For many years now, cybercriminals have been efficiency abusing both legitimate compromised and automatically registered FTP accounts (using CAPTCHA outsourcing) in an attempt to monetize the process by uploading cybercrime-friendly ‘doorways’ or plain simple malicious scripts to be used later on in their campaigns.
This practice led to the emergence of DIY (do-it-yourself) tools and managed service platforms that allow virtually anyone to start monetizing these fraudulently or automatically registered accounting data, signaling a trend towards an efficiency-driven cybercrime ecosystem – a concept that’s been materializing on a daily basis for a couple of years.
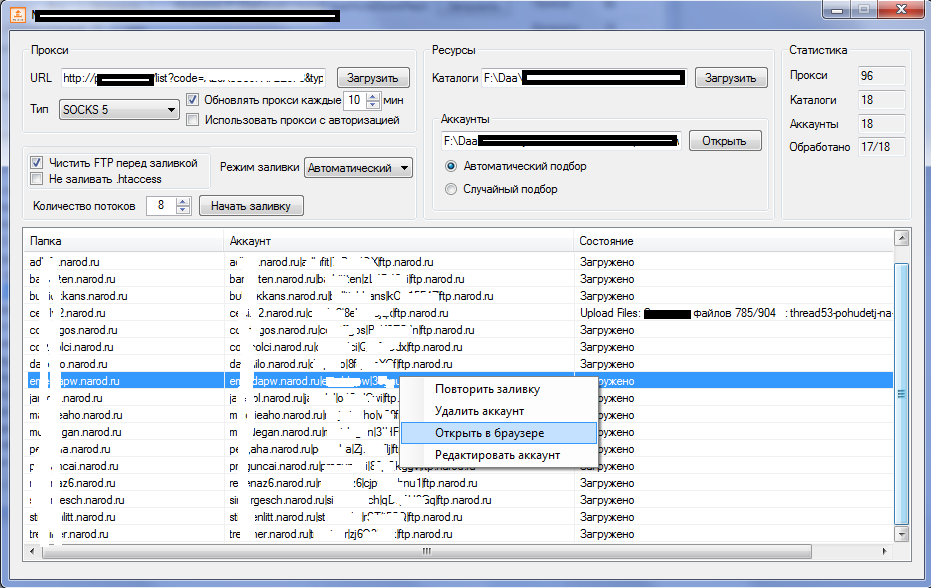
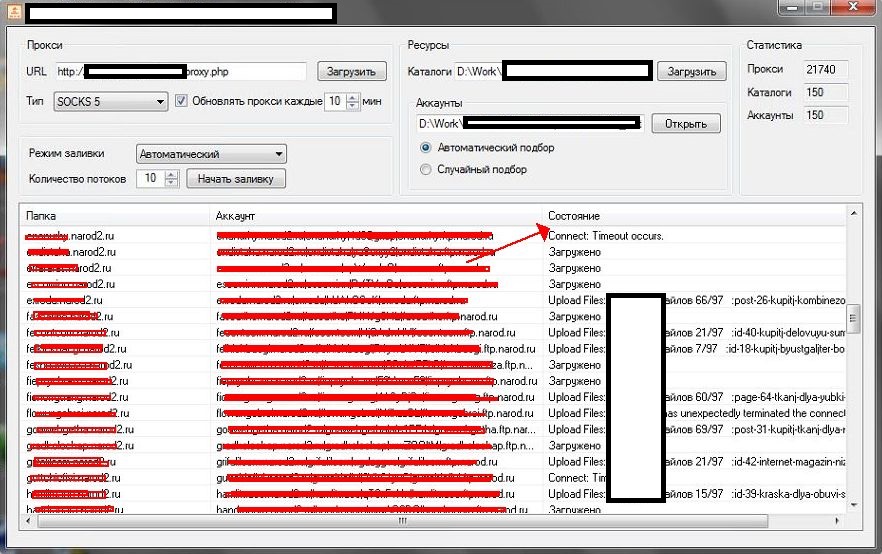
In this post, I’ll profile a desktop-based tool that allows cybercriminals to automatically syndicate lists of free/paid proxies — think malware-infected hosts — adding an additional layer of anonymity in the process of uploading their doorways/malicious scripts on any given FTP server whose accounting data they’ve managed to compromise or automatically register.
More details:
Sample screenshots of the application in action:
The tool works in a fairly simple way. It requires a list of user names and passwords, which it will then use to automatically upload any given set of files/scripts through the use of automatically syndicated fresh lists of proxies. Despite the tool’s rather modest set of features, it’s still capable of causing widespread damage, given that the cybercriminal using it, has managed to obtain/generate the accounting data.
Will this boutique cybercrime operation continue introducing new features in the long-term? As long as its author manages to build a loyal customer base, we believe that it will, however, in these highly competitive times within the cybercrime ecosystem, sophisticated efficiency-centered exploitation platforms are the tools that are truly re-shaping the threat landscape.
We’ll continue monitoring its development, and post updates as soon as new developments emerge.
You can find more about Dancho Danchev at his LinkedIn Profile. You can also follow him on Twitter.