 PUA’s (Potentially Unwanted Applications) are often nuisance applications which serve little purpose other than using your computer as a gateway for online advertisements or as a catalyst to deliver annoying applications that may pester you to the point where you want to throw your computer out a window. Anti-Malware companies usually have pretty weak detection of these types of programs and have generally failed to protect their customers’ computers from this sort of bloatware. As a result, countless users have to suffer through agonizing pains of pop-up windows, webpage redirects, search redirects, and sometimes even bluescreens just to try and get their daily TMZ fix.
PUA’s (Potentially Unwanted Applications) are often nuisance applications which serve little purpose other than using your computer as a gateway for online advertisements or as a catalyst to deliver annoying applications that may pester you to the point where you want to throw your computer out a window. Anti-Malware companies usually have pretty weak detection of these types of programs and have generally failed to protect their customers’ computers from this sort of bloatware. As a result, countless users have to suffer through agonizing pains of pop-up windows, webpage redirects, search redirects, and sometimes even bluescreens just to try and get their daily TMZ fix.
The problem from an Anti-Malware point-of-view stems from the fact that many of these types of PUA applications could have legitimate uses for some people who choose to install the software. Some people may enjoy the fact that their Google search results are redirected to some no-name search company (that often still uses Google results anyway) and that advertisements are inserted into their browser window all in exchange of being able to use that email smiley program for free. But the reality is, most people who obtain software in such a way have no interest in all the redirects, pop-up’s and advertisements. They simply want their smileys – which leads to the second problem.
People don’t read what appears on the screen!
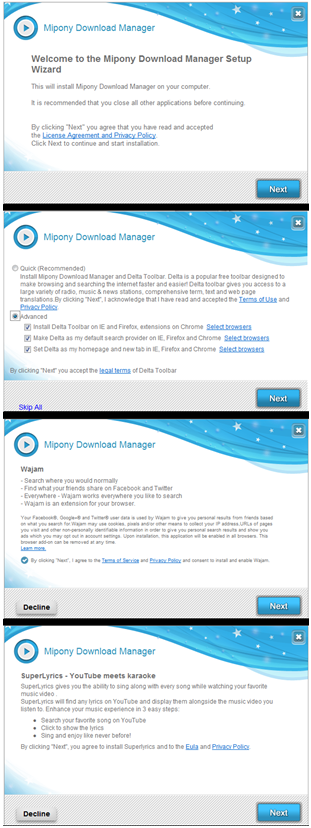
If users of such downloaded software would often just read the dialogue windows that appear, they would see that a combination of a few carefully selected ratio boxes would usually allow them to obtain their much-desired smiley program without obtaining all the garbage that comes along with it.
From a malware research perspective, it’s downright impossible to determine the intent of all the users of a software product. If we know that a certain application is being distributed via a deceptive download manager, but also, know some people use that same product for their own personal benefit, it becomes a difficult task in trying to make a determination whether or not to advise removal of the software in question. Many of us grew up in an era where the folk who were knowledgeable with computers would advise novice users to “download a program and just click next, next, next, until it is installed”. People learned the behavior of not reading and just clicking. (SouthPark devoted an entire episode to this exact issue) So I guess it should only be expected that people who have a financial motivation to install software to your computer have capitalized on this fact.
Take example the image to the left. This particular download manager attempts to install at least 5 different applications (We cut the image by 1 screen for the sake of saving space). After all the applications have been installed, our home page and search results were redirected. Advertisements were inserted to our browser windows and plugins were added to the browsers themselves. Simply reading the screen and clicking the ‘Decline’ button would have thwarted almost all of those unwanted behaviors.
Cases like what are shown above are usually quite easy to make a determination. We’ve previously written about many different campaigns that were distributing Potentially Unwanted Applications.
Other cases are a bit more vague, and making a determination on these types of installations is not so easy. We’re not setting out to write a blog post where we call-out reputable software vendors who bundle software with their products for the sole purpose of trying to earn a few dollars, but we would like to point out a recent example which has come to our attention and which highlights the difficulty we face when trying to make determinations within the PUA category.
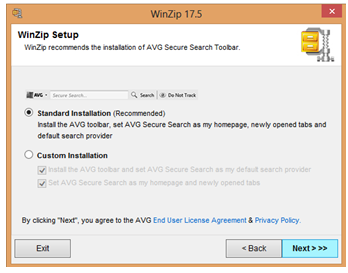
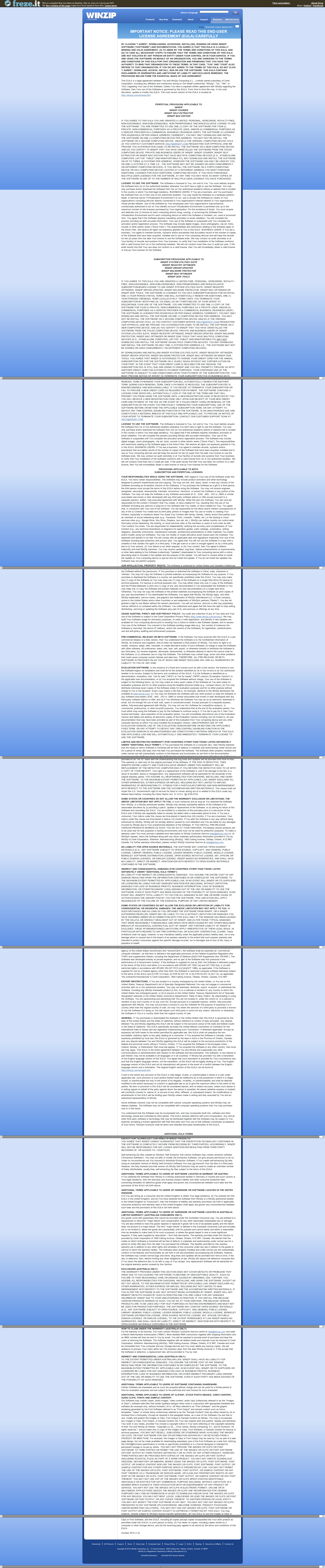
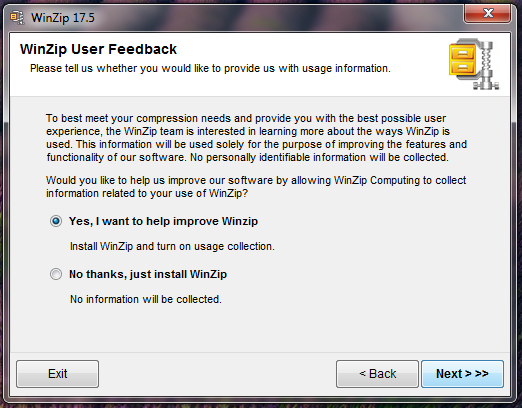
We have recently been provided a WinZip installer that we are flagging as PUA.Open.Install. The file in question writes files to the computer system identified as OpenInstall. Users who downloaded this particular Winzip wrapper were not presented with any sort of opt-out mechanism and after installation the users have software related to the security vendor AVG installed to their machine, plus have their homepage redirected without consent or authorization. (Please note that we don’t detect any of the WinZip or AVG files as PUA, simply the download wrapper.)
The MD5 in question can be seen from the following VirusTotal page:
Note the ‘Behavioural information’ tab. The information contained clearly indicates the creation of files related to OpenInstall as well as associated Network traffic:
Opened files
C:DOCUME~1<USER>~1LOCALS~1TempOIC1.tmp (successful)
C:DOCUME~1<USER>~1LOCALS~1Tempoi_WgCsg9bAeBOIAssistWTD.exe (successful)
Written files
C:DOCUME~1<USER>~1LOCALS~1TempOIC1.tmp (successful)
C:DOCUME~1<USER>~1LOCALS~1Tempoi_WgCsg9bAeBOIAssistWTD.exe (successful)
Runtime DLLs
c:docume~1<USER>~1locals~1tempoic1.tmp (successful)
HTTP requests
URL: http://st.cloins.com/
TYPE: POST
USER AGENT: Mozilla/4.0 (compatible; MSIE 6.0; Windows NT 5.1; SV1; OI build 3287)
URL: http://inst.avg.com/serve/getSetup.php?pid=2793661&k=43a9519ed4b5e9c75eb7d683e3d1e09708f9b34a&sid=&pid=2793661&k=43a9519ed4b5e9c75eb7d683e3d1e09708f9b34a&sid=&user_agent=Mozilla%2F5.0+%28compatible%3B+MSIE+10.0%3B+Windows+NT+6.2%3B%29
TYPE: POST
USER AGENT: Mozilla/4.0 (compatible; MSIE 6.0; Windows NT 5.1; SV1; OI build 3287)
DNS requests
st.cloins.com (173.203.98.33)
inst.avg.com (173.203.98.33)
As can be seen, several files relating to OpenInstall (OI) are written to the box and a specialized User Agent string is added to the network connection. Simply Googling the OIAssistWTD.exe file turns up many pages indicating that the software is not a desirable application. Additionally, the results indicate that several of our competitors also have detection criteria for the software, as-well-as being identified as unwanted by a variety of malware-related blogs:
- http://forums.malwarebytes.org/index.php?showtopic=101345
- http://www.microsoft.com/security/portal/threat/encyclopedia/entry.aspx?Name=Adware%3AWin32%2FOpenInstall&ThreatID=157719
- http://home.mcafee.com/VirusInfo/VirusProfile.aspx?key=3420873#none
- http://www.sophos.com/en-us/threat-center/threat-analyses/adware-and-puas/Open%20Install/detailed-analysis.aspx
- http://www.wilderssecurity.com/showthread.php?t=341325
- http://www.scumware.org/report/install.winzip.com
- http://kimletkeman.blogspot.com/2012/11/winzip-and-avg-partner-to-be-worlds.html
- https://news.ycombinator.com/item?id=2914341
To verify the behavior that we had seen on the submitted file, we downloaded the most recent version of the Winzip file from the Winzip website. On this particular version of the software, there were no disclaimers or warnings advising of the changes. Screenshots have been included below which show the various screens during the install process. Note that none indicated the installation of OpenInstall or AVG products.
When conducting these very same steps again today (while preparing for this blog entry), we see that the Winzip installer is now providing a disclaimer and ‘opt-out’ functionality prior to initiating the download. This quick change shows the fast-paced and quickly evolving landscape that we find ourselves in, and shows the difficulty we face with Download Managers that are capable of changing their wrapper at a moment’s notice.
So, who is OpenInstall? According to Bloomberg Businessweek, OpenInstall “operates as a cloud based installation company”, and that ‘the company offers CloudInstaller to manage software download and installation for development teams to focus on their core product and for marketing teams to provide input into the conversion funnel for their software’. The overview goes on to state that OpenInstall “provides a management platform to make right offers to right users at the right time”. The overview provides the company web address of www.openinstall.com . Clearly, the Company Overview indicates an advertising agenda. Trying to access the OpenInstall.com website proves to be an act of futility as the site is no longer online. This downed website comes despite the fact that some download locations for the Winzip software still indicate that “By clicking download, you agree to the OpenInstall EULA and Privacy Policy”. Those EULA and Privacy Policy links attempt to direct users to the OpenInstall.com website.
A bit more research into the company turns up this filing with the S.E.C. which indicates that security vendor AVG acquired OpenInstall in January 2012.
I think we can all agree that reputable companies such as Winzip and AVG are not performing activities on computers which would be deemed malicious, but it’s hard not to ignore the fact that the OpenInstall product does write files to the computer (OI related files) and that in at least some cases, a means to opt-out is not provided, and yet that in even more cases, there is not a valid EULA.
As if all the above information isn’t confusing enough, the data produced by the Webroot Security Intelligence Network reveals some interesting information regarding files related to OpenInstall. We would like to highlight some file characteristics which most people won’t have the ability to see on a large scale, but from a Malware Research perspective seem quite suspicious.
In the below view, we have grouped together a partial listing of the OpenInstall files. The following files all share the same internal data-points, meaning they are all files that share a similar code-base. None of the files have ever been seen on more than 1 PC. We have columns for: File Name, Vendor (from the file properties tab), Product Description, Version, and Digital Vendor. Take note of some of the included entries. Several of the files have file names relating to one product, Vendors relating to other products, and then Digital Vendors relating to something totally different. Our Intelligence Network has identified thousands of similar files. Even people who don’t spend their days researching malware must acknowledge that conflicting Filenames, Vendors and Digital Vendors should be a characteristic that stands out as not being normal.

Being presented with all this varying and sometimes conflicting information, what type of determination should a Malware Analysis take on this type of software? At least in some cases, users have no option to opt-out. If they can’t opt-out, users face changes to their search provider as well as a home page reset. The software in question has a dubious reputation among members of the Anti-Malware community, and some of our competitors have detections for this software. From an analysis perspective, we see some interesting (to say the least) aspects with the topical information of files. Search results for the written files (OIAssistWTD.exe) indicate OpenInstall as the owner, yet there is no website information for OpenInstall, and thus no available EULA under that name. It takes a good bit of research to uncover the fact that the OI related files are now owned by AVG.
Considering all of this, how do we not consider the software in question to be Potentially Unwanted?
Maybe others will have a different view. We’re more than willing to entertain a discussion on this topic. If you have a different opinion or viewpoint regarding this issue, we would be more than happy to hear it. Leave your thoughts in the comments section below and we will be sure to read them.












OpenInstall used to install a bunch of adware, but now it seems to just install the AVG toolbar. Before they got bought by AVG, they were seen mostly installed by GameTheory, LLC, who were responsible for makemybaby/vampireme stuff:
https://profiles.google.com/109412257237874861202/buzz/FXL1y8qG7YF
Thanks for sharing about some unwanted software install signature this may helpful to identify the threat.
My son has installed a potentially unwanted applications on to our computer. I cannot remove it – it is called Key-find.com and it will not allow me to reinstall my home page. Any suggestions?
see more
http://tec24x7.blogspot.in/ http://tec24x7.blogspot.in/2014/08/norton-support-resolves-issues-and.html
detected fusion.dll as a PUA.Core.Fusion
Can someone explain what this is, and what it does, as it was downloaded alongside a program called CheatEngine V6.6, where fusion.dll was in temp, other than in any file associated with CheatEngine. I deleted it and the program works fine, but I still want to know what this PUA.Core.Fusion could have done to my computer.
Hello Deuce,
Please contact our Technical Support Team directly. They will collect the logs from your daily scans to analyze the file in question.
Support Number: 1-866-612-4227 M-F 7am−6pm MT
Send us a Support Ticket: https://detail.webrootanywhere.com/servicewelcome.asp
Warm Regards,
Josh P.
Social Media Coordinator
Latest webroot scans have picked up at least 2 up to 5 of these pua’s. But I am not sure how to resolve, correct, or get rid of the problem. Maybe it is too late. Is there some way to determine which engines, etc., these have added so I can get rid of them?
It’s never too late, Bob.
Please let our Support Team address this for you. They’ll be able to completely remove these PUA’s and answer all your questions.
Support Number: 1-866-612-4227 M-F 7am−6pm MT
Send a Support Ticket: http://wbrt.io/eyqx
Warm Regards,
Josh P.
Social Media Coordinator