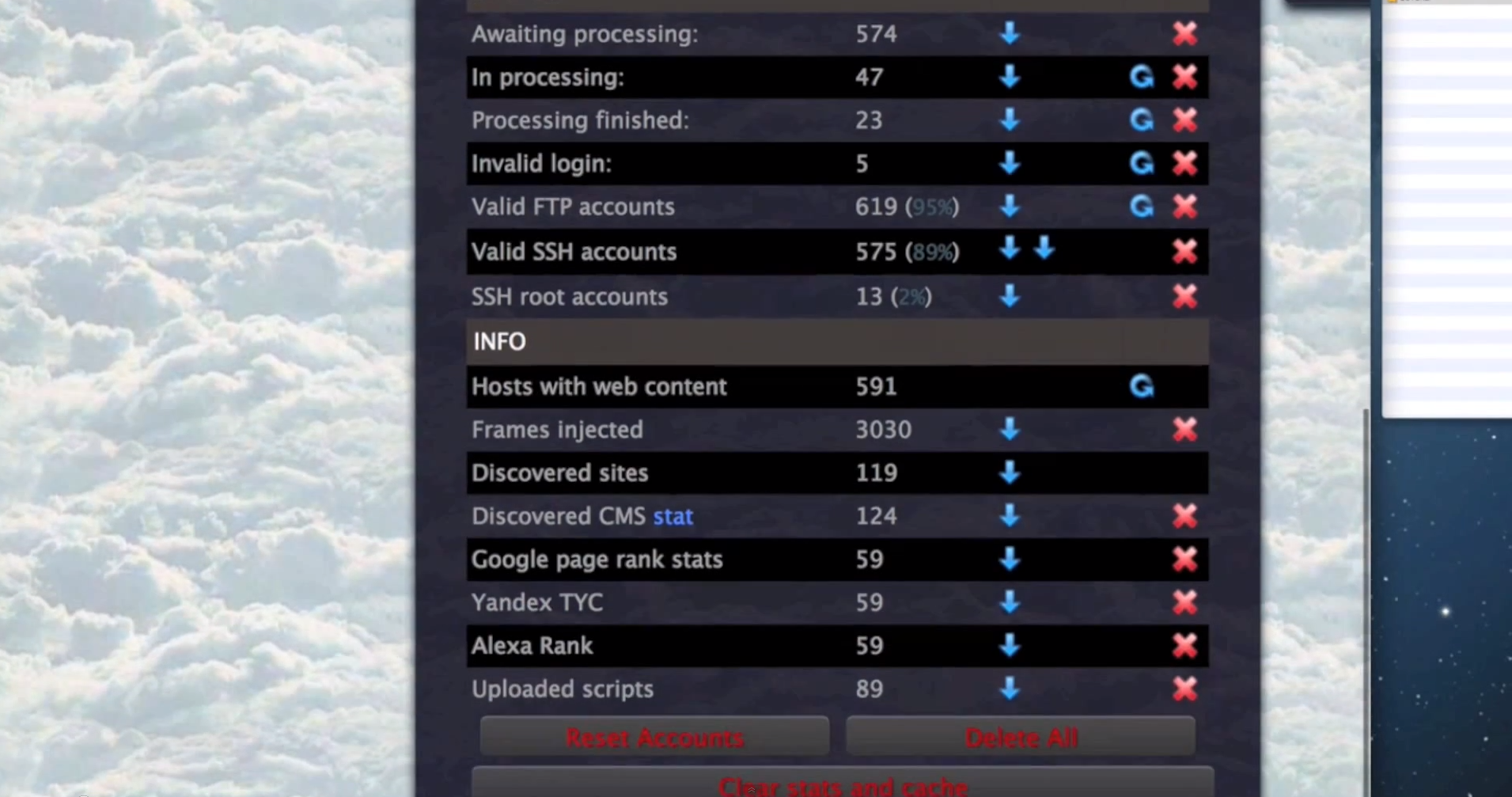
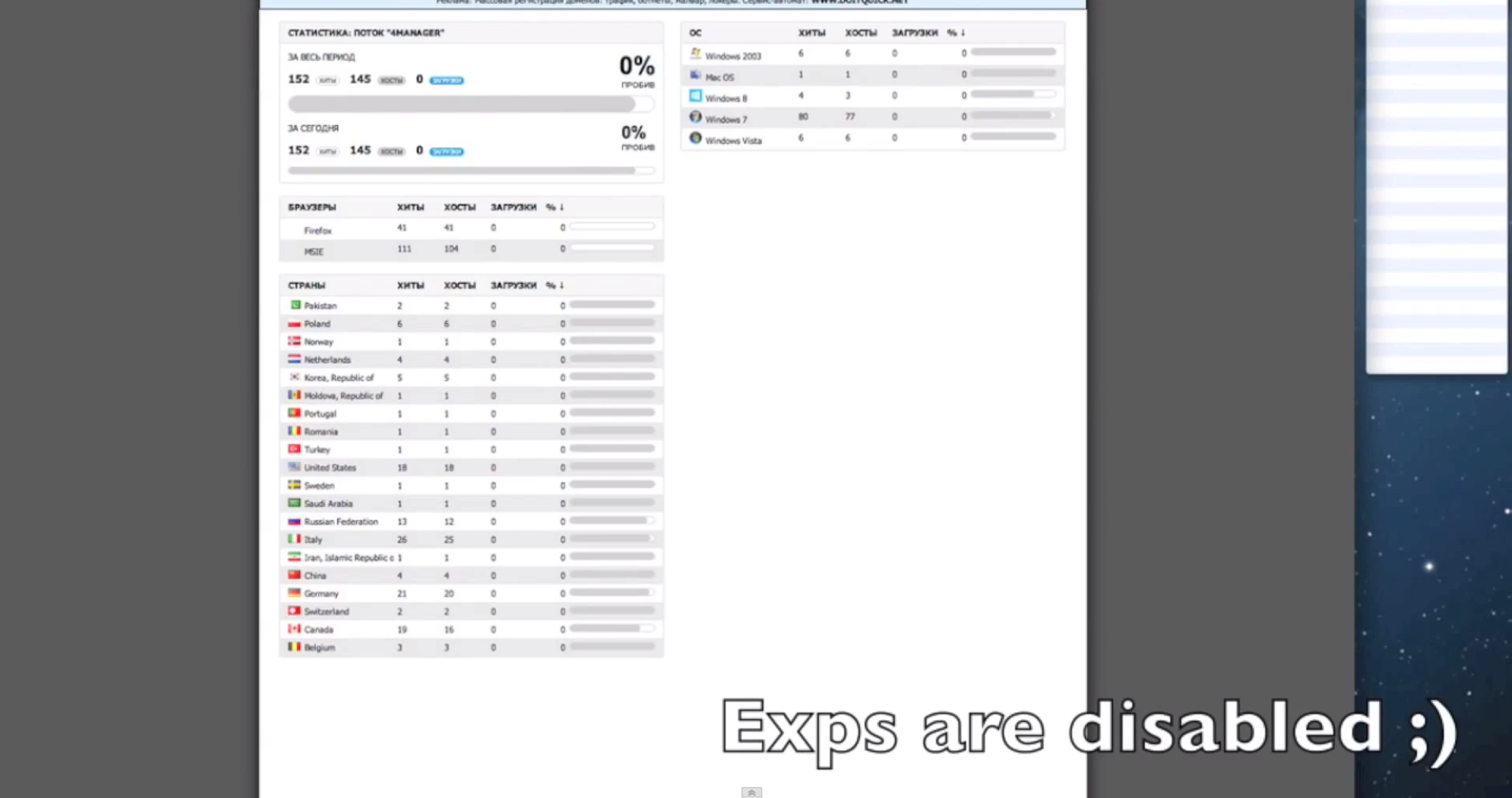
- It has built-in SEO-friendly statistics, including Alexa Rank and Google Page Rank.
- It has built-in CMS (Content Management System) detection capabilities, and is therefore comparible with the most popular ones.
- Traffic can be maliciously “optimized” and redirected to a set of pre-defined URLs, based on the browser and operating system used by the visitors.
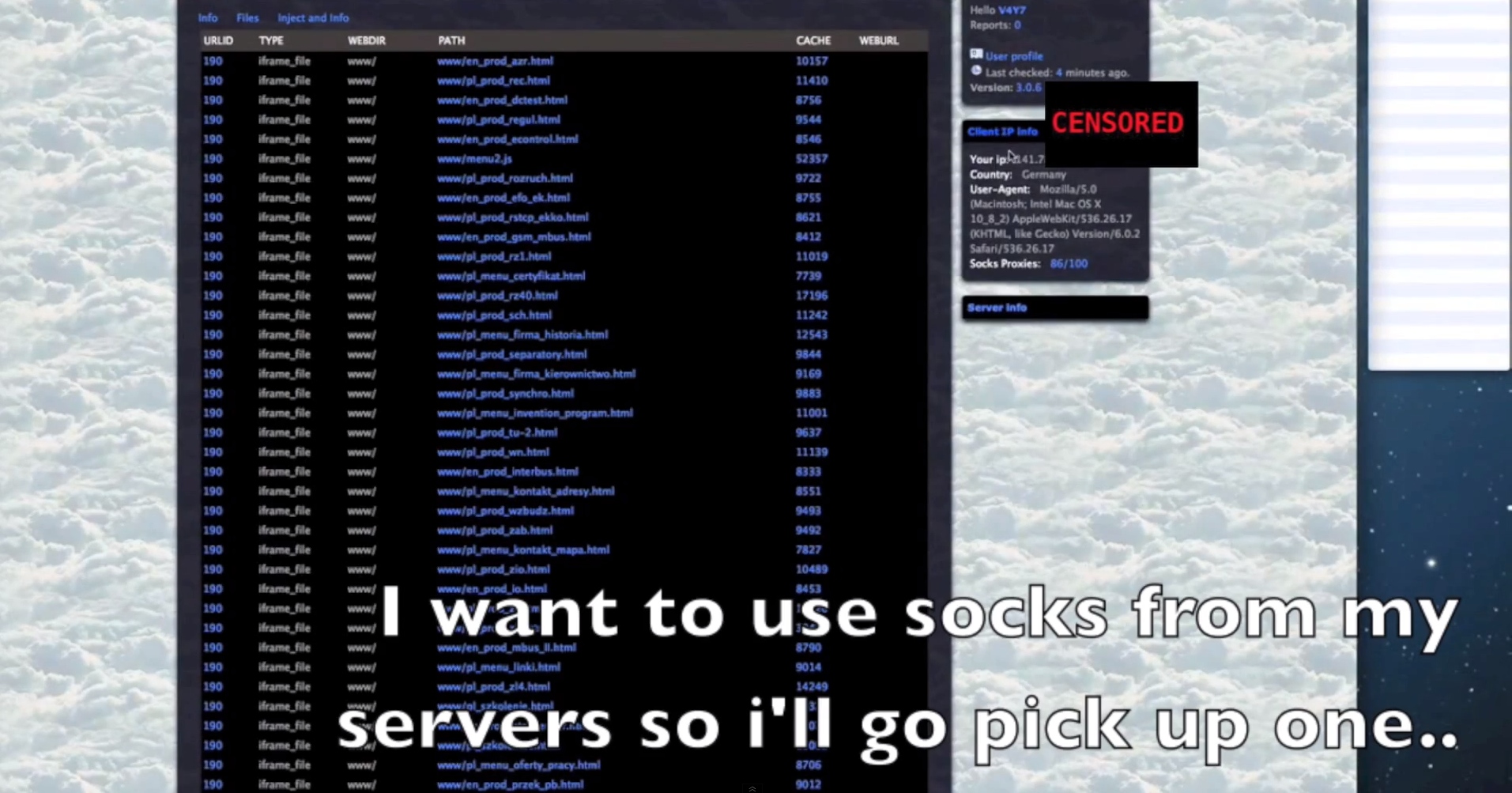
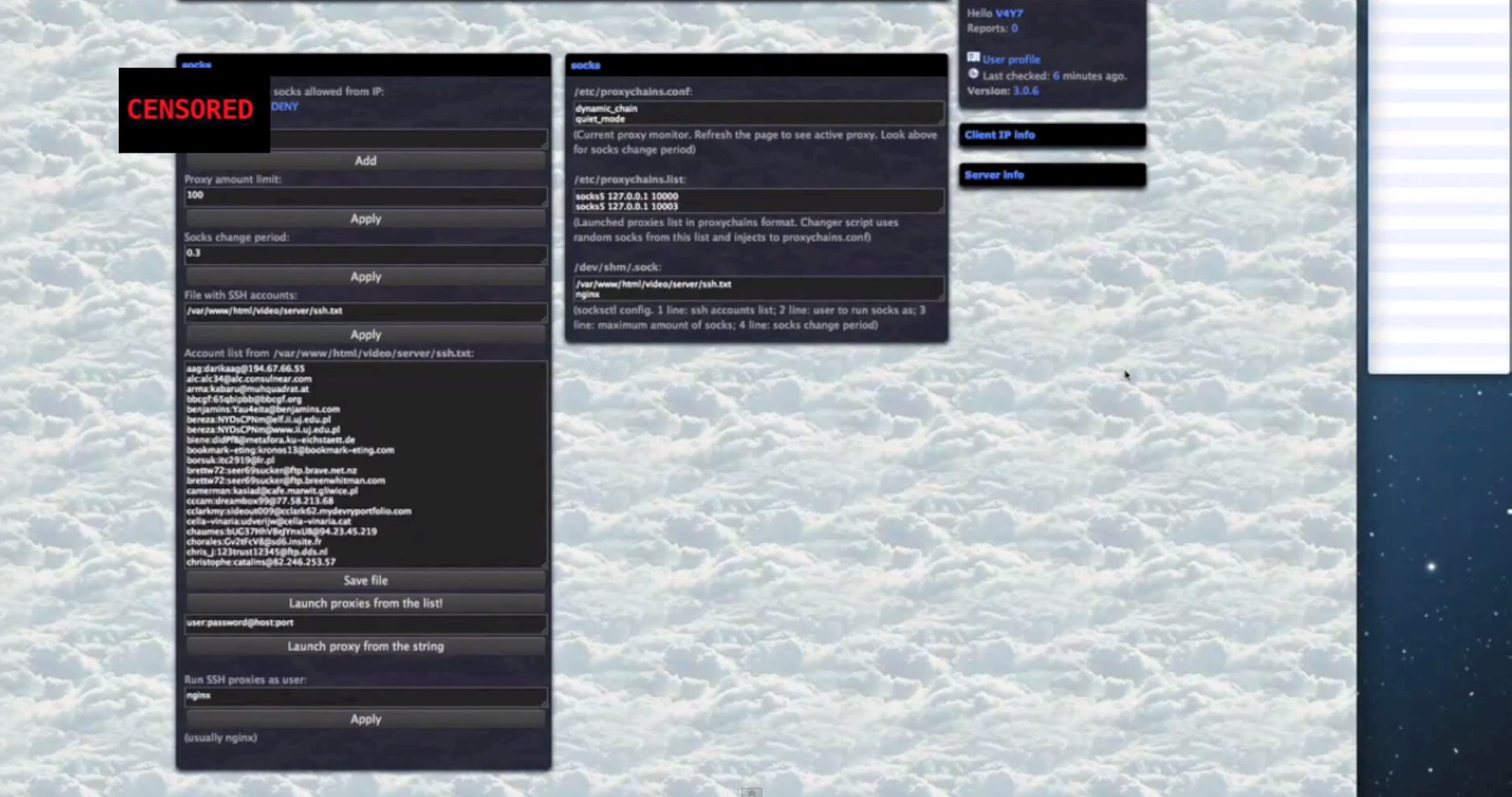
- The platform can also convert compromised servers into Socks servers, allowing the cybercriminals using it to add additional layers of anonymity to their operations.
- The source code is encrypted and, according to the author of the platform, is installed in a TrueCrypt container.
- Customer support is 24/7 with dedicated “specialists” ready to take into account the wishes of the customers regarding the future development of the platform.
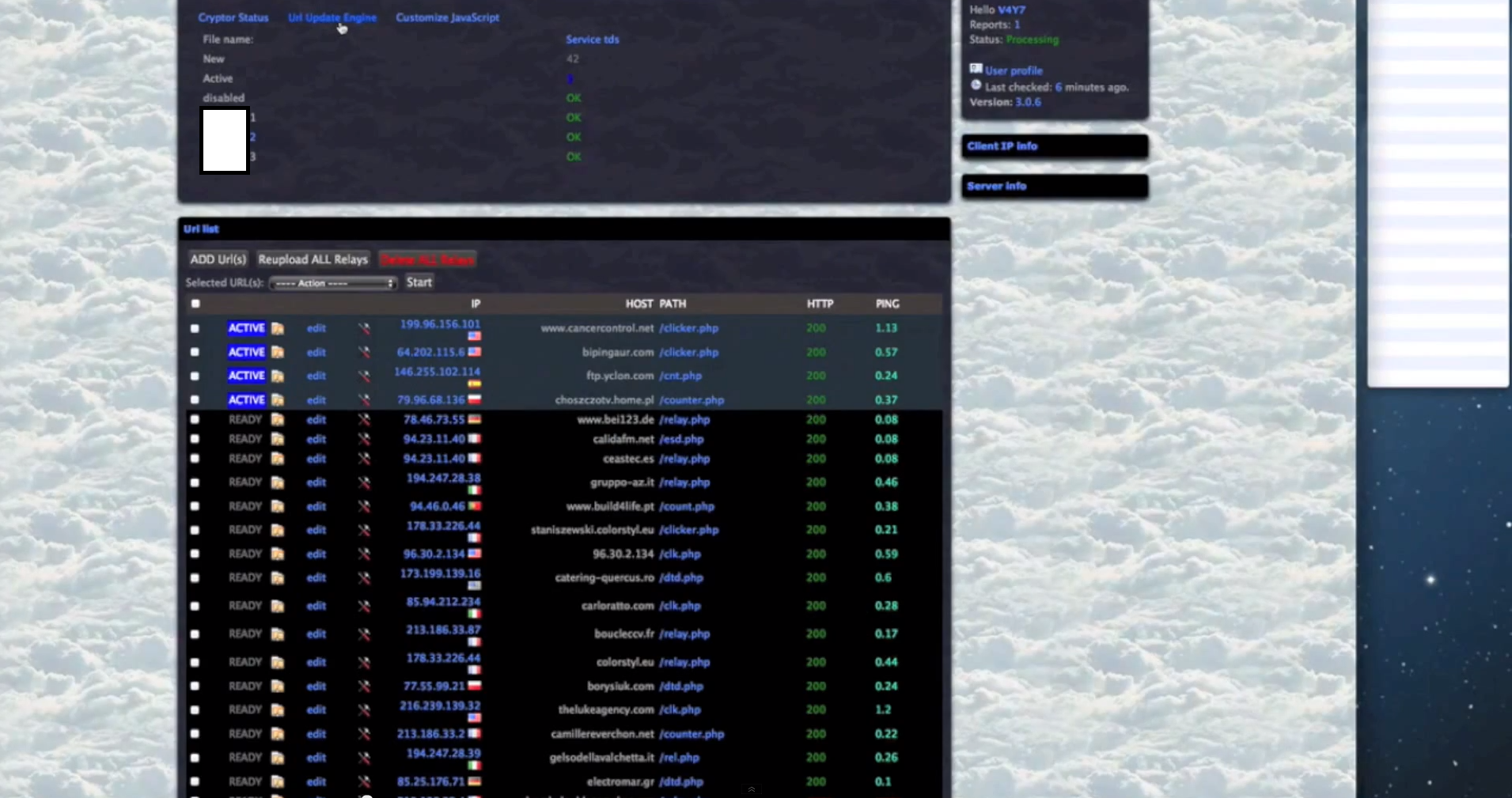
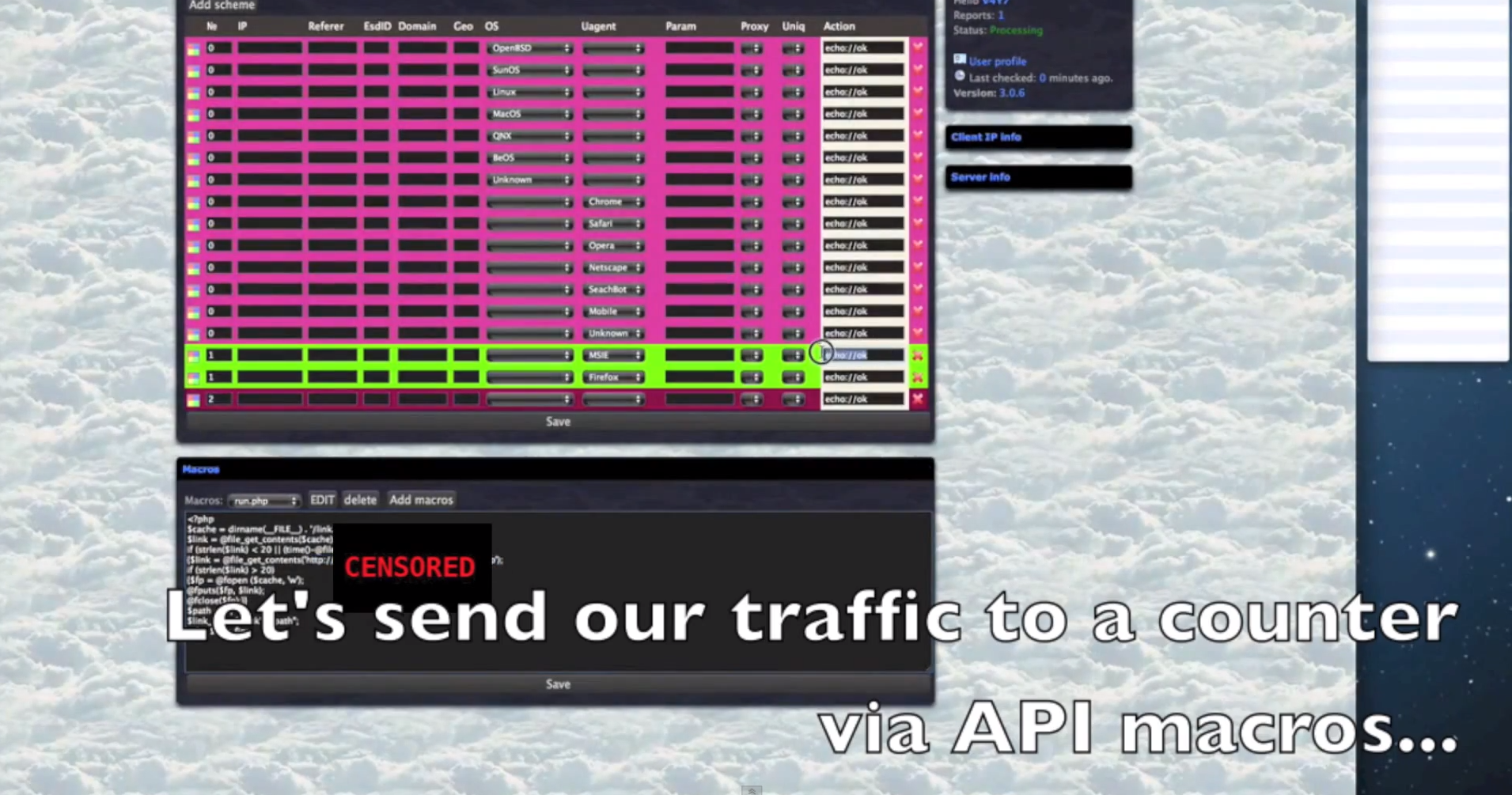
Sample screenshots of the platform in action:
The platform comes in both Lite and Pro versions. The software license for the Lite version is $1,000 for 30 days, or $6,000 for 1 year. The software license for the Pro version is $1,000 for 30 days, or $9,000 for 1 year. The vendor accepts Bitcoin, Perfect Money and WebMoney. Bulletproof platform hosting servers come as a bonus.
We’ll definitely be keeping an eye on the future development of this platform.
You can find more about Dancho Danchev at his LinkedIn Profile. You can also follow him on Twitter.